Palo Alto Networks PCNSA Palo Alto Networks Certified Network Security Administrator Online Training
Palo Alto Networks PCNSA Online Training
The questions for PCNSA were last updated at Apr 24,2025.
- Exam Code: PCNSA
- Exam Name: Palo Alto Networks Certified Network Security Administrator
- Certification Provider: Palo Alto Networks
- Latest update: Apr 24,2025
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
- A . Reset-server
- B . Deny
- C . Drop
- D . Block
C
Explanation:
Drop silently drops the packet, while deny gives an update.
Based on the graphic, which statement accurately describes the output shown in the Server Monitoring panel?
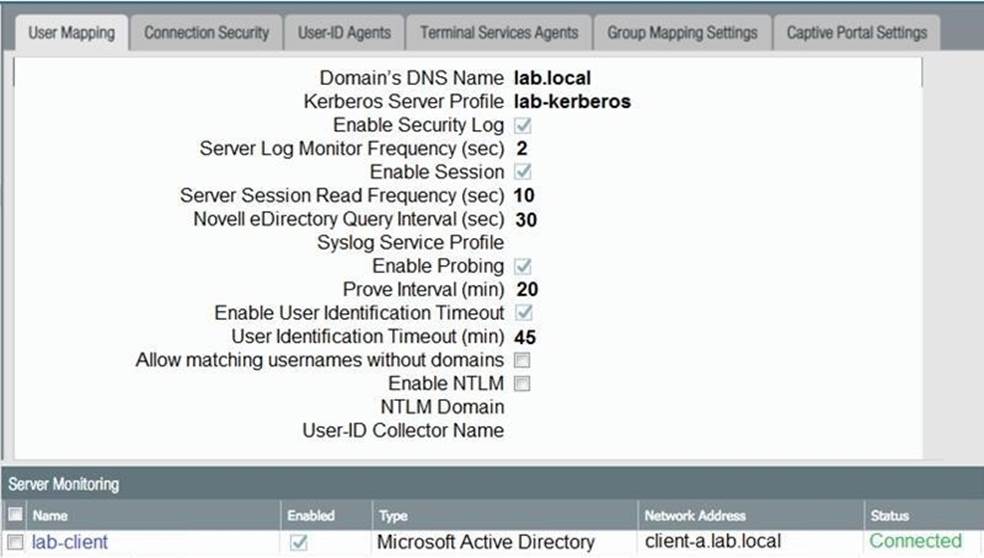
- A . The User-ID agent is connected to a domain controller labeled lab-client.
- B . The host lab-client has been found by the User-ID agent.
- C . The host lab-client has been found by a domain controller.
- D . The User-ID agent is connected to the firewall labeled lab-client.
A
Explanation:
lab-client is not a host, it is the name we are giving to the agent that is connecting to the specified domain controller (Active Directory).
The Administrator profile "PCNSA Admin" is configured with an Authentication profile "Authentication Sequence PCNSA".
The Authentication Sequence PCNSA has a profile list with four Authentication profiles: Auth Profile LDAP
Auth Profile Radius Auth Profile Local Auth Profile TACACS
After a network outage, the LDAP server is no longer reachable. The RADIUS server is still reachable but has lost the "PCNSA Admin" username and password.
Which option describes the "PCNSA Admin" login capabilities after the outage?
- A . Auth OK because of the Auth Profile TACACS
- B . Auth KO because RADIUS server lost user and password for PCNSA Admin
- C . Auth OK because of the Auth Profile Local
- D . Auth KO because LDAP server is not reachable
An administrator needs to add capability to perform real-time signature lookups to block or sinkhole all known malware domains.
Which type of single unified engine will get this result?
- A . User-ID
- B . App-ID
- C . Security Processing Engine
- D . Content-ID
D
Explanation:
Content-IDTM combines a real-time threat prevention engine with a comprehensive URL database and elements of application identification to limit unauthorized data and file transfers and detect and block a wide range of exploits, malware, dangerous web surfing as well as targeted and unknown threats.
https://www.paloaltonetworks.com/content/dam/pan/en_US/assets/pdf/tech-briefs/techbrief- content-id.pdf
Which three types of entries can be excluded from an external dynamic list? (Choose three.)
- A . IP addresses
- B . Applications
- C . User-ID
- D . Domains
- E . URLs
ADE
Explanation:
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/view-external-dynamic-list-entries
An administrator would like to determine the default deny action for the application dns-over-
https.
Which action would yield the information?
- A . View the application details in beacon paloaltonetworks.com
- B . Check the action for the Security policy matching that traffic
- C . Check the action for the decoder in the antivirus profile
- D . View the application details in Objects > Applications
An administrator configured a Security policy rule with an Antivirus Security profile. The administrator did not change the action for the profile.
If a virus gets detected, how will the firewall handle the traffic?
- A . It allows the traffic but generates an entry in the Threat logs.
- B . It drops the traffic because the profile was not set to explicitly allow the traffic.
- C . It allows the traffic because the profile was not set the explicitly deny the traffic.
- D . It uses the default action assigned to the virus signature.
Which security policy rule would be needed to match traffic that passes between the Outside zone and Inside zone, but does not match traffic that passes within the zones?
- A . global
- B . intrazone
- C . interzone
- D . universal
C
Explanation:
intrazone allows traffic within a zone not between different zones.
An internal host wants to connect to servers of the internet through using source NAT.
Which policy is required to enable source NAT on the firewall?
- A . post-NAT policy with external source and any destination address
- B . NAT policy with no source of destination zone selected
- C . NAT policy with source zone and destination zone specified
- D . pre-NAT policy with external source and any destination address
An administrator would like to create a URL Filtering log entry when users browse to any gambling website.
What combination of Security policy and Security profile actions is correct?
- A . Security policy = drop, Gambling category in URL profile = allow
- B . Security policy = deny. Gambling category in URL profile = block
- C . Security policy = allow, Gambling category in URL profile = alert
- D . Security policy = allow. Gambling category in URL profile = allow
C
Explanation:
A log entry is generated in the URL filtering log.
https://docs.paloaltonetworks.com/advanced-url-filtering/administration/url-filtering-basics/url-filtering-profiles
Latest PCNSA Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

