Palo Alto Networks PCNSA Palo Alto Networks Certified Network Security Administrator Online Training
Palo Alto Networks PCNSA Online Training
The questions for PCNSA were last updated at Apr 27,2025.
- Exam Code: PCNSA
- Exam Name: Palo Alto Networks Certified Network Security Administrator
- Certification Provider: Palo Alto Networks
- Latest update: Apr 27,2025
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
- A . URL Filtering
- B . Vulnerability Protection
- C . Anti-Spyware
- D . Antivirus
C
Explanation:
In addition, you can enable the DNS sinkholing action in Anti-Spyware profiles to enable the firewall to forge a response to a DNS query for a known malicious domain, causing the malicious domain name to resolve to an IP address that you define.
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/security-profiles
Actions can be set for which two items in a URL filtering security profile? (Choose two.)
- A . Block List
- B . Custom URL Categories
- C . PAN-DB URL Categories
- D . Allow List
BC
Explanation:
Action can be set to following three categories:
-Custom URL categories
-External dynamic Lists
-Pan-DB predefined URL categories
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/content-inspection-features/url-filtering-multi-category.html
Which interface type requires no routing or switching but applies Security or NAT policy rules before passing allowed traffic?
- A . Tap
- B . Virtual Wire
- C . Layer 2
- D . Layer 3
B
Explanation:
A virtual wire logically binds two Ethernet interfaces together, allowing for all traffic to pass between the interfaces, or just traffic with selected VLAN tags (no other switching or routing services are available). You can create virtual wire subinterfaces to classify traffic according to an IP address, IP range, or subnet. A virtual wire requires no changes to adjacent network devices.
A virtual wire can bind two Ethernet interfaces of the same medium (both copper or both fiber optic),
or bind a copper interface to a fiber optic interface.
In order to protect users against exploit kits that exploit a vulnerability and then automatically download malicious payloads, which Security profile should be configured?
- A . Anti-Spyware
- B . WildFire
- C . Vulnerability Protection
- D . Antivirus
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-admin/policy/security-profiles
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
- A . DNS Security
- B . Threat Prevention
- C . WildFire
- D . SD-Wan
B
Explanation:
An active Threat Prevention license is required to obtain Palo Alto Networks built-in EDLs. These built-in EDLs protect your network against malicious hosts.
Which prevention technique will prevent attacks based on packet count?
- A . zone protection profile
- B . URL filtering profile
- C . antivirus profile
- D . vulnerability profile
A
Explanation:
DoS Protection adds another layer of defense against attacks on individual devices, which can succeed if the Zone Protection profile thresholds are above the CPS rate of the attack on the device.
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis Unit 42 research and data gathered from telemetry?
- A . Palo Alto Networks C&C IP Addresses
- B . Palo Alto Networks Bulletproof IP Addresses
- C . Palo Alto Networks High-Risk IP Addresses
- D . Palo Alto Networks Known Malicious IP Addresses
D
Explanation:
Palo Alto Networks Known Malicious IP Addresses
–Contains IP addresses that are verified malicious based on WildFire analysis, Unit 42 research, and data gathered from telemetry (Share Threat Intelligence with Palo Alto Networks). Attackers use these IP addresses almost exclusively to distribute malware, initiate command-and-control activity,
and launch attacks.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/policy/use-an-external-dynamic-list-in-policy/built-in-edls
An administrator reads through the following Applications and Threats Content Release Notes before an update:
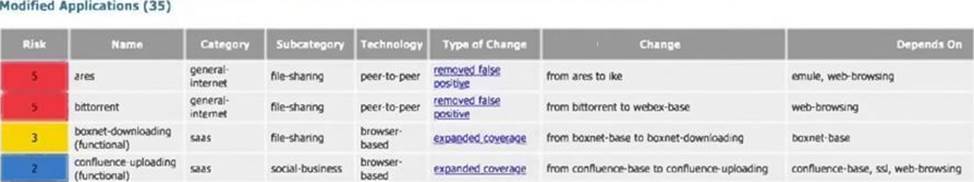
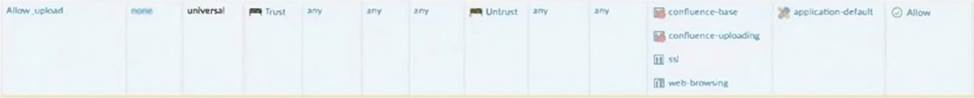
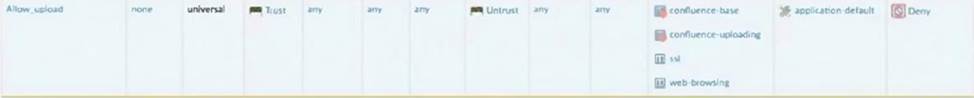
Which rule would continue to allow the file upload to confluence after the update?
A)
B)

C)
![]()
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
In order to fulfill the corporate requirement to backup the configuration of Panorama and the Panorama-managed firewalls securely, which protocol should you select when adding a new scheduled config export?
- A . HTTPS
- B . SMB v3
- C . SCP
- D . FTP
In order to fulfill the corporate requirement to backup the configuration of Panorama and the Panorama-managed firewalls securely, which protocol should you select when adding a new scheduled config export?
- A . HTTPS
- B . SMB v3
- C . SCP
- D . FTP
Latest PCNSA Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

