Palo Alto Networks PCNSA Palo Alto Networks Certified Network Security Administrator Online Training
Palo Alto Networks PCNSA Online Training
The questions for PCNSA were last updated at Apr 28,2025.
- Exam Code: PCNSA
- Exam Name: Palo Alto Networks Certified Network Security Administrator
- Certification Provider: Palo Alto Networks
- Latest update: Apr 28,2025
What is a function of application tags?
- A . creation of new zones
- B . application prioritization
- C . automated referenced applications in a policy
- D . IP address allocations in DHCP
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
- A . Configure an authentication policy
- B . Configure an authentication sequence
- C . Configure an authentication profile
- D . Isolate the management interface on a dedicated management VLAN
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/firewall-administration/manage-firewall-administrators/configure-administrative-accounts-and-authentication/configure-a-firewall-administrator-account
Which rule type is appropriate for matching traffic occurring within a specified zone?
- A . Universal
- B . Shadowed
- C . Intrazone
- D . Interzone
Drag and Drop Question
Place the following steps in the packet processing order of operations from first to last.
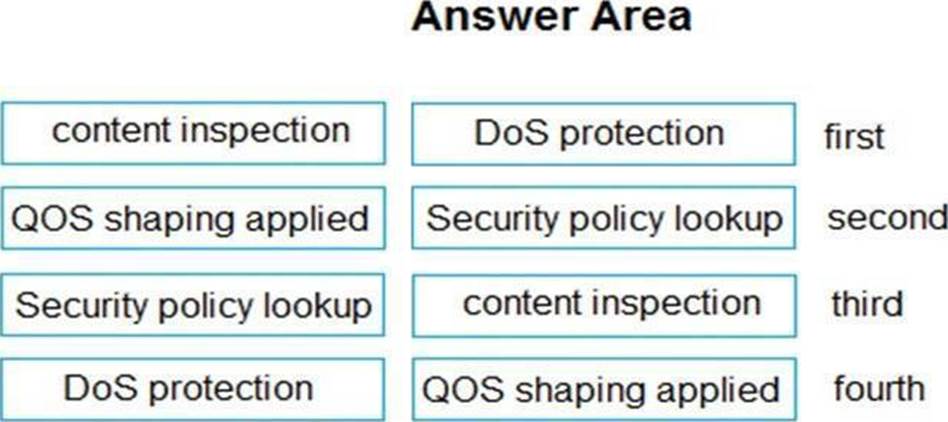
Explanation:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClVHCA0
You receive notification about a new malware that infects hosts. An infection results in the infected host attempting to contact a command-and-control server.
Which Security Profile when applied to outbound Security policy rules detects and prevents this threat from establishing a command-and-control connection?
- A . Antivirus Profile
- B . Data Filtering Profile
- C . Vulnerability Protection Profile
- D . Anti-Spyware Profile
D
Explanation:
Anti-Spyware Security Profiles block spyware on compromised hosts from trying to communicate with external command-and-control (C2) servers, thus enabling you to detect malicious traffic leaving
the network from infected clients.
The data plane provides which two data processing features of the firewall? (Choose two.)
- A . signature matching
- B . reporting
- C . network processing
- D . logging
Which type of DNS signatures are used by the firewall to identify malicious and command-and-control domains?
- A . DNS Malicious signatures
- B . DNS Security signatures
- C . DNS Malware signatures
- D . DNS Block signatures
B
Explanation:
https://docs.paloaltonetworks.com/dns-security/administration/configure-dns-security/enable-dns-security#tabs-id066476b2-c4dd-4fc0-b7e4-f4ba32e19f60
What is an advantage for using application tags?
- A . They are helpful during the creation of new zones
- B . They help with the design of IP address allocations in DHCP.
- C . They help content updates automate policy updates
- D . They help with the creation of interfaces
C
Explanation:
Tags. All Tags. Are specific to the creation of Policy. They have several purposes, apply to any object, can be defined and so forth. I am uncertain as to whether any action subsequent to their application is automated or not. The only thing I’m clear on is, they are Security Policy related, or to it’s creation, whether automated or not.
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
- A . override
- B . allow
- C . block
- D . continue
Which two statements are correct about App-ID content updates? (Choose two.)
- A . Updated application content may change how security policy rules are enforced
- B . After an application content update, new applications must be manually classified prior to use
- C . Existing security policy rules are not affected by application content updates
- D . After an application content update, new applications are automatically identified and classified
AD
Explanation:
As new App-IDs are introduced and delivered to the firewall via weekly updates, dynamic filters are automatically updated for those applications that meet the filter criteria. This helps minimize administrative effort associated with security policy management. https://www.paloaltonetworks.com/resources/techbriefs/app-id-tech-brief.html
Latest PCNSA Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

