Palo Alto Networks PCCSE Prisma Certified Cloud Security Engineer Online Training
Palo Alto Networks PCCSE Online Training
The questions for PCCSE were last updated at Dec 24,2025.
- Exam Code: PCCSE
- Exam Name: Prisma Certified Cloud Security Engineer
- Certification Provider: Palo Alto Networks
- Latest update: Dec 24,2025
Which options show the steps required after upgrade of Console?
- A . Uninstall Defenders Upgrade Jenkins Plugin
Upgrade twistcli where applicable
Allow the Console to redeploy the Defender - B . Update the Console image in the Twistlock hosted registry Update the Defender image in the
Twistlock hosted registry Uninstall Defenders - C . Upgrade Defenders Upgrade Jenkins Plugin
Upgrade twistcli where applicable - D . Update the Console image in the Twistlock hosted registry Update the Defender image in the Twistlock hosted registry Redeploy Console
Create an Alert rule
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
- A . https://api.prismacloud.io/cloud/
- B . https://api.prismacloud.io/account/aws
- C . https://api.prismacloud.io/cloud/aws
- D . https://api.prismacloud.io/accountgroup/aws
A security team has a requirement to ensure the environment is scanned for vulnerabilities.
What are three options for configuring vulnerability policies? (Choose three.)
- A . individual actions based on package type
- B . output verbosity for blocked requests
- C . apply policy only when vendor fix is available
- D . individual grace periods for each severity level
- E . customize message on blocked requests
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
- A . Disable the policy
- B . Set the Alert Disposition to Conservative
- C . Change the Training Threshold to Low
- D . Set Alert Disposition to Aggressive
What is the behavior of Defenders when the Console is unreachable during upgrades?
- A . Defenders continue to alert, but not enforce, using the policies and settings most recently cached before upgrading the Console.
- B . Defenders will fail closed until the web-socket can be re-established.
- C . Defenders will fail open until the web-socket can be re-established.
- D . Defenders continue to alert and enforce using the policies and settings most recently cached before upgrading the Console.
How are the following categorized?
Backdoor account access Hijacked processes Lateral movement
Port scanning
- A . audits
- B . incidents
- C . admission controllers
- D . models
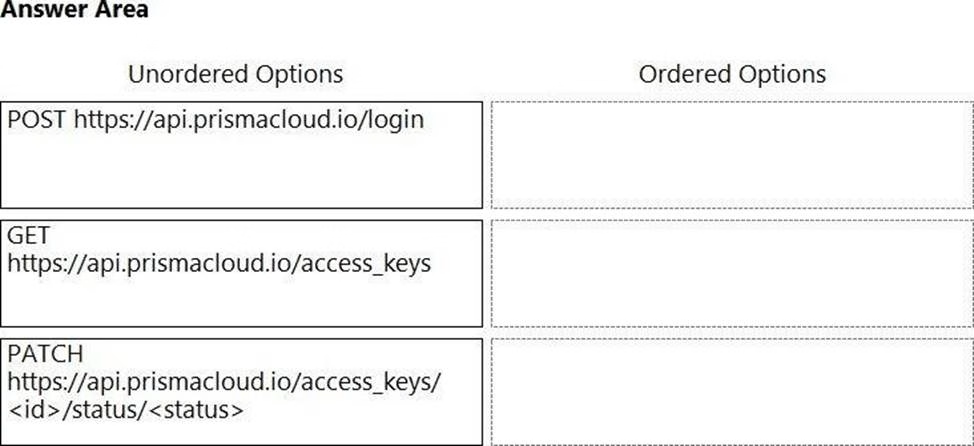
DRAG DROP
An administrator needs to write a script that automatically deactivates access keys that have not been used for 30 days.
In which order should the API calls be used to accomplish this task? (Drag the steps into the correct order from the first step to the last.)
Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?
- A . single sign-on
- B . SAML
- C . basic authentication
- D . access key
Which option shows the steps to install the Console in a Kubernetes Cluster?
- A . Download the Console and Defender image Generate YAML for Defender Deploy Defender YAML using kubectl
- B . Download and extract release tarball Generate YAML for Console Deploy Console YAML using kubectl
- C . Download the Console and Defender image Download YAML for Defender from the document site Deploy Defender YAML using kubectl
- D . Download and extract release tarball Download the YAML for Console Deploy Console YAML using kubectl
Latest PCCSE Dumps Valid Version with 85 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


