Palo Alto Networks PCCSA Palo Alto Networks Certified Cybersecurity Associate Online Training
Palo Alto Networks PCCSA Online Training
The questions for PCCSA were last updated at Apr 21,2025.
- Exam Code: PCCSA
- Exam Name: Palo Alto Networks Certified Cybersecurity Associate
- Certification Provider: Palo Alto Networks
- Latest update: Apr 21,2025
Which type of adversary would commit cybercrimes with the authorization of their country’s government?
- A . state-sponsored
- B . hacktivist
- C . gray hat
- D . white hat
When a company chooses to deploy a branch location with antivirus software, which risk model are they using to manage risk?
- A . limiting
- B . assuming
- C . trasnferring
- D . avoiding
Which option describes a characteristic of a distributed denial-of-service attack?
- A . uses multiple types of malware to corrupt system services
- B . uses a single remote host to delete data from multiple target servers
- C . uses a single remote host to flood a target network with traffic
- D . uses a botnet to flood traffic to a target network
What is a component of a public key infrastructure?
- A . Key Distribution Center
- B . KDC ticket
- C . SSH key
- D . certificate authority
From which resource can a Palo Alto Networks firewall get URL category information for URLs whose categories cannot be found on the firewall?
- A . App-ID database
- B . WildFire
- C . PDF file
- D . PAN-DB database
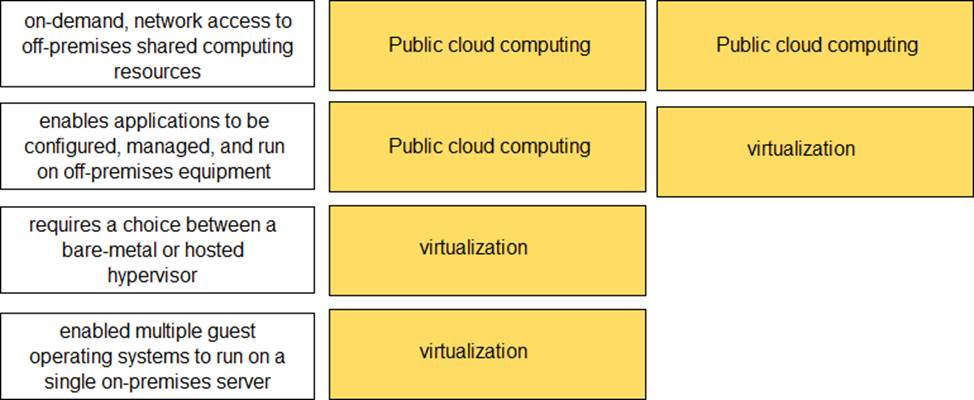
What does a hypervisor enable?
- A . high-speed searching of already aggregated security log files
- B . high-speed aggregation and viewing of security log files
- C . multiple physical machines to be configured into a high-performance cluster
- D . multiple guest operating systems to run on a single physical machine
DRAG DROP
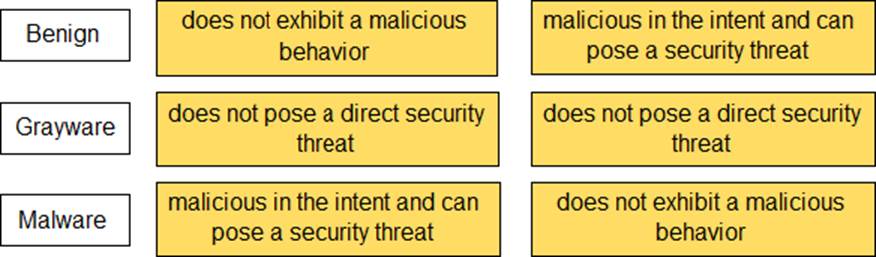
Match the Palo Alto Networks Wild Fire analysis verdict with its definition.
Identify a weakness of a perimeter-based network security strategy to protect an organization’s endpoint systems.
- A . It cannot identify command-and-control traffic.
- B . It cannot monitor all potential network ports.
- C . It assumes that all internal devices are untrusted.
- D . It assumes that every internal endpoint can be trusted.
Which type of security device uses a single-pass, parallel processor hardware architecture to accelerate content inspection?
- A . unified threat management
- B . stateless firewalls
- C . next-generation firewall
- D . PoS-based firewall
Latest PCCSA Dumps Valid Version with 50 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund