Nutanix NCP-MCI-5.15 Nutanix Certified Professional – Multicloud Infrastructure (v5.15) Online Training
Nutanix NCP-MCI-5.15 Online Training
The questions for NCP-MCI-5.15 were last updated at Dec 20,2025.
- Exam Code: NCP-MCI-5.15
- Exam Name: Nutanix Certified Professional - Multicloud Infrastructure (v5.15)
- Certification Provider: Nutanix
- Latest update: Dec 20,2025
An administrator has set up a local web server accessible to the Nutanix clusters.
Which two steps are required to set up LCM for an environment without Internet access? (Choose two.)
- A . Download the lcai_disconnecced_version. tar.gz LCM bundle from the support portal.
- B . Edit LCM Advanced Settings in Prism Element and enter the address of the web server.
- C . Edit LCM Advanced Settings m Prism Central and enter the address of the web server.
- D . Download the lcm_dark_site_version. tar . gz LCM bundle from the support portal.
An administrator needs to boot a VM to a bootable CD. The administrator tries to configure the VM to boot to it, select to add disk, and goes to the images available. The image for the bootable CD is unavailable.
What is the Likely issue?
- A . The CD-ROM interface is too slow.
- B . The administrator selected a disk attached before it can boot to a CD.
- C . The VM needs to have a standard disk attached before it can boot to a CD.
- D . The bootable CD image is corrupted during creation.
B
Explanation:
Reference: https://next.nutanix.com/prism-infrastructure-management-26/booting-vm-to-cd-no-drives-present-31800
Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
- A . Continuous Data Protection
- B . Copy-on-Write
- C . Split-mirror
- D . Redirect-On-Write
A VM in a 12-node Nutanix cluster is hosting an application that has specific Physical GPU requirements. Only three nodes in the cluster meet this requirement.
The administrator wants to allow a general workload to be distributed across all nodes in the cluster and must make sure that the node hosting the VM meets its requirements.
How should the administrator perform this task?
- A . Create a sperate three-node cluster using the nodes that meet the requirement.
- B . Configure VM-Host affinity for the nodes that meet the application’s GPU requirement.
- C . Over-Provision the application VM with additional virtual GPUs.
- D . Configure anti-affinity rules between the application VM and the other VMs running on the cluster.
In which two scenarios is Native Key Management Server supported? (Choose two)
- A . XenServer and AHV mixed cluster.
- B . Hyper-V and AHV mixed cluster.
- C . KVM and AHV mixed cluster.
- D . ESXi and AHV mixed cluster.
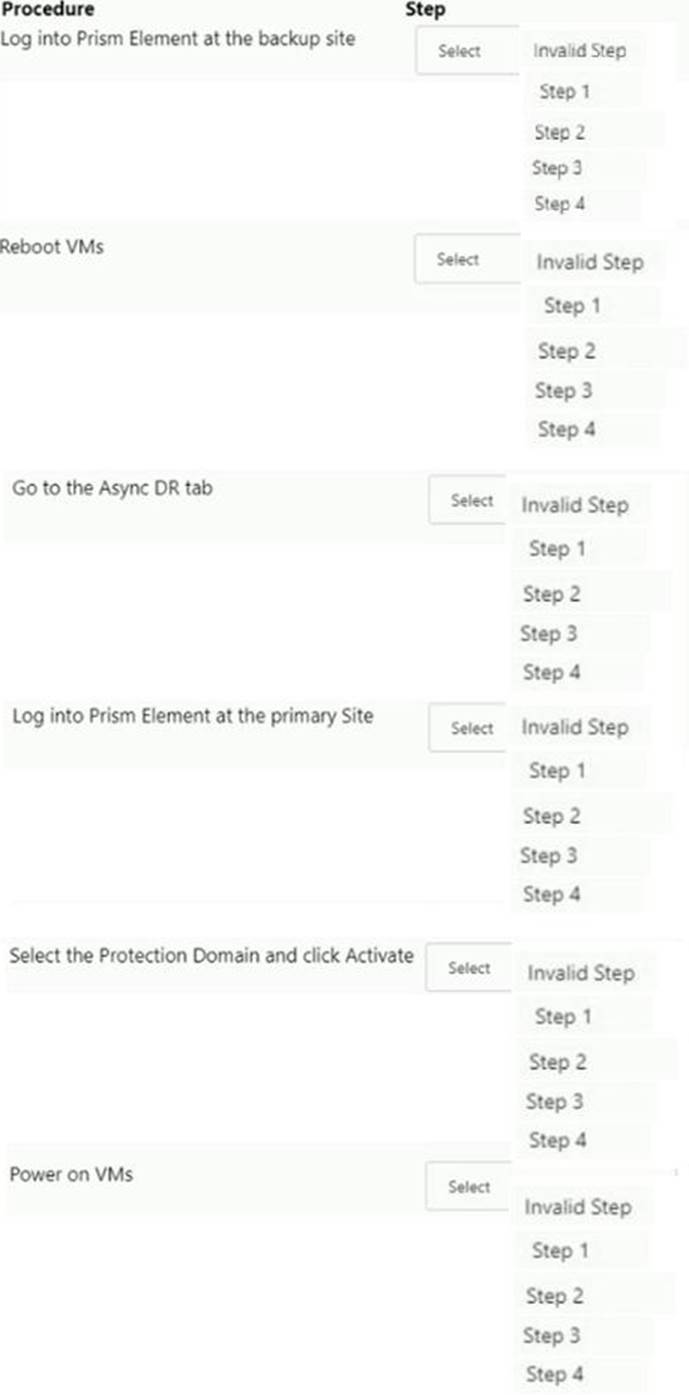
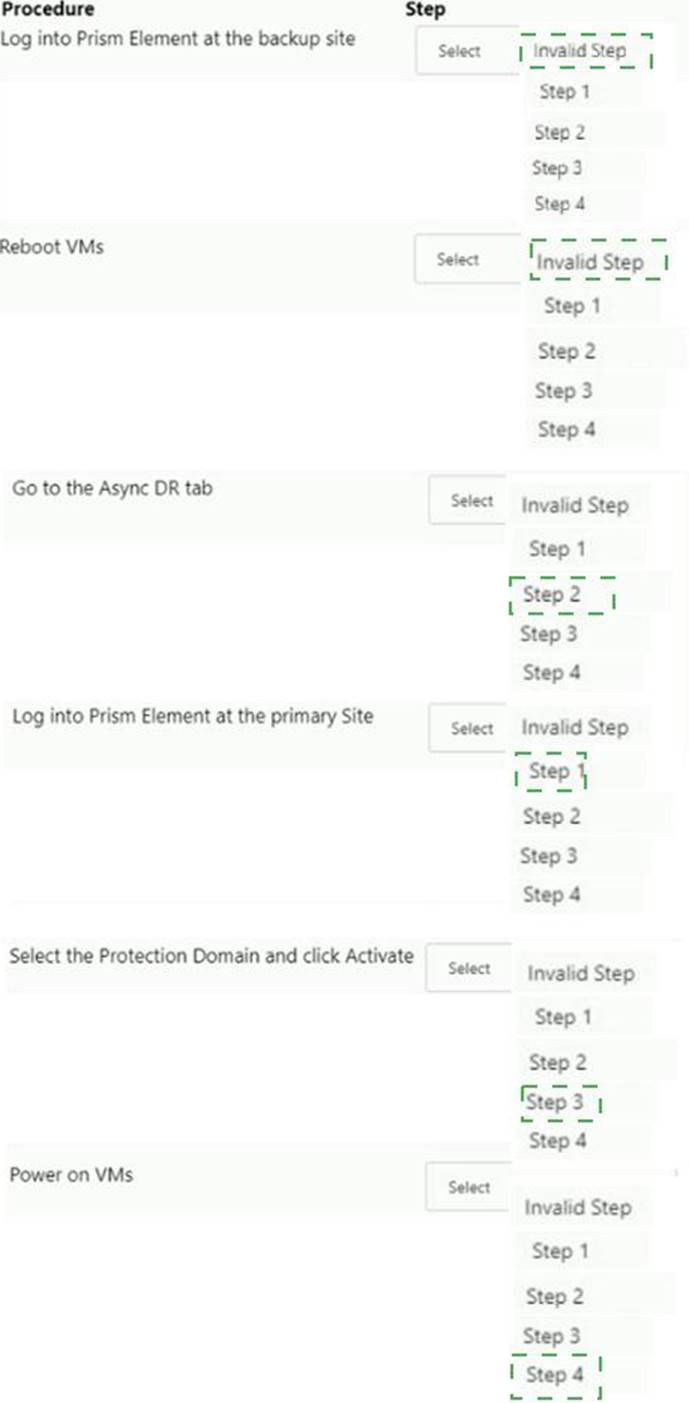
HOTSPOT
Async DR is configured between two sites. A network outage occurs at the primary site.
Which steps must the administrator perform to bring the VMs back into service at the backup site?
Item instructions: For each procedure, indicate the order in which that procedure must take place to meet the item requirements. Not all procedures are valid. Identify any invalid procedures using the drop-down option.
What is the function of the virbr0 bridge on AHV?
- A . To carry all traffic between the user VMs and the upstream network.
- B . To carry management and storage communication between user VMs and the CVM.
- C . To carry management and storage communication between user VMs and AHV host.
- D . To carry storage communication between the guest VMs and the CVM
C
Explanation: http://www.vstellar.com/2019/01/10/ahv-networking-part-1-basics/#:~:text=AHV%20Network%20Architecture&text=virbr0%20is%20an%20internal%2 0switch, virbr0) %20have%20IP%20address%20192.168.
The Linux administration team has requested access rights to any current or future Linux VM in the environment
What entity should be selected when assigning this new role?
- A . Image
- B . AHV Cluster
- C . Category
- D . Project
A cluster has RF2. The cluster loses two drives on different nodes in the same storage tier.
What is the effect on the replicas of the VMs?
- A . Some VM data may be lost
- B . No VMs lose data if the node has two or more SSDs
- C . Some VMs may reboot and gain access to data
- D . No VMs lose data because of RF2
A
Explanation:
Reference: https://next.nutanix.com/how-it-works-22/disk-fault-tollerance-8822
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)
![]()
B)
![]()
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Latest NCP-MCI-5.15 Dumps Valid Version with 280 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

