An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835. The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC:
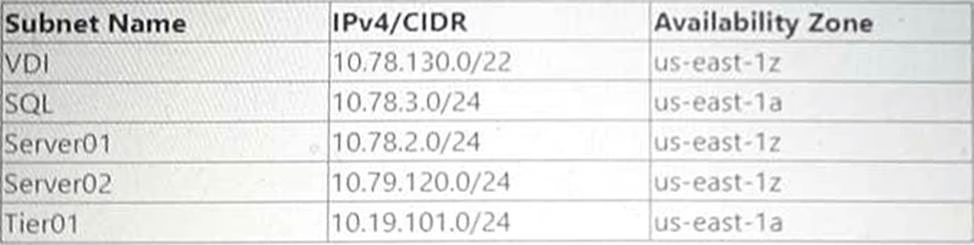
The following tags have been applied to a Custom Network Security Group:
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network.
Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment"? (Choose two.)
- A . Server01
- B . Tier01
- C . SQL
- D . VDl
AB
Explanation:
To determine which subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment, we need to look at the configured subnets and their CIDR ranges, as well as the custom network security group’s inbound rules.
Available CIDR ranges in VPC:
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835. The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC:
The following tags have been applied to a Custom Network Security Group:
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network.
Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment"? (Choose two.)
- A . Server01
- B . Tier01
- C . SQL
- D . VDl
AB
Explanation:
To determine which subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment, we need to look at the configured subnets and their CIDR ranges, as well as the custom network security group’s inbound rules.
Available CIDR ranges in VPC:
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835. The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC:
The following tags have been applied to a Custom Network Security Group:
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network.
Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment"? (Choose two.)
- A . Server01
- B . Tier01
- C . SQL
- D . VDl
AB
Explanation:
To determine which subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment, we need to look at the configured subnets and their CIDR ranges, as well as the custom network security group’s inbound rules.
Available CIDR ranges in VPC:
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835. The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
• 70.73.0.0/16
• 10.79.107.0/24
• 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC:
The following tags have been applied to a Custom Network Security Group:
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network.
Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment"? (Choose two.)
- A . Server01
- B . Tier01
- C . SQL
- D . VDl
AB
Explanation:
To determine which subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment, we need to look at the configured subnets and their CIDR ranges, as well as the custom network security group’s inbound rules.
Available CIDR ranges in VPC:
preparing the landing zone networking resources for a Nutanix cluster on AWS. The administrator has created a VPC with two private subnets: one for cluster management and one for user VMs.
What additional subnet must the administrator create?
- A . Public subnet for S3 access
- B . Public subnet for Internet access
- C . Private subnet for VPN gateway
- D . Private subnet for Prism Central
B
Explanation:
When setting up a landing zone for Nutanix clusters on AWS, having only private subnets for cluster management and user VMs is not sufficient for full cluster functionality. Nutanix clusters often need to communicate with the internet for updates, patches, and other cloud services. VPC Configuration:
The VPC already has two private subnets (one for cluster management and one for user VMs).
Additional Requirements:
To access public services like S3 or for the cluster nodes to reach Nutanix services for updates, a public subnet is essential.
Why Public Subnet for Internet Access?:
A public subnet allows resources within it to communicate directly with the internet, which is necessary for accessing Nutanix’s update servers, applying patches, and other maintenance tasks.
This subnet typically includes an internet gateway, enabling instances in the public subnet to receive and send traffic directly to the internet.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
AWS Networking Best Practices
Nutanix Networking and Subnet Configuration Guidelines
An organization wants to control network traffic at the individual User VM (UVM) subnet level.
Which action will help achieve this goal?
- A . Create a custom security group.
- B . Modify the default UVM security group.
- C . Modify the user management security group.
- D . Modify the internal management security group.
A
Explanation:
To control network traffic at the individual User VM (UVM) subnet level, creating a custom security group is the appropriate action. This approach allows for fine-grained control over inbound and outbound traffic rules that can be applied to specific subnets or individual instances within those subnets.
Custom Security Group:
Custom security groups enable administrators to define specific traffic rules tailored to the needs of individual subnets or VMs. This includes specifying allowed IP ranges, ports, and protocols.
By applying these custom security groups to the UVMs, the organization can control access and enhance security according to their policies and requirements. Steps to Create a Custom Security Group:
Navigate to the AWS Management Console and go to the VPC service.
Select "Security Groups" under the "Security" section.
Click on "Create Security Group" and define the name, description, and VPC. Add inbound and outbound rules according to the desired traffic control policies. Attach the custom security group to the UVMs or subnets in question.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Security Groups
When configuring an alert email in Prism Central deployed within an NC2 environment, what is required in order for the emails to be sent properly?
- A . SMTP server configured in Prism Central settings
- B . Cluster Super Admin permissions
- C . Name servers configured in Prism Central
- D . A whitelisted public cloud console endpoint
A
Explanation:
To ensure that alert emails are sent properly from Prism Central within an NC2 environment, configuring an SMTP server in the Prism Central settings is required. The SMTP server facilitates the sending of email notifications for alerts and other communications.
SMTP Configuration:
Prism Central requires an SMTP server to send email alerts. This involves specifying the SMTP server address, port, and authentication details if needed.
The configuration must include the email address from which the alerts will be sent and the recipient addresses.
Steps to Configure SMTP Server in Prism Central:
Log in to Prism Central.
Navigate to the "Settings" menu.
Select "Email Server" under the "Alerts" section.
Enter the SMTP server details, including the server address, port, and authentication credentials.
Test the configuration to ensure emails are sent correctly.
Reference: Nutanix Prism Central Administration Guide
Nutanix Support Documentation on Email Alert Configuration Best Practices for Configuring SMTP Servers in Cloud Environments
An administrator has deployed an NC2 on AWS cluster and doesn’t have connectivity back to the on-premises environment yet. The administrator wants to SSH into a CVM to edit a security setting and has deployed a Jump Host into an existing public subnet.
What action must the administrator still take to gain access to the CVM?
- A . Edit the CVM iptables to allow SSH.
- B . Edit the User Management Network Security Group to allow SSH from the Jump Host IP.
- C . Edit the UVM security group to allow SSH from the Jump Host IP and remove Cluster Lockdown.
- D . Create Custom Network Security Group at the subnet level and add the IP address of the Jump Host
B
Explanation:
To SSH into a Controller VM (CVM) in an NC2 on AWS cluster without on-premises connectivity, the administrator needs to ensure that the security settings allow SSH access from the Jump Host. This involves editing the User Management Network Security Group to permit SSH traffic from the Jump Host IP.
Deploy Jump Host:
Ensure the Jump Host is deployed in a public subnet with an Elastic IP (EIP) assigned for external access.
Edit User Management Network Security Group:
Locate the security group associated with the user management network.
Modify the inbound rules to allow SSH (port 22) from the Jump Host’s IP address. This ensures that the Jump Host can establish an SSH connection to the CVM.
Steps to Edit Security Group:
Navigate to the EC2 dashboard in the AWS Management Console.
Select "Security Groups" under the "Network & Security" section.
Find and select the appropriate security group.
Edit the inbound rules to add a new rule:
Type: SSH
Protocol: TCP
Port Range: 22
Source: Custom IP (enter the Jump Host’s public IP address)
Additional Configuration:
Ensure that the CVM itself allows SSH connections and that no internal firewall rules block the traffic.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Secure Access
Which service enables the monitoring of key metrics on various AWS services, inducing EC2, EBS, and VPC for an NC2 cluster deployments?
- A . Amazon CloudWatch
- B . AWS CloudTrail
- C . AWS CloudFormation
- D . Amazon inspector
A
Explanation:
Amazon CloudWatch is the service that enables the monitoring of key metrics on various AWS services, including EC2, EBS, and VPC, for NC2 cluster deployments.
Amazon CloudWatch:
Amazon CloudWatch provides monitoring for AWS cloud resources and applications. It collects and tracks metrics, collects and monitors log files, and sets alarms.
Specifically, for NC2 deployments, CloudWatch can be used to monitor key metrics such as CPU utilization, disk I/O, network I/O for EC2 instances, EBS volume performance, and VPC network traffic.
Features:
Metrics Monitoring: Collects and visualizes operational data in the form of metrics, including utilization, performance, and health.
Logs Monitoring: Collects log data, monitors it in real-time, and triggers alarms based on predefined thresholds.
Alarms: Notifies when operational performance thresholds are breached.
Integration with NC2:
By setting up CloudWatch, administrators can ensure they have visibility into the performance and health of their Nutanix clusters on AWS, aiding in proactive management and troubleshooting.
Reference: Amazon CloudWatch Documentation
Nutanix Cloud Clusters on AWS Administration Guide
AWS Monitoring Best Practices
An administrator needs the permissions to create and manage multiple organizations and clusters in NC2, as well as manage user access for the entire company.
What role should be assigned to meet the minimum requirements of this task?
- A . Organization Administrator
- B . Customer Administrator
- C . Customer Security Administrator
- D . Cluster Administrator
B
Explanation:
The role of "Customer Administrator" in Nutanix Cloud Integration with AWS (NC2) is designed to meet the requirements of creating and managing multiple organizations and clusters, as well as managing user access for the entire company.
Roles and Permissions:
Customer Administrator: This role has the broadest set of permissions, allowing the user to create and manage organizations, clusters, and user access across the entire company. It encompasses administrative control over multiple aspects of the NC2 environment.
Capabilities:
Organization Management: Ability to create and manage multiple organizations.
Cluster Management: Full control over creating, configuring, and managing clusters.
User Access Management: Manage user roles and permissions, ensuring that the right individuals
have access to the necessary resources.
Why Not Other Roles:
Organization Administrator: Limited to managing organizations but not clusters and user access at the company level.
Customer Security Administrator: Focuses on security aspects, lacking broader administrative capabilities.
Cluster Administrator: Limited to managing clusters without the ability to manage organizations and user access comprehensively.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Role-Based Access Control Documentation
An administrator needs to create user VM subnets for multiple NC2 clusters in AWS.
What would be the best approach to take?
- A . Create guest-VM VNets for each cluster.
- B . Use the cluster management subnet dedicated to each cluster.
- C . Create guest-VM subnets to be shared by all clusters.
- D . Create guest-VM subnets for each cluster.
D
Explanation:
When creating user VM subnets for multiple NC2 clusters in AWS, the best approach is to create guest-VM subnets for each cluster. This ensures that each cluster has its own dedicated subnets, which simplifies network management and avoids potential IP conflicts. Advantages of Dedicated Subnets:
Isolation: Each cluster operates in its own subnet, providing better isolation and security. Management: Easier to manage and troubleshoot network issues when each cluster has its own subnets.
Scalability: More scalable as each subnet can be managed and expanded independently.
Steps to Create Guest-VM Subnets:
Identify the IP range for each subnet.
In the AWS VPC console, create a new subnet for each cluster using the identified IP ranges. Associate the new subnets with the respective clusters during or after the cluster deployment process.
Why Not Shared Subnets:
Shared subnets could lead to IP conflicts and make network management more complex, especially as the number of clusters grows.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
AWS VPC Subnet Creation Documentation
An administrator has been tasked with deploying an NC2 cluster on AWS with the requirement to protect workloads.
Which two options are valid to protect the workloads on this cluster? (Choose two.)
- A . Deploy one-node cluster in another availability zone.
- B . Create a second NCZ cluster in a different availability zone.
- C . Use an existing on-prem Nutanix cluster as a disaster recovery target.
- D . Deploy a cluster across two availability zones.
B
Explanation:
To protect workloads on an NC2 cluster on AWS, deploying strategies that ensure high availability and disaster recovery are essential.
The two valid options are:
Create a Second NC2 Cluster in a Different Availability Zone:
High Availability: Deploying a second NC2 cluster in a different availability zone ensures that workloads can be quickly recovered in case of an availability zone failure.
Disaster Recovery: This setup enables asynchronous replication between clusters, providing a robust disaster recovery solution.
Use an Existing On-Prem Nutanix Cluster as a Disaster Recovery Target:
Hybrid DR: Leveraging an existing on-premises Nutanix cluster for disaster recovery provides a cost-effective and efficient DR solution.
Replication: Set up replication policies to ensure data is consistently copied from the NC2 cluster on AWS to the on-premises cluster.
Why Not Other Options:
One-node cluster in another availability zone: Not a valid DR solution as a single-node cluster cannot provide the required resilience and high availability.
Deploy a cluster across two availability zones: While this can enhance availability, it is not a typical approach for Nutanix clusters which are designed to operate within a single availability zone for simplicity and performance reasons.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Disaster Recovery Best Practices
AWS Availability Zones and Disaster Recovery Documentation
Exhibit.
An administrator is attempting, but failing to create an NC2 cluster in AWS.
The administrator checks the configuration in the NC and notices the configuration shown in the exhibit.
What action should the administrator take to resolve the issue?
- A . Recreate the AWS CloudFormation stack.
- B . Create a new cloud account in the organization.
- C . Restart Genesis on a Prism Central instance.
- D . Grant the administrator’s account access to the NC2 organization.
B
Explanation:
The exhibit shows two cloud accounts, one for Azure and one for AWS, with their statuses indicated.
The AWS cloud account status is marked as "U" (which likely stands for "Unavailable" or "Unreachable"). This indicates that the AWS cloud account configuration is not properly connected or accessible.
Status Check:
The AWS cloud account is marked with an "U" status, meaning it is not active or accessible.
This status prevents the creation of an NC2 cluster because the necessary cloud resources cannot be allocated or managed without a proper connection.
Action:
The best course of action is to create a new cloud account in the organization. This involves setting up the cloud account details correctly and ensuring it is properly configured to communicate with Nutanix and AWS.
Steps to Create a New Cloud Account:
Log in to the Nutanix console.
Navigate to the "Organizations" section.
Select "Add Cloud Account" and provide the required AWS credentials and permissions.
Ensure the new cloud account is active and correctly configured.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for Cloud Account Management
An administrator has been tasked with ensuring NC2 VMs are able to access AWS resources. The NC2 VM traffic must not traverse the internet.
in which two ways would the administrator achieve this? (Choose two.)
- A . By using a Gateway Endpoint
- B . By using a NAT Gateway.
- C . By using an Interface Endpoint
- D . By using a VPC Peer.
CD
Explanation:
To ensure that NC2 VMs can access AWS resources without traversing the internet, the administrator can use AWS VPC Peering and Interface Endpoints. Both methods ensure that traffic stays within the AWS network, maintaining security and efficiency.
Interface Endpoint:
Interface Endpoints allow you to privately connect your VPC to supported AWS services. They use AWS PrivateLink to route traffic directly to services within the AWS network, bypassing the public internet.
Steps:
Create an interface endpoint for the required service in the AWS VPC console.
Ensure the security groups and route tables are configured to allow traffic to the interface endpoint.
VPC Peering:
VPC Peering allows the routing of traffic between VPCs using private IP addresses, without the need for internet gateways, NAT devices, or VPN connections.
Steps:
Create a VPC peering connection between the VPCs.
Update the route tables to direct traffic between the peered VPCs. Ensure security group rules allow the necessary traffic between VPCs.
Reference: AWS VPC Peering Documentation
AWS Interface Endpoint Documentation
Nutanix Cloud Clusters on AWS Administration Guide
During the recovery of entities protected by Cluster Project, an administrator discovers that the recovery plan is not executing correctly because it exceeds the number of supported entities.
How many entities can be recovered using a Single recovery plan?
- A . 100
- B . 200
- C . 300
- D . 400
C
Explanation:
The Nutanix disaster recovery capabilities include recovery plans that define how entities are recovered in the event of a failure. There is a limit to the number of entities that can be managed within a single recovery plan.
Entity Limit:
According to Nutanix documentation, the maximum number of entities that can be recovered using a single recovery plan is 300. Exceeding this limit will cause issues during the execution of the recovery plan.
Impact of Exceeding the Limit:
If the number of entities in a recovery plan exceeds the supported limit, the recovery process may fail or not execute correctly, as observed in the scenario.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Disaster Recovery Best Practices Documentation
An administrator needs to allow wide open access to one particular NC2 AWS cluster from an on-premises subnet of 10.19.160.0/24.
What is the proper Custom Security Group formatting to satisfy this task?
A)
B)
C)
D)
- A . Option A
- B . Option B
- C . Option C
- D . Option D
B
Explanation:
To allow wide open access to a particular NC2 AWS cluster from an on-premises subnet (10.19.160.0/24), the proper Custom Security Group formatting needs to include the necessary tags that specify the external cluster UUID and the networks allowed.
Custom Security Group Configuration:
The configuration should include tags to identify the cluster and the networks that should be granted access.
Key: nutanix:clusters
Key: nutanix:clusters:external
Value: <cluster-uuid>
Explanation of Choice:
Option B includes the necessary tags and values, ensuring that the specific cluster UUID is recognized and the on-premises subnet (10.19.160.0/24) can communicate with the NC2 cluster.
Security Group Tags:
nutanix:clusters:external – Identifies the cluster as external.
nutanix:clusters:external:cluster-uuid – Specifies the unique identifier for the cluster, enabling proper traffic routing and access.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Custom Security Group Configuration
Which interface must be used to deploy NC2?
- A . Cloud Provider portal
- B . NC2 Tile within the my.nutanix.com portal
- C . Prism Central Dashboard
- D . Foundation running in a Cloud Virtual Machine
B
Explanation:
The NC2 Tile within the my.nutanix.com portal is the correct interface to deploy NC2. This portal provides an integrated and user-friendly interface specifically designed for deploying and managing Nutanix Clusters on AWS.
NC2 Deployment Interface:
NC2 Tile within the my.nutanix.com portal: This portal provides the necessary tools and options to deploy and manage NC2 clusters. It includes functionalities for setting up the clusters, configuring network settings, and managing resources.
Advantages:
User-Friendly Interface: Simplifies the deployment process with a guided setup.
Integrated Tools: Provides access to all necessary tools for managing the deployment and monitoring of NC2 clusters.
Reference: Nutanix Cloud Clusters on AWS Administration Guide
Nutanix my.nutanix.com Portal Documentation
Nutanix Best Practices for Cluster Deployment
Which entity should be contacted for AOS software supported related to NC2?
- A . Internal IT Operations team
- B . Nutanix
- C . Partner
- D . Public Cloud Vendor
B
Explanation:
For AOS software support related to NC2, the appropriate entity to contact is Nutanix. Nutanix provides comprehensive support for their software, including the Acropolis Operating System (AOS) used in NC2 deployments.
Support Scope:
Nutanix offers support for the deployment, configuration, and management of NC2 clusters, including any issues related to AOS software.
This includes troubleshooting, updates, and technical assistance.
Why Not Other Options:
Internal IT Operations team: Typically handles internal issues but does not have the specialized knowledge or resources for AOS software support.
Partner: May provide support but would ultimately escalate issues to Nutanix for software-specific concerns.
Public Cloud Vendor: Manages infrastructure-related issues but does not provide support for Nutanix AOS software.
Reference: Nutanix Support Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for AOS Support
A company has purchased Nutanix AOS Pro licensing.
Which add-on products are available with this license tier in the AWS cluster deployment wizard?
- A . EUC
- B . Nus
- C . Self-Service and Cost Governance
- D . Files, Advanced Replication, and DARE
D
Explanation:
With the Nutanix AOS Pro licensing, several advanced features and add-on products become available. Specifically, in the AWS cluster deployment wizard, the following add-ons are available:
Files:
Nutanix Files provides a software-defined, scale-out file storage solution that simplifies the management and scaling of unstructured data.
Advanced Replication:
Advanced Replication features in Nutanix include synchronous and asynchronous replication capabilities, allowing for robust disaster recovery and data protection solutions.
DARE (Data-At-Rest Encryption):
DARE ensures that all data stored on Nutanix clusters is encrypted, providing a higher level of security for sensitive information.
These features are included in the AOS Pro licensing tier, offering enhanced data management,
protection, and security capabilities.
Reference: Nutanix Licensing Guide
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for Advanced Features
An administrator is planning a new NC2 on AWS deployment. The workload VMs to be deployed on the new cluster have low storage and memory, but high CPU frequency (>3.0 GHz) requirements. The administrate! has also been tasked with ensuring that the cluster nodes have the lowest number of CPU cores to reduce application licensing requirements.
Which node type will satisfy this new deployment?
- A . i3.metal
- B . zld.metal
- C . i4i.metal
- D . m5d.metal
A
Explanation:
For a new NC2 on AWS deployment where workload VMs have low storage and memory requirements but high CPU frequency (>3.0 GHz) requirements, and the goal is to minimize the number of CPU cores to reduce application licensing costs, the i3.metal instance type is the most suitable.
i3.metal:
High CPU Frequency: i3.metal instances offer high-frequency Intel Xeon processors (up to 3.1 GHz) which meet the high CPU frequency requirement.
Low Storage and Memory: These instances come with a balanced amount of storage and memory, suitable for workloads with low requirements in these areas.
Minimized CPU Cores: i3.metal instances have fewer CPU cores compared to other high-frequency instances like i4i.metal, making them ideal for minimizing application licensing costs.
Other Instance Types:
z1d.metal: While also offering high CPU frequency, these instances typically come with a higher core count and more memory, which may not be optimal for minimizing licensing costs. i4i.metal: Designed for I/O intensive applications with higher core counts.
m5d.metal: Balanced instance type but with more cores and not as high CPU frequency as required.
Reference: AWS EC2 Instance Types Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for Instance Selection
Exhibit.
What does the exhibit indicate?
- A . No ongoing replication
- B . Ongoing replication
- C . Replication in paused state
- D . Replication in error state
A
Explanation:
The exhibit indicates a replication operation with specific details about the protection domain, remote site, and snapshot.
Key points to note are:
Bytes Completed: 0 bytes completed.
Complete Percent: 0.0%
Paused: false
Aborted: false
Given these details:
No ongoing replication: The operation has started, but there is no progress in terms of bytes completed or percentage completed. Since the status shows 0 bytes and 0 percent completed, it indicates that no data has been replicated yet.
Reference: Nutanix Protection Domain and Replication Documentation Nutanix Best Practices for Monitoring Replication
An administrator is tasked with adding an AWS account to the NC2 console. A requirement is to configure an AWS IAM user with the appropriate permissions.
Which permission must be assigned to the user?
- A . lAMFullAccess
- B . lAMReadOnlyAccess
- C . AmazonEC2ReadOnlyAccess
- D . AmazonEC2FullAccess
D
Explanation:
To add an AWS account to the NC2 console, an AWS IAM user needs to be configured with the appropriate permissions to manage the EC2 resources. The required permission for the IAM user includes full access to manage EC2 instances, volumes, and related resources.
AmazonEC2FullAccess:
This permission grants full access to all EC2 resources, including the ability to create, modify, and delete instances, volumes, security groups, and more.
Essential for NC2 operations to manage the lifecycle of EC2 instances and associated components within the AWS environment.
Why Not Other Permissions:
IAMFullAccess: Grants full access to IAM resources but not specifically needed for EC2 operations. IAMReadOnlyAccess: Only provides read access to IAM resources, insufficient for managing EC2 instances.
AmazonEC2ReadOnlyAccess: Provides read-only access to EC2 resources, insufficient for creating or modifying instances and other resources.
Reference: AWS IAM Policies Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for IAM User Permissions
An administrator has created an NC2 cluster on AWS, but the NC2 console has issued this alert:
Which two scenarios could have resulted in the cluster creation failure? (Choose two.)
- A . Bad Terraform (TF) state in provisioning
- B . Insufficient permissions
- C . No available AWS credits
- D . AWS Quota exceeded/instance limit exceeded
BD
Explanation:
The error message in the image indicates that the cluster creation failed due to reaching the maximum retries for provisioning cluster nodes.
Here are two possible scenarios that could lead to this issue:
Insufficient Permissions (Answer B):
If the AWS user or role used to create the cluster does not have sufficient permissions, it can result in failures during the provisioning process. Proper IAM policies must be attached to ensure that the necessary actions can be performed, such as launching instances, creating VPCs, or managing networking components.
AWS Quota Exceeded/Instance Limit Exceeded (Answer D):
AWS imposes quotas and limits on the number of instances and other resources that can be created within an account. If these quotas are exceeded, new instances cannot be provisioned, causing the cluster creation to fail. This can be resolved by requesting a quota increase from AWS.
Reference: Nutanix Knowledge Base Article 9774
AWS Service Quotas
Nutanix NC2 on AWS Documentation
An administrator has deployed an NC2 cluster on AWS to an existing environment for VDI. Afterwards, the corporate security teams direct the administrator to reuse an existing AWS subnet, 10.79.4.0/24 that has two EC2 instances: EC2-1 (10.79.4.200) and EC2-2 (10.79.4.201). The security team indicates that this directive is to avoid overlap with the AHV IPAM.
Which two configuration actions should the administrator take to ensure there are no configuration issues? (Choose two.)
- A . aCLI > net.add_to_ip_bfacklist 10.79.4.200 aCLI > net.add_to_ip_blacklist 10.79.4.201
- B . Deploy two VMs on the NC2 cluster and assign 10.79.4.200 and 10.79.4.201 as the assigned IPs in Prism Element
- C . aCLI > net.de/ete_from_ip_blacklist 10.79.4.200 aCLI > net.defete_fromjp_blacklist 10.79.4.201
- D . Configure the AHV JPAM to use DHCP range 10.79.4.2 -10.79.4.253.
AD
Explanation:
To avoid IP address conflicts and ensure there are no configuration issues when reusing an existing AWS subnet, the administrator should take the following actions:
aCLI > net.add_to_ip_blacklist 10.79.4.200 aCLI > net.add_to_ip_blacklist 10.79.4.201 (Answer A): This command adds the specified IP addresses to the blacklist, preventing AHV IPAM from assigning these addresses to any VMs. This ensures that the existing EC2 instances with IPs 10.79.4.200 and 10.79.4.201 are not allocated to other VMs in the NC2 cluster.
Configure the AHV IPAM to use DHCP range 10.79.4.2 -10.79.4.253 (Answer D):
By configuring the AHV IPAM to use a specific DHCP range, you ensure that the IP addresses assigned to the EC2 instances (10.79.4.200 and 10.79.4.201) are not included in the DHCP pool. This prevents IP address conflicts within the subnet.
Reference: Nutanix aCLI Reference
Nutanix NC2 on AWS Documentation
AWS VPC and Subnet Basics
Which two statements are the most accurate regarding Cluster Protect? (Choose two.)
- A . An AWS subnet can be shared by VMs, Prism Central, and Multicloud Snapshort Technology (MST).
- B . Nutanix Guest Tools (NGT) is not required to be installed on User VMs.
- C . The dusters that are to be protected must be registered with the same instance of Prism Central.
- D . The Cluster Protect feature requires AOS version 6.7 or higher.
CD
Explanation:
The clusters that are to be protected must be registered with the same instance of Prism Central (Answer C):
For Cluster Protect to function correctly, all clusters intended for protection must be registered under the same Prism Central instance. This ensures consistent management and coordination of protection policies and operations across clusters.
The Cluster Protect feature requires AOS version 6.7 or higher (Answer D):
Cluster Protect is a feature that is available starting from AOS version 6.7. To utilize this feature, ensure that the Nutanix clusters are running this version or a newer one.
Reference: Nutanix Cluster Protection Documentation
Nutanix AOS Release Notes
Exhibit.
What action is taken against the Condemned node shown in the exhibit?
- A . The node has a power reset sent to it.
- B . The node is restarted.
- C . The node is powered off.
- D . The node Is automatically replaced.
A
Explanation:
When a node is marked as "Condemned," it indicates that the system has determined that the node is no longer reliable for operations.
As part of the automated recovery and protection process, the following action is typically taken:
The node has a power reset sent to it (Answer A):
In most cases, a condemned node undergoes a power reset as an initial recovery attempt. This action attempts to reboot the node to bring it back to a healthy state. If the reset fails, further manual or
automated steps may be required to address the hardware or software issue.
Reference: Nutanix Cluster Management Documentation
Nutanix Support Knowledge Base
An administrator is tasked with providing VMs outbound internet connectivity in AWS.
Which components would the administrator need to create in the VPC to achieve this?
- A . Public Subnet NAT Gateway, Public EIP, Route Table
- B . Private Subnet NAT Gateway, Public EIP, Route Table
- C . Private Subnet Flow Gateway, Public EIP, Route Table
- D . Public Subnet Flow Gateway, Public EIP, Route Table
B
Explanation:
To provide VMs with outbound internet connectivity in AWS using a private subnet, the administrator needs to create the following components in the VPC:
Private Subnet: A private subnet is required to house the VMs that need outbound internet access but do not require direct inbound access from the internet.
NAT Gateway: A NAT (Network Address Translation) Gateway is necessary to allow instances in the private subnet to connect to the internet or other AWS services while preventing the internet from initiating a connection with those instances.
Public EIP (Elastic IP Address): An EIP is associated with the NAT Gateway to provide a persistent
public IP address that allows outbound internet traffic from the private subnet to be routed correctly.
Route Table: A route table is configured to route traffic from the private subnet to the NAT Gateway
for outbound internet access.
Reference: AWS NAT Gateway Documentation
AWS VPC Subnet Basics
An administrator needs to backup Prism Central configuration data to an Amazon S3 bucket.
Which pcdr-cli command parameters is needed to satisfy this task?
- A . deployment-info
- B . protect
- C . list-protection-targets
- D . recover
B
Explanation:
To backup Prism Central configuration data to an Amazon S3 bucket, the pcdr-cli command with the protect parameter is used. This parameter is specifically designed for creating protection policies and backing up Prism Central data.
Reference: Nutanix Prism Central Documentation
Nutanix pcdr-cli Command Reference