Network Appliance NS0-527 NetApp Certified Implementation Engineer, Data Protection Online Training
Network Appliance NS0-527 Online Training
The questions for NS0-527 were last updated at Feb 25,2026.
- Exam Code: NS0-527
- Exam Name: NetApp Certified Implementation Engineer, Data Protection
- Certification Provider: Network Appliance
- Latest update: Feb 25,2026
Click the Exhibit button.
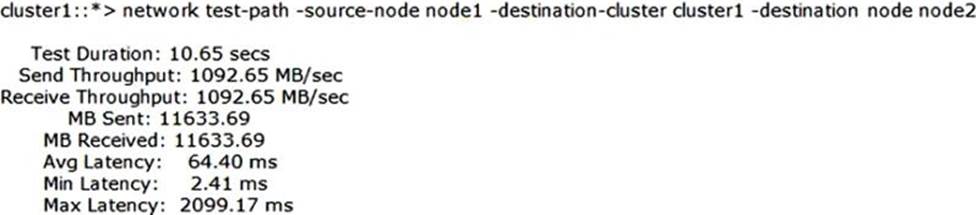
You need to verify that you have a 10 Gb path between two clusters for SnapMirror traffic. Referring to the exhibit, how fast is the network path between the clusters?
- A . 10 Mb
- B . 100 Mb
- C . 1 Gb
- D . 10 Gb
C
Explanation:
Reference: https://docs.netapp.com/ontap-9/topic/com.netapp.doc.dot-cm-nmg/Network%20and%20LIF%20management.pdf
Which two NetApp products reduce the backup time and create a consistent backup for a primary Oracle target? (Choose two.)
- A . SnapMirror for Open Systems
- B . Open Systems SnapVault
- C . SnapManager for Orade
- D . SnapProtect
Which two NetApp technologies allow for synchronous replication of data between two remote sites? (Choose two.)
- A . SyncMirror
- B . SnapVault
- C . Metro Cluster
- D . SnapMirror
A customer has ONTAP 9.5 clusters running at two nearby locations. The customer wants a zero RPO for one mission-critical volume.
In thisscenario, which two NetApp solutions satisfy this requirement while using the existing ONTAP clusters? (Choose two.)
- A . SnapMirror Synchronous in StrictSync mode
- B . FabricPool
- C . SnapMirror Synchronous in Sync mode
- D . SyncMirror
An ONTAP administrator is trying to configure a three-way-disaster recovery solution. Cluster 2 is within 50 km of Cluster 1, the primarycluster, with an RTT of 7 ms. Cluster 3 is over 300 km from Cluster 1 with an RTT of 29 ms.
In this scenario, what are two topologies that would accomplish this task? (Choose two.)
- A . a cascade topology from Cluster 1 to Cluster 2 with SnapMirror Synchronous, and then SnapMirror asynchronous from Cluster 2 to Cluster 3
- B . a fan out topology with SnapMirror Synchronous from Cluster 1 to Cluster 2 and SnapMirror Synchronous to Cluster 3
- C . a fan out topology with SnapMirror Synchronous from Cluster 1 to Cluster 2 and SnapMirror asynchronous from Cluster 1 to Cluster 3
- D . a cascade topology from Cluster 1 to Cluster 2 with SnapMirror Synchronous, and then SnapMirror Synchronous from Cluster 2 to Cluster 3
Click the Exhibit button.
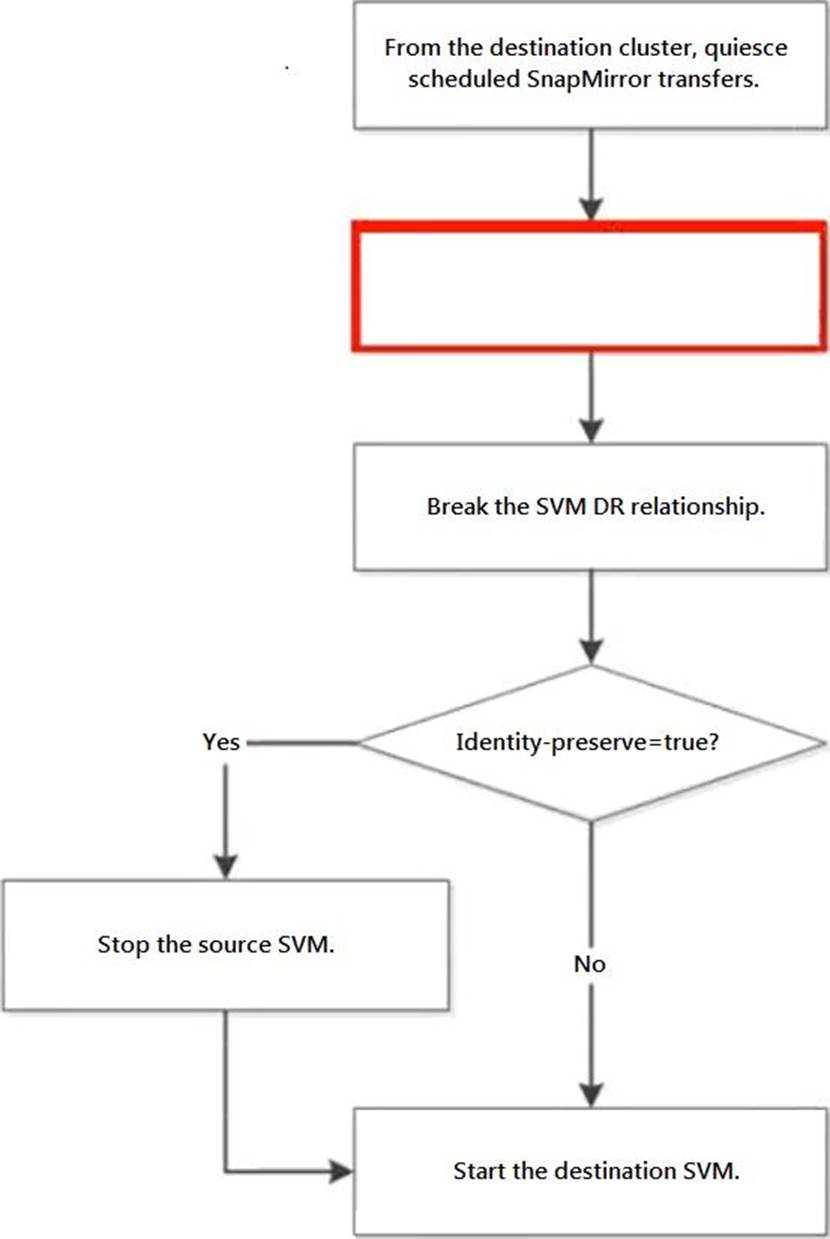
In an ONTAP environment, an SVM-DR relationship exists between your AFF A220 cluster and your FAS2720 cluster, with identity preserve enabled. You are asked to test thedisaster recovery workflow in an upcoming maintenance window.
Referring to the exhibit, which step should be performed next to test the recovery workflow?
- A . Delete the SVM-DR relationship.
- B . Pause any ongoing transfers.
- C . Abort any ongoing transfers.
- D . Update any ongoing transfers.
Which two statements are correct about configuring a peering connection between clusters? (Choose two.)
- A . The LIFs should be on the same subnet.
- B . You must use at least one intercluster LIF per node.
- C . You must use one cluster LIF per node per network.
- D . The intercluster LIFs must have full connectivity to each other.
B,D
Explanation:
Reference: https://docs.netapp.com/ontap-9/index.jsp?topic=%2Fcom.netapp.doc.pow-csp%2FGUID-0F81B700-7B79-456F-9C89-3A7D6451AEB6.html
You noticed that your SnapVault relationship is healthy but that the destination volume does not have any Snapshot copies.
In this scenario, what should be performed to solve the problem?
- A . Set up volume destination free space.
- B . Set up volume source free space.
- C . Use the snapvault update command.
- D . Configure a rule with the Snapshot label.
A customer wants a new solution that reaches a near-zero recovery time objective (RTO) and a zero recovery point objective (RPO).
In thisscenario, which NetApp solution satisfies the requirements?
- A . NDMP
- B . MetroCluster
- C . SnapMirror
- D . SnapVault
C
Explanation:
Reference: https://blog.netapp.com/effective-disaster-recovery-solution
Click the Exhibit button.
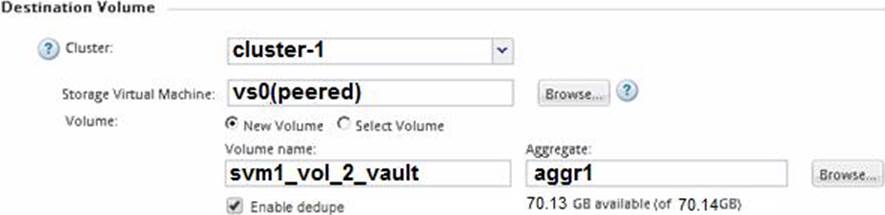
An employee’s computer and mapped home folder has been encrypted with ransomware.
You are asked to restore the data from a SnapVault repository.
Referring to the exhibit, what happens when the volume is restored?
- A . All files in the volume are restored.
- B . The restore is performed locally.
- C . The original data is decrypted in place.
- D . Only files that have changed in the volume are restored.
Latest NS0-527 Dumps Valid Version with 212 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

