Netskope NSK300 Netskope Certified Cloud Security Architect Exam Online Training
Netskope NSK300 Online Training
The questions for NSK300 were last updated at Apr 24,2025.
- Exam Code: NSK300
- Exam Name: Netskope Certified Cloud Security Architect Exam
- Certification Provider: Netskope
- Latest update: Apr 24,2025
You are asked to create a customized restricted administrator role in your Netskope tenant for a newly hired employee.
Which two statements are correct in this scenario? (Choose two.)
- A . An admin role prevents admins from downloading and viewing file content by default.
- B . The scope of the data shown in the Ul can be restricted to specific events.
- C . All role privileges default to Read Only for all functional areas.
- D . Obfuscation can be applied to all functional areas.
You are deploying the Netskope Client to Windows devices.
The following command line would be used to install the client MSI file:
![]()
In this scenario, what is <token> referring to in the command line?
- A . a Netskope user identifier
- B . the Netskope organization ID
- C . the URL of the IdP used to authenticate the users
- D . a private token given to you by the SCCM administrator
Given the following:
![]()
Which result does this Skope IT query provide?
- A . The query returns all events of [email protected] downloading or uploading to or from the site ‘Amazon S3" using the Netskope Client.
- B . The query returns all events of an IP address downloading or uploading to or from Amazon S3 using the Netskope Client.
- C . The query returns all events of everyone except [email protected] downloading or uploading to or from the site "Amazon S3" using the Netskope Client.
- D . The query returns all events of [email protected] downloading or uploading to or from the application "Amazon S3" using the Netskope Client.
You want customers to configure Real-time Protection policies.
In which order should the policies be placed in this scenario?
- A . Threat, CASB, RBI, Web
- B . RBI, CASB, Web, Threat
- C . Threat, RBI, CASB, Web
- D . CASB, RBI, Threat, Web
A company has deployed Explicit Proxy over Tunnel (EPoT) for their VDI users They have configured Forward Proxy authentication using Okta Universal Directory They have also configured a number of Real-time Protection policies that block access to different Web categories for different AD groups so.
for example, marketing users are blocked from accessing gambling sites. During User Acceptance Testing, they see inconsistent results where sometimes marketing users are able to access gambling sites and sometimes they are blocked as expected They are seeing this inconsistency based on who logs into the VDI server first.
What is causing this behavior?
- A . Forward Proxy is not configured to use the Cookie Surrogate
- B . Forward Proxy is not configured to use the IP Surrogate
- C . Forward Proxy authentication is configured but not enabled.
- D . Forward Proxy is configured to use the Cookie Surrogate
Review the exhibit.
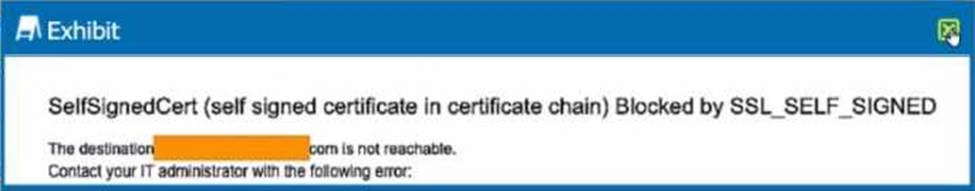
You are the proxy administrator for a medical devices company. You recently changed a pilot group of users from cloud app steering to all Web traffic. Pilot group users have started to report that they receive the error shown in the exhibit when attempting to access the company intranet site that is publicly available. During troubleshooting, you realize that this site uses your company’s internal certificate authority for SSL certificates.
Which three statements describe ways to solve this issue? (Choose three.)
- A . Import the root certificate for your internal certificate authority into Netskope.
- B . Bypass SSL inspection for the affected site(s).
- C . Create a Real-time Protection policy to allow access.
- D . Change the SSL Error Settings from Block to Bypass in the Netskope tenant.
- E . Instruct the user to proceed past the error message
Review the exhibit.
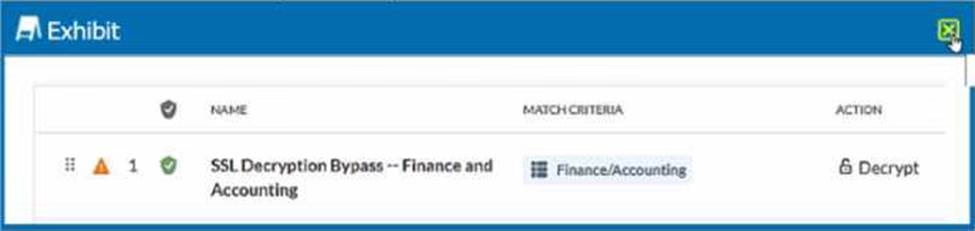
You created an SSL decryption policy to bypass the inspection of financial and accounting Web categories. However, you still see banking websites being inspected.
What are two possible causes of this behavior? (Choose two.)
- A . The policy is in a "disabled" state.
- B . An incorrect category has been selected
- C . The policy is in a "pending changes" state.
- D . An incorrect action has been specified.
You deployed the Netskope Client for Web steering in a large enterprise with dynamic steering. The steering configuration includes a bypass rule for an application that is IP restricted.
What is the source IP for traffic to this application when the user is on-premises at the enterprise?
- A . Loopback IPv4
- B . Netskope data plane gateway IPv4
- C . Enterprise Egress IPv4
- D . DHCP assigned RFC1918 IPv4
You do not want a scheduled Advanced Analytics dashboard to be automatically updated when Netskope makes improvements to that dashboard.
In this scenario, what would you do to retain the original dashboard?
- A . Create a new dashboard from scratch that mimics the Netskope dashboard you want to use.
- B . Copy the dashboard into your Group or Personal folders and schedule from these folders.
- C . Ask Netskope Support to provide the dashboard and import into your Personal folder.
- D . Download the dashboard you want and Import from File into your Group or Personal folder.
You have multiple networking clients running on an endpoint and client connectivity is a concern.
You are configuring co-existence with a VPN solution in this scenario, what is recommended to prevent potential routing issues?
- A . Configure the VPN to split tunnel traffic by adding the Netskope IP and Google DNS ranges and set to Exclude in the VPN configuration.
- B . Modify the VPN to operate in full tunnel mode at Layer 3. so that the Netskope agent will always see the traffic first.
- C . Configure the VPN to full tunnel traffic and add an SSL Do Not Decrypt policy to the VPN
configuration for all Netskope traffic. - D . Configure a Network Location with the VPN IP ranges and add it as a Steering Configuration exception.
Latest NSK300 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

