Netskope NSK200 Netskope Certified Cloud Security Integrator (NCCSI) Online Training
Netskope NSK200 Online Training
The questions for NSK200 were last updated at Apr 09,2025.
- Exam Code: NSK200
- Exam Name: Netskope Certified Cloud Security Integrator (NCCSI)
- Certification Provider: Netskope
- Latest update: Apr 09,2025
Recently your company implemented Zoom for collaboration purposes and you are attempting to inspect the traffic with Netskope. Your initial attempt reveals that you are not seeing traffic from the Zoom client that is used by all users. You must ensure that this traffic is visible to Netskope.
In this scenario, which two steps must be completed to satisfy this requirement? (Choose two.)
- A . Create a steering exception for Zoom to ensure traffic is reaching Netskope.
- B . Create a Do Not Decrypt SSL policy for the Zoom application suite.
- C . Remove the Zoom certificate-pinned application from the default steering configuration.
- D . Remove the default steering exception for the Web Conferencing Category.
Which statement describes how Netskope’s REST API, v1 and v2, handles authentication?
- A . Both REST API v1 and v2 require the use of tokens to make calls to the API
- B . Neither REST API v1 nor v2 require the use of tokens.
- C . REST API v2 requires the use of a token to make calls to the API. while API vl does not.
- D . REST API v1 requires the use of a token to make calls to the API. while API v2 does not.
You are provisioning Netskope users from Okta with SCIM Provisioning, and users are not showing up in the tenant.
In this scenario, which two Netskope components should you verify first In Okta for accuracy? (Choose two.)
- A . IdP Entity ID
- B . OAuth token
- C . Netskope SAML certificate
- D . SCIM server URL
You are given an MD5 hash of a file suspected to be malware by your security incident response team. They ask you to offer insight into who has encountered this file and from where was the threat initiated.
In which two Skope IT events tables would you search to find the answers to these questions? (Choose two.)
- A . Application Events
- B . Network Events
- C . Alerts
- D . Page Events
A city uses many types of forms, including permit applications. These forms contain personal and financial information of citizens. Remote employees download these forms and work directly with the citizens to complete them. The city wants to be able to identify and monitor the specific forms and block the employees from downloading completed forms.
Which feature would you use to accomplish this task?
- A . exact data match (EDM)
- B . regular expressions (regex)
- C . document fingerprinting
- D . optical character recognition (OCR)
Review the exhibit.
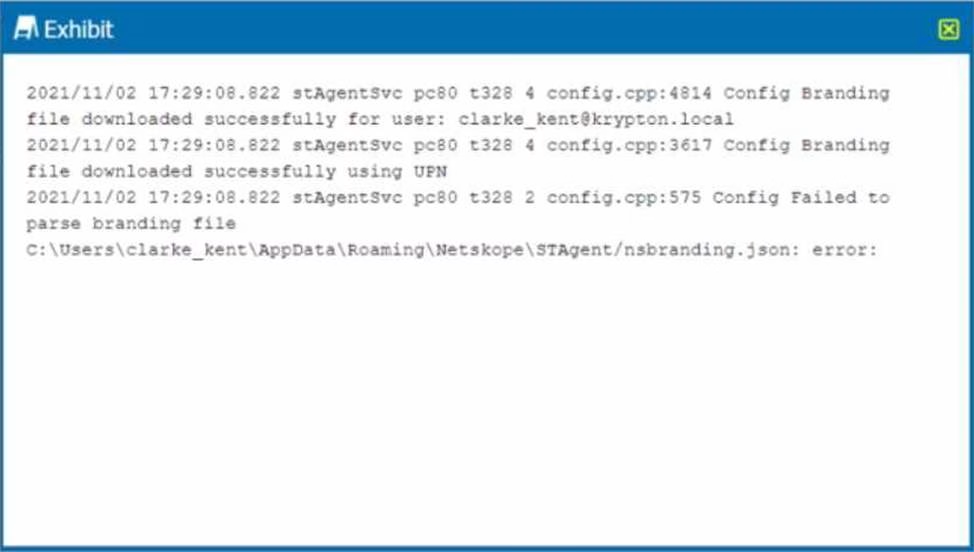
You receive a service request from a user who indicates that their Netskope client is in a disabled state. The exhibit shows an excerpt (rom the affected client nsdebuglog.log.
What is the problem in this scenario?
- A . User authentication failed during IdP-based enrollment.
- B . The Netskope client connection is being decrypted.
- C . Custom installation parameters are incorrectly specified
- D . The user’s account has not been provisioned into Netskope.
Your customer is migrating all of their applications over to Microsoft 365 and Azure. They have good practices and policies in place (or their inline traffic, but they want to continuously detect reconfigurations and enforce compliance standards.
Which two solutions would satisfy their requirements? (Choose two.)
- A . Netskope SaaS Security Posture Management
- B . Netskope Cloud Confidence Index
- C . Netskope Risk Insights
- D . Netskope Continuous Security Assessment
You are an administrator writing Netskope Real-time Protection policies and must determine proper policy ordering.
Which two statements are true in this scenario? (Choose two.)
- A . You must place Netskope private access malware policies in the middle.
- B . You do not need to create an "allow all" Web Access policy at the bottom.
- C . You must place DLP policies at the bottom.
- D . You must place high-risk block policies at the top.
What are three methods to deploy a Netskope client? (Choose three.)
- A . Deploy Netskope client using SCCM.
- B . Deploy Netskope client using REST API v2.
- C . Deploy Netskope client using email invite.
- D . Deploy Netskope client using REST API v1.
- E . Deploy Netskope client using IdP.
Netskope is being used as a secure Web gateway. Your organization’s URL list changes frequently.
In this scenario, what makes It possible for a mass update of the URL list in the Netskope platform?
- A . REST API v2
- B . Assertion Consumer Service URL
- C . Cloud Threat Exchange
- D . SCIM provisioning
Latest NSK200 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

