Netskope NSK200 Netskope Certified Cloud Security Integrator (NCCSI) Online Training
Netskope NSK200 Online Training
The questions for NSK200 were last updated at Dec 17,2025.
- Exam Code: NSK200
- Exam Name: Netskope Certified Cloud Security Integrator (NCCSI)
- Certification Provider: Netskope
- Latest update: Dec 17,2025
Review the exhibit.
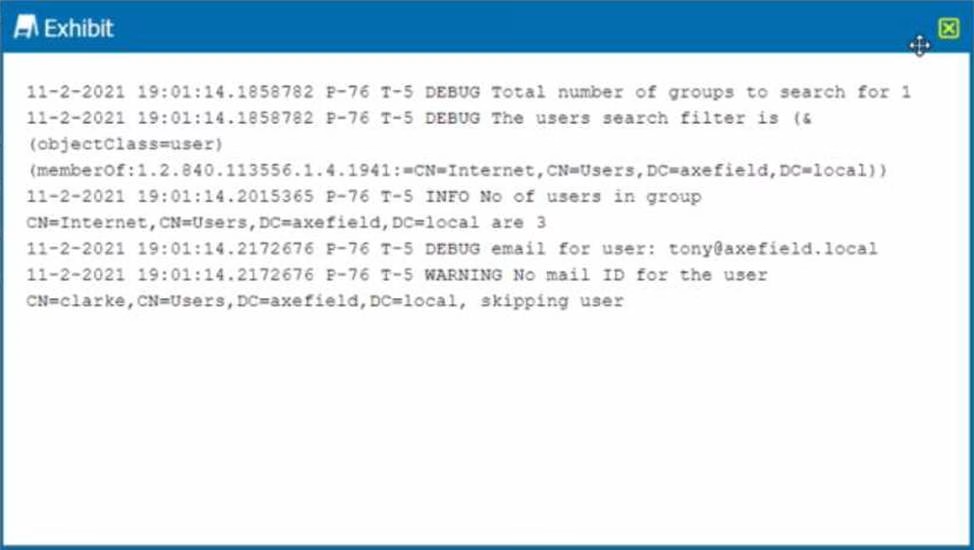
You are troubleshooting a Netskope client for user Clarke which remains in a disabled state after being installed. After looking at various logs, you notice something which might explain the problem. The exhibit is an excerpt from the nsADImporterLog.log.
Referring to the exhibit, what is the problem?
- A . The client was not Installed with administrative privileges.
- B . The Active Directory user is not synchronized to the Netskope tenant.
- C . This is normal; it might take up to an hour to be enabled.
- D . The client traffic is decrypted by a network security device.
You are having issues with fetching user and group Information periodically from the domain controller and posting that information to your tenant instance in the Netskope cloud.
To begin the troubleshooting process, what would you Investigate first in this situation?
- A . On-Premises Log Parser
- B . Directory Importer
- C . DNS Connector
- D . AD Connector
You are troubleshooting an issue with Microsoft where some users complain about an issue accessing OneDrive and SharePoint Online. The configuration has the Netskope client deployed and active for most users, but some Linux machines are routed to Netskope using GRE tunnels. You need to disable inspection for all users to begin troubleshooting the issue.
In this scenario, how would you accomplish this task?
- A . Create a Real-time Protection policy to isolate Microsoft 365.
- B . Create a Do Not Decrypt SSL policy for the Microsoft 365 App Suite.
- C . Create a steering exception for the Microsoft 365 domains.
- D . Create a Do Not Decrypt SSL policy for OneDrive.
Your company has many users that are remote and travel often. You want to provide the greatest visibility into their activities, even while traveling. Using Netskope. which deployment method would be used in this scenario?
- A . Use proxy chaining.
- B . Use a Netskope client.
- C . Use an IPsec tunnel.
- D . Use a GRE tunnel.
Your company has Microsoft Azure ADFS set up as the Identity Provider (idP). You need to deploy the Netskope client to all company users on Windows laptops without user intervention.
In this scenario, which two deployment options would you use? (Choose two.)
- A . Deploy the Netskope client with SCCM.
- B . Deploy the Netskope client with Microsoft GPO.
- C . Deploy the Netskope client using IdP.
- D . Deploy the Netskope client using an email Invitation.
What is the purpose of the file hash list in Netskope?
- A . It configures blocklist and allowlist entries referenced in the custom Malware Detection profiles.
- B . It is used to allow and block URLs.
- C . It provides the file types that Netskope can inspect.
- D . It provides Client Threat Exploit Prevention (CTEP).
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected.
In this scenario, how would you accomplish this task?
- A . Create a Do Not Decrypt Policy using User Group and Domain in the policy page.
- B . Create a Do Not Decrypt Policy using Application in the policy page and a Steering Exception for Group
- C . Create a Do Not Decrypt Policy using Destination IP and Application in the policy page.
- D . Create a Do Not Decrypt Policy using Source IP and Application in the policy page.
Your organization has a homegrown cloud application. You are required to monitor the activities that users perform on this cloud application such as logins, views, and downloaded files. Unfortunately, it seems Netskope is unable to detect these activities by default.
How would you accomplish this goal?
- A . Enable access to the application with Netskope Private Access.
- B . Ensure that the cloud application is added as a steering exception.
- C . Ensure that the application is added to the SSL decryption policy.
- D . Create a new cloud application definition using the Chrome extension.
You are implementing tenant access security and governance controls for privileged users. You want to start with controls that are natively available within the Netskope Cloud Security Platform and do not require external or third-party integration.
Which three access controls would you use in this scenario? (Choose three.)
- A . IP allowlisting to control access based upon source IP addresses.
- B . Login attempts to set the number of failed attempts before the admin user is locked out of the Ul.
- C . Applying predefined or custom roles to limit the admin’s access to only those functions required for their job.
- D . Multi-factor authentication to verify a user’s authenticity.
- E . History-based access control based on past security actions.
You want to prevent a document stored in Google Drive from being shared externally with a public link.
What would you configure in Netskope to satisfy this requirement?
- A . Threat Protection policy
- B . API Data Protection policy
- C . Real-time Protection policy
- D . Quarantine
Latest NSK200 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

