Netskope NSK200 Netskope Certified Cloud Security Integrator (NCCSI) Online Training
Netskope NSK200 Online Training
The questions for NSK200 were last updated at Jan 02,2026.
- Exam Code: NSK200
- Exam Name: Netskope Certified Cloud Security Integrator (NCCSI)
- Certification Provider: Netskope
- Latest update: Jan 02,2026
To which three event types does Netskope’s REST API v2 provide access? (Choose three.)
- A . application
- B . alert
- C . client
- D . infrastructure
- E . user
Review the exhibit.
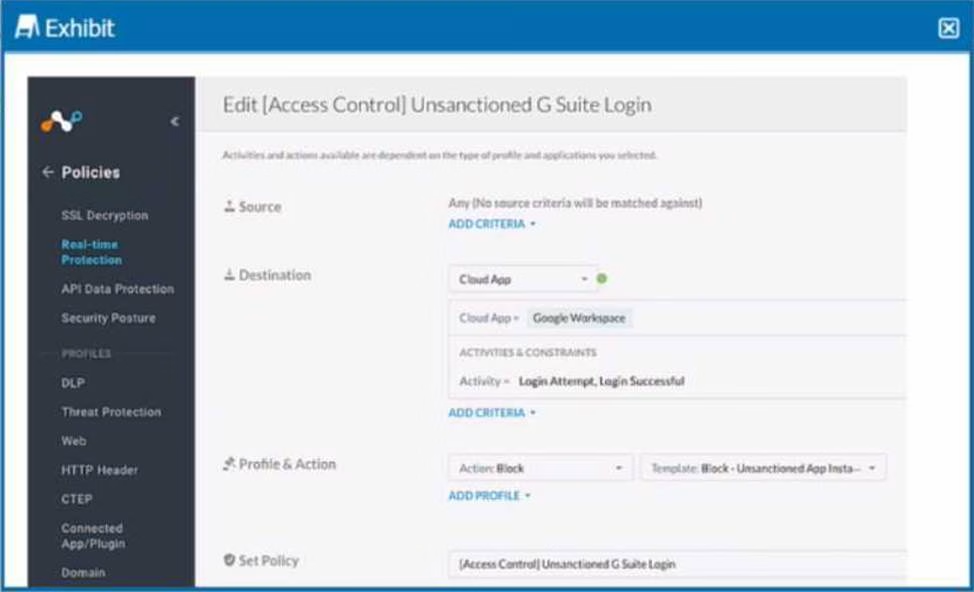
Your company uses Google as the corporate collaboration suite; however, corporate policy restricts the use of personal Google services. The exhibit provides a partially completed policy to ensure that users cannot log into their personal account.
What should be added to achieve the desired outcome in this scenario?
- A . Google Gmail app
- B . User Constraint
- C . DLP profile
- D . Device classification
You have deployed a development Web server on a public hosting service using self-signed SSL certificates. After some troubleshooting, you determined that when the Netskope client is enabled, you are unable to access the Web server over SSL. The default Netskope tenant steering configuration is in place.
In this scenario, which two settings are causing this behavior? (Choose two.)
- A . SSL pinned certificates are blocked.
- B . Untrusted root certificates are blocked.
- C . Incomplete certificate trust chains are blocked.
- D . Self-signed server certificates are blocked.
Your customer currently only allows users to access the corporate instance of OneDrive using SSO with the Netskope client. The users are not permitted to take their laptops when vacationing, but sometimes they must have access to documents on OneDrive when there is an urgent request. The customer wants to allow employees to remotely access OneDrive from unmanaged devices while enforcing DLP controls to prohibit downloading sensitive files to unmanaged devices.
Which steering method would satisfy the requirements for this scenario?
- A . Use a reverse proxy integrated with their SSO.
- B . Use proxy chaining with their cloud service providers integrated with their SSO.
- C . Use a forward proxy integrated with their SSO.
- D . Use a secure forwarder integrated with an on-premises proxy.
An engineering firm is using Netskope DLP to identify and block sensitive documents, including schematics and drawings. Lately, they have identified that when these documents are blocked, certain employees may be taking screenshots and uploading them. They want to block any screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
- A . exact data match (EDM)
- B . document fingerprinting
- C . ML image classifier
- D . optical character recognition (OCR)
Review the exhibit.
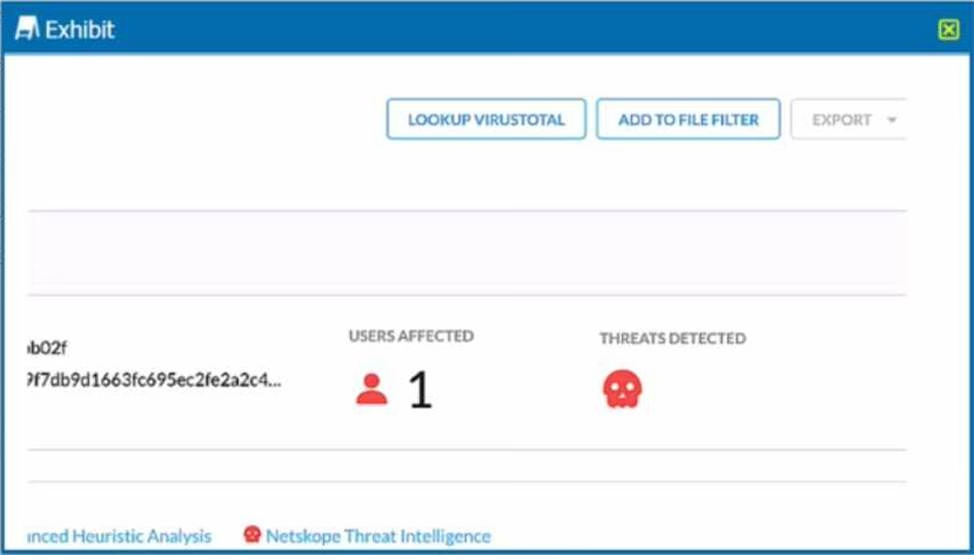
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . Click the "Add To File Filter button to add the IOC to a file list.
- B . Contact the CrowdStrike administrator to have the file marked as safe.
- C . Click the ”Lookup VirusTotal" button to verify if this IOC is a false positive.
- D . Create a malware detection profile and update the file hash list with the IOC.
Which object would be selected when creating a Malware Detection profile?
- A . DLP profile
- B . File profile
- C . Domain profile
- D . User profile
Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents.
In this scenario, which two statements are true? (Choose two.)
- A . The Skope IT Applications tab will list the top five DLP policies.
- B . You can see the top Ave DLP policies triggered using the Analyze feature
- C . You can create a report using Reporting or Advanced Analytics.
- D . The Skope IT Alerts tab will list the top five DLP policies.
You want to secure Microsoft Exchange and Gmail SMTP traffic for DLP using Netskope.
Which statement is true about this scenario when using the Netskope client?
- A . Netskope can inspect outbound SMTP traffic for Microsoft Exchange and Gmail.
- B . Enable Cloud Firewall to Inspect Inbound SMTP traffic for Microsoft Exchange and Gmail.
- C . Netskope can inspect inbound and outbound SMTP traffic for Microsoft Exchange and Gmail.
- D . Enable REST API v2 to Inspect inbound SMTP traffic for Microsoft Exchange and Gmail.
Your company needs to keep quarantined files that have been triggered by a DLP policy.
In this scenario, which statement Is true?
- A . The files are stofed remotely In your data center assigned In the Quarantine profile.
- B . The files are stored In the Netskope data center assigned in the Quarantine profile.
- C . The files are stored In the Cloud provider assigned In the Quarantine profile.
- D . The files are stored on the administrator console PC assigned In the Quarantine profile.
Latest NSK200 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

