Netskope NSK101 Netskope Certified Cloud Security Administrator (NCCSA) Online Training
Netskope NSK101 Online Training
The questions for NSK101 were last updated at Apr 27,2025.
- Exam Code: NSK101
- Exam Name: Netskope Certified Cloud Security Administrator (NCCSA)
- Certification Provider: Netskope
- Latest update: Apr 27,2025
In the Skope IT interface, which two event tables would be used to label a cloud application instance? (Choose two.)
- A . Network Events
- B . Page Events
- C . Application Events
- D . Alerts
Your department is asked to report on GDPR data publicly exposed in Microsoft 365, Salesforce. and Slack-sanctioned cloud applications.
Which deployment model would you use to discover this data?
- A . reverse proxy
- B . on-premises appliance
- C . API-enabled protection
- D . inline protection
Which two technologies form a part of Netskope’s Threat Protection module? (Choose two.)
- A . log parser
- B . DLP
- C . sandbox
- D . heuristics
You just deployed the Netskope client in Web mode and several users mention that their messenger application is no longer working. Although you have a specific real-time policy that allows this application, upon further investigation you discover that it is using proprietary encryption. You need to permit access to all the users and maintain some visibility.
In this scenario, which configuration change would accomplish this task?
- A . Change the real-time policy to block the messenger application.
- B . Create a new custom cloud application using the custom connector that can be used in the real-time policy.
- C . Add a policy in the SSL decryption section to bypass the messenger domain(s).
- D . Edit the steering configuration and add a steering exception for the messenger application.
You consume application infrastructure (middleware) capabilities by a third-party provider.
What is the cloud service model that you are using in this scenario?
- A . PaaS
- B . MaaS
- C . DaaS
- D . SaaS
You are deploying TLS support for real-time Web and SaaS transactions.
What are two secure implementation methods in this scenario? (Choose two.)
- A . Bypass TLS 1.3 because it is not widely adopted.
- B . Downgrade to TLS 1.2 whenever possible.
- C . Support TLS 1.2 only when 1.3 is not supported by the server.
- D . Require TLS 1.3 for every server that accepts it.
What correctly defines the Zero Trust security model?
- A . least privilege access
- B . multi-layered security
- C . strong authentication
- D . double encryption
Exhibit
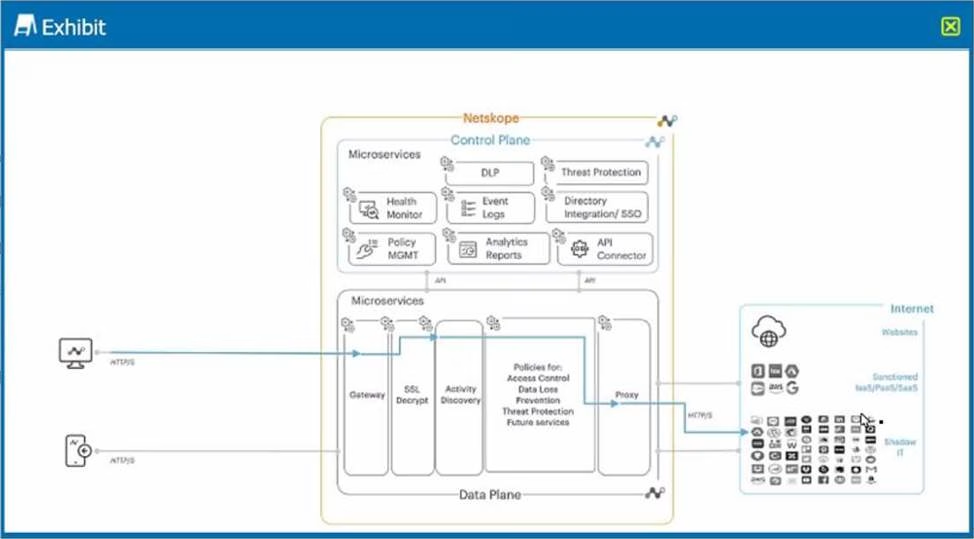
A user is connected to a cloud application through Netskope’s proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
- A . username. device location
- B . destination IP. OS patch version
- C . account instance, URL category
- D . user activity, cloud app risk rating
- E . file version, shared folder
What is a benefit that Netskope instance awareness provides?
- A . It prevents movement of corporate sensitive data to a personal Dropbox account.
- B . It prevents the user from copying information from a corporate email and pasting the information into a GitHub repository.
- C . It differentiates between an IT managed Google Drive instance versus a personal Dropbox account.
- D . It differentiates between an IT managed Google Drive instance versus a personal Google Drive instance.
According to Netskope. what are two preferred methods to report a URL miscategorization? (Choose two.)
- A . Use www.netskope.com/url-lookup.
- B . Use the URL Lookup page in the dashboard.
- C . Email [email protected].
- D . Tag Netskope on Twitter.
Latest NSK101 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

