Mulesoft MCIA-Level 1 MuleSoft Certified Integration Architect – Level 1 Online Training
Mulesoft MCIA-Level 1 Online Training
The questions for MCIA-Level 1 were last updated at Mar 02,2026.
- Exam Code: MCIA-Level 1
- Exam Name: MuleSoft Certified Integration Architect - Level 1
- Certification Provider: Mulesoft
- Latest update: Mar 02,2026
What is a key difference between synchronous and asynchronous logging from Mule applications?
- A . Synchronous logging writes log messages in a single logging thread but does not block the Mule event being processed by the next event processor
- B . Asynchronous logging can improve Mule event processing throughput while also reducing the processing time for each Mule event
- C . Asynchronous logging produces more reliable audit trails with more accurate timestamps
- D . Synchronous logging within an ongoing transaction writes log messages in the same thread that processes the current Mule event
B
Explanation:
Types of logging:
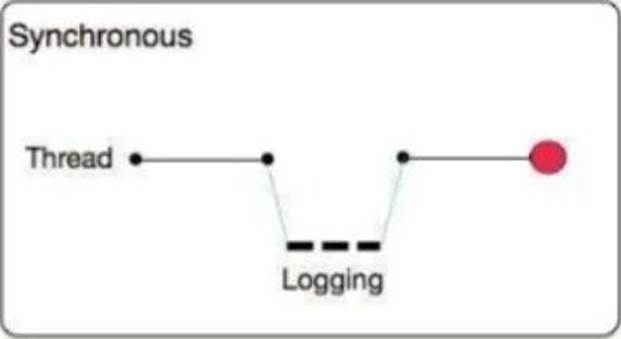
A) Synchronous: The execution of thread that is processing messages is interrupted to wait for the log message to be fully handled before it can continue.
The execution of the thread that is processing your message is interrupted to wait for the log message to be fully output before it can continue
Performance degrades because of synchronous logging
Used when the log is used as an audit trail or when logging ERROR/CRITICAL messages If the logger fails to write to disk, the exception would raise on the same thread that’s currently processing the Mule event. If logging is critical for you, then you can rollback the transaction.
Chart, diagram
Description automatically generated
Chart, diagram,
box and whisker chart
Description automatically generated
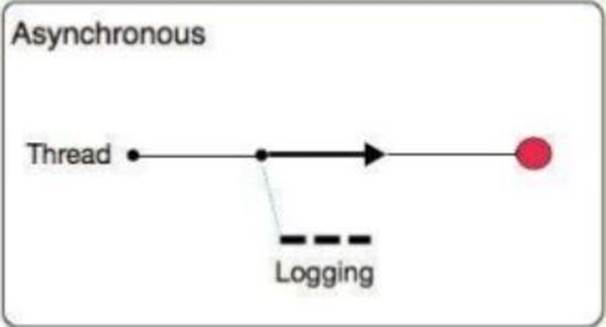
B) Asynchronous:
The logging operation occurs in a separate thread, so the actual processing of your message won’t be delayed to wait for the logging to complete
Substantial improvement in throughput and latency of message processing
Mule runtime engine (Mule) 4 uses Log4j 2 asynchronous logging by default
The disadvantage of asynchronous logging is error handling.
If the logger fails to write to disk, the thread doing the processing won’t be aware of any issues writing to the disk, so you won’t be able to rollback anything. Because the actual writing of the log gets differed, there’s a chance that log messages might never make it to disk and get lost, if Mule were to crash before the buffers are flushed.
——————————————————————————————————————
So Correct answer is: Asynchronous logging can improve Mule event processing throughput while also reducing the processing time for each Mule event
An organization is designing Mule application which connects to a legacy backend. It has been reported that backend services are not highly available and experience downtime quite often.
As an integration architect which of the below approach you would propose to achieve high reliability goals?
- A . Alerts can be configured in Mule runtime so that backend team can be communicated when services are down
- B . Until Successful scope can be implemented while calling backend API’s
- C . On Error Continue scope to be used to call in case of error again
- D . Create a batch job with all requests being sent to backend using that job as per the availability of backend API’s
B
Explanation:
Correct answer is Untill Successful scope can be implemented while calling backend API’s The Until Successful scope repeatedly triggers the scope’s components (including flow references) until they all succeed or until a maximum number of retries is exceeded The scope provides option to control the max number of retries and the interval between retries The scope can execute any sequence of processors that may fail for whatever reason and may succeed upon retry
According to MuleSoft’s IT delivery and operating model, which approach can an organization adopt in order to reduce the frequency of IT project delivery failures?
- A . Decouple central IT projects from the innovation that happens within each line of business
- B . Adopt an enterprise data model
- C . Prevent technology sprawl by reducing production of API assets
- D . Stop scope creep by centralizing requirements-gathering
Which component of Anypoint platform belongs to the platform control plane?
- A . Runtime Fabric
- B . Runtime Replica
- C . Anypoint Connectors
- D . API Manager
When the mule application using VM is deployed to a customer-hosted cluster or multiple cloudhub workers, how are messages consumed by the Mule engine?
- A . in non-deterministic way
- B . by starting an XA transaction for each new message
- C . in a deterministic way
- D . the primary only in order to avoid duplicate processing
Refer to the exhibit.
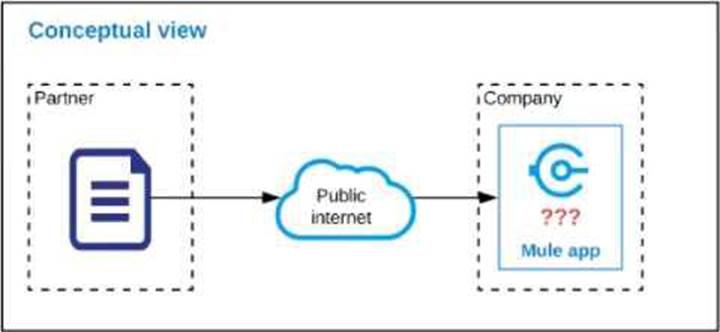
An organization is designing a Mule application to receive data from one external business partner. The two companies currently have no shared IT infrastructure and do not want to establish one. Instead, all communication should be over the public internet (with no VPN).
What Anypoint Connector can be used in the organization’s Mule application to securely receive data from this external business partner?
- A . File connector
- B . VM connector
- C . SFTP connector
- D . Object Store connector
C
Explanation:
* Object Store and VM Store is used for sharing data inter or intra mule applications in same setup. Can’t be used with external Business Partner
* Also File connector will not be useful as the two companies currently have no shared IT infrastructure. It’s specific for local use.
* Correct answer is SFTP connector. The SFTP Connector implements a secure file transport channel so that your Mule application can exchange files with external resources.
SFTP uses the SSH security protocol to transfer messages. You can implement the SFTP endpoint as an inbound endpoint with a one-way exchange pattern, or as an outbound endpoint configured for either a one-way or request-response exchange pattern.
A Mule application is synchronizing customer data between two different database systems.
What is the main benefit of using XA transaction over local transactions to synchronize these two database system?
- A . Reduce latency
- B . Increase throughput
- C . Simplifies communincation
- D . Ensure consistency
D
Explanation:
* XA transaction add tremendous latency so "Reduce Latency" is incorrect option XA transactions define "All or No" commit protocol.
* Each local XA resource manager supports the A.C.I.D properties (Atomicity, Consistency, Isolation, and Durability).
———————————————————————————————————————
So correct choice is "Ensure consistency"
Reference: https://docs.mulesoft.com/mule-runtime/4.3/xa-transactions
A company is planning to migrate its deployment environment from on-premises cluster to a Runtime Fabric (RTF) cluster. It also has a requirement to enable Mule applications deployed to a Mule runtime instance to store and share data across application replicas and restarts.
How can these requirements be met?
- A . Anypoint object store V2 to share data between replicas in the RTF cluster
- B . Install the object store pod on one of the cluster nodes
- C . Configure Persistence Gateway in any of the servers using Mule Object Store
- D . Configure Persistent Gateway at the RTF
A Mule application uses the Database connector.
What condition can the Mule application automatically adjust to or recover from without needing to restart or redeploy the Mule application?
- A . One of the stored procedures being called by the Mule application has been renamed
- B . The database server was unavailable for four hours due to a major outage but is now fully operational again
- C . The credentials for accessing the database have been updated and the previous credentials are no longer valid
- D . The database server has been updated and hence the database driver library/JAR needs a minor version upgrade
B
Explanation:
* Any change in the application will require a restart except when the issue outside the app. For below situations, you would need to redeploy the code after doing necessary changes — One of the stored procedures being called by the Mule application has been renamed. In this case, in the Mule application you will have to do changes to accommodate the new stored procedure name.
— Required redesign of Mule applications to follow microservice architecture principles. As code is changed, deployment is must
— If the credentials changed and you need to update the connector or the properties. — The credentials for accessing the database have been updated and the previous credentials are no longer valid. In this situation you need to restart or redeploy depending on how credentials are configured in Mule application.
* So Correct answer is The database server was unavailable for four hours due to a major outage but is now fully operational again as this is the only external issue to application.
An organization has several APIs that accept JSON data over HTTP POST. The APIs are all publicly available and are associated with several mobile applications and web applications. The organization does NOT want to use any authentication or compliance policies for these APIs, but at the same time, is worried that some bad actor could send payloads that could somehow compromise the applications or servers running the API implementations.
What out-of-the-box Anypoint Platform policy can address exposure to this threat?
- A . Apply a Header injection and removal policy that detects the malicious data before it is used
- B . Apply an IP blacklist policy to all APIs; the blacklist will Include all bad actors
- C . Shut out bad actors by using HTTPS mutual authentication for all API invocations
- D . Apply a JSON threat protection policy to all APIs to detect potential threat vectors
D
Explanation:
We need to note few things about the scenario which will help us in reaching the correct solution.
Point 1: The APIs are all publicly available and are associated with several mobile applications and web applications. This means Apply an IP blacklist policy is not viable option. as blacklisting IPs is limited to partial web traffic. It can’t be useful for traffic from mobile application
Point 2: The organization does NOT want to use any authentication or compliance policies for these APIs. This means we can not apply HTTPS mutual authentication scheme. Header injection or removal will not help the purpose.
By its nature, JSON is vulnerable to JavaScript injection. When you parse the JSON object, the malicious code inflicts its damages. An inordinate increase in the size and depth of the JSON payload can indicate injection. Applying the JSON threat protection policy can limit the size of your JSON payload and thwart recursive additions to the JSON hierarchy. Hence correct answer is Apply a JSON threat protection policy to all APIs to detect potential threat vectors
Latest MCIA-Level 1 Dumps Valid Version with 79 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

