Mulesoft MCIA-Level 1 MuleSoft Certified Integration Architect – Level 1 Online Training
Mulesoft MCIA-Level 1 Online Training
The questions for MCIA-Level 1 were last updated at Feb 28,2026.
- Exam Code: MCIA-Level 1
- Exam Name: MuleSoft Certified Integration Architect - Level 1
- Certification Provider: Mulesoft
- Latest update: Feb 28,2026
An organization is creating a set of new services that are critical for their business. The project team prefers using REST for all services but is willing to use SOAP with common WS-" standards if a particular service requires it.
What requirement would drive the team to use SOAP/WS-* for a particular service?
- A . Must use XML payloads for the service and ensure that it adheres to a specific schema
- B . Must publish and share the service specification (including data formats) with the consumers of the service
- C . Must support message acknowledgement and retry as part of the protocol
- D . Must secure the service, requiring all consumers to submit a valid SAML token
D
Explanation:
Security Assertion Markup Language (SAML) is an open standard that allows identity providers (IdP) to pass authorization credentials to service providers (SP).
SAML transactions use Extensible Markup Language (XML) for standardized communications between the identity provider and service providers.
SAML is the link between the authentication of a user’s identity and the authorization to use a service.
WS-Security is the key extension that supports many authentication models including:
basic username/password credentials, SAML, OAuth and more.
A common way that SOAP API’s are authenticated is via SAML Single Sign On (SSO). SAML works by facilitating the exchange of authentication and authorization credentials across applications. However, there is no specification that describes how to add SAML to REST web services.
Reference: https://www.oasis-open.org/committees/download.php/16768/wss-v1.1-spec-os-SAMLTokenProfile.pdf
An application load balancer routes requests to a RESTful web API secured by Anypoint Flex Gateway.
Which protocol is involved in the communication between the load balancer and the Gateway?
- A . SFTP
- B . HTTPS
- C . LDAP
- D . SMTP
A trading company handles millions of requests a day. Due to nature of its business, it requires excellent performance and reliability within its application.
For this purpose, company uses a number of event-based API’s hosted on various mule clusters that communicate across a shared message queue sitting within its network.
Which method should be used to meet the company’s requirement for its system?
- A . XA transactions and XA connected components
- B . JMS transactions
- C . JMS manual acknowledgements with a reliability pattern
- D . VM queues with reliability pattern
An XA transaction Is being configured that involves a JMS connector listening for Incoming JMS messages.
What is the meaning of the timeout attribute of the XA transaction, and what happens after the timeout expires?
- A . The time that is allowed to pass between committing the transaction and the completion of the Mule flow After the timeout, flow processing triggers an error
- B . The time that Is allowed to pass between receiving JMS messages on the same JMS connection After the timeout, a new JMS connection Is established
- C . The time that Is allowed to pass without the transaction being ended explicitly After the timeout, the transaction Is forcefully rolled-back
- D . The time that Is allowed to pass for state JMS consumer threads to be destroyed After the timeout, a new JMS consumer thread is created
C
Explanation:
* Setting a transaction timeout for the Bitronix transaction manager Set the transaction timeout either
C In wrapper.conf
C In CloudHub in the Properties tab of the Mule application deployment The default is 60 secs. It is defined as
mule.bitronix.transactiontimeout = 120
* This property defines the timeout for each transaction created for this manager.
If the transaction has not terminated before the timeout expires it will be automatically rolled back.
———————————————————————————————————————
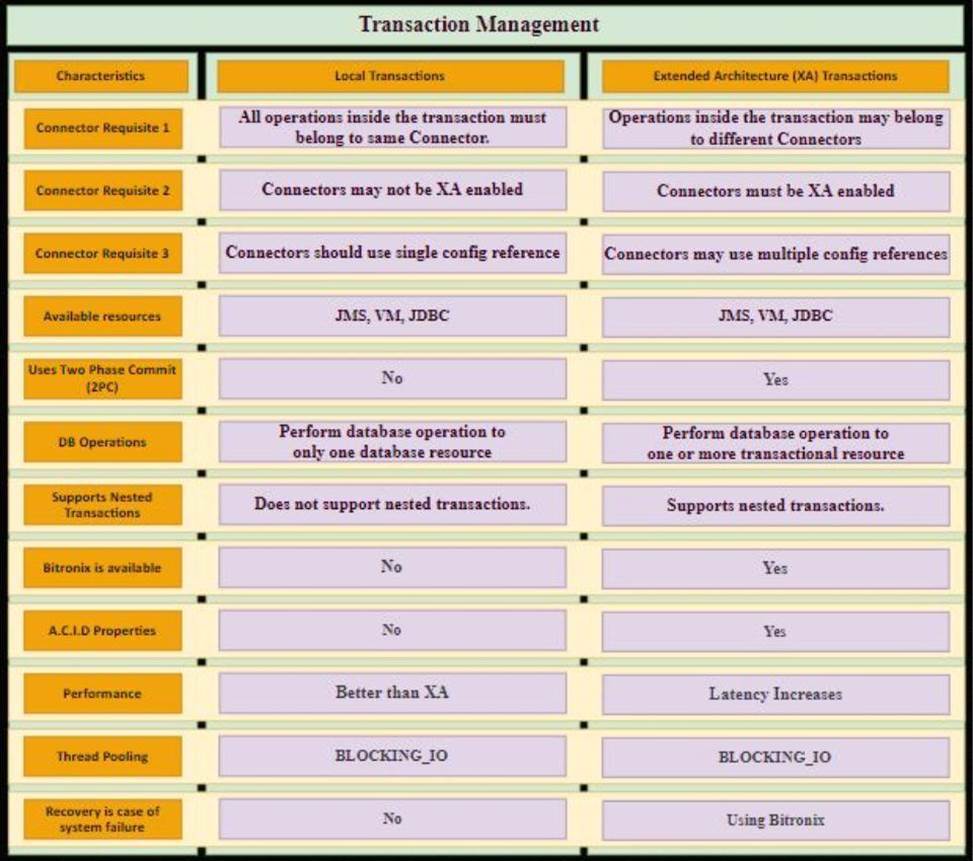
Additional Info around Transaction Management:
Bitronix is available as the XA transaction manager for Mule applications
To use Bitronix, declare it as a global configuration element in the Mule application <bti:transaction-manager />
Each Mule runtime can have only one instance of a Bitronix transaction manager, which is shared by all Mule applications
For customer-hosted deployments, define the XA transaction manager in a Mule domain C Then share this global element among all Mule applications in the Mule runtime
Graphical user interface, table
Description automatically generated with medium confidence
As a part of design, Mule application is required call the Google Maps API to perform a distance computation. The application is deployed to cloudhub.
At the minimum what should be configured in the TLS context of the HTTP request configuration to meet these requirements?
- A . The configuration is built-in and nothing extra is required for the TLS context
- B . Request a private key from Google and create a PKCS12 file with it and add it in keyStore as a part of TLS context
- C . Download the Google public certificate from a browser, generate JKS file from it and add it in key store as a part of TLS context
- D . Download the Google public certificate from a browser, generate a JKS file from it and add it in Truststore as part of the TLS context
An organization has strict unit test requirement that mandate every mule application must have an MUnit test suit with a test case defined for each flow and a minimum test coverage of 80%.
A developer is building Munit test suit for a newly developed mule application that sends API request to an external rest API.
What is the effective approach for successfully executing the Munit tests of this new application while still achieving the required test coverage for the Munit tests?
- A . Invoke the external endpoint of the rest API from the mule floors
- B . Mark the rest API invocations in the Munits and then call the mocking service flow that simulates standard responses from the REST API
- C . Mock the rest API invocation in the Munits and return a mock response for those invocations
- D . Create a mocking service flow to simulate standard responses from the rest API and then configure the mule flows to call the marking service flow
An organization is choosing between API-led connectivity and other integration approaches.
According to MuleSoft, which business benefits is associated with an API-led connectivity approach using Anypoint Platform?
- A . improved security through adoption of monolithic architectures
- B . Increased developer productivity through sell-service of API assets
- C . Greater project predictability through tight coupling of systems
- D . Higher outcome repeatability through centralized development
A stock broking company makes use of CloudHub VPC to deploy Mule applications. Mule application needs to connect to a database application in the customers on-premises corporate data center and also to a Kafka cluster running in AWS VPC.
How is access enabled for the API to connect to the database application and Kafka cluster securely?
- A . Set up a transit gateway to the customers on-premises corporate datacenter to AWS VPC
- B . Setup AnyPoint VPN to the customer’s on-premise corporate data center and VPC peering with AWS VPC
- C . Setup VPC peering with AWS VPC and the customers devices corporate data center
- D . Setup VPC peering with the customers onto my service corporate data center and Anypoint VPN to AWS VPC
What Anypoint Connectors support transactions?
- A . Database, JMS, VM
- B . Database, 3MS, HTTP
- C . Database, JMS, VM, SFTP
- D . Database, VM, File
A
Explanation:
Below Anypoint Connectors support transactions JMS C Publish C Consume VM C Publish C Consume Database C All operations
An integration Mule application is deployed to a customer-hosted multi-node Mule 4 runtime duster. The Mule application uses a Listener operation of a JMS connector to receive incoming messages from a JMS queue.
How are the messages consumed by the Mule application?
- A . Depending on the JMS provider’s configuration, either all messages are consumed by ONLY the primary cluster node or else ALL messages are consumed by ALL cluster nodes
- B . Regardless of the Listener operation configuration, all messages are consumed by ALL cluster nodes
- C . Depending on the Listener operation configuration, either all messages are consumed by ONLY the primary cluster node or else EACH message is consumed by ANY ONE cluster node
- D . Regardless of the Listener operation configuration, all messages are consumed by ONLY the primary cluster node
C
Explanation:
Correct answer is Depending on the Listener operation configuration, either all messages are consumed by ONLY the primary cluster node or else EACH message is consumed by ANY ONE cluster node
For applications running in clusters, you have to keep in mind the concept of primary node and how the connector will behave. When running in a cluster, the JMS listener default behavior will be to receive messages only in the primary node, no matter what kind of destination you are consuming from. In case of consuming messages from a Queue, you’ll want to change this configuration to receive messages in all the nodes of the cluster, not just the primary.
This can be done with the primaryNodeOnly parameter:
<jms:listener config-ref="config" destination="${inputQueue}" primaryNodeOnly="false"/>
Latest MCIA-Level 1 Dumps Valid Version with 79 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

