Mulesoft MCD-Level 2 MuleSoft Certified Developer – Level 2 (Mule 4) Online Training
Mulesoft MCD-Level 2 Online Training
The questions for MCD-Level 2 were last updated at Feb 20,2026.
- Exam Code: MCD-Level 2
- Exam Name: MuleSoft Certified Developer - Level 2 (Mule 4)
- Certification Provider: Mulesoft
- Latest update: Feb 20,2026
Which command is used to convert a JKS keystore to PKCS12?
- A . Keytool-importkeystore Csrckeystore keystore p12-srcstoretype PKCS12 Cdestkeystore keystore.jks Cdeststoretype JKS
- B . Keytool-importkeystore Csrckeystore keystore p12-srcstoretype JKS Cdestkeystore keystore.p12 Cdeststoretype PKCS12
- C . Keytool-importkeystore Csrckeystore keystore jks-srcstoretype JKS Cdestkeystore keystore.p13 Cdeststoretype PKCS12
- D . Keytool-importkeystore Csrckeystore keystore jks-srcstoretype PKCS12 Cdestkeystore keystore.p12 Cdeststoretype JKS
B
Explanation:
To convert a JKS keystore to PKCS12, the developer needs to use the keytool-importkeystore command with the following options: -srckeystore keystore.jks -srcstoretype JKS -destkeystore keystore.p12 -deststoretype
PKCS12. This command imports all entries from a source JKS keystore (keystore.jks) into a destination
PKCS12 keystore (keystore.p12).
References: https://docs.oracle.com/en/java/javase/11/tools/keytool.html#GUID-5990A2E4-78E3-47B7-AE75-6D18262595
When a client and server are exchanging messages during the mTLS handshake, what is being agreed on during the cipher suite exchange?
- A . A protocol
- B . The TLS version
- C . An encryption algorithm
- D . The Public key format
C
Explanation:
A cipher suite is a set of cryptographic algorithms that are used to secure the communication between a client and a server. A cipher suite consists of four components: a key exchange algorithm, an authentication algorithm, an encryption algorithm, and a message authentication code (MAC) algorithm. During the cipher suite exchange, the client and the server agree on which encryption algorithm to use for encrypting and decrypting the data.
References: https://docs.mulesoft.com/mule-runtime/4.3/tls-configuration#cipher-suites
The flow is invoicing a target API. The API’s protocol is HTTPS. The TLS configuration in the HTTP Request Configuration global element is set to None. A web client submits a request to http:localhost:8081/vehicles.
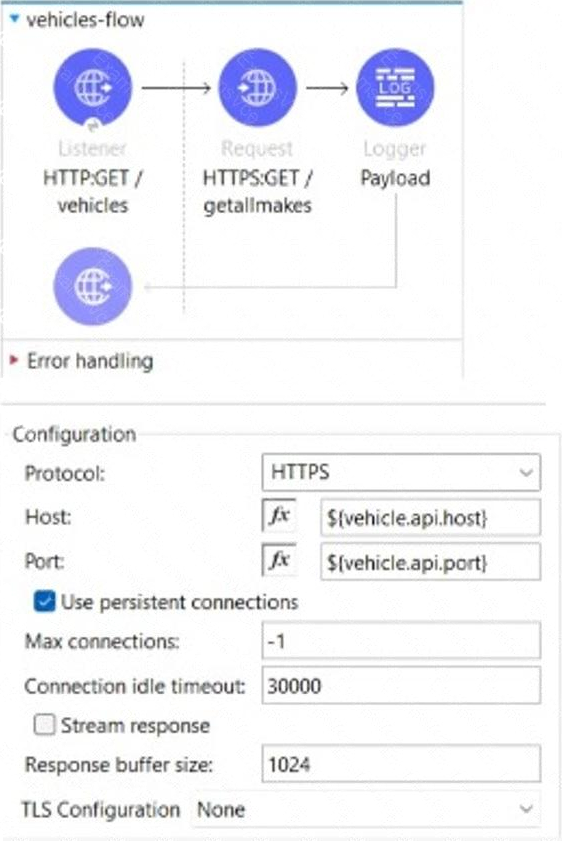
If the certificate of the target API is signed by a certificate authority (CA), what is true about the HTTP Request operation when the flow executes?
- A . The HTTP Request operation will succeed if the CA’S certificate is present in the JRE’s default keystore
- B . The HTTP Request operation will succeed if the CA’s certificate is present in the JRE’s default truststore.
- C . The HTTP Request operation will always succeed regardless of the CA
- D . The HTTP Request operation will always fail regardless of the CA
B
Explanation:
The HTTP Request operation will use the default truststore of the JRE to validate the certificate of the target API. If the CA’s certificate is present in the truststore, the operation will succeed. Otherwise, it will fail with a handshake exception.
References: https://docs.mulesoft.com/mule-runtime/4.3/tls-configuration#tls-default
Refer to the exhibit.
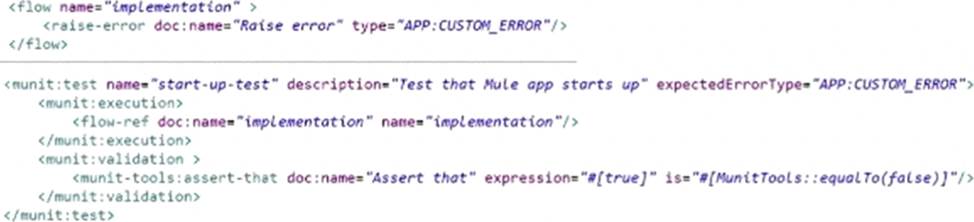
The flow name is ‘’implementation’’ with code for the MUnit test case.
When the MUnit test case is executed, what is the expected result?
- A . The test case fails with an assertion error
- B . The test throws an error and does not start
- C . The test case fails with an unexpected error type
- D . The test case passes
A
Explanation:
Based on the code snippet and MUnit test case below, when the MUnit test case is executed, the expected result is that the test case fails with an assertion error. This is because the assert-equals processor compares two values for equality, and fails if they are not equal. In this case, the expected value is ‘Hello World’, but the actual value returned by the implementation flow is ‘Hello Mule’. Therefore, the assertion fails and an error is thrown.
References: https://docs.mulesoft.com/munit/2.3/assert-equals-processor
A Mule application need to invoice an API hosted by an external system to initiate a process. The external API takes anywhere between one minute and 24 hours to compute its process.
Which implementation should be used to get response data from the external API after it completes processing?
- A . Use an HTTP Connector to invoke the API and wait for a response
- B . Use a Scheduler to check for a response every minute
- C . Use an HTTP Connector inside Async scope to invoice the API and wait for a response
- D . Expose an HTTP callback API in Mule and register it with the external system
D
Explanation:
To get response data from the external API after it completes processing, the developer should expose an
HTTP callback API in Mule and register it with the external system. This way, the external API can invoke the callback API with the response data when it is ready, instead of making the Mule application wait for a long time or poll for a response repeatedly.
References: https://docs.mulesoft.com/mule-runtime/4.3/http-listener-ref#callback
When registering a client application with an existing API instance or API Group instance, what is required to manually approve or reject request access?
- A . To configure the SLA tier for the application and have the role of Organization Administrator, API Manager Environment Administrator, or the Manage Contacts permission
- B . To configure the SLA tier for the application and have the Exchange Administrator permission
- C . To configure the SLA tier for the application
- D . To only have Exchange Administrator permission
A
Explanation:
To manually approve or reject request access when registering a client application with an existing API
instance or API Group instance, it is required to configure the SLA tier for the application and have one of the following roles or permissions: Organization Administrator, API Manager Environment Administrator, or Manage Contracts permission. These roles or permissions allow managing client applications and contracts in API Manager.
References: https://docs.mulesoft.com/api-manager/2.x/client-applications#managing-client-applications-and-contracts
A Mule application defines as SSL/TLS keystore properly ‘tis,keystore.keyPassword’’ as secure.
How can this property be referenced to access its value within the application?
- A . #{secure::tiskeystore,keyPassowrd}
- B . ${secure::tiskeystore,keyPassowrd}
- C . ${secure::tiskeystore,keyPassowrd}
- D . p{secure::tiskeystore,keyPassowrd}
B
Explanation:
secure::tiskeystore,keyPassowrdShor : ofCorrectAnswerOnly:Toreferenceasecurepropertyvaluewithin
In this case, the property name is tiskeystore,keyPassword, so the correct syntax is ${secure::tiskeystore,keyPassowrd}.
References: https://docs.mulesoft.com/mule-runtime/4.3/secure-configuration-properties#referencing-secure-properties
Which configurations are required for HTTP Listener to enable mTLS authentication?
- A . Set an appropriate reconnection strategy and use persistent connections for the listener
- B . Set an appropriate keystore configuration and use persistent connections for the listener
- C . Set an appropriate keystore and truststore configuration for the listener
- D . Set an appropriate truststore configuration and reconnection strategy for the listener
C
Explanation:
To enable mTLS authentication for HTTP Listener, the developer needs to set an appropriate keystore and truststore configuration for the listener. The keystore contains the certificate and private key of the Mule application that are used to prove its identity to clients. The truststore contains the certificates of trusted clients that are allowed to access the Mule application.
References: https://docs.mulesoft.com/mule-runtime/4.3/tls-configuration#mutual-authentication
Which statement is true about using mutual TLS to secure an application?
- A . Mutual TLS requires a hardware security module to be used
- B . Mutual TLS authenticates the identity of the server before the identity of the client
- C . Mutual TLS ensures only authorized end users are allowed to access an endpoint
- D . Mutual TLS increases the encryption strength versus server-side TLS alone
B
Explanation:
Mutual TLS (mTLS) is an extension of TLS that requires both parties (client and server) to present their certificates to each other during the handshake process. This way, both parties can verify each other’s identity and establish a secure connection. The authentication of the server happens before the authentication of the client, as the server sends its certificate first and then requests the client’s certificate.
References: https://docs.mulesoft.com/mule-runtime/4.3/tls-configuration#mutual-authentication
Which type of cache invalidation does the Cache scope support without having to write any additional code?
- A . Write-through invalidation
- B . White-behind invalidation
- C . Time to live
- D . Notification-based invalidation
C
Explanation:
The Cache scope supports time to live (TTL) as a cache invalidation strategy without having to write any additional code. TTL specifies how long the cached response is valid before it expires and needs to be refreshed. The Cache scope also supports custom invalidation strategies using MEL or Data Weave expressions.
References: https://docs.mulesoft.com/mule-runtime/4.3/cache-scope#cache_invalidation
Latest MCD-Level 2 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

