Microsoft SC-400 Microsoft Information Protection Administrator Online Training
Microsoft SC-400 Online Training
The questions for SC-400 were last updated at Mar 02,2026.
- Exam Code: SC-400
- Exam Name: Microsoft Information Protection Administrator
- Certification Provider: Microsoft
- Latest update: Mar 02,2026
You are implementing a data classification solution.
The research department at your company requires that documents containing programming code be labeled as Confidential. The department provides samples of the code from its document library. The solution must minimize administrative effort.
What should you do?
- A . Create a custom classifier.
- B . Create a sensitive info type that uses Exact Data Match (EDM).
- C . Use the source code classifier.
- D . Create a sensitive info type that uses a regular expression.
You have a new Microsoft 365 tenant.
You need to ensure that custom trainable classifiers can be created in the tenant.
To which role should you be assigned to perform the configuration?
- A . Security administrator
- B . Security operator
- C . Global administrator
- D . Compliance administrator
You need to automatically apply a sensitivity label to documents that contain information about your company’s
network including computer names, IP addresses, and configuration information.
Which two objects should you use? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. (Choose two.)
- A . an Information protection auto-labeling policy
- B . a custom trainable classifier
- C . a sensitive info type that uses a regular expression
- D . a data loss prevention (DLP) policy
- E . a sensitive info type that uses keywords
- F . a sensitivity label that has auto-labeling
You are creating a custom trainable classifier to identify organizational product codes referenced in Microsoft 365 content.
You identify 300 files to use as seed content.
Where should you store the seed content?
- A . a Microsoft SharePoint Online folder
- B . a Microsoft OneDrive for Business folder
- C . an Azure file share
- D . Microsoft Exchange Online shared mailbox
Each product group at your company must show a distinct product logo in encrypted emails instead of the standard Microsoft Office 365 logo.
What should you do to create the branding templates?
- A . Create a Transport rule.
- B . Create an RMS template.
- C . Run the Set-IRMConfiguration cmdlet.
- D . Run the New-OMEConfiguration cmdlet.
HOTSPOT
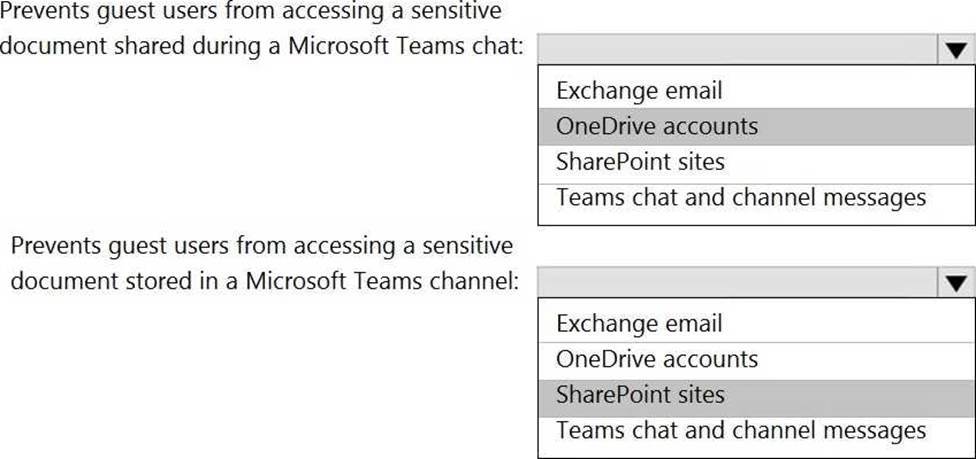
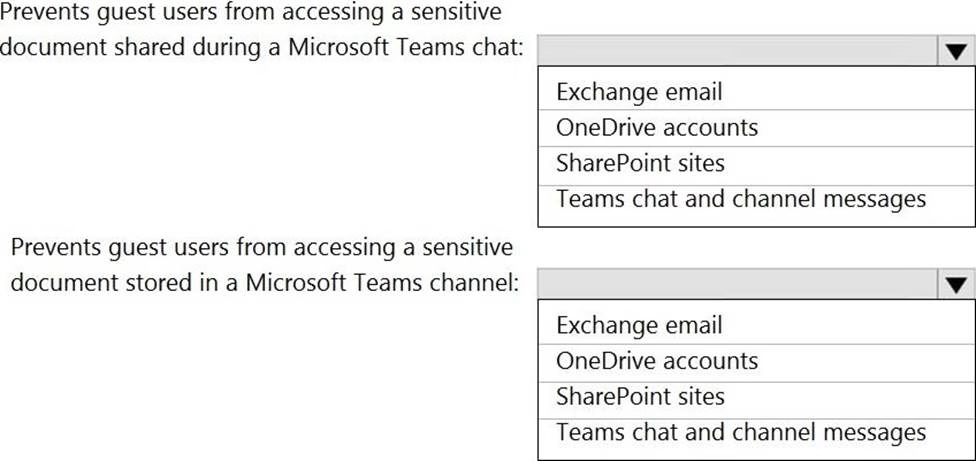
You create a data loss prevention (DLP) policy that meets the following requirements:
Prevents guest users from accessing a sensitive document shared during a Microsoft Teams chat Prevents guest users from accessing a sensitive document stored in a Microsoft Teams channel
Which location should you select for each requirement? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You are configuring a data loss prevention (DLP) policy to report when credit card data is found on a Windows 10 device joined to Azure Active Directory (Azure AD).
You plan to use information from the policy to restrict the ability to copy the sensitive data to the clipboard.
What should you configure in the policy rule?
- A . the incident report
- B . an action
- C . user notifications
- D . user overrides
HOTSPOT
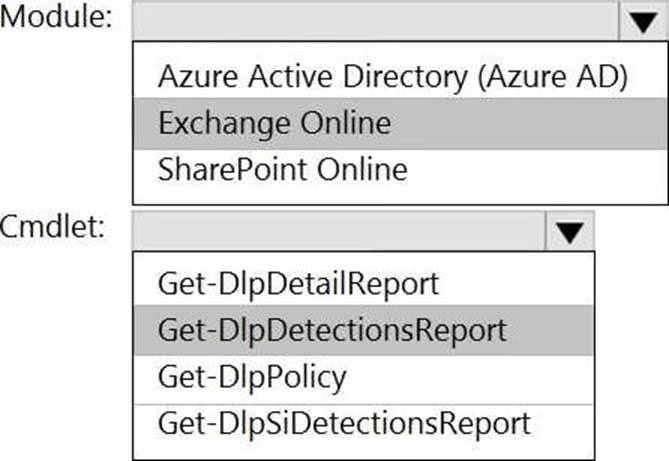
You have a Microsoft 365 E5 tenant.
Data loss prevention (DLP) policies are applied to Exchange email, SharePoint sites, and OneDrive accounts locations.
You need to use PowerShell to retrieve a summary of the DLP rule matches from the last seven days.
Which PowerShell module and cmdlet should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
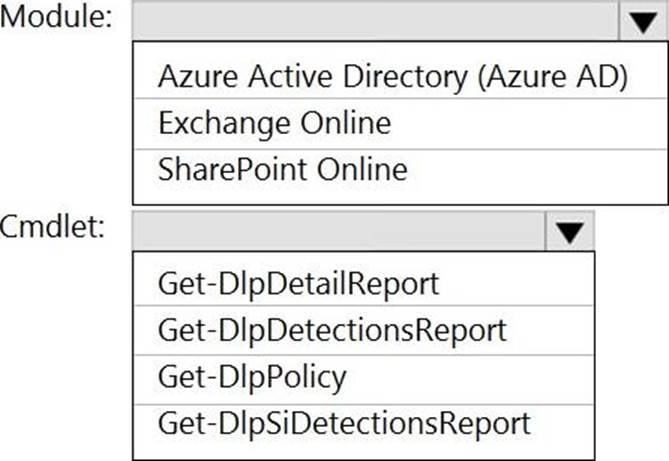
HOTSPOT
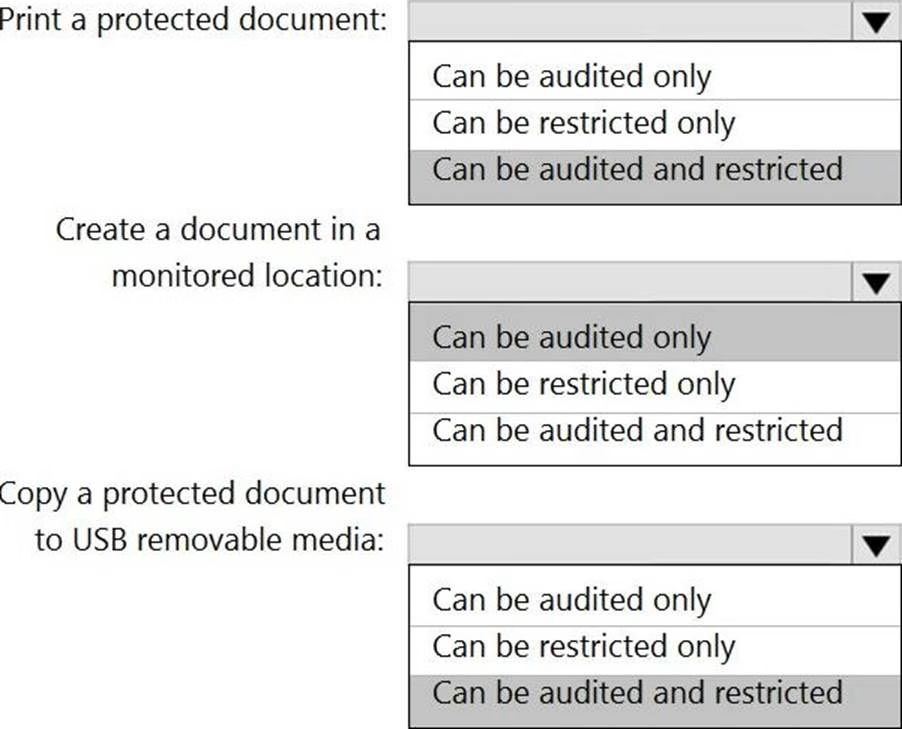
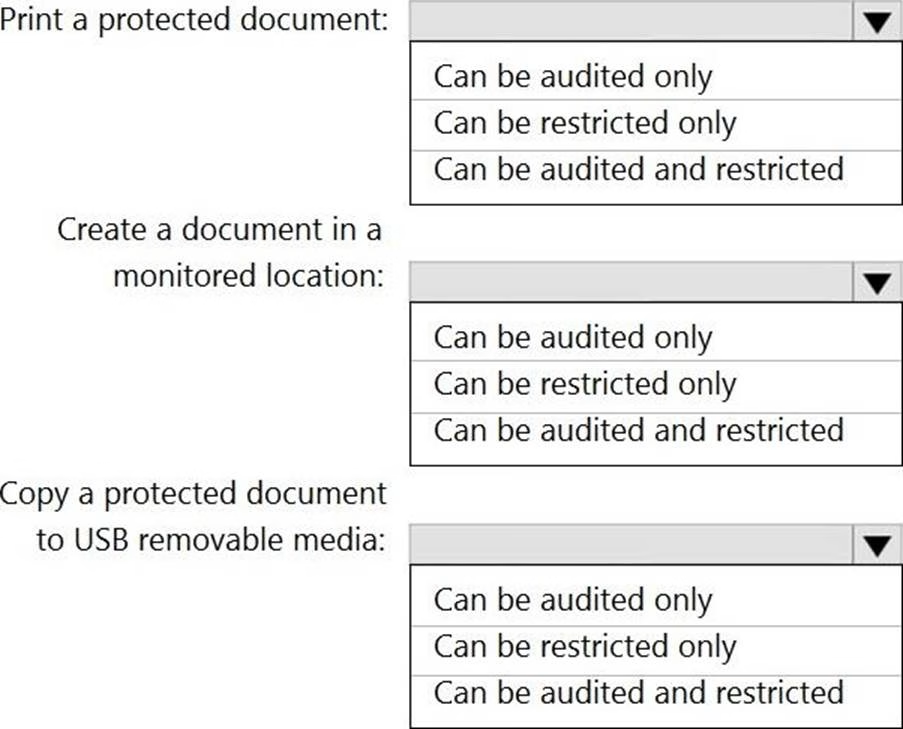
You plan to implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You need to identify which end user activities can be audited on the endpoints, and which activities can be restricted on the endpoints.
What should you identify for each activity? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 tenant and the Windows 10 devices shown in the following table.
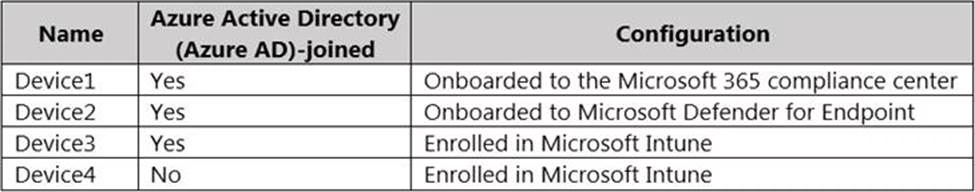
To which devices can you apply Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings?
- A . Device1, Device3, and Device4 only
- B . Device1, Device2, Device3, and Device4
- C . Device1 and Device2 only
- D . Device1 and Device3 only
- E . Device1 only
Latest SC-400 Dumps Valid Version with 83 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund