Microsoft SC-300 Microsoft Identity and Access Administrator Online Training
Microsoft SC-300 Online Training
The questions for SC-300 were last updated at Dec 16,2025.
- Exam Code: SC-300
- Exam Name: Microsoft Identity and Access Administrator
- Certification Provider: Microsoft
- Latest update: Dec 16,2025
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD.
Solution: You configure password writeback.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD.
Solution: You configure pass-through authentication.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD.
Solution: You configure conditional access policies.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
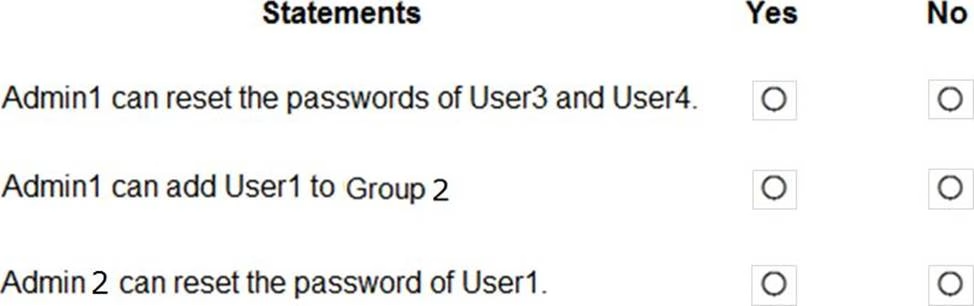
You have an Azure Active Directory (Azure AD) tenant that contains an administrative unit named Department1.
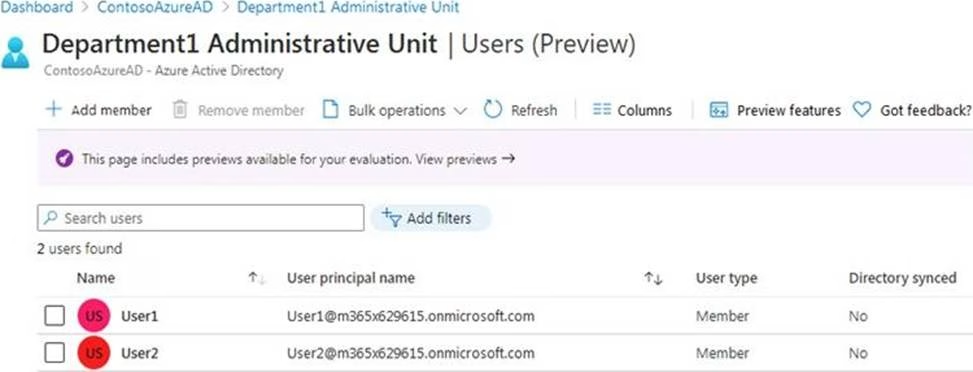
Department1 has the users shown in the Users exhibit. (Click the Users tab.)
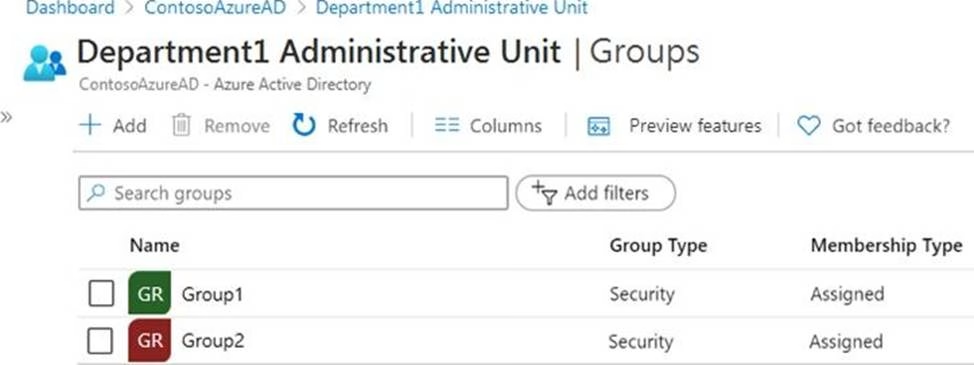
Department1 has the groups shown in the Groups exhibit. (Click the Groups tab.)
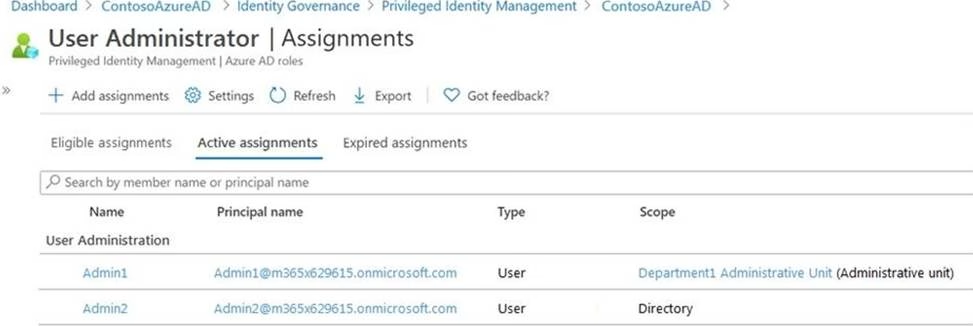
Department1 has the user administrator assignments shown in the Assignments exhibit. (Click the Assignments tab.)
The members of Group2 are shown in the Group2 exhibit. (Click the Group2 tab.)
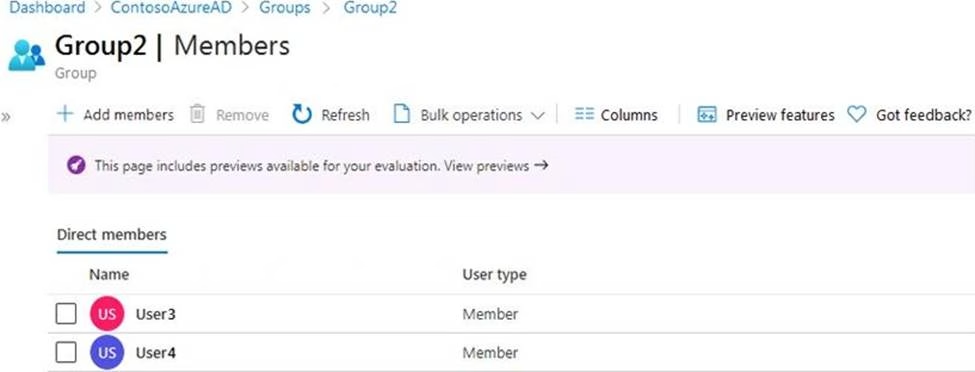
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant that contains a user named SecAdmin1. SecAdmin1 is assigned the Security administrator role.
SecAdmin1 reports that she cannot reset passwords from the Azure AD Identity Protection portal.
You need to ensure that SecAdmin1 can manage passwords and invalidate sessions on behalf of nonadministrative users. The solution must use the principle of least privilege.
Which role should you assign to SecAdmin1?
- A . Authentication administrator
- B . Helpdesk administrator
- C . Privileged authentication administrator
- D . Security operator
You configure Azure Active Directory (Azure AD) Password Protection as shown in the exhibit. (Click the Exhibit tab.)
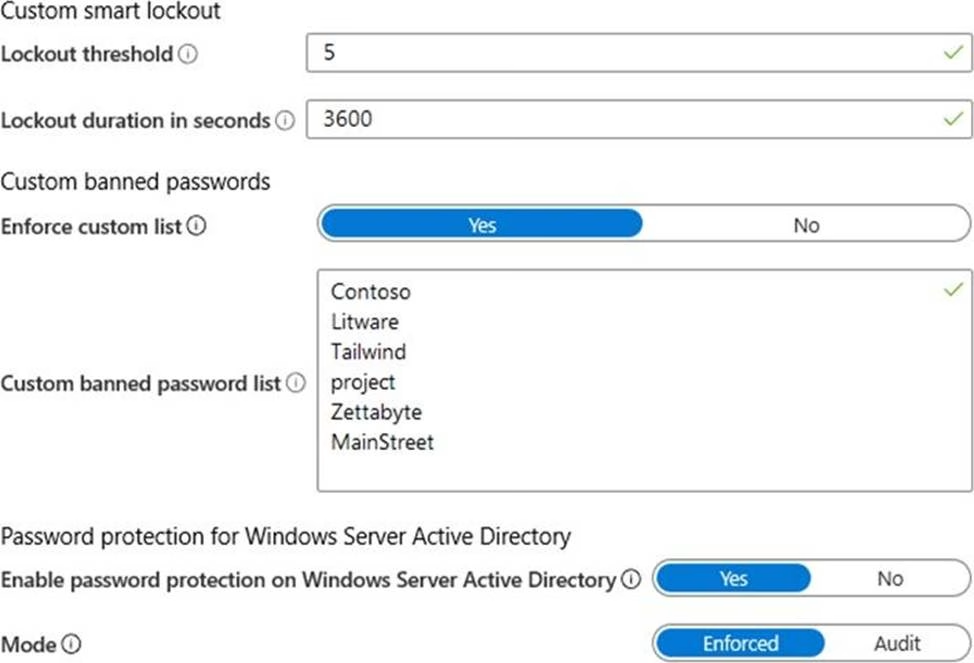
You are evaluating the following passwords:
✑ Pr0jectlitw@re
✑ T@ilw1nd
✑ C0nt0s0
Which passwords will be blocked?
- A . Pr0jectlitw@re and T@ilw1nd only
- B . C0nt0s0 only
- C . C0nt0s0, Pr0jectlitw@re, and T@ilw1nd
- D . C0nt0s0 and T@ilw1nd only
- E . C0nt0s0 and Pr0jectlitw@re only
You have a Microsoft 365 tenant.
All users have mobile phones and laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile phone connectivity.
While working from the remote locations, the users connect their laptop to a wired network that has internet access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
- A . a notification through the Microsoft Authenticator app
- B . security questions
- C . voice
- D . an app password
You configure a new Microsoft 365 tenant to use a default domain name of contoso.com.
You need to ensure that you can control access to Microsoft 365 resources by using conditional access policies.
What should you do first?
- A . Disable the User consent settings.
- B . Disable Security defaults.
- C . Configure a multi-factor authentication (MFA) registration policy.
- D . Configure password protection for Windows Server Active Directory.
Your company has a Microsoft 365 tenant.
The company has a call center that contains 300 users. In the call center, the users share desktop computers and might use a different computer every day. The call center computers are NOT configured for biometric identification.
The users are prohibited from having a mobile phone in the call center.
You need to require multi-factor authentication (MFA) for the call center users when they access Microsoft 365 services.
What should you include in the solution?
- A . a named network location
- B . the Microsoft Authenticator app
- C . Windows Hello for Business authentication
- D . FIDO2 tokens
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
All users who run applications registered in Azure AD are subject to conditional access policies.
You need to prevent the users from using legacy authentication.
What should you include in the conditional access policies to filter out legacy authentication attempts?
- A . a cloud apps or actions condition
- B . a user risk condition
- C . a client apps condition
- D . a sign-in risk condition
Latest SC-300 Dumps Valid Version with 106 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund