Microsoft SC-200 Microsoft Security Operations Analyst Online Training
Microsoft SC-200 Online Training
The questions for SC-200 were last updated at Feb 20,2026.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Feb 20,2026
You have an Azure subscription that has Azure Defender enabled for all supported resource types.
You need to configure the continuous export of high-severity alerts to enable their retrieval from a third-party security information and event management (SIEM) solution.
To which service should you export the alerts?
- A . Azure Cosmos DB
- B . Azure Event Grid
- C . Azure Event Hubs
- D . Azure Data Lake
You are responsible for responding to Azure Defender for Key Vault alerts.
During an investigation of an alert, you discover unauthorized attempts to access a key vault from a Tor exit node.
What should you configure to mitigate the threat?
- A . Key Vault firewalls and virtual networks
- B . Azure Active Directory (Azure AD) permissions
- C . role-based access control (RBAC) for the key vault
- D . the access policy settings of the key vault
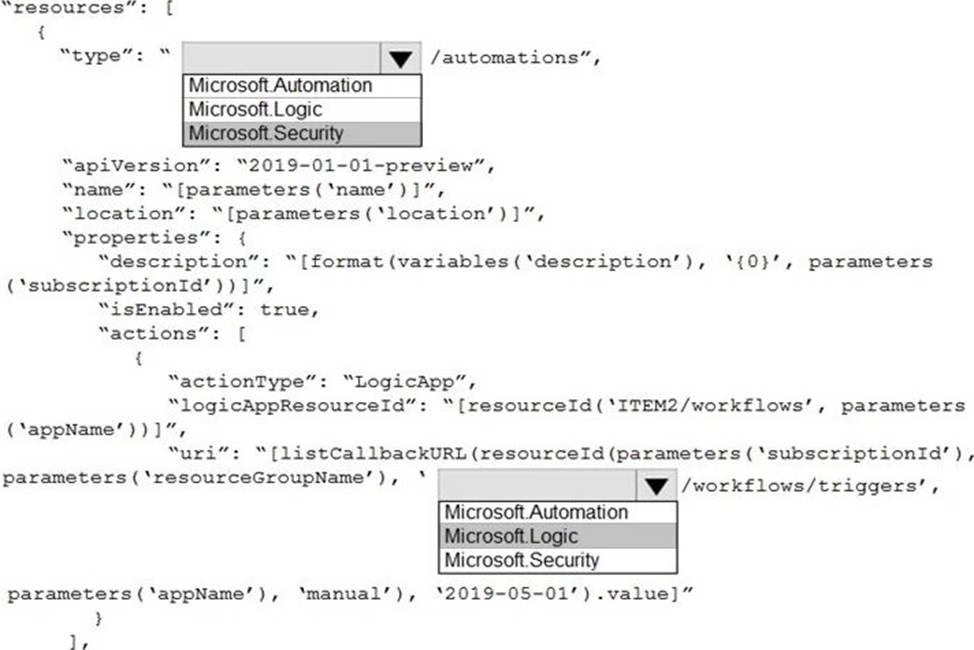
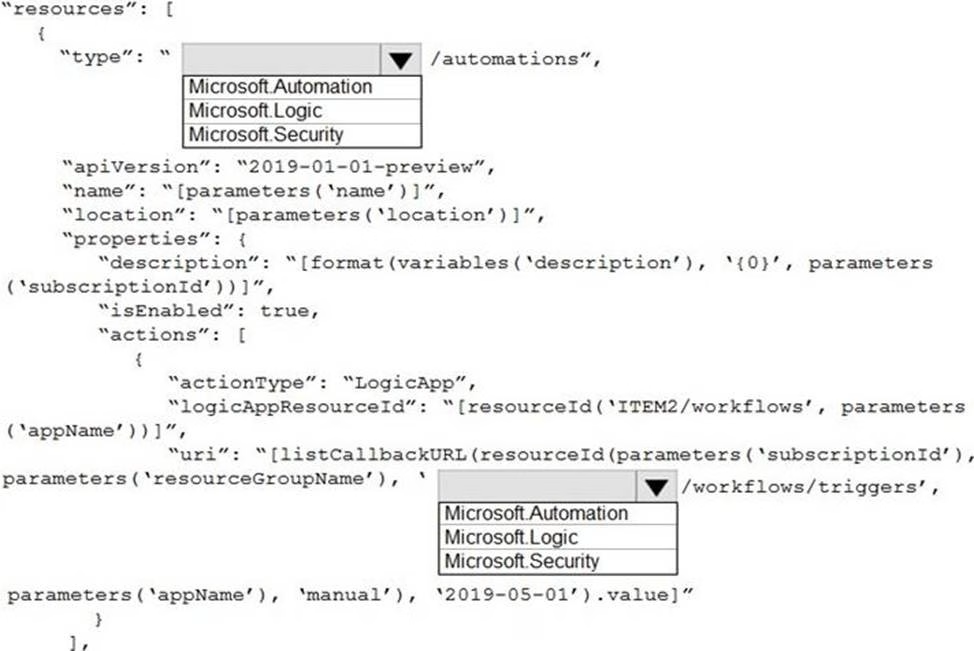
HOTSPOT
You need to use an Azure Resource Manager template to create a workflow automation that will trigger an automatic remediation when specific security alerts are received by Azure Security Center.
How should you complete the portion of the template that will provision the required Azure resources? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a Log Analytics workspace.
You need to enable just-in-time (JIT) VM access and network detections for Azure resources.
Where should you enable Azure Defender?
- A . at the subscription level
- B . at the workspace level
- C . at the resource level
You use Azure Defender.
You have an Azure Storage account that contains sensitive information.
You need to run a PowerShell script if someone accesses the storage account from a suspicious IP address.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . From Azure Security Center, enable workflow automation.
- B . Create an Azure logic appthat has a manual trigger
- C . Create an Azure logic app that has an Azure Security Center alert trigger.
- D . Create an Azure logic appthat has an HTTP trigger.
- E . From Azure Active Directory (Azure AD), add an app registration.
You recently deployed Azure Sentinel.
You discover that the default Fusion rule does not generate any alerts. You verify that the rule is enabled.
You need to ensure that the Fusion rule can generate alerts.
What should you do?
- A . Disable, and then enable the rule.
- B . Add data connectors
- C . Create a new machine learning analytics rule.
- D . Add a hunting bookmark.
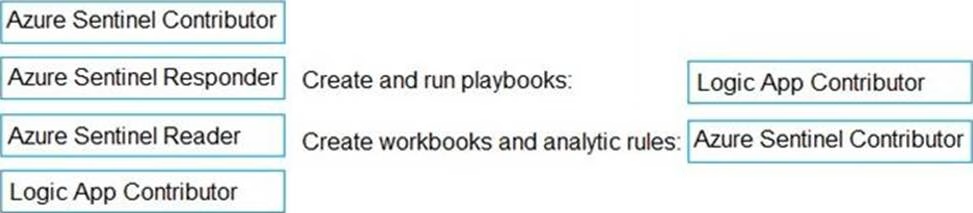
DRAG DROP
Your company deploys Azure Sentinel.
You plan to delegate the administration of Azure Sentinel to various groups.
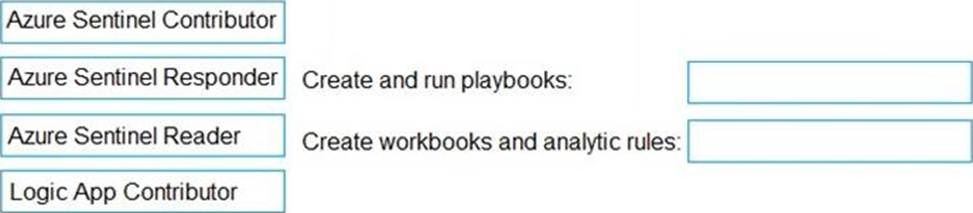
You need to delegate the following tasks:
✑ Create and run playbooks
✑ Create workbooks and analytic rules.
The solution must use the principle of least privilege.
Which role should you assign for each task? To answer, drag the appropriate roles to the correct tasks. Each role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
A company uses Azure Sentinel.
You need to create an automated threat response.
What should you use?
- A . a data connector
- B . a playbook
- C . a workbook
- D . a Microsoft incident creation rule
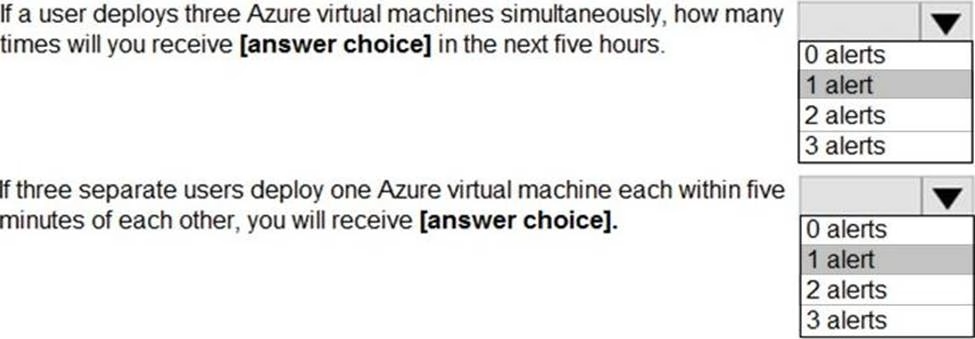
HOTSPOT
You use Azure Sentinel to monitor irregular Azure activity.
You create custom analytics rules to detect threats as shown in the following exhibit.
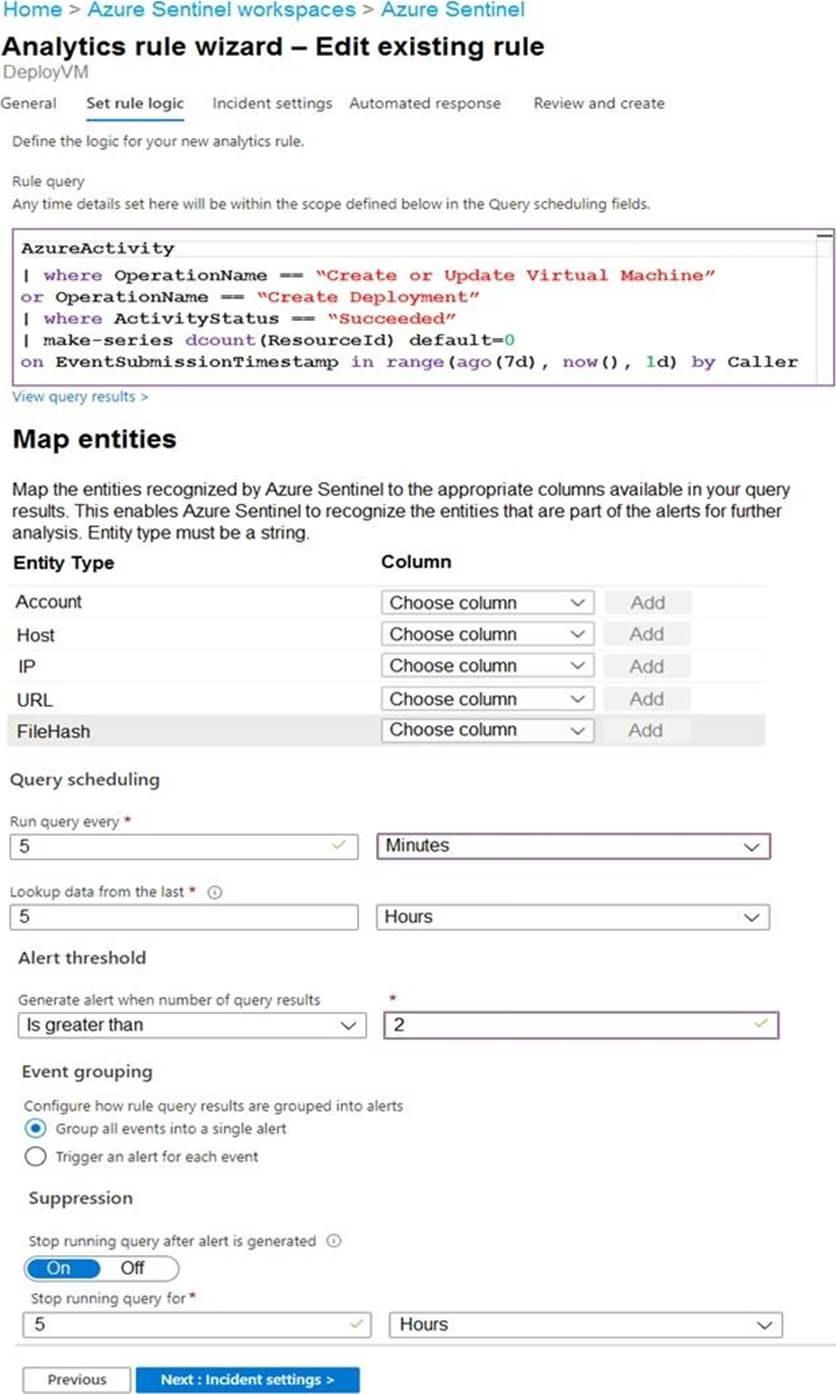
You do NOT define any incident settings as part of the rule definition.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
You have an Azure Sentinel deployment in the East US Azure region.
You create a Log Analytics workspace named LogsWest in the West US Azure region.
You need to ensure that you can use scheduled analytics rules in the existing Azure Sentinel deployment to generate alerts based on queries to LogsWest.
What should you do first?
- A . Deploy Azure Data Catalog to the West US Azure region.
- B . Modify the workspace settings of the existing Azure Sentinel deployment
- C . Add Microsoft Sentinel to a workspace.
- D . Create a data connector in Azure Sentinel.
Latest SC-200 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund