Microsoft SC-200 Microsoft Security Operations Analyst Online Training
Microsoft SC-200 Online Training
The questions for SC-200 were last updated at Feb 19,2026.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Feb 19,2026
You provision Azure Sentinel for a new Azure subscription. You are configuring the Security Events connector.
While creating a new rule from a template in the connector, you decide to generate a new alert for every event. You create the following rule query.
By which two components can you group alerts into incidents? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . user
- B . resource group
- C . IP address
- D . computer
Your company stores the data for every project in a different Azure subscription. All the subscriptions use the same Azure Active Directory (Azure AD) tenant.
Every project consists of multiple Azure virtual machines that run Windows Server. The Windows events of the virtual machines are stored in a Log Analytics workspace in each machine’s respective subscription.
You deploy Azure Sentinel to a new Azure subscription.
You need to perform hunting queries in Azure Sentinel to search across all the Log Analytics workspaces of all the subscriptions.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Add the Security Events connector to the Azure Sentinel workspace.
- B . Create a query that uses the workspace expression and the union operator.
- C . Use the alias statement.
- D . Create a query that uses the resource expression and the alias operator.
- E . Add the Azure Sentinel solution to each workspace.
You have an Azure Sentinel workspace.
You need to test a playbook manually in the Azure portal.
From where can you run the test in Azure Sentinel?
- A . Playbooks
- B . Analytics
- C . Threat intelligence
- D . Incidents
You have a custom analytics rule to detect threats in Azure Sentinel.
You discover that the analytics rule stopped running. The rule was disabled, and the rule name has a prefix of AUTO DISABLED.
What is a possible cause of the issue?
- A . There are connectivity issues between the data sources and Log Analytics.
- B . The number of alerts exceeded 10,000 within two minutes.
- C . The rule query takes too long to run and times out.
- D . Permissions to one of the data sources of the rule query were modified.
Your company uses Azure Sentinel.
A new security analyst reports that she cannot assign and dismiss incidents in Azure Sentinel. You need to resolve the issue for the analyst. The solution must use the principle of least privilege.
Which role should you assign to the analyst?
- A . Azure Sentinel Responder
- B . Logic App Contributor
- C . Azure Sentinel Contributor
- D . Azure Sentinel Reader
You implement Safe Attachments policies in Microsoft Defender for Office 365.
Users report that email messages containing attachments take longer than expected to be received.
You need to reduce the amount of time it takes to deliver messages that contain attachments without compromising security. The attachments must be scanned for malware, and any messages that contain malware must be blocked.
What should you configure in the Safe Attachments policies?
- A . Dynamic Delivery
- B . Replace
- C . Block and Enable redirect
- D . Monitor and Enable redirect
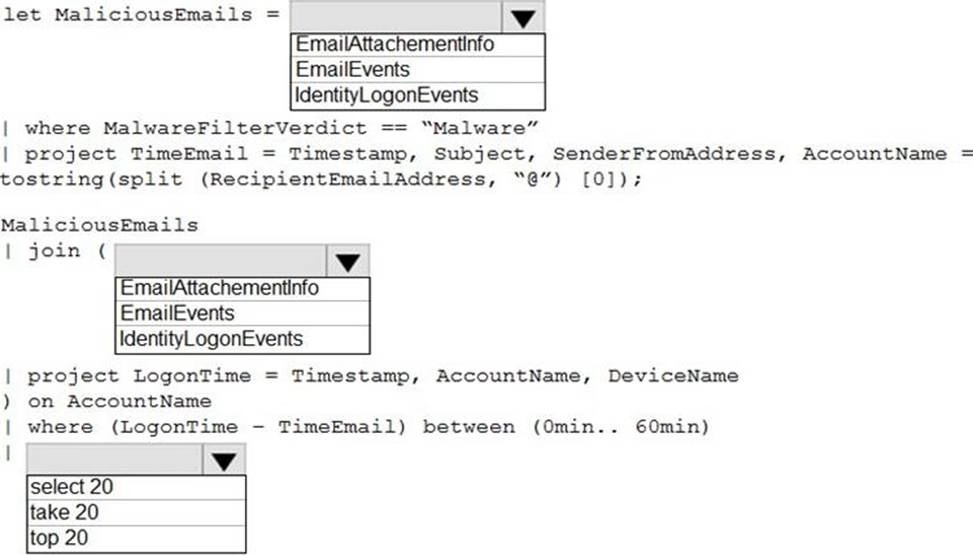
HOTSPOT
You are informed of an increase in malicious email being received by users.
You need to create an advanced hunting query in Microsoft 365 Defender to identify whether the accounts of the email recipients were compromised. The query must return the most recent 20 sign-ins performed by the recipients within an hour of receiving the known malicious email.
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You receive a security bulletin about a potential attack that uses an image file.
You need to create an indicator of compromise (IoC) in Microsoft Defender for Endpoint to prevent the attack.
Which indicator type should you use?
- A . a URL/domain indicator that has Action set to Alert only
- B . a URL/domain indicator that has Action set to Alert and block
- C . a file hash indicator that has Action set to Alert and block
- D . a certificate indicator that has Action set to Alert and block
Your company deploys the following services:
✑ Microsoft Defender for Identity
✑ Microsoft Defender for Endpoint
✑ Microsoft Defender for Office 365
You need to provide a security analyst with the ability to use the Microsoft 365 security center. The analyst must be able to approve and reject pending actions generated by Microsoft Defender for Endpoint. The solution must use the principle of least privilege.
Which two roles should assign to the analyst? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . the Compliance Data Administrator in Azure Active Directory (Azure AD)
- B . the Active remediation actions role in Microsoft Defender for Endpoint
- C . the Security Administrator role in Azure Active Directory (Azure AD)
- D . the Security Reader role in Azure Active Directory (Azure AD)
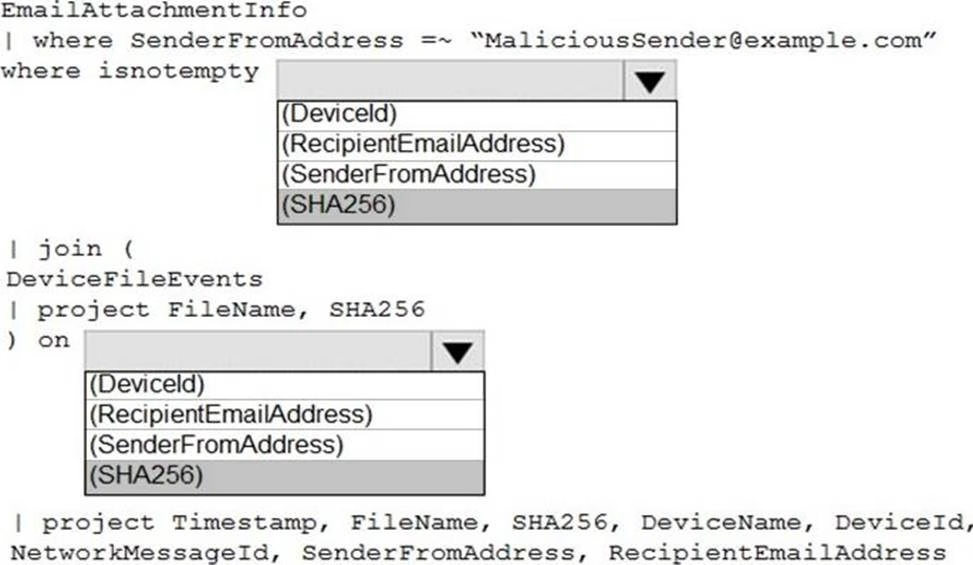
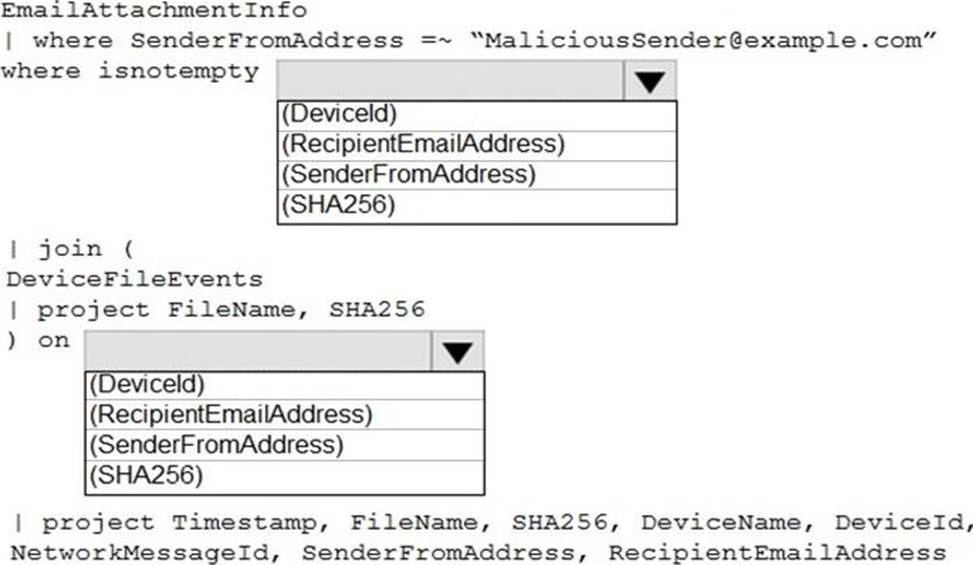
HOTSPOT
You have a Microsoft 365 E5 subscription that uses Microsoft Defender and an Azure subscription that uses Azure Sentinel.
You need to identify all the devices that contain files in emails sent by a known malicious email sender. The query will be based on the match of the SHA256 hash.
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Latest SC-200 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund