Microsoft SC-200 Microsoft Security Operations Analyst Online Training
Microsoft SC-200 Online Training
The questions for SC-200 were last updated at Feb 20,2026.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Feb 20,2026
You are configuring Azure Sentinel.
You need to send a Microsoft Teams message to a channel whenever a sign-in from a suspicious IP address is detected.
Which two actions should you perform in Azure Sentinel? Each correct answer presents part of the
solution. NOTE: Each correct selection is worth one point.
- A . Add a playbook.
- B . Associate a playbook to an incident.
- C . Enable Entity behavior analytics.
- D . Create a workbook.
- E . Enable the Fusion rule.
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of compromise (IoC).
What should you use?
- A . notebooks in Azure Sentinel
- B . Microsoft Cloud App Security
- C . Azure Monitor
- D . hunting queries in Azure Sentinel
You plan to create a custom Azure Sentinel query that will provide a visual representation of the security alerts generated by Azure Security Center.
You need to create a query that will be used to display a bar graph.
What should you include in the query?
- A . extend
- B . bin
- C . count
- D . workspace
You use Azure Sentinel.
You need to receive an immediate alert whenever Azure Storage account keys are enumerated.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Create a livestream
- B . Add a data connector
- C . Create an analytics rule
- D . Create a hunting query.
- E . Create a bookmark.
DRAG DROP
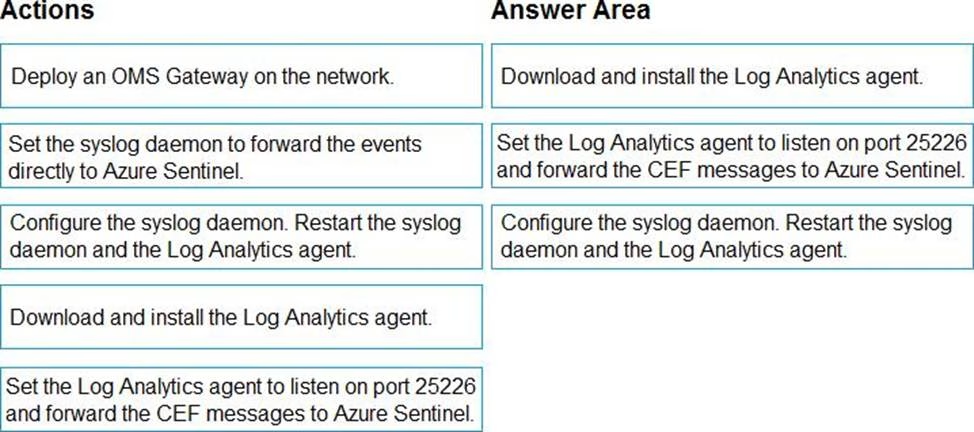
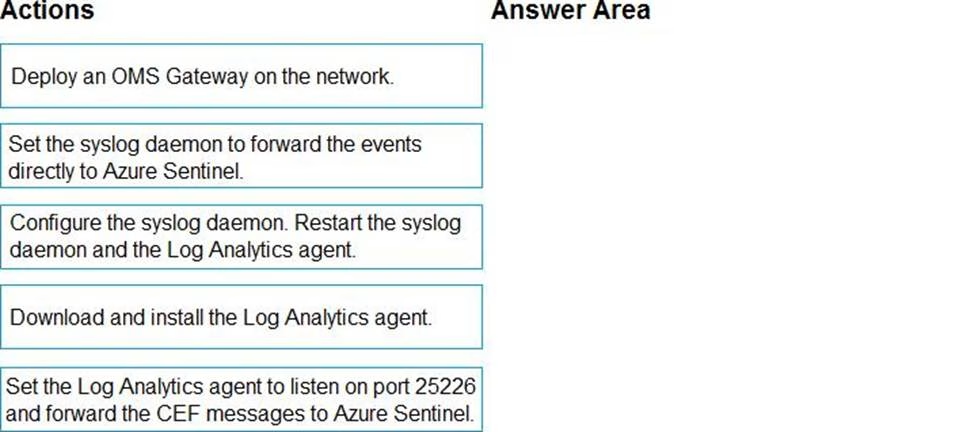
You plan to connect an external solution that will send Common Event Format (CEF) messages to Azure Sentinel.
You need to deploy the log forwarder.
Which three actions should you perform in sequence? To answer, move the appropriate actions form the list of actions to the answer area and arrange them in the correct order.
HOTSPOT
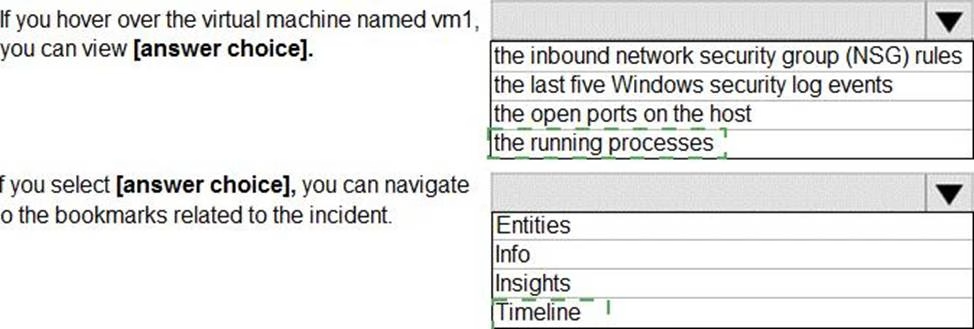
From Azure Sentinel, you open the Investigation pane for a high-severity incident as shown in the following exhibit.
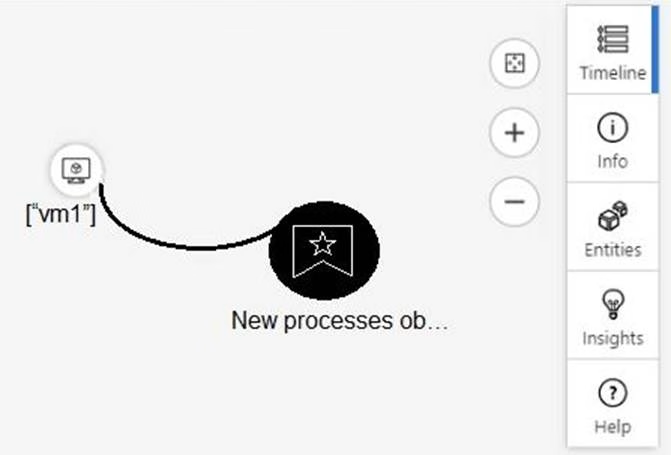
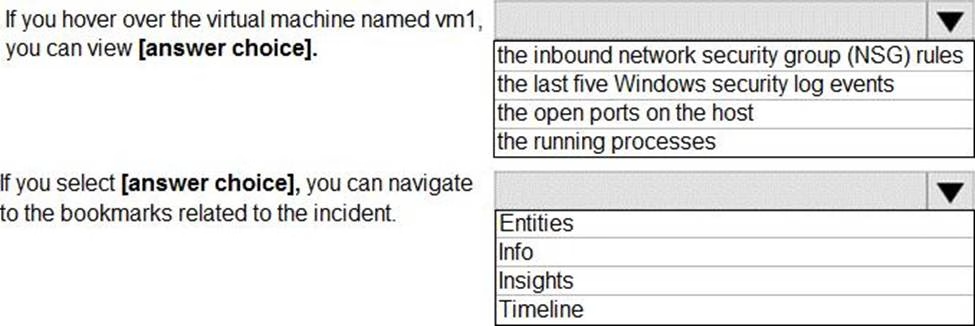
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
DRAG DROP
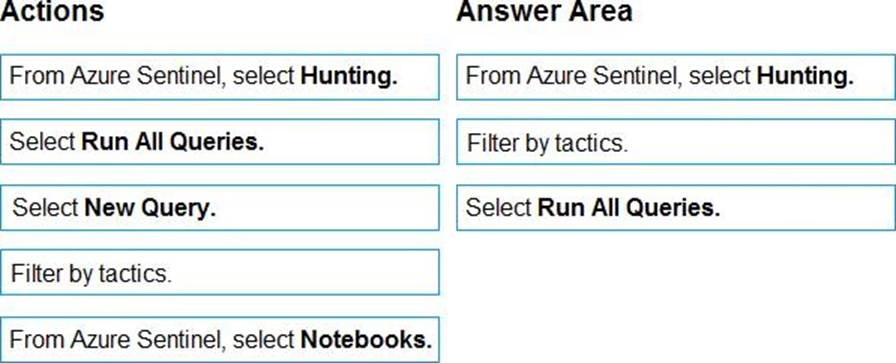
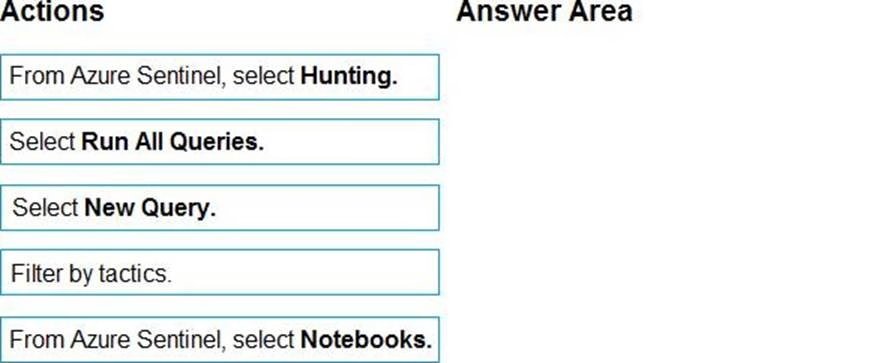
You have an Azure Sentinel deployment.
You need to query for all suspicious credential access activities.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an existing Azure logic app that is used to block Azure Active Directory (Azure AD) users.
The logic app is triggered manually.
You deploy Azure Sentinel.
You need to use the existing logic app as a playbook in Azure Sentinel.
What should you do first?
- A . And a new scheduled query rule.
- B . Add a data connector to Azure Sentinel.
- C . Configure a custom Threat Intelligence connector in Azure Sentinel.
- D . Modify the trigger in the logic app.
Your company uses Azure Sentinel to manage alerts from more than 10,000 IoT devices.
A security manager at the company reports that tracking security threats is increasingly difficult due to the large number of incidents.
You need to recommend a solution to provide a custom visualization to simplify the investigation of threats and to infer threats by using machine learning.
What should you include in the recommendation?
- A . built-in queries
- B . livestream
- C . notebooks
- D . bookmarks
You have a playbook in Azure Sentinel.
When you trigger the playbook, it sends an email to a distribution group.
You need to modify the playbook to send the email to the owner of the resource instead of the distribution group.
What should you do?
- A . Add a parameter and modify the trigger.
- B . Add a custom data connector and modify the trigger.
- C . Add a condition and modify the action.
- D . Add a parameter and modify the action.
Latest SC-200 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund