Microsoft SC-200 Microsoft Security Operations Analyst Online Training
Microsoft SC-200 Online Training
The questions for SC-200 were last updated at Feb 19,2026.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Feb 19,2026
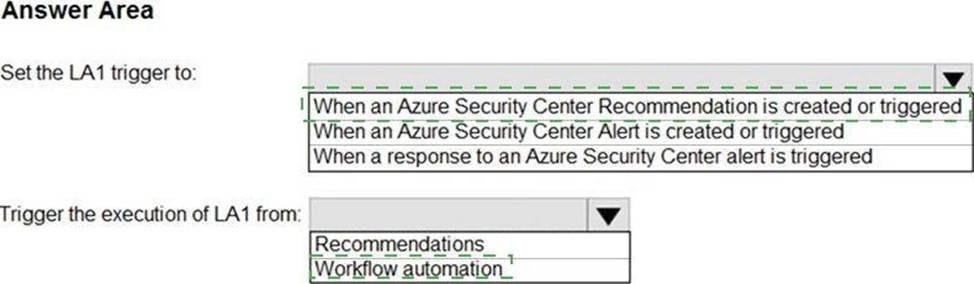
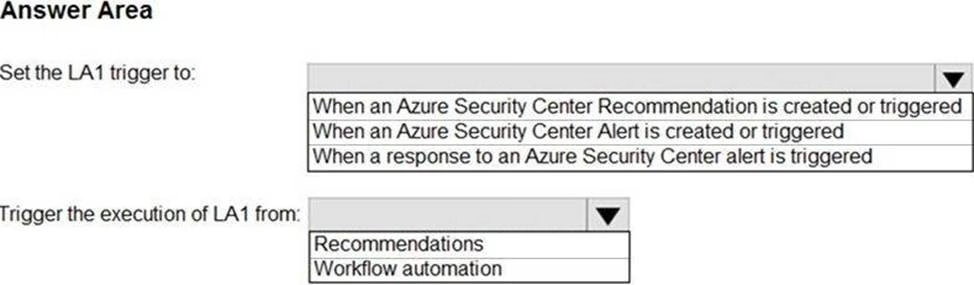
HOTSPOT
You have an Azure subscription that has Azure Defender enabled for all supported resource types.
You create an Azure logic app named LA1.
You plan to use LA1 to automatically remediate security risks detected in Azure Security Center. View the window
You need to test LA1 in Security Center.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that uses Azure Defender. You have 100 virtual machines in a resource group named RG1.
You assign the Security Admin roles to a new user named SecAdmin1.
You need to ensure that SecAdmin1 can apply quick fixes to the virtual machines by using Azure Defender. The solution must use the principle of least privilege.
Which role should you assign to SecAdmin1?
- A . the Security Reader role for the subscription
- B . the Contributor for the subscription
- C . the Contributor role for RG1
- D . the Owner role for RG1
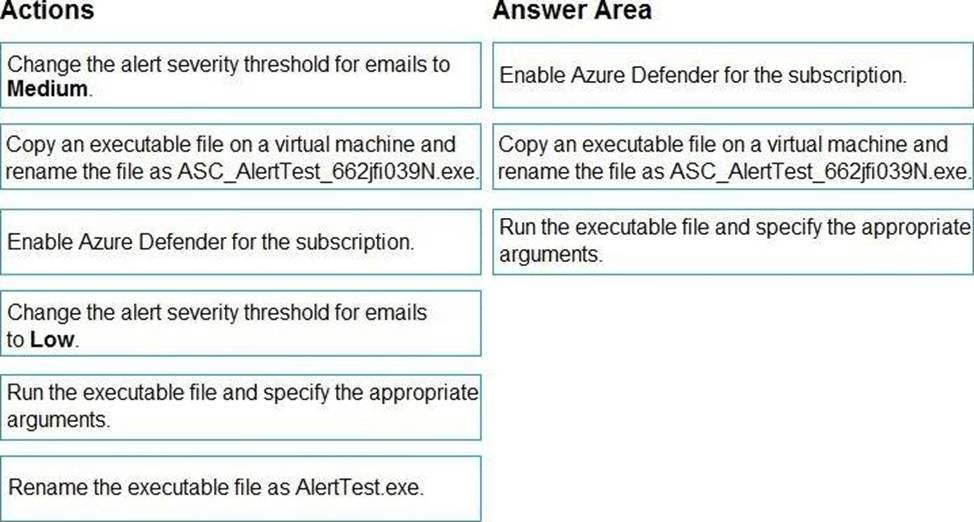
You provision a Linux virtual machine in a new Azure subscription.
You enable Azure Defender and onboard the virtual machine to Azure Defender.
You need to verify that an attack on the virtual machine triggers an alert in Azure Defender.
Which two Bash commands should you run on the virtual machine? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . cp /bin/echo ./asc_alerttest_662jfi039n
- B . ./alerttest testing eicar pipe
- C . cp /bin/echo ./alerttest
- D . ./asc_alerttest_662jfi039n testing eicar pipe
You create an Azure subscription named sub1.
In sub1, you create a Log Analytics workspace named workspace1.
You enable Azure Security Center and configure Security Center to use workspace1.
You need to ensure that Security Center processes events from the Azure virtual machines that report to workspace1.
What should you do?
- A . In workspace1, install a solution.
- B . In sub1, register a provider.
- C . From Security Center, create a Workflow automation.
- D . In workspace1, create a workbook.
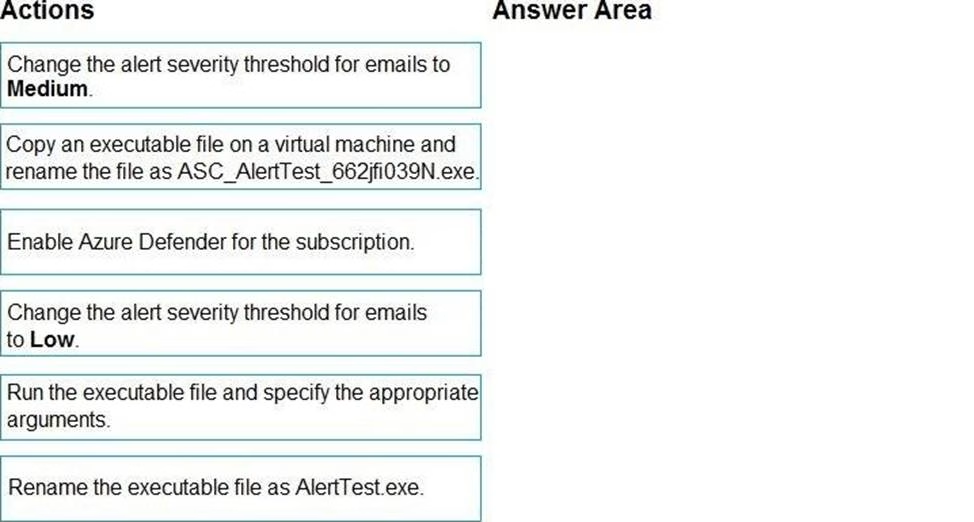
DRAG DROP
You create a new Azure subscription and start collecting logs for Azure Monitor.
You need to configure Azure Security Center to detect possible threats related to sign-ins from suspicious IP addresses to Azure virtual machines. The solution must validate the configuration.
Which three actions should you perform in a sequence? To answer, move the appropriate actions from the list of action to the answer area and arrange them in the correct order.
Your company uses Azure Security Center and Azure Defender.
The security operations team at the company informs you that it does NOT receive email notifications for security alerts.
What should you configure in Security Center to enable the email notifications?
- A . Security solutions
- B . Security policy
- C . Pricing & settings
- D . Security alerts
- E . Azure Defender
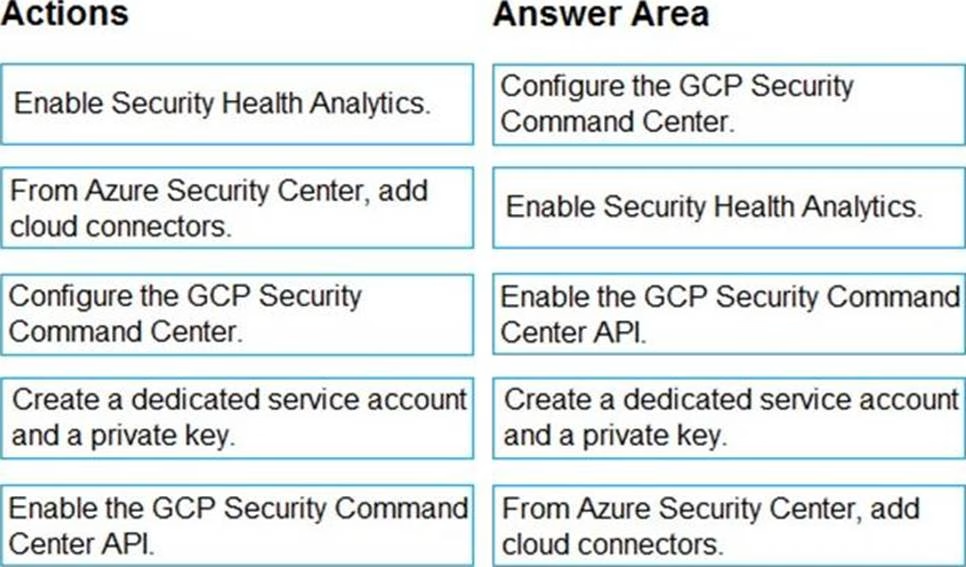
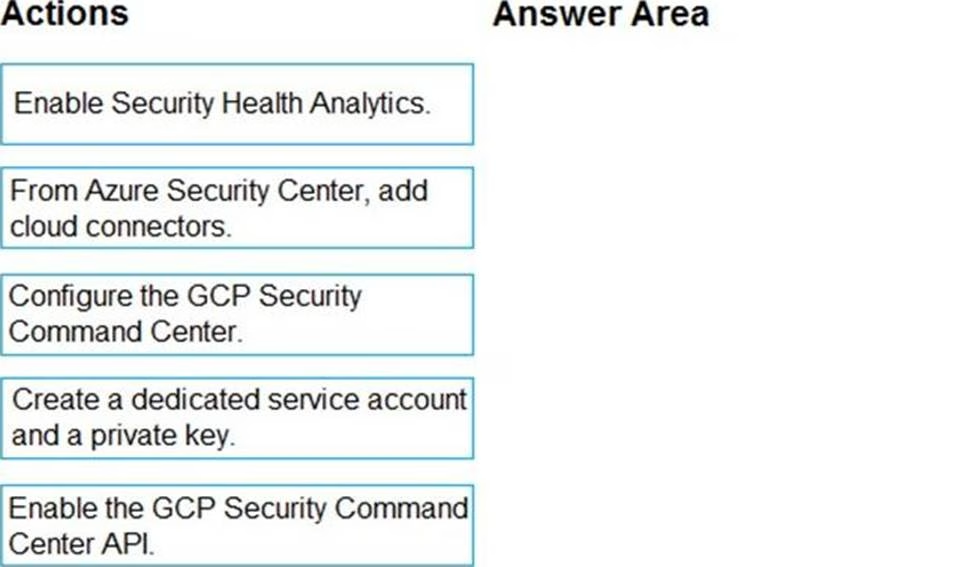
DRAG DROP
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Regulatory compliance, you download the report.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
Solution: From Security alerts, you select the alert, select Take Action, and then expand the Mitigate the threat section.
Does this meet the goal?
- A . Yes
- B . No
You plan to create a custom Azure Sentinel query that will track anomalous Azure Active Directory (Azure AD) sign-in activity and present the activity as a time chart aggregated by day.
You need to create a query that will be used to display the time chart.
What should you include in the query?
- A . extend
- B . bin
- C . makeset
- D . workspace
Latest SC-200 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund