Microsoft SC-200 Microsoft Security Operations Analyst Online Training
Microsoft SC-200 Online Training
The questions for SC-200 were last updated at Feb 19,2026.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Feb 19,2026
You need to ensure that the processing of incidents generated by rulequery1 meets the Microsoft Sentinel requirements.
What should you create first?
- A . a playbook with an incident trigger
- B . a playbook with an entity trigger
- C . an Azure Automation rule
- D . a playbook with an alert trigger
You need to implement the Defender for Cloud requirements.
Which subscription-level role should you assign to Group1?
- A . Security Admin
- B . Owner
- C . Security Assessment Contributor
- D . Contributor
You need to implement the scheduled rule for incident generation based on rulequery1.
What should you configure first?
- A . entity mapping
- B . custom details
- C . event grouping
- D . alert details
You need to ensure that the Group1 members can meet the Microsoft Sentinel requirements.
Which role should you assign to Group1?
- A . Microsoft Sentinel Automation Contributor
- B . Logic App Contributor
- C . Automation Operator
- D . Microsoft Sentinel Playbook Operator
Topic 4, Misc. Questions
Fabrikam. Inc. is a financial services company.
The company has branch offices in New York. London, and Singapore. Fabrikam has remote users located across the globe. The remote users access company resources, including cloud resources, by using a VPN connection to a branch office.
The network contains an Active Directory Domain Services (AD DS) forest named fabrikam.com that syncs with an Azure AD tenant named fabrikam.com. To sync the forest, Fabrikam uses Azure AD Connect with pass-through authentication enabled and password hash synchronization disabled. The fabrikam.com forest contains two global groups named Group1 and Group2.
All the users at Fabrikam are assigned a Microsoft 365 E5 license and an Azure Active Directory Premium Plan 2 license. Fabrikam implements Microsoft Defender for Identity and Microsoft Defender for Cloud Apps and enables log collectors.
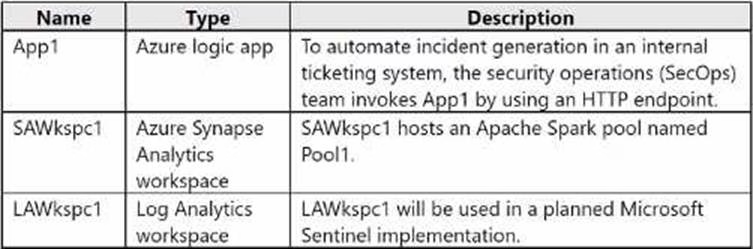
Fabrikam has an Azure subscription that contains the resources shown in the following table.
Fabrikam has an Amazon Web Services (AWS) account named Account1. Account1 contains 100 Amazon Elastic Compute Cloud (EC2) instances that run a custom Windows Server 2022. The image includes Microsoft SQL Server 2019 and does NOT have any agents installed.
When the users use the VPN connections. Microsoft 365 Defender raises a high volume of impossible travel alerts that are false positives. Defender for Identity raises a high volume of Suspected DCSync attack alerts that are false positives.
Fabrikam plans to implement the following services:
• Microsoft Defender for Cloud
• Microsoft Sentinel
Fabrikam identifies the following business requirements:
• Use the principle of least privilege, whenever possible.
• Minimize administrative effort.
Fabrikam identifies the following Microsoft Defender for Cloud Apps requirements:
• Ensure that impossible travel alert policies are based on the previous activities of each user.
• Reduce the amount of impossible travel alerts that are false positives.
Minimize the administrative effort required to investigate the false positive alerts.
Fabrikam identifies the following Microsoft Defender for Cloud requirements:
• Ensure that the members of Group2 can modify security policies.
• Ensure that the members of Group1 can assign regulatory compliance policy initiatives at the Azure subscription level.
• Automate the deployment of the Azure Connected Machine agent for Azure Arc-enabled servers to the existing and future resources of Account1.
• Minimize the administrative effort required to investigate the false positive alerts.
Fabrikam identifies the following Microsoft Sentinel requirements:
• Query for NXDOMAIN DNS requests from the last seven days by using built-in Advanced Security Information Model (ASIM) unifying parsers.
• From AWS EC2 instances, collect Windows Security event log entries that include local group membership changes.
• Identify anomalous activities of Azure AD users by using User and Entity Behavior Analytics (UEBA).
• Evaluate the potential impact of compromised Azure AD user credentials by using UEBA.
• Ensure that App1 is available for use in Microsoft Sentinel automation rules.
• Identify the mean time to triage for incidents generated during the last 30 days.
• Identify the mean time to close incidents generated during the last 30 days.
• Ensure that the members of Group1 can create and run playbooks.
• Ensure that the members of Group1 can manage analytics rules.
• Run hunting queries on Pool! by using Jupyter notebooks.
• Ensure that the members of Group2 can manage incidents.
• Maximize the performance of data queries.
• Minimize the amount of collected data.
DRAG DROP
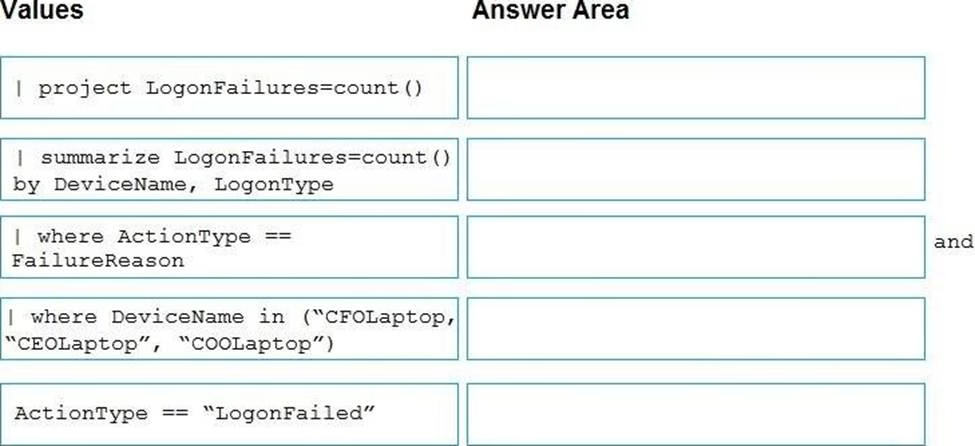
You are investigating an incident by using Microsoft 365 Defender.
You need to create an advanced hunting query to detect failed sign-in authentications on three devices named CFOLaptop, CEOLaptop, and COOLaptop.
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to receive a security alert when a user attempts to sign in from a location that was never used by the other users in your organization to sign in.
Which anomaly detection policy should you use?
- A . Impossible travel
- B . Activity from anonymous IP addresses
- C . Activity from infrequent country
- D . Malware detection
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You have Microsoft SharePoint Online sites that contain sensitive documents. The documents contain customer account numbers that each consists of 32 alphanumeric characters.
You need to create a data loss prevention (DLP) policy to protect the sensitive documents.
What should you use to detect which documents are sensitive?
- A . SharePoint search
- B . a hunting query in Microsoft 365 Defender
- C . Azure Information Protection
- D . RegEx pattern matching
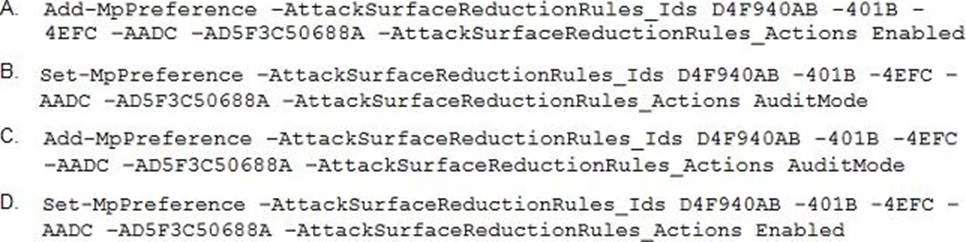
Your company uses line-of-business apps that contain Microsoft Office VBA macros.
You plan to enable protection against downloading and running additional payloads from the Office VBA macros as additional child processes.
You need to identify which Office VBA macros might be affected.
Which two commands can you run to achieve the goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Your company uses Microsoft Defender for Endpoint.
The company has Microsoft Word documents that contain macros. The documents are used frequently on the devices of the company’s accounting team.
You need to hide false positive in the Alerts queue, while maintaining the existing security posture.
Which three actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Resolve the alert automatically.
- B . Hide the alert.
- C . Create a suppression rule scoped to any device.
- D . Create a suppression rule scoped to a device group.
- E . Generate the alert.
DRAG DROP
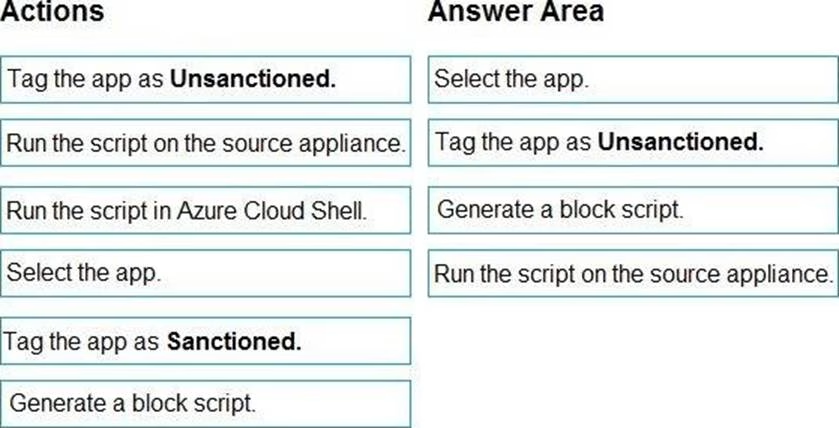
You open the Cloud App Security portal as shown in the following exhibit.
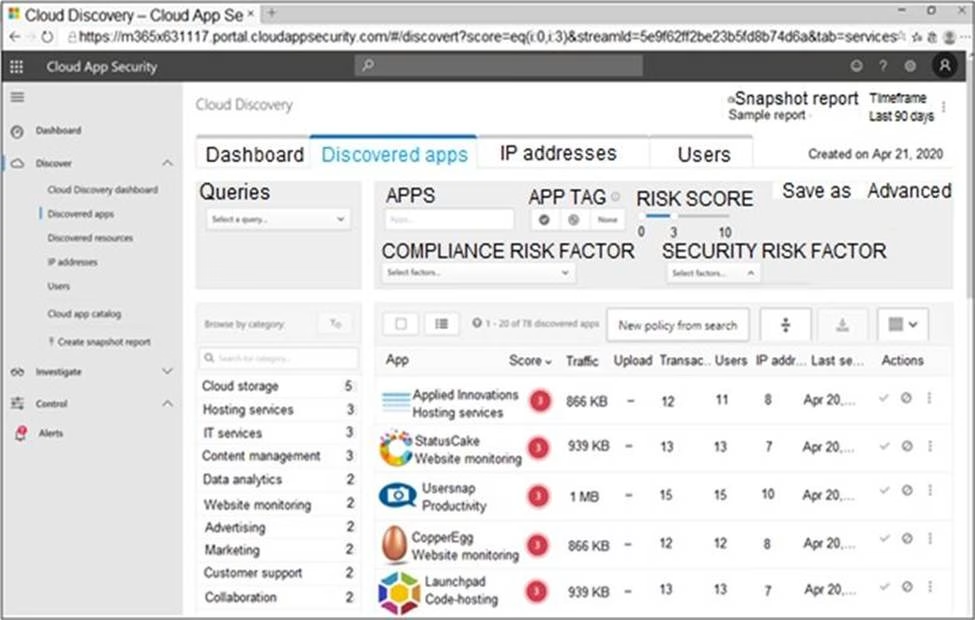
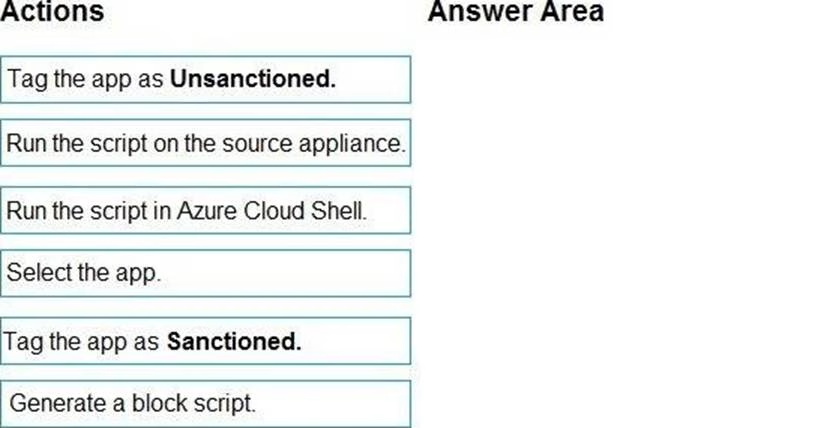
You need to remediate the risk for the Launchpad app.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Latest SC-200 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund