Microsoft SC-200 Microsoft Security Operations Analyst Online Training
Microsoft SC-200 Online Training
The questions for SC-200 were last updated at Feb 20,2026.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Feb 20,2026
You create a custom analytics rule to detect threats in Azure Sentinel.
You discover that the rule fails intermittently.
What are two possible causes of the failures? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . The rule query takes too long to run and times out.
- B . The target workspace was deleted.
- C . Permissions to the data sources of the rule query were modified.
- D . There are connectivity issues between the data sources and Log Analytics
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a scheduled query rule for a data connector.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a hunting bookmark.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a Microsoft incident creation rule for a data connector.
Does this meet the goal?
- A . Yes
- B . No
You need to configure Microsoft Cloud App Security to generate alerts and trigger remediation actions in response to external sharing of confidential files.
Which two actions should you perform in the Cloud App Security portal? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . From Settings, select Information Protection, select Azure Information Protection, and then select Only scan files for Azure Information Protection classification labels and content inspection warnings from this tenant
- B . Select Investigate files, and then filter App to Office 365.
- C . Select Investigate files, and then select New policy from search
- D . From Settings, select Information Protection, select Azure Information Protection, and then select Automatically scan new files for Azure Information Protection classification labels and content inspection warnings
- E . From Settings, select Information Protection, select Files, and then enable file monitoring.
- F . Select Investigate files, and then filter File Type to Document.
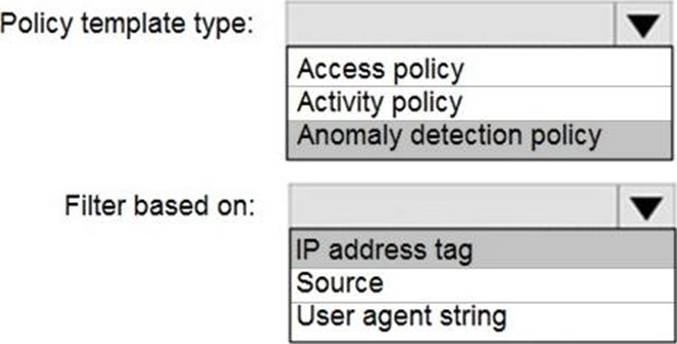
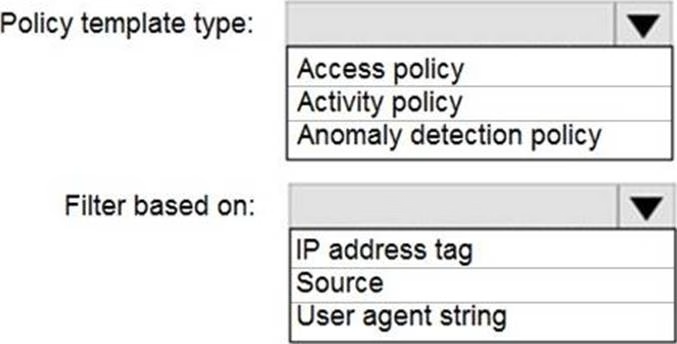
HOTSPOT
You purchase a Microsoft 365 subscription.
You plan to configure Microsoft Cloud App Security.
You need to create a custom template-based policy that detects connections to Microsoft 365 apps that originate from a botnet network.
What should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
What should you do?
- A . From Security alerts, select the alert, select Take Action, and then expand the Prevent future attacks section.
- B . From Security alerts, select Take Action, and then expand the Mitigate the threat section.
- C . From Regulatory compliance, download the report.
- D . From Recommendations, download the CSV report.
You have a suppression rule in Azure Security Center for 10 virtual machines that are used for testing.
The virtual machines run Windows Server.
You are troubleshooting an issue on the virtual machines.
In Security Center, you need to view the alerts generated by the virtual machines during the last five days.
What should you do?
- A . Change the rule expiration date of the suppression rule.
- B . Change the state of the suppression rule to Disabled.
- C . Modify the filter for the Security alerts page.
- D . View the Windows event logs on the virtual machines.
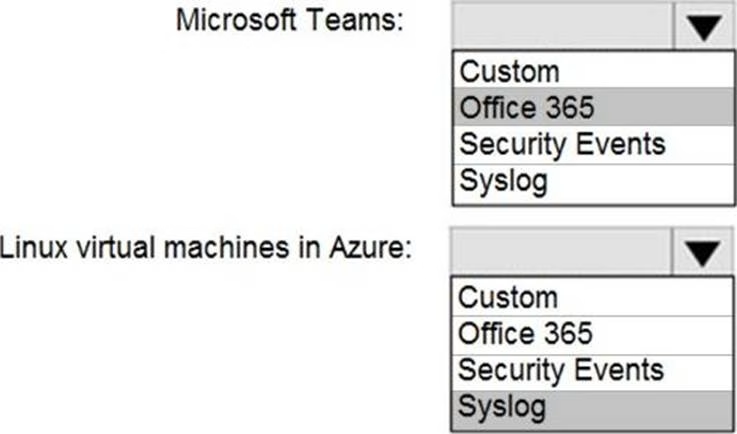
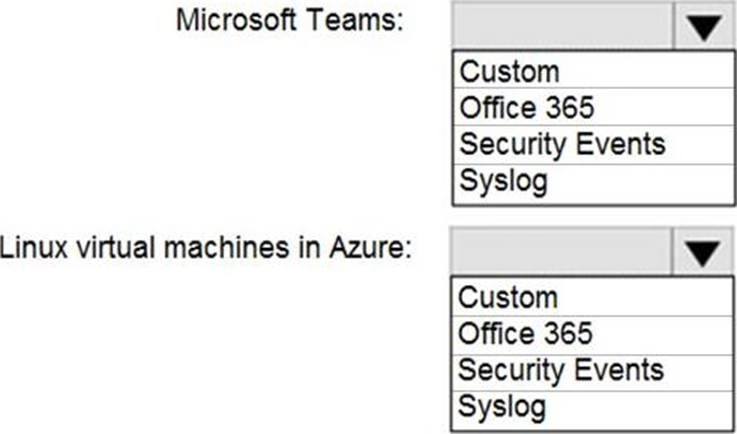
HOTSPOT
You deploy Azure Sentinel.
You need to implement connectors in Azure Sentinel to monitor Microsoft Teams and Linux virtual machines in Azure. The solution must minimize administrative effort.
Which data connector type should you use for each workload? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You are investigating an incident in Azure Sentinel that contains more than 127 alerts.
You discover eight alerts in the incident that require further investigation.
You need to escalate the alerts to another Azure Sentinel administrator.
What should you do to provide the alerts to the administrator?
- A . Create a Microsoft incident creation rule
- B . Share the incident URL
- C . Create a scheduled query rule
- D . Assign the incident
Latest SC-200 Dumps Valid Version with 75 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund