Microsoft SC-100 Microsoft Cybersecurity Architect Online Training
Microsoft SC-100 Online Training
The questions for SC-100 were last updated at Feb 21,2026.
- Exam Code: SC-100
- Exam Name: Microsoft Cybersecurity Architect
- Certification Provider: Microsoft
- Latest update: Feb 21,2026
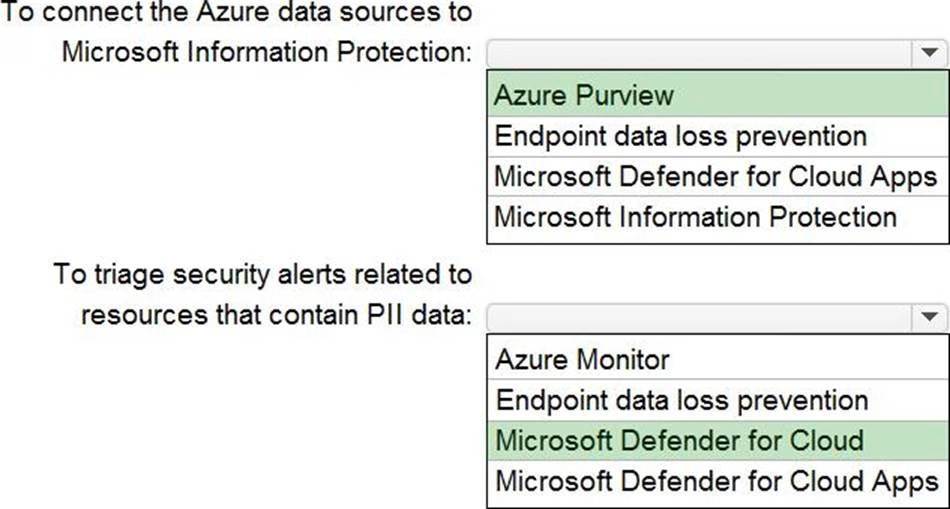
HOTSPOT
Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to recommend a solution to add a watermark to email attachments that contain sensitive data.
What should you include in the recommendation?
- A . Microsoft Defender for Cloud Apps
- B . insider risk management
- C . Microsoft Information Protection
- D . Azure Purview
Your company has a hybrid cloud infrastructure.
The company plans to hire several temporary employees within a brief period. The temporary employees will need to access applications and data on the company’ premises network.
The company’s security policy prevents the use of personal devices for accessing company data and applications.
You need to recommend a solution to provide the temporary employee with access to company resources. The solution must be able to scale on demand.
What should you include in the recommendation?
- A . Migrate the on-premises applications to cloud-based applications.
- B . Redesign the VPN infrastructure by adopting a split tunnel configuration.
- C . Deploy Microsoft Endpoint Manager and Azure Active Directory (Azure AD) Conditional Access.
- D . Deploy Azure Virtual Desktop, Azure Active Directory (Azure AD) Conditional Access, and Microsoft Defender for Cloud Apps.
You have an Azure subscription that contains virtual machines, storage accounts, and Azure SQL databases. All resources are backed up multiple times a day by using Azure Backup. You are developing a strategy to protect against ransomware attacks.
You need to recommend which controls must be enabled to ensure that Azure Backup can be used to restore the resources in the event of a successful ransomware attack.
Which two controls should you include in the recommendation? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Use Azure Monitor notifications when backup configurations change.
- B . Require PINs for critical operations.
- C . Perform offline backups to Azure Data Box.
- D . Encrypt backups by using customer-managed keys (CMKs).
- E . Enable soft delete for backups.
Your company develops several applications that are accessed as custom enterprise applications in Azure Active Directory (Azure AD). You need to recommend a solution to prevent users on a specific list of countries from connecting to the applications.
What should you include in the recommendation?
- A . activity policies in Microsoft Defender for Cloud Apps
- B . sign-in risk policies in Azure AD Identity Protection
- C . device compliance policies in Microsoft Endpoint Manager
- D . Azure AD Conditional Access policies
- E . user risk policies in Azure AD Identity Protection
Your company has a Microsoft 365 subscription and uses Microsoft Defender for Identity. You are informed about incidents that relate to compromised identities.
You need to recommend a solution to expose several accounts for attackers to exploit. When the attackers attempt to exploit the accounts, an alert must be triggered.
Which Defender for Identity feature should you include in the recommendation?
- A . standalone sensors
- B . honeytoken entity tags
- C . sensitivity labels
- D . custom user tags
You have a Microsoft 365 E5 subscription and an Azure subscription. You are designing a Microsoft Sentinel deployment.
You need to recommend a solution for the security operations team. The solution must include custom views and a dashboard for analyzing security events.
What should you recommend using in Microsoft Sentinel?
- A . playbooks
- B . workbooks
- C . notebooks
- D . threat intelligence
Your company has an on-premise network in Seattle and an Azure subscription. The on-premises network contains a Remote Desktop server.
The company contracts a third-party development firm from France to develop and deploy resources to the virtual machines hosted in the Azure subscription.
Currently, the firm establishes an RDP connection to the Remote Desktop server. From the Remote Desktop connection, the firm can access the virtual machines hosted in Azure by using custom administrative tools installed on the Remote Desktop server. All the traffic to the Remote Desktop server is captured by a firewall, and the firewall only allows specific connections from France to the server.
You need to recommend a modern security solution based on the Zero Trust model. The solution must minimize latency tor developers.
Which three actions should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Configure network security groups (NSGs) to allow access from only specific logical groupings of IP address ranges.
- B . Implement Azure Firewall to restrict host pool outbound access.
- C . Configure Azure Active Directory (Azure AD) Conditional Access with multi-factor authentication (MFA) and named locations.
- D . Migrate from the Remote Desktop server to Azure Virtual Desktop.
- E . Deploy a Remote Desktop server to an Azure region located in France.
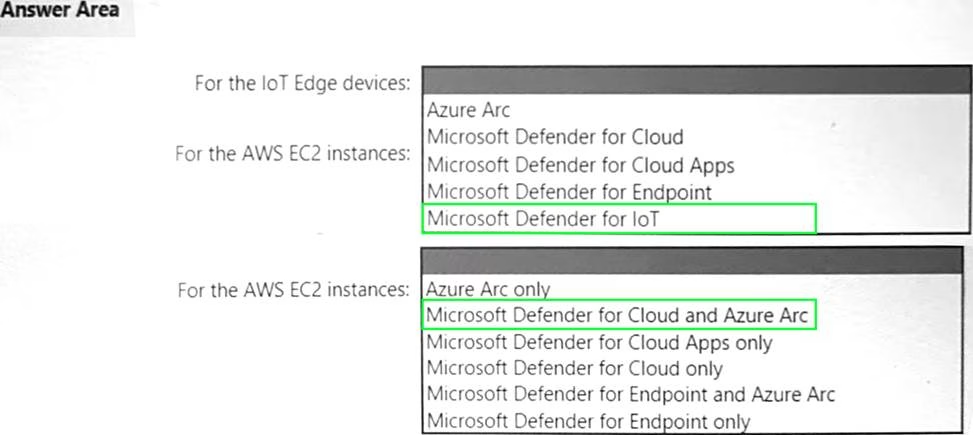
HOTSPOT
Your company has a multi-cloud environment that contains a Microsoft 365 subscription, an Azure subscription, and Amazon Web Services (AWS) implementation.
You need to recommend a security posture management solution for the following components:
• Azure loT Edge devices
• AWS EC2 instances
Which services should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company is moving all on-premises workloads to Azure and Microsoft 365.
You need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements:
• Minimizes manual intervention by security operation analysts
• Supports Waging alerts within Microsoft Teams channels
What should you include in the strategy?
- A . data connectors
- B . playbooks
- C . workbooks
- D . KQL
Latest SC-100 Dumps Valid Version with 105 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund