Microsoft SC-100 Microsoft Cybersecurity Architect Online Training
Microsoft SC-100 Online Training
The questions for SC-100 were last updated at Feb 20,2026.
- Exam Code: SC-100
- Exam Name: Microsoft Cybersecurity Architect
- Certification Provider: Microsoft
- Latest update: Feb 20,2026
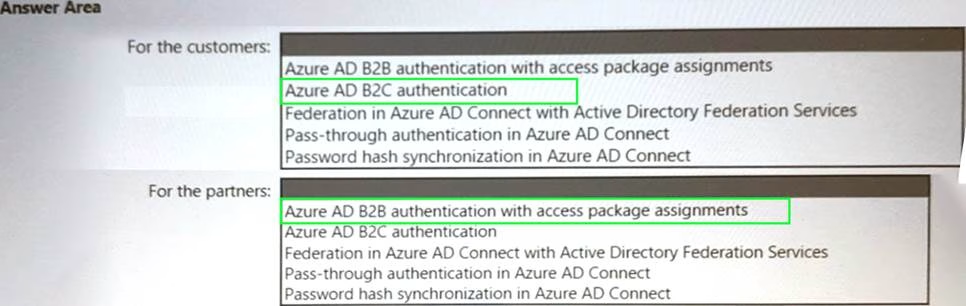
HOTSPOT
Your company has a Microsoft 365 E5 subscription, an Azure subscription, on-premises applications, and Active Directory Domain Services (AD DS).
You need to recommend an identity security strategy that meets the following requirements:
• Ensures that customers can use their Facebook credentials to authenticate to an Azure App Service website
• Ensures that partner companies can access Microsoft SharePoint Online sites for the project to which they are assigned
The solution must minimize the need to deploy additional infrastructure components.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls. Solution: You recommend enabling adaptive network hardening. Does this meet the goal?
- A . Yes
- B . No
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You are evaluating
the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points. You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend onboarding all virtual machines to Microsoft Defender for Endpoint.
Does this meet the goal?
- A . Yes
- B . No
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend configuring gateway-required virtual network integration.
Does this meet the goal?
- A . Yes
- B . No
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions to allow traffic from the backend IP address of the Front Door instance.
Does this meet the goal?
- A . Yes
- B . No
You are designing a security strategy for providing access to Azure App Service web apps through an Azure Front Door instance.
You need to recommend a solution to ensure that the web apps only allow access through the Front Door instance.
Solution: You recommend access restrictions that allow traffic from the Front Door service tags.
Does this meet the goal?
- A . Yes
- B . No
You are creating an application lifecycle management process based on the Microsoft Security Development Lifecycle (SDL).
You need to recommend a security standard for onboarding applications to Azure. The standard will include recommendations for application design, development, and deployment.
What should you include during the application design phase?
- A . static application security testing (SAST) by using SonarQube
- B . dynamic application security testing (DAST) by using Veracode
- C . threat modeling by using the Microsoft Threat Modeling Tool
- D . software decomposition by using Microsoft Visual Studio Enterprise
Your company is developing a new Azure App Service web app. You are providing design assistance to verify the security of the web app.
You need to recommend a solution to test the web app for vulnerabilities such as insecure server configurations, cross-site scripting (XSS), and SQL injection.
What should you include in the recommendation?
- A . interactive application security testing (IAST)
- B . static application security testing (SAST)
- C . runtime application se/f-protection (RASP)
- D . dynamic application security testing (DAST)
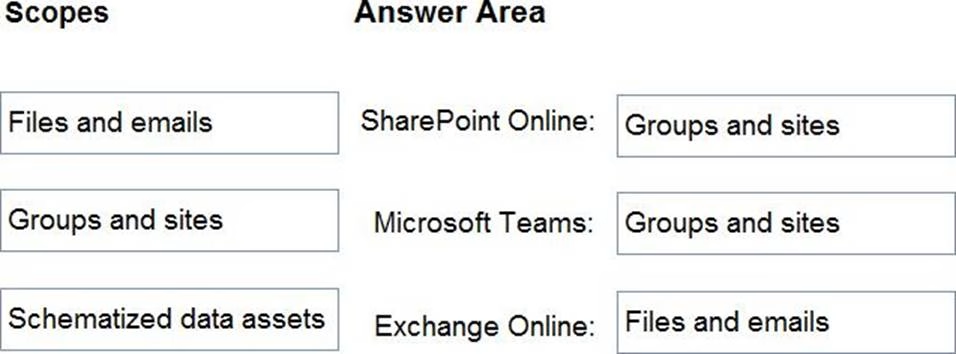
DRAG DROP
Your company has Microsoft 365 E5 licenses and Azure subscriptions.
The company plans to automatically label sensitive data stored in the following locations:
• Microsoft SharePoint Online
• Microsoft Exchange Online
• Microsoft Teams
You need to recommend a strategy to identify and protect sensitive data.
Which scope should you recommend for the sensitivity label policies? To answer, drag the appropriate scopes to the correct locations. Each scope may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
Your company plans to deploy several Azure App Service web apps. The web apps will be deployed to the West Europe Azure region. The web apps will be accessed only by customers in Europe and the United States.
You need to recommend a solution to prevent malicious bots from scanning the web apps for vulnerabilities. The solution must minimize the attach surface.
What should you include in the recommendation?
- A . Azure Firewall Premium
- B . Azure Application Gateway Web Application Firewall (WAF)
- C . network security groups (NSGs)
- D . Azure Traffic Manager and application security groups
Latest SC-100 Dumps Valid Version with 105 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund