Microsoft SC-100 Microsoft Cybersecurity Architect Online Training
Microsoft SC-100 Online Training
The questions for SC-100 were last updated at Feb 21,2026.
- Exam Code: SC-100
- Exam Name: Microsoft Cybersecurity Architect
- Certification Provider: Microsoft
- Latest update: Feb 21,2026
Your company has a Microsoft 365 E5 subscription.
Users use Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive for sharing and collaborating. The company identifies protected health information (PHI) within stored documents and communications.
What should you recommend using to prevent the PHI from being shared outside the company?
- A . insider risk management policies
- B . data loss prevention (DLP) policies
- C . sensitivity label policies
- D . retention policies
You are designing the security standards for containerized applications onboarded to Azure. You are evaluating the use of Microsoft Defender for Containers.
In which two environments can you use Defender for Containers to scan for known vulnerabilities? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Linux containers deployed to Azure Container Registry
- B . Linux containers deployed to Azure Kubernetes Service (AKS)
- C . Windows containers deployed to Azure Container Registry
- D . Windows containers deployed to Azure Kubernetes Service (AKS)
- E . Linux containers deployed to Azure Container Instances
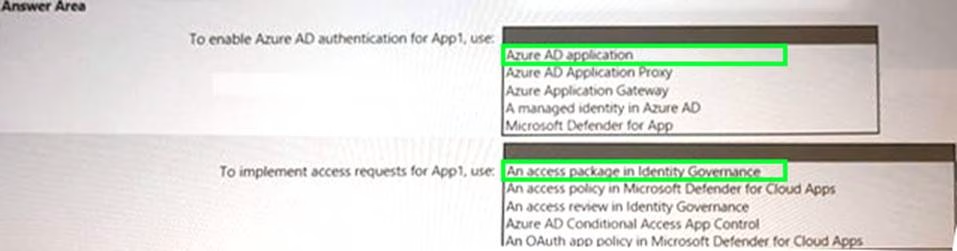
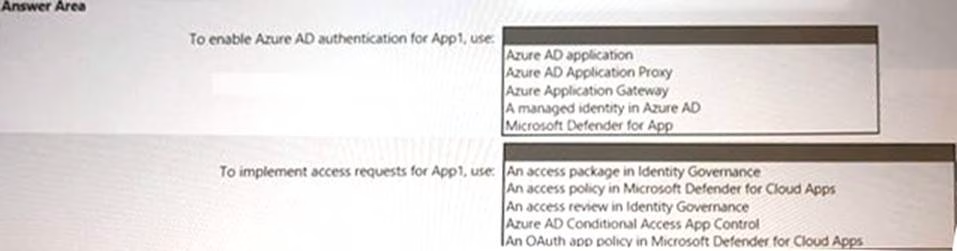
HOTSPOT
You are creating the security recommendations for an Azure App Service web app named App1.
App1 has the following specifications:
• Users will request access to App1 through the My Apps portal. A human resources manager will approve the requests.
• Users will authenticate by using Azure Active Directory (Azure AD) user accounts.
You need to recommend an access security architecture for App1.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has an on-premises network and an Azure subscription.
The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure.
You are designing the security standards for Azure App Service web apps. The web apps will access Microsoft SQL Server databases on the network.
You need to recommend security standards that will allow the web apps to access the databases. The solution must minimize the number of open internet-accessible endpoints to the on-premises network.
What should you include in the recommendation?
- A . a private endpoint
- B . hybrid connections
- C . virtual network NAT gateway integration
- D . virtual network integration
Your company has a hybrid cloud infrastructure that contains an on-premises Active Directory Domain Services (AD DS) forest, a Microsoft B65 subscription, and an Azure subscription.
The company’s on-premises network contains internal web apps that use Kerberos authentication.
Currently, the web apps are accessible only from the network.
You have remote users who have personal devices that run Windows 11.
You need to recommend a solution to provide the remote users with the ability to access the web apps. The solution must meet the following requirements:
• Prevent the remote users from accessing any other resources on the network.
• Support Azure Active Directory (Azure AD) Conditional Access.
• Simplify the end-user experience.
What should you include in the recommendation?
- A . Azure AD Application Proxy
- B . Azure Virtual WAN
- C . Microsoft Tunnel
- D . web content filtering in Microsoft Defender for Endpoint
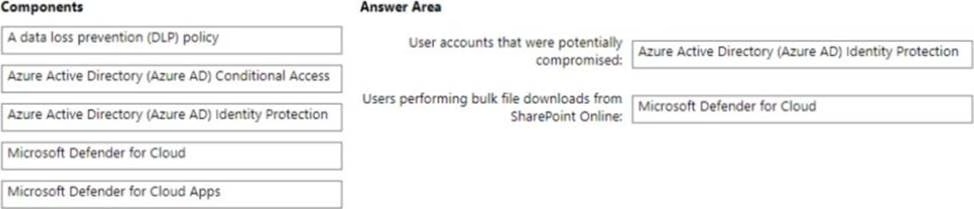
DRAG DROP
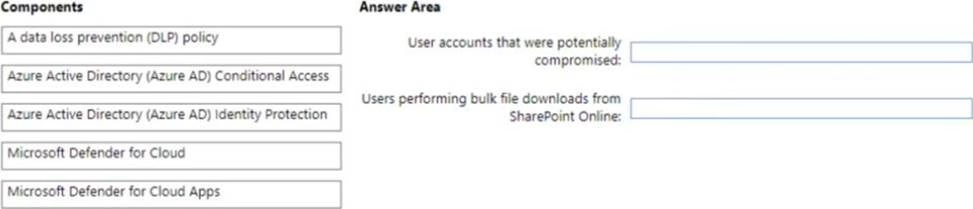
You have a Microsoft 365 subscription
You need to recommend a security solution to monitor the following activities:
• User accounts that were potentially compromised
• Users performing bulk file downloads from Microsoft SharePoint Online
What should you include in the recommendation for each activity? To answer, drag the appropriate components to the correct activities. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each Correct selection is worth one Point.
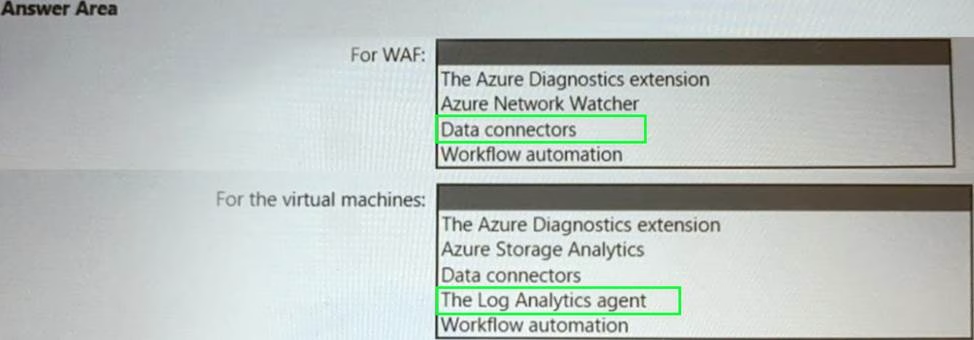
HOTSPOT
Your company uses Microsoft Defender for Cloud and Microsoft Sentinel.
The company is designing an application that will have the architecture shown in the following exhibit.
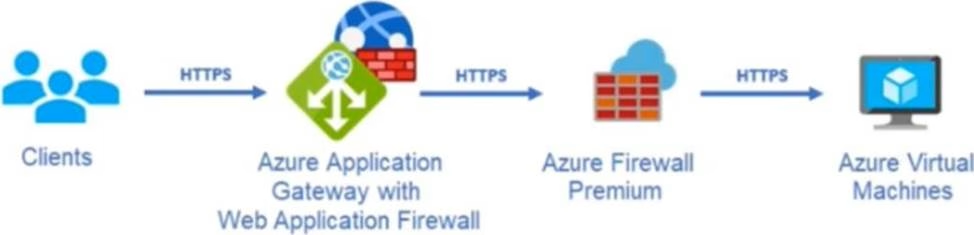
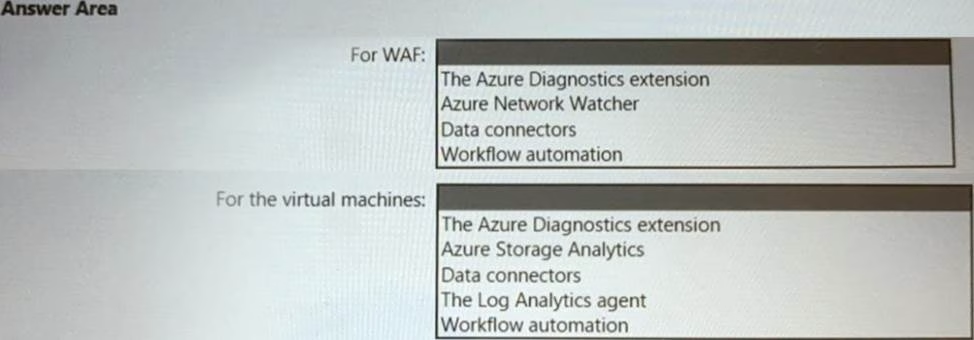
You are designing a logging and auditing solution for the proposed architecture.
The solution must meet the following requirements:
• Integrate Azure Web Application Firewall (WAF) logs with Microsoft Sentinel.
• Use Defender for Cloud to review alerts from the virtual machines.
What should you include in the solution? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Your company has a third-party security information and event management (SIEM) solution that uses Splunk and Microsoft Sentinel. You plan to integrate Microsoft Sentinel with Splunk.
You need to recommend a solution to send security events from Microsoft Sentinel to Splunk.
What should you include in the recommendation?
- A . Azure Event Hubs
- B . Azure Data Factor
- C . a Microsoft Sentinel workbook
- D . a Microsoft Sentinel data connector
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon
Web Services (AWS) implementation.
You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc.
Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
- A . Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
- B . Azure Active Directory (Azure AD) Conditional Access
- C . Microsoft Defender for servers
- D . Azure Policy
- E . Microsoft Defender for Containers
You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service. You are migrating the on-premises infrastructure to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy applications. The solution must minimize the administrative effort to maintain the infrastructure.
Which identity service should you include in the recommendation?
- A . Azure Active Directory Domain Services (Azure AD DS)
- B . Azure Active Directory (Azure AD) B2C
- C . Azure Active Directory (Azure AD)
- D . Active Directory Domain Services (AD DS)
Latest SC-100 Dumps Valid Version with 105 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund