Microsoft SC-100 Microsoft Cybersecurity Architect Online Training
Microsoft SC-100 Online Training
The questions for SC-100 were last updated at Feb 21,2026.
- Exam Code: SC-100
- Exam Name: Microsoft Cybersecurity Architect
- Certification Provider: Microsoft
- Latest update: Feb 21,2026
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You need to enforce ISO 2700V2013 standards for the subscription. The solution must ensure that noncompliant resources are remediated automatically
What should you use?
- A . the regulatory compliance dashboard in Defender for Cloud
- B . Azure Policy
- C . Azure Blueprints
- D . Azure role-based access control (Azure RBAC)
You receive a security alert in Microsoft Defender for Cloud as shown in the exhibit. (Click the Exhibit tab.)
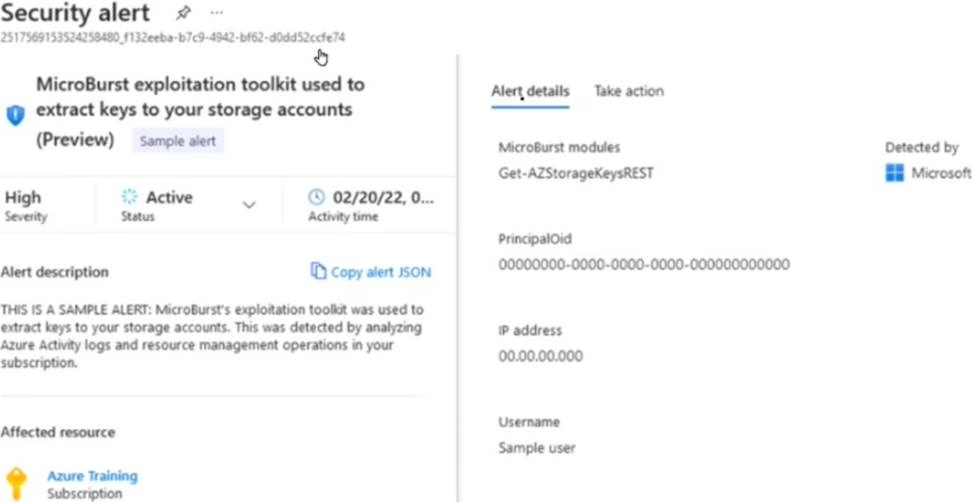
After remediating the threat which policy definition should you assign to prevent the threat from reoccurring?
- A . Storage account public access should be disallowed
- B . Azure Key Vault Managed HSM should have purge protection enabled
- C . Storage accounts should prevent shared key access
- D . Storage account keys should not be expired
Your company is preparing for cloud adoption.
You are designing security for Azure landing zones.
Which two preventative controls can you implement to increase the secure score? Each NOTE: Each correct selection is worth one point.
- A . Azure Firewall
- B . Azure Web Application Firewall (WAF)
- C . Microsoft Defender for Cloud alerts
- D . Azure Active Directory (Azure AD Privileged Identity Management (PIM)
- E . Microsoft Sentinel
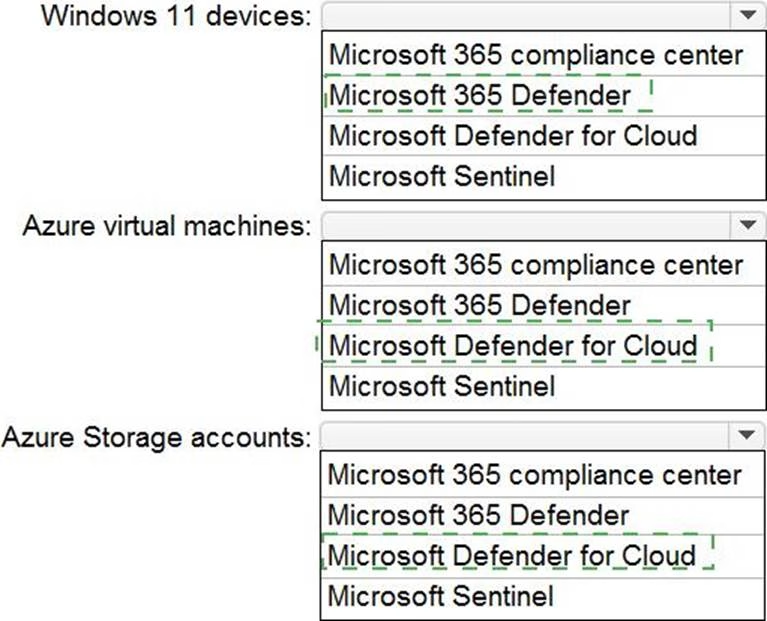
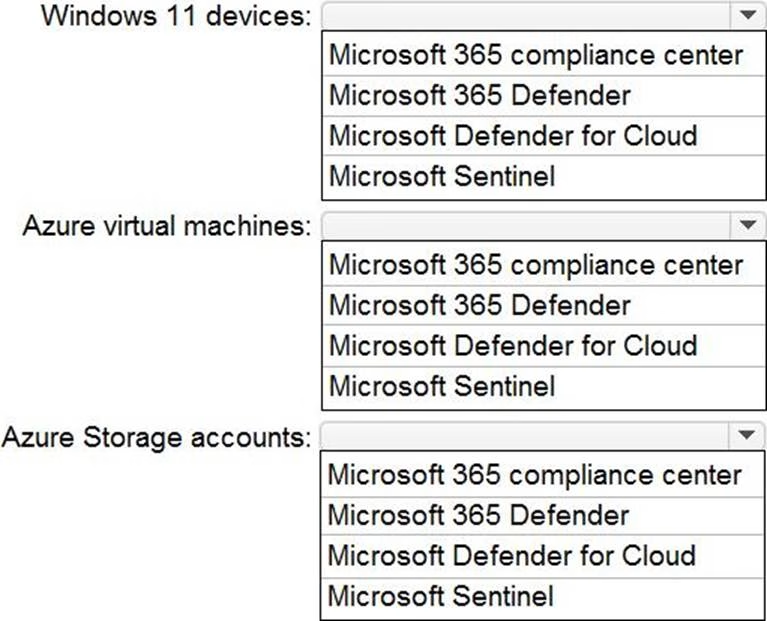
HOTSPOT
You have a Microsoft 365 E5 subscription and an Azure subscripts.
You need to evaluate the existing environment to increase the overall security posture for the following components:
• Windows 11 devices managed by Microsoft Intune
• Azure Storage accounts
• Azure virtual machines
What should you use to evaluate the components? To answer, select the appropriate options in the answer area.
You are designing security for an Azure landing zone.
Your company identifies the following compliance and privacy requirements:
• Encrypt cardholder data by using encryption keys managed by the company.
• Encrypt insurance claim files by using encryption keys hosted on-premises.
Which two configurations meet the compliance and privacy requirements? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Store the insurance claim data in Azure Blob storage encrypted by using customer-provided keys.
- B . Store the cardholder data in an Azure SQL database that is encrypted by using keys stored in Azure Key Vault Managed HSM
- C . Store the insurance claim data in Azure Files encrypted by using Azure Key Vault Managed HSM.
- D . Store the cardholder data in an Azure SQL database that is encrypted by using Microsoft-managed Keys.
Your company finalizes the adoption of Azure and is implementing Microsoft Defender for Cloud.
You receive the following recommendations in Defender for Cloud
• Access to storage accounts with firewall and virtual network configurations should be restricted,
• Storage accounts should restrict network access using virtual network rules.
• Storage account should use a private link connection.
• Storage account public access should be disallowed.
You need to recommend a service to mitigate identified risks that relate to the recommendations.
What should you recommend?
- A . Azure Storage Analytics
- B . Azure Network Watcher
- C . Microsoft Sentinel
- D . Azure Policy
You have 50 Azure subscriptions.
You need to monitor resource in the subscriptions for compliance with the ISO 27001:2013 standards.
The solution must minimize the effort required to modify the list of monitored policy definitions for the subscriptions. NOTE: Each correct selection is worth one point.
- A . Assign an initiative to a management group.
- B . Assign a policy to each subscription.
- C . Assign a policy to a management group.
- D . Assign an initiative to each subscription.
- E . Assign a blueprint to each subscription.
- F . Assign a blueprint to a management group.
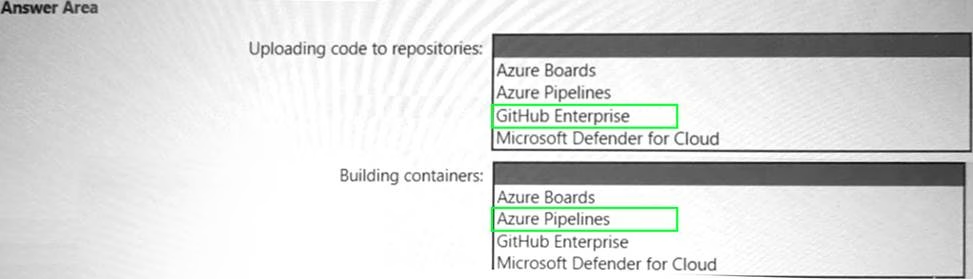
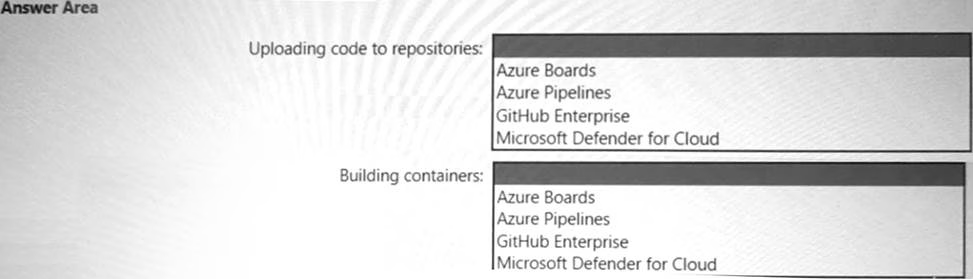
HOTSPOT
Your company has an Azure App Service plan that is used to deploy containerized web apps. You are designing a secure DevOps strategy for deploying the web apps to the App Service plan. You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle. The code must be scanned during the following two phases: Uploading the code to repositories Building containers
Where should you integrate code scanning for each phase? To answer, select the appropriate options in the answer area.
Your company has a Microsoft 365 E5 subscription. The company wants to identify and classify data in Microsoft Teams, SharePoint Online, and Exchange Online. You need to recommend a solution to identify documents that contain sensitive information.
What should you include in the recommendation?
- A . data classification content explorer
- B . data loss prevention (DLP)
- C . eDiscovery
- D . Information Governance
Your company is developing an invoicing application that will use Azure Active Directory (Azure AD) B2C. The application will be deployed as an App Service web app. You need to recommend a solution to the application development team to secure the application from identity related attacks.
Which two configurations should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Azure AD Conditional Access integration with user flows and custom policies
- B . Azure AD workbooks to monitor risk detections
- C . custom resource owner password credentials (ROPC) flows in Azure AD B2C
- D . access packages in Identity Governance
- E . smart account lockout in Azure AD B2C
Latest SC-100 Dumps Valid Version with 105 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund