Microsoft SC-100 Microsoft Cybersecurity Architect Online Training
Microsoft SC-100 Online Training
The questions for SC-100 were last updated at Feb 20,2026.
- Exam Code: SC-100
- Exam Name: Microsoft Cybersecurity Architect
- Certification Provider: Microsoft
- Latest update: Feb 20,2026
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
- A . Azure AD Conditional Access
- B . Microsoft Defender for Cloud Apps
- C . Microsoft Defender for Cloud
- D . Microsoft Defender for Endpoint
- E . access reviews in Azure AD
Topic 3, Mix Questions
Your company has on-premises Microsoft SQL Server databases.
The company plans to move the databases to Azure.
You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs.
What should you include in the recommendation?
- A . Azure SQL Managed Instance
- B . Azure Synapse Analytics dedicated SQL pools
- C . Azure SQL Database
- D . SQL Server on Azure Virtual Machines
You have an Azure subscription that contains several storage accounts. The storage accounts are accessed by legacy applications that are authenticated by using access keys.
You need to recommend a solution to prevent new applications from obtaining the access keys of the storage accounts. The solution must minimize the impact on the legacy applications.
What should you include in the recommendation?
- A . Apply read-only locks on the storage accounts.
- B . Set the AllowSharcdKeyAccess property to false.
- C . Set the AllowBlobPublicAcccss property to false.
- D . Configure automated key rotation.
Azure subscription that uses Azure Storage.
The company plans to share specific blobs with vendors. You need to recommend a solution to provide the vendors with secure access to specific blobs without exposing the blobs publicly. The access must be tme-Vimted.
What should you include in the recommendation?
- A . Create shared access signatures (SAS).
- B . Share the connection string of the access key.
- C . Configure private link connections.
- D . Configure encryption by using customer-managed keys (CMKs)
You are planning the security requirements for Azure Cosmos DB Core (SQL) API accounts. You need to recommend a solution to audit all users that access the data in the Azure Cosmos DB accounts.
Which two configurations should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Enable Microsoft Defender for Cosmos DB.
- B . Send the Azure Active Directory (Azure AD) sign-in logs to a Log Analytics workspace.
- C . Disable local authentication for Azure Cosmos DB.
- D . Enable Microsoft Defender for Identity.
- E . Send the Azure Cosmos DB logs to a Log Analytics workspace.
You need to design a solution to provide administrators with secure remote access to the virtual machines.
The solution must meet the following requirements:
• Prevent the need to enable ports 3389 and 22 from the internet.
• Only provide permission to connect the virtual machines when required.
• Ensure that administrators use the Azure portal to connect to the virtual machines.
Which two actions should you include in the solution? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Enable Azure Active Directory (Azure AD) Privileged Identity Management (PIM) roles as virtual machine contributors.
- B . Configure Azure VPN Gateway.
- C . Enable Just Enough Administration (JEA).
- D . Enable just-in-time (JIT) VM access.
- E . Configure Azure Bastion.
Your company is designing an application architecture for Azure App Service Environment (ASE) web apps as shown in the exhibit. (Click the Exhibit tab.)
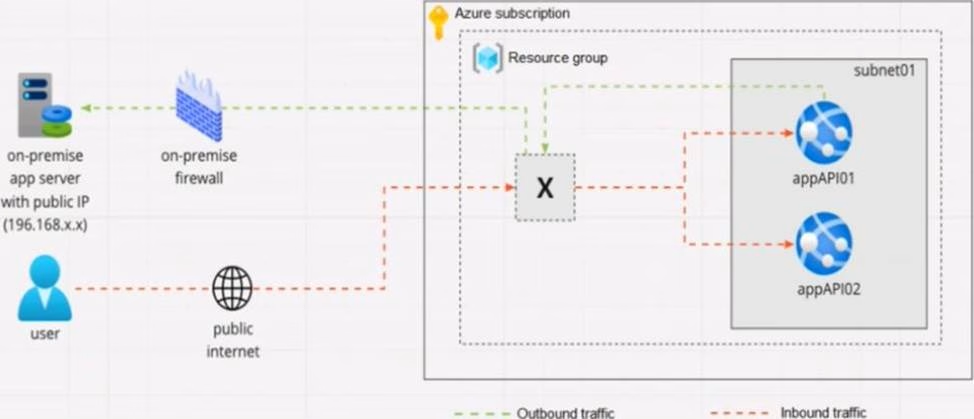
Communication between the on-premises network and Azure uses an ExpressRoute connection.
You need to recommend a solution to ensure that the web apps can communicate with the on-premises application server. The solution must minimize the number of public IP addresses that are allowed to access the on-premises network.
What should you include in the recommendation?
- A . Azure Traffic Manager with priority traffic-routing methods
- B . Azure Application Gateway v2 with user-defined routes (UDRs).
- C . Azure Front Door with Azure Web Application Firewall (WAF)
- D . Azure Firewall with policy rule sets
You have Windows 11 devices and Microsoft 365 E5 licenses.
You need to recommend a solution to prevent users from accessing websites that contain adult content such as gambling sites.
What should you include in the recommendation?
- A . Microsoft Endpoint Manager
- B . Compliance Manager
- C . Microsoft Defender for Cloud Apps
- D . Microsoft Defender for Endpoint
Your company plans to move all on-premises virtual machines to Azure.
A network engineer proposes the Azure virtual network design shown in the following table.
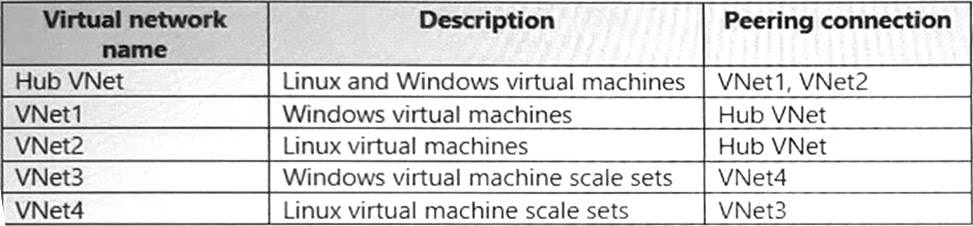
You need to recommend an Azure Bastion deployment to provide secure remote access to all the virtual machines.
Based on the virtual network design, how many Azure Bastion subnets are required?
- A . 1
- B . 2
- C . 3
- D . 4
- E . 5
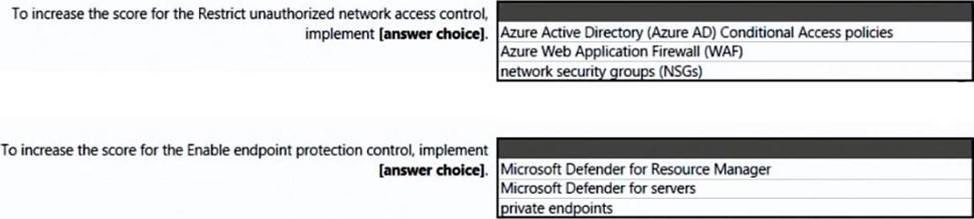
HOTSPOT
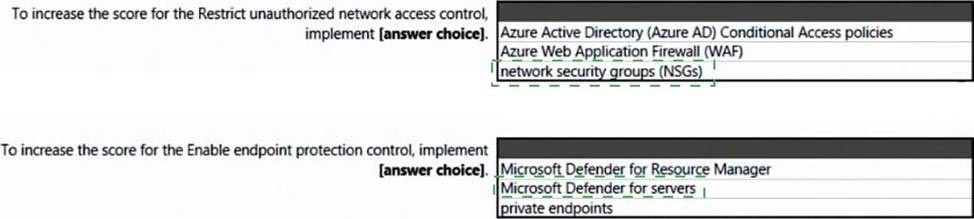
You open Microsoft Defender for Cloud as shown in the following exhibit.
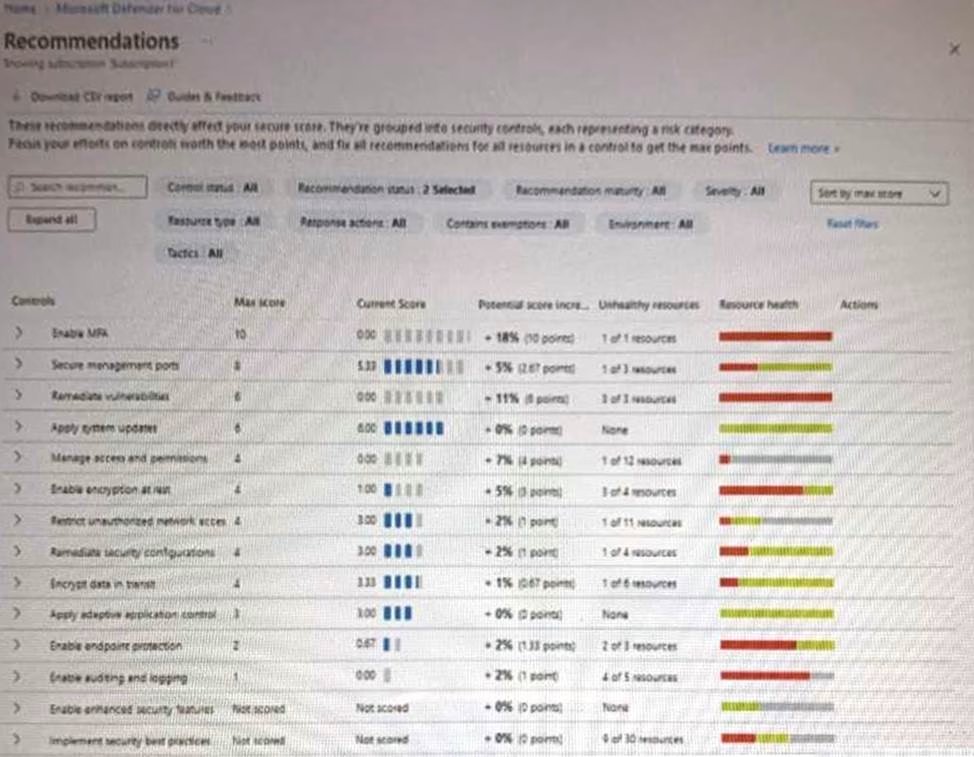
Use the drop-down menus to select the answer choice that complete each statements based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Latest SC-100 Dumps Valid Version with 105 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund