Microsoft MS-900 Microsoft 365 Fundamentals Online Training
Microsoft MS-900 Online Training
The questions for MS-900 were last updated at Feb 26,2026.
- Exam Code: MS-900
- Exam Name: Microsoft 365 Fundamentals
- Certification Provider: Microsoft
- Latest update: Feb 26,2026
A company has a Microsoft 365 subscription. Employees use personal devices to access company data in the cloud.
You need to restrict employees from copying data to personal OneDrive folders.
What should you use?
- A . Information Rights Management
- B . Microsoft Azure Security Center
- C . Office 365 Advanced Threat Protection
- D . Intune App Protection
This question requires that you evaluate the bold text to determine if it is correct.
You use Microsoft Intune for device management. You must determine how many devices run each operating system.
You must launch Intune and navigate to the Mobile Apps blade.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed” if the underlined text makes the statement correct.
- A . Device configuration
- B . Device compliance
- C . No change is needed
- D . Devices
You are the Microsoft 365 administrator for a company.You need to ensure that users receive a warning message if they select links in emails that might be unsafe.
What should you do?
- A . Use Windows PowerShell to install the latest antimalware engine updates
- B . Enable Microsoft Office 365 Advanced Threat Protection
- C . Use the Microsoft Exchange Admin Center to configure a new spam-filter policy
- D . Use the Microsoft Exchange Admin Center to create a new antimalware policy
You are a Microsoft 365 administrator for a company. Employees use Microsoft Office 365 ProPlus to create documents.
You need to implement document classification and protection by using Microsoft Azure Information Protection.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point. NOTE: Each correct selection is worth one point.
- A . Add an Azure subscription to your Microsoft 365 tenant
- B . Install the Azure Information Protection client
- C . Create a custom Azure Information Protection policy with the Confidential label
- D . Enable the default Azure Information Protection policy
- E . Install the Rights Management Service client
A company deploys Microsoft Azure AD. You enable multi-factor authentication.
You need to inform users about the multi-factor authentication methods that they can use.
Which of the following methods is NOT a valid multi-factor authentication method in Microsoft 365?
- A . Receive an automated call on the desk phone that includes a verification code
- B . Insert a small card in to a desktop computer and provide a PIN code when prompted
- C . Receive a call on a mobile phone and select the pound sign (#) when prompted
- D . Receive an SMS text message that includes a verification code
You are a Microsoft 365 administrator for a company.
Several users report that they receive emails which have a PDF attachment. The PDF attachment launches malicious code.
You need to remove the message from inboxes and disable the PDF threat if an affected document is opened.
Which feature should you implement?
- A . Microsoft Exchange Admin Center block lists
- B . Sender Policy Framework
- C . Advanced Threat Protection anti-phishing
- D . zero-hour auto purge
- E . DKIM signed messages with mail flow rules
DRAG DROP
You are a Microsoft 365 administrator for a company.
A customer submits a data subject request (DSR) to delete customer information in compliance with General Data Protection Regulation (GDPR). You must place legal holds on related data whenever possible.
You need to respond to the request by searching for the customer’s data in various Microsoft 365 tools.
How should you search for the data? To answer, drag the appropriate search methods to the correct Microsoft 365 applications. Each search method may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.

HOTSPOT
A company deploys Microsoft Intune.
An employee loses a Windows 10 device that contains corporate data.
You need to ensure that the corporate data on the device is secured as quickly as possible.
Which four options can you use? To answer, select the appropriate actions in the answer area. NOTE: Each correct selection is worth one point.
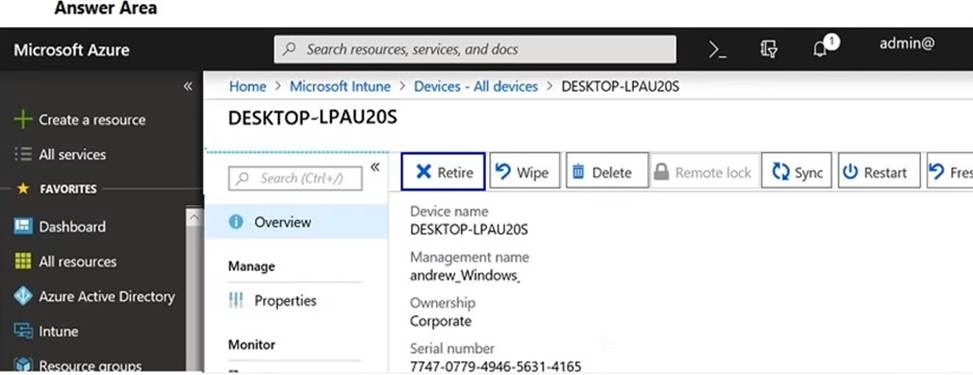
You are the Microsoft 365 administrator for a company.
All staff must use Microsoft Outlook to access corporate email. When users access Outlook on mobile devices, they must use a PIN to open the application.
You need to implement a Microsoft Intune policy to enforce the security requirements.
Which policy should you use?
- A . device compliance
- B . device configuration
- C . app protection
- D . app configuration
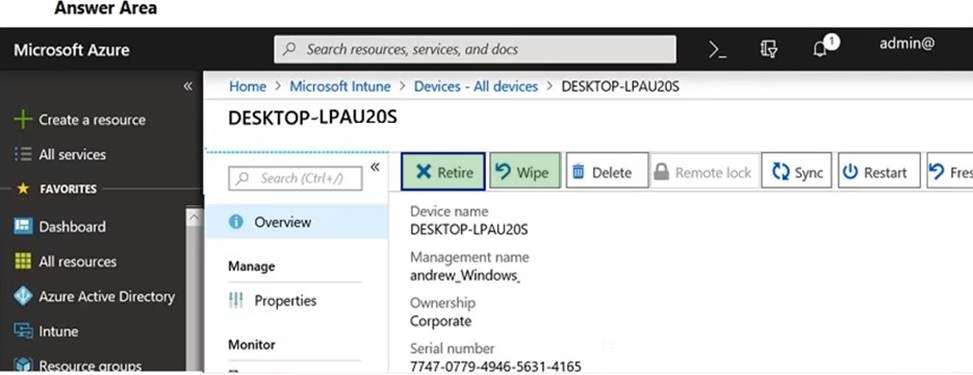
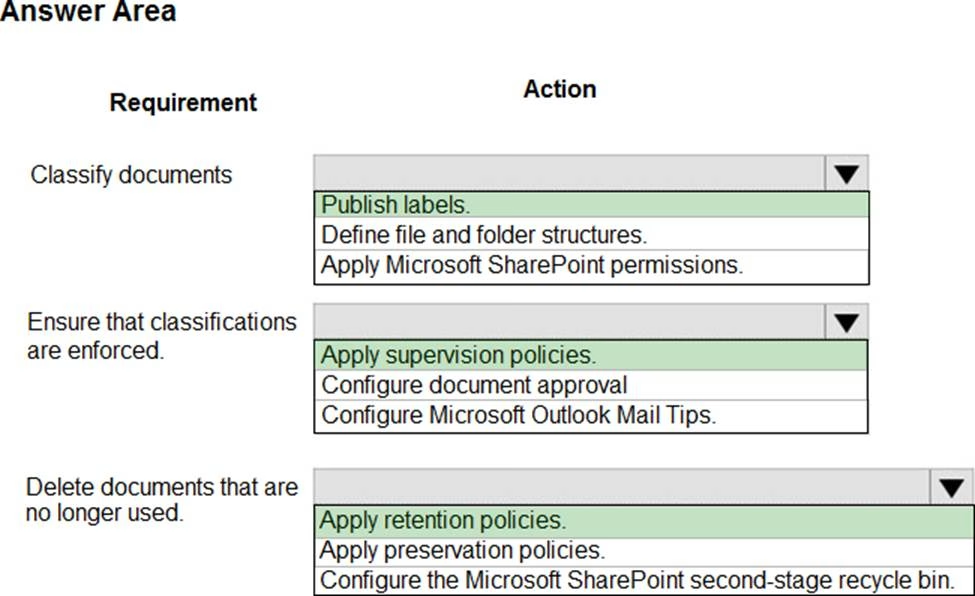
HOTSPOT
You need to configure a data governance solution for your company.
The solution must meet the following requirements:
✑ Classify documents
✑ Ensure that classifications are enforced
✑ Delete documents that are no longer used
Which actions should you perform? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Latest MS-900 Dumps Valid Version with 202 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund



Many questions was doubled.