Microsoft MS-500 Microsoft 365 Security Administration Online Training
Microsoft MS-500 Online Training
The questions for MS-500 were last updated at Feb 22,2026.
- Exam Code: MS-500
- Exam Name: Microsoft 365 Security Administration
- Certification Provider: Microsoft
- Latest update: Feb 22,2026
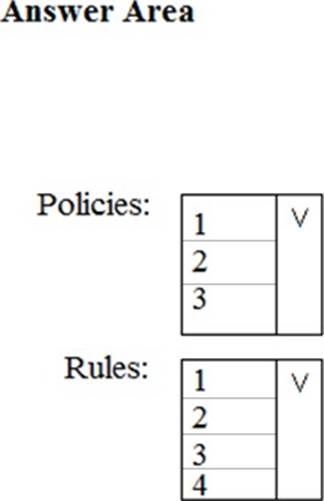
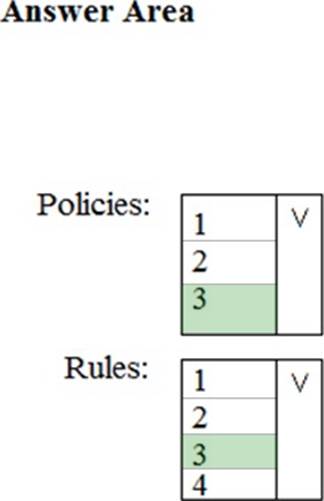
HOTSPOT
You have a Microsoft 365 subscription.
You identify the following data loss prevention (DLP) requirements:
✑ Send notifications to users if they attempt to send attachments that contain EU social security numbers
✑ Prevent any email messages that contain credit card numbers from being sent outside your organization
✑ Block the external sharing of Microsoft OneDrive content that contains EU passport numbers
✑ Send administrators email alerts if any rule matches occur.
What is the minimum number of DLP policies and rules you must create to meet the requirements? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
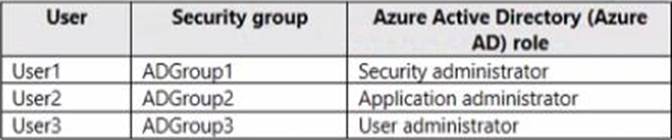
HOTSPOT
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
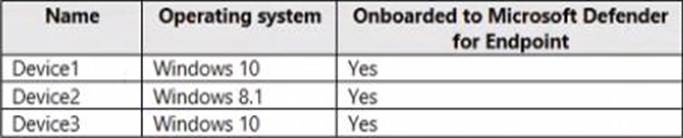
You have the devices shown in the following table.
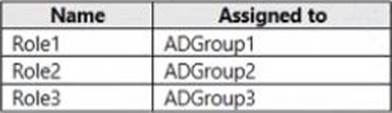
You have the Microsoft Defender for Endpoint portal roles shown in the following table.
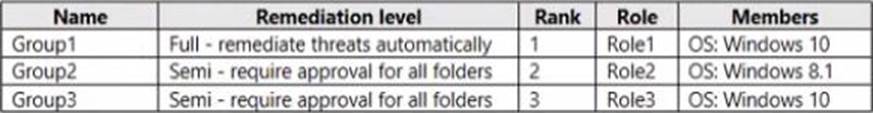
You have the Microsoft Defender for Endpoint device groups shown in the following table.
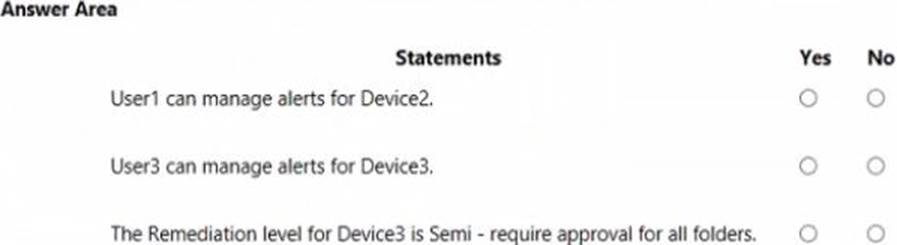
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
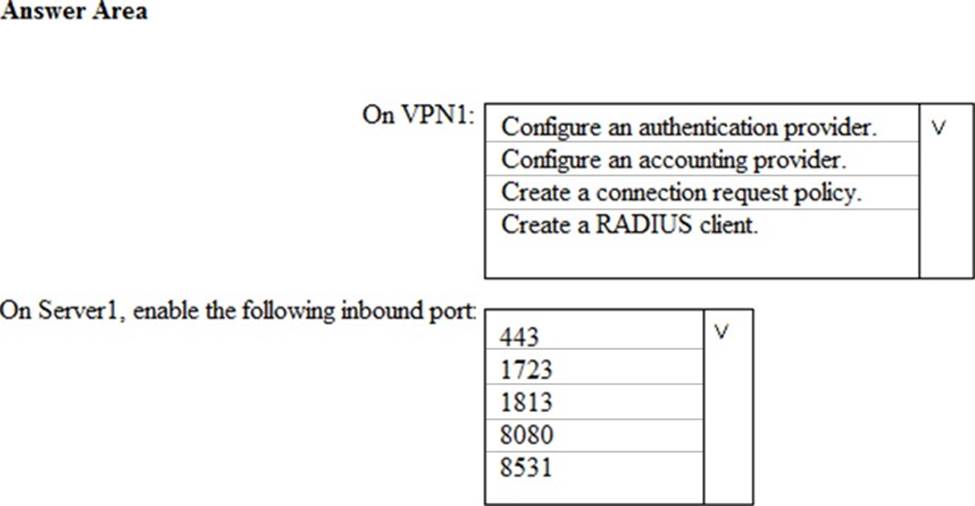
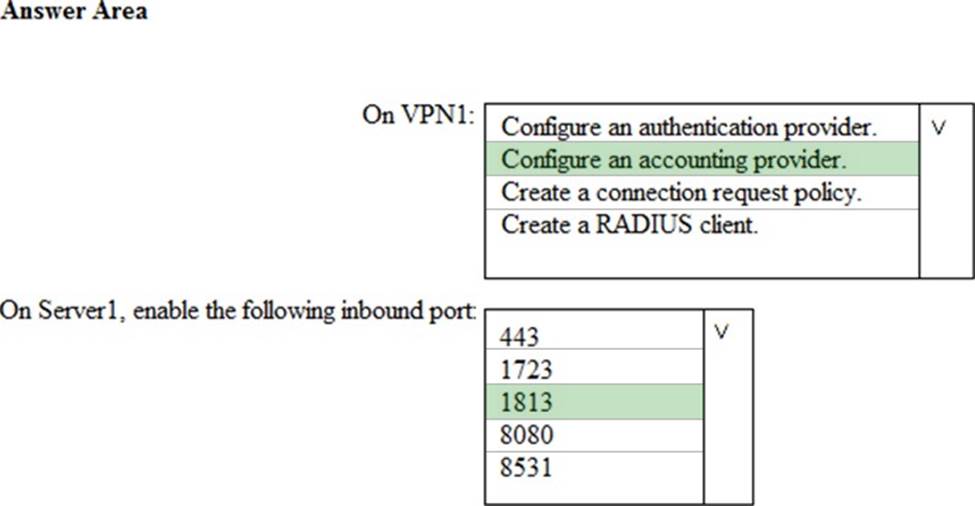
Your network contains an Active Directory domain named contoso.com. The domain contains a VPN server named VPN1 that runs Windows Server 2016 and has the Remote Access server role installed.
You have a Microsoft Azure subscription.
You are deploying Azure Advanced Threat Protection (ATP)
You install an Azure ATP standalone sensor on a server named Server1 that runs Windows Server 2016.
You need to integrate the VPN and Azure ATP.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
Your company uses Jamf Pro to manage macOS devices.
You plan to create device compliance policies for the macOS devices based on the Jamf Pro data.
You need to connect Microsoft Endpoint Manager to Jamf Pro.
What should you do first?
- A . From the Azure Active Directory admin center, add a Mobility (MDM and MAM) application.
- B . From the Endpoint Management admin center, add the Mobile Threat Defense connector.
- C . From the Endpoint Management admin center, configure Partner device management.
- D . From the Azure Active Directory admin center, register an application.
D
Explanation:
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/conditional-access-integrate-jamf
You have Microsoft 365subscription.
You need to be notified by email whenever an administrator starts an ediscovery search
What should you do from the Security & Compliance admin center?
- A . Prom Alerts, create an alert policy.
- B . From Search & investigation, create a guided search.
- C . From ediscovery orate an eDiscovery case
- D . From Reports, create a managed schedule
You have a Microsoft 365 E5 subscription that contains 500 Windows 10 devices. The subscription uses Microsoft Defender for Endpoint and is integrated with Microsoft Endpoint Manager. AJI the devices have Defender for Endpoint deployed.
You create a Conditional Access policy as shown in the following table.
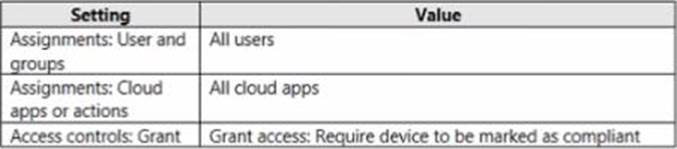
You need to ensure that devices that have a machine risk score of high are blocked.
What should you do in Microsoft Endpoint Manager?
- A . Apply a security baseline to all the devices.
- B . Apply an endpoint detection and response policy to the subscription.
- C . Configure the Compliance policy settings.
- D . Apply a compliance policy to all the devices.
You have a Microsoft 365 E5 subscription.
You need to investigate threats to the subscription by using the Campaigns view in Microsoft Defender for Office 365.
Which types of threats will appear?
- A . phishing and password attacks only
- B . malware and password attacks only
- C . malware only
- D . phishing only
- E . phishing and malware only
E
Explanation:
According to the article “Campaigns in Microsoft Defender for Office 365 Plan” 1, campaigns in the Microsoft 365 Defender portal identifies and categorizes coordinated email attacks, including phishing and malware 1. The article “Track and respond to emerging threats with campaigns in Microsoft Defender for Office 365” 2 also confirms that campaigns allow you to investigate a coordinated email attack against your organization that involves phishing and malware 2. The article “Microsoft Defender for Office 365 service description” 3 lists the features of Defender for Office 365 Plan 2, which include anti-phishing and anti-malware protection 3. Password attacks are not mentioned as a type of threat that will appear in the Campaigns view.
CORRECT TEXT
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@[email protected]
Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support only:
Lab instance: 11032396
You need to ensure that each user can join up to five devices to Azure Active Directory (Azure AD).
To complete this task, sign in to the Microsoft Office 365 admin center.
✑ Navigate to Device Settings.
✑ Set the Users may join devices to Azure AD setting to All.
✑ Set the Additional local administrators on Azure AD joined devices setting to None.
✑ Set the Users may register their devices with Azure AD setting to All.
✑ Leave the Require Multi-Factor Auth to join devices setting on it default setting.
✑ Set the Maximum number of devices setting to 5.
✑ Set the Users may sync settings and app data across devices setting to All.
✑ Click the Save button at the top left of the screen.
HOTSPOT
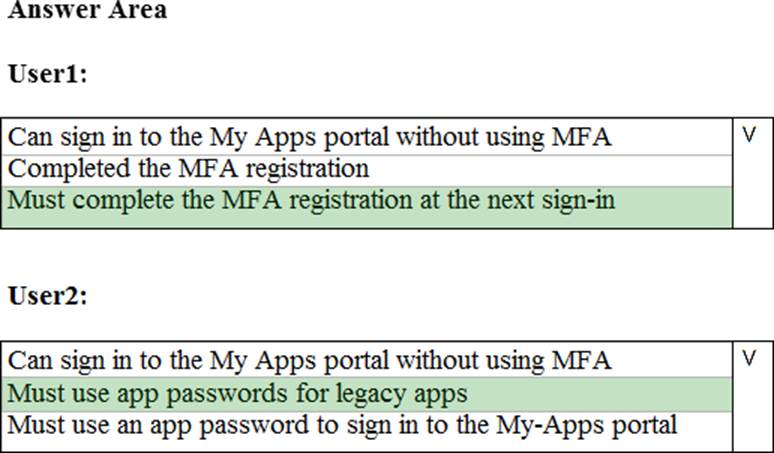
You have a Microsoft 365 subscription that uses a default domain name of contoso.com.
The multi-factor authentication (MFA) service settings are configured as shown in the exhibit. (Clock the Exhibit tab.)
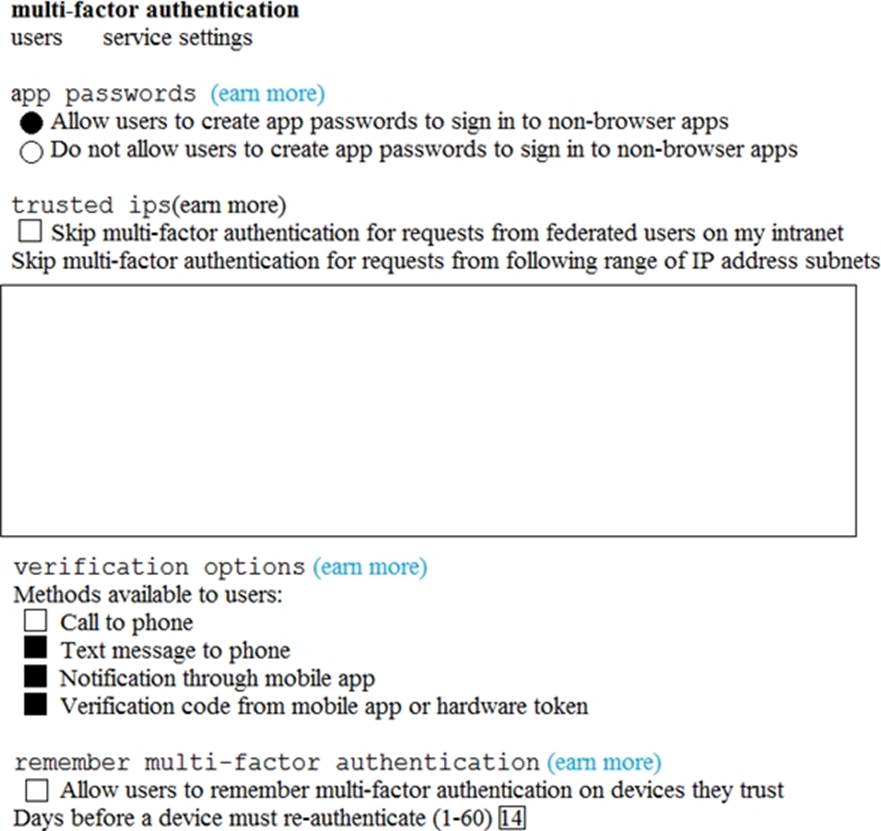
In contoso.com, you create the users shown in the following table.

What is the effect of the configuration? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that has Microsoft Defender for Cloud Apps enabled. You need to create an alert in Defender for Cloud Apps when source code is shared externally.
Which type of policy should you create?
- A . Cloud Discovery anomaly detection
- B . file
- C . access
- D . activity
Latest MS-500 Dumps Valid Version with 193 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


You know you need help when you are preparing for a hard exam like Microsoft 365 Security Administration. MS-500 Dumps PDF 2019 is the best source to get familiar with the latest exam patterns and terms. You can easily get a wide range of 2019 MS-500 Exam Questions at affordable rates from Testmayor. Check out the Free Demo to make sure the MS-500 Dumps are up to your demand. Get free 3-month updates with your purchase and a fabulous discount on using the coupon code.