Microsoft MS-500 Microsoft 365 Security Administration Online Training
Microsoft MS-500 Online Training
The questions for MS-500 were last updated at Feb 21,2026.
- Exam Code: MS-500
- Exam Name: Microsoft 365 Security Administration
- Certification Provider: Microsoft
- Latest update: Feb 21,2026
You have a Microsoft 365 E5 subscription that contains 1,000 Windows 10 devices. The devices are onboarded to Microsoft Defender for Endpoint.
You need to view a consolidated list of the common vulnerabilities and exposures (CVE) that affect the devices. The solution must minimize administrative effort.
Which Threat & Vulnerability Management page should you use?
- A . Software inventory
- B . Event timeline
- C . Weaknesses
- D . Security recommendations
C
Explanation:
Reference: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/tvm-weaknesses?view=o365-worldwide
You have a hybrid deployment of Azure Active Directory (Azure AD) that contains two users named User1 and User2.
You need to assign Role Based Access Control (RBAC) roles to User1 and User2 to meet the following requirements:
✑ Use the principle of least privilege
✑ Enable User1 to view sync errors by using Azure AD Connect Health
✑ Enable User2 to configure Azure Active Directory Connect Health Settings
Which two roles should you assign?
- A . The Monitoring Readers role in Azure AD Connect Health to User1
- B . The Security reader role in Azure AD to User 1
- C . The Reports reader role in Azure AD to User 1
- D . The Contributor role in Azure AD Connect Health to User 2
- E . The Monitoring Contributor role in Azure Connect Health to User 2
- F . The Security operator role in Azure AD to User2
CORRECT TEXT
Please wait while the virtual machine loads. Once loaded, you may proceed to the lab section. This may take a few minutes, and the wait time will not be deducted from your overall test time.
When the Next button is available, click it to access the lab section. In this section, you will perform a set of tasks in a live environment. While most functionality will be available to you as it would be in a live environment, some functionality (e.g., copy and paste, ability to navigate to external websites) will not be possible by design.
Scoring is based on the outcome of performing the tasks stated in the lab. In other words, it doesn’t matter how you accomplish the task, if you successfully perform it, you will earn credit for that task.
Labs are not timed separately, and this exam may more than one lab that you must complete. You can use as much time as you would like to complete each lab. But, you should manage your time appropriately to ensure that you are able to complete the lab(s) and all other sections of the exam in the time provided.
Please note that once you submit your work by clicking the Next button within a lab, you will NOT be able to return to the lab.
Username and password
Use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password, place your cursor in the Enter password box and click on the password below.
Microsoft 365 Username:
admin@[email protected]
Microsoft 365 Password: &=Q8v@2qGzYz
If the Microsoft 365 portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support only:
Lab instance: 11032396
You need to ensure that a user named Lee Gu can manage all the settings for Exchange
Online. The solution must use the principle of least privilege.
To complete this task, sign in to the Microsoft Office 365 admin center.
✑ Select the group: Organization Management and then click on Edit.
✑ In the Members section, click on Add.
✑ Select the users, USGs, or other role groups you want to add to the role group, click on Add, and then click on OK.
✑ Click on Save to save the changes to the role group.
HOTSPOT
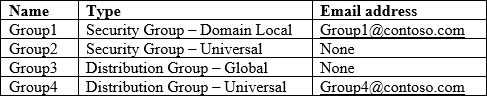
Your network contains an on-premises Active Directory domain named contoso.com.
The domain contains the groups shown in the following table.
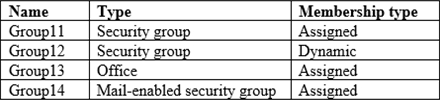
The domain is synced to an Azure AD tenant that contains the groups shown in the following table.
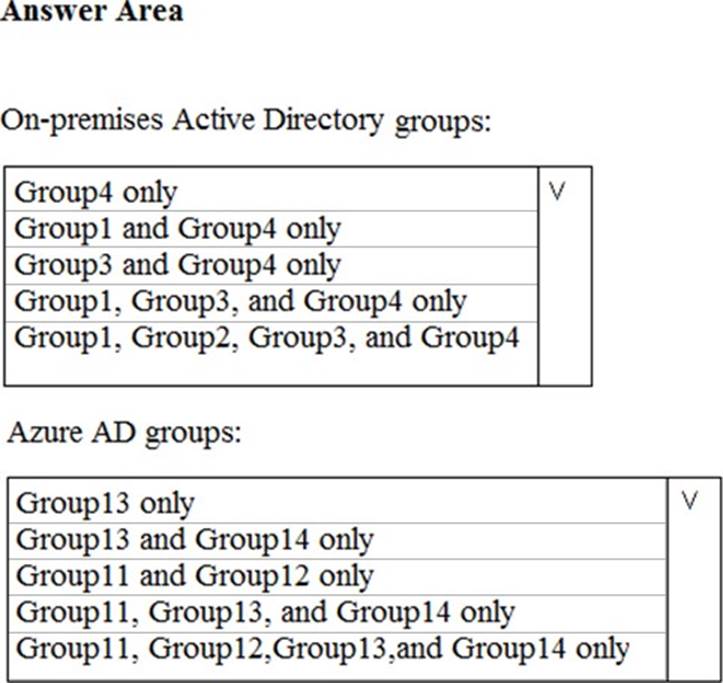
You create a sensitivity label named Label1.
You need to publish Label1.
To which groups can you publish Label1? To answer, se NOTE: Each correct selection is worth one point.
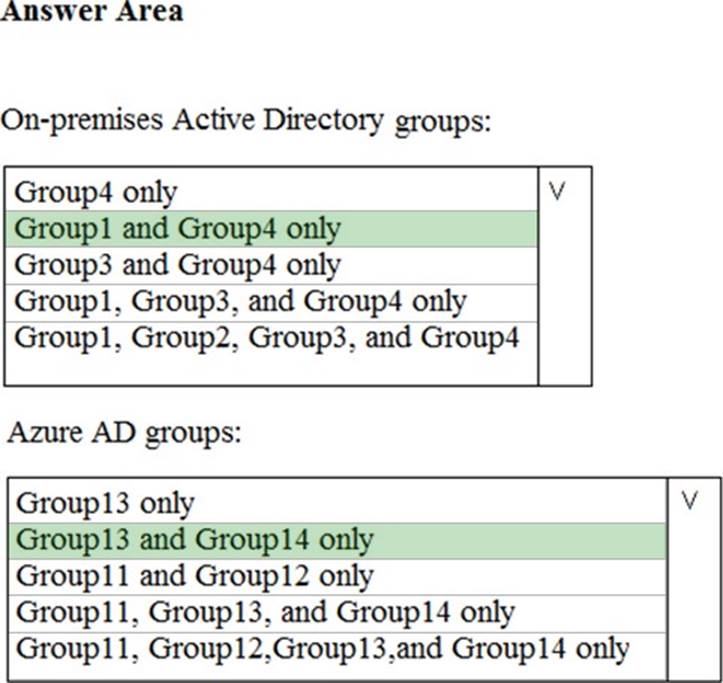
HOTSPOT
You have a Microsoft 365 subscription that contains three users named User1, User2. and User2.
You have the named locations shown in the following table.
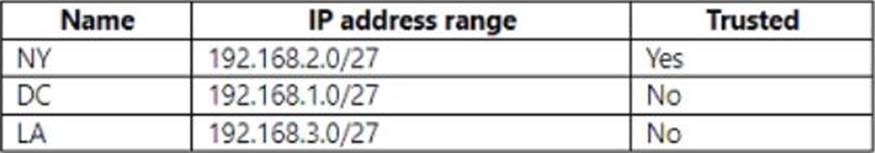
You configure an Azure Multi-Factor Authentication (MFA) trusted IP address range of 192.168.1.0/27.
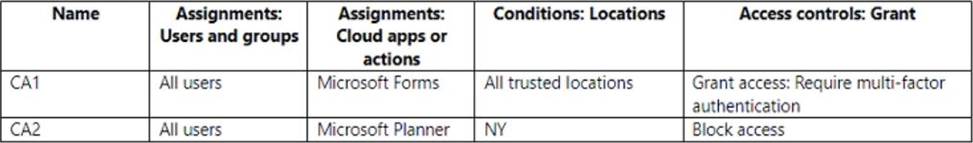
You have the Conditional Access policies shown in the following table.
The users have the IP addresses shown in the following table.
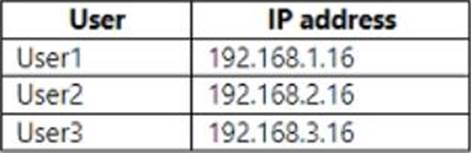
For each of the following statements, select Yes if the statement is true. Otherwise, se ect No. NOTE: Each correct selection is worth one point.
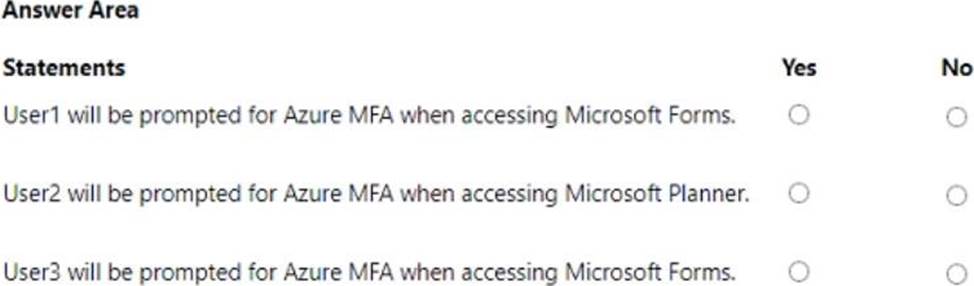
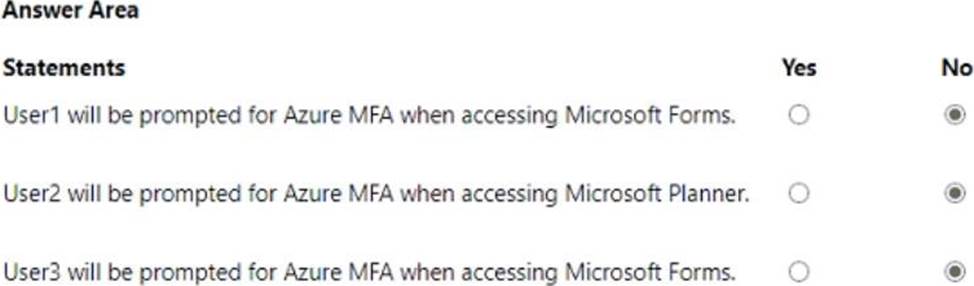
HOTSPOT
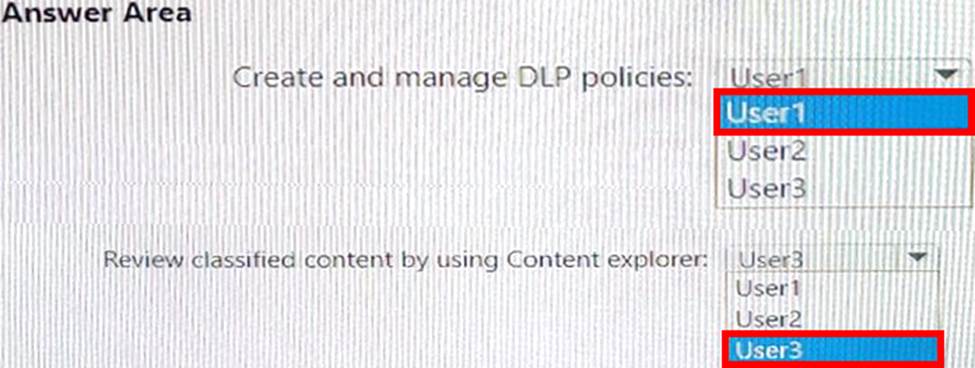
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
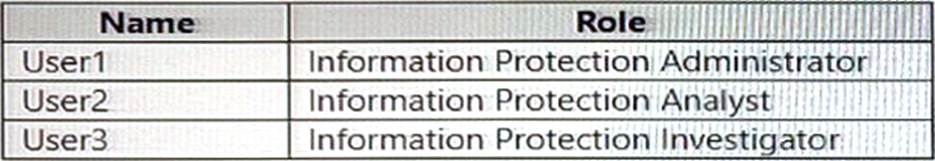
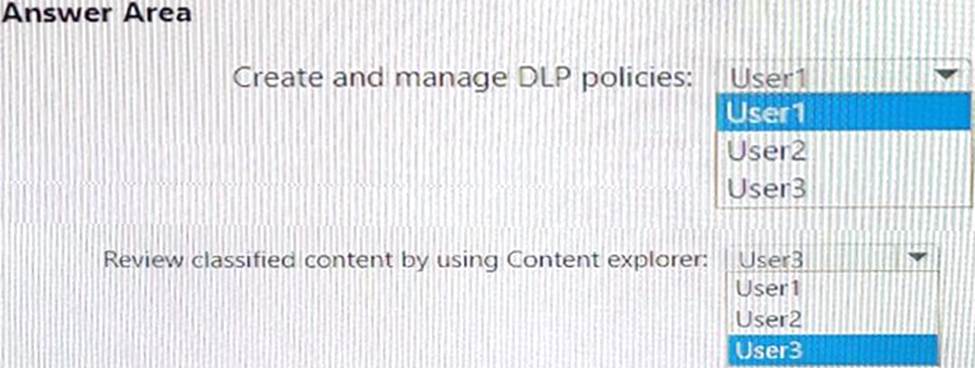
You need to delegate the following tasks:
Create and manage data loss prevention (DLP) policies. Review classified content by using Content explorer.
The solution must use the principle of least privilege.
Which user should perform each task? To answer, drag the appropriate users to the correct tasks. Each user may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription that contains several Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager.
You need to enable Microsoft Defender Exploit Guard (Microsoft Defender EG) on the devices.
Which type of device configuration profile should you use?
- A . Endpoint protection
- B . Device restrictions
- C . Microsoft Defender for Endpoint
- D . identity protection
You have a Microsoft 365 tenant that uses Azure Information Protection to encrypt sensitive content.
You plan to implement Microsoft Cloud App Security to inspect protected files that are uploaded to Microsoft OneDrive for Business.
You need to ensure that at Azure Information Protection-protected files can be scanned by using Cloud App Security
Which two actions should you perform7 Each correct answer presents part of the solution? NOTE: Each correct selection is worth one point.
- A . From the Cloud App Security admin center, enable file monitoring of software as a service (SaaS) apps.
- B . From the Cloud App Security admin center, create an OAuth app policy for apps that have the Have full access to user files permission
- C . From the Microsoft 365 compliance admin center create a data loss prevention (EXP) policy that contains an exception for content that contains a sensitive information type.
- D . From the Azure Active Directory admin center, grant Cloud App Security permission to read all the protected content of the tenant
You have a Microsoft 365 E5 subscription that uses Azure Active Directory (Azure AD) Privileged identity Management (PIM). A user named User! is eligible for the User Account Administrator role. You need User! to request to activate the User Account Administrator role.
From where should User1 request to activate the role?
- A . the My Access portal
- B . the Microsoft 365 Defender portal
- C . the Azure Active Directory admin center
- D . the Microsoft 365 admin center
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some questions sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in Security & Compliance to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true
-AdminAuditLogCmdlets *Mailbox* command.
Does that meet the goal?
- A . Yes
- B . No
B
Explanation:
References: https://docs.microsoft.com/en-us/powershell/module/exchange/policy-and-compliance-audit/setadminauditlogconfig?view=exchange-ps
Latest MS-500 Dumps Valid Version with 193 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


You know you need help when you are preparing for a hard exam like Microsoft 365 Security Administration. MS-500 Dumps PDF 2019 is the best source to get familiar with the latest exam patterns and terms. You can easily get a wide range of 2019 MS-500 Exam Questions at affordable rates from Testmayor. Check out the Free Demo to make sure the MS-500 Dumps are up to your demand. Get free 3-month updates with your purchase and a fabulous discount on using the coupon code.