Microsoft MS-101 Microsoft 365 Mobility and Security Online Training
Microsoft MS-101 Online Training
The questions for MS-101 were last updated at Feb 21,2026.
- Exam Code: MS-101
- Exam Name: Microsoft 365 Mobility and Security
- Certification Provider: Microsoft
- Latest update: Feb 21,2026
Your company uses on-premises Windows Server File Classification Infrastructure (FCI).
Some documents on the on-premises file servers are classified as Confidential.
You migrate the files from the on-premises file servers to Microsoft SharePoint Online.
You need to ensure that you can implement data loss prevention (DLP) policies for the uploaded file based on the Confidential classification.
What should you do first?
- A . From the SharePoint admin center, configure hybrid search.
- B . From the SharePoint admin center, create a managed property.
- C . From the Security & Compliance Center PowerShell, run the New-DataClassification cmdlet.
- D . From the Security & Compliance Center PowerShell, run the New-DlpComplianceRule cmdlet.
HOTSPOT
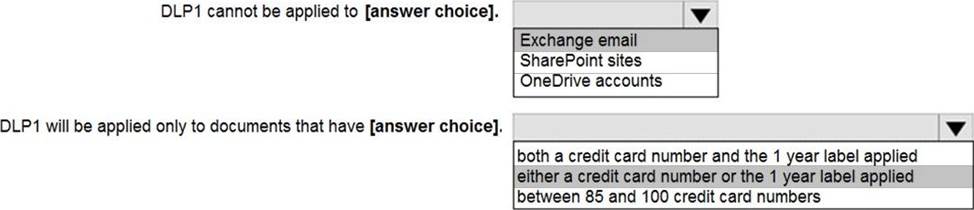
You configure a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.
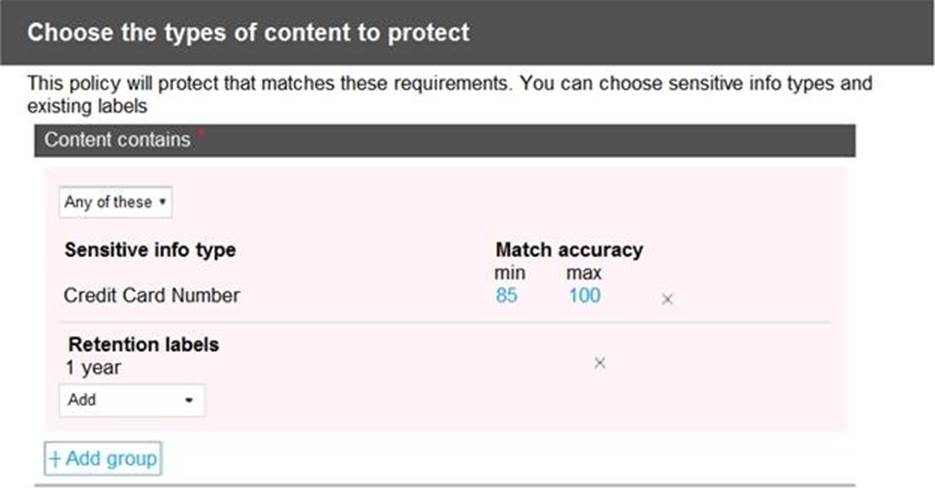
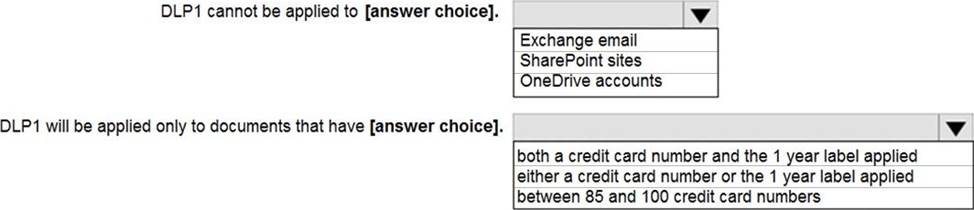
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
HOTSPOT
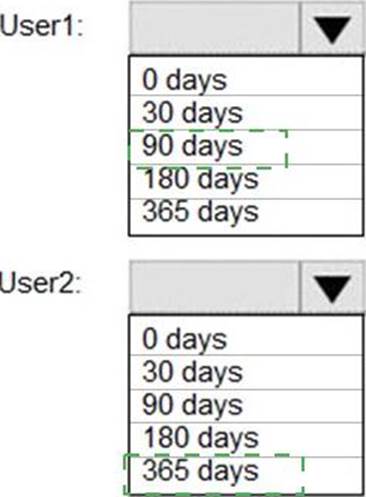
You have a Microsoft 365 E5 subscription that contains two users named Admin1 and Admin2.
All users are assigned a Microsoft 365 Enterprise E5 license and auditing is turned on.
You create the audit retention policy shown in the exhibit. (Click the Exhibit tab.)
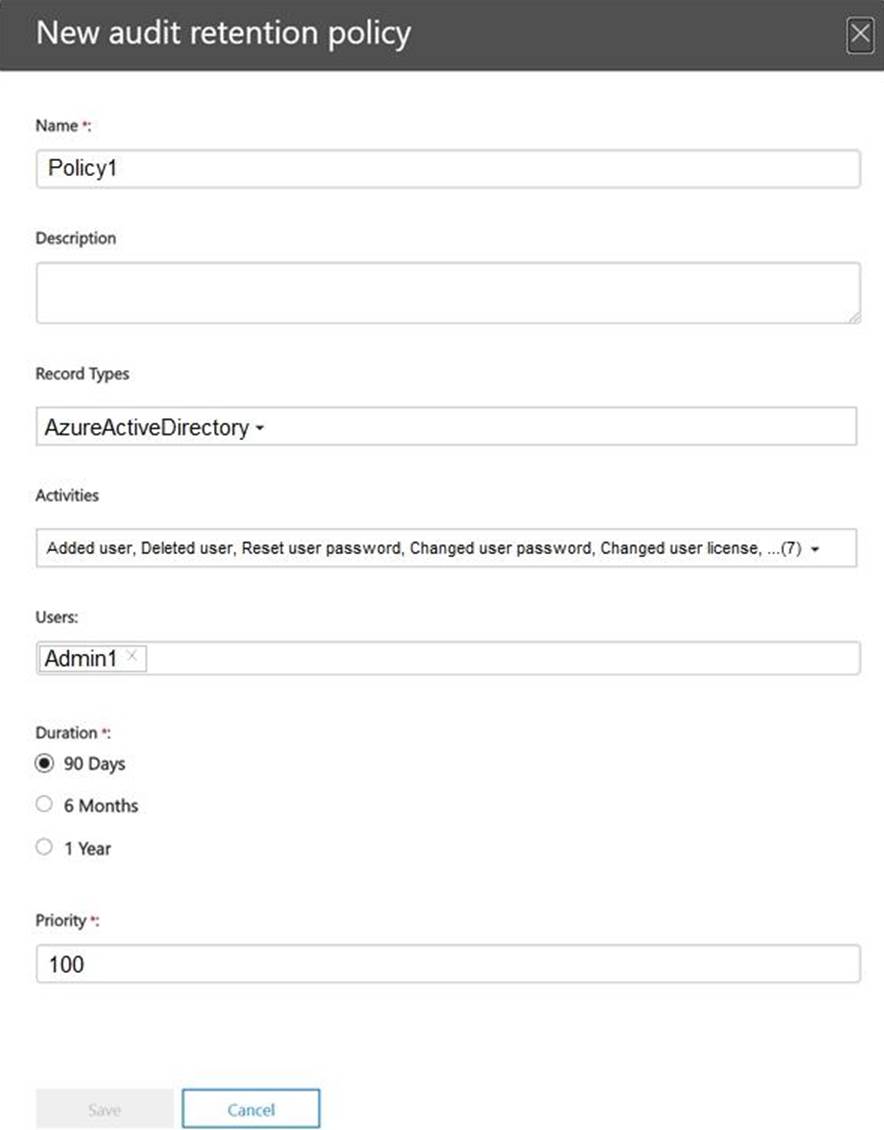
After Policy1 is created, the following actions are performed:
✑ Admin1 creates a user named User1.
✑ Admin2 creates a user named User2.
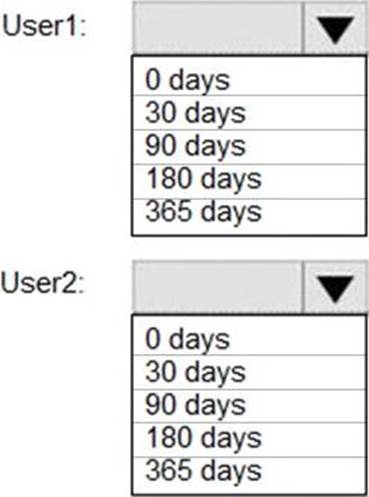
How long will the audit events for the creation of User1 and User2 be retained? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
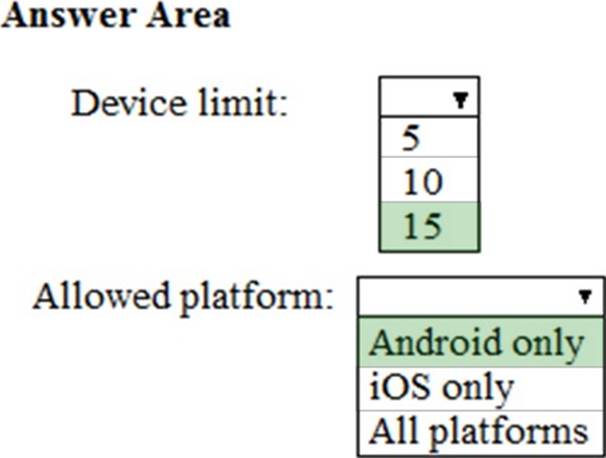
You plan to allow users from the engineering department to enroll their mobile device in mobile device management (MDM).
The device type restrictions are configured as shown in the following table.
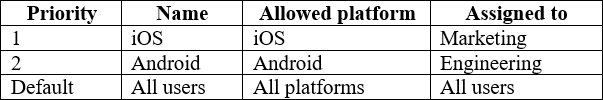
The device limit restrictions are configured as shown in the following table.
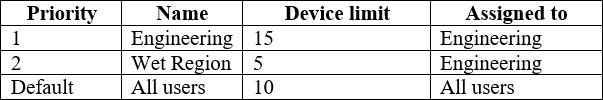
What is the effective configuration for the members of the Engineering group? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

You have a Microsoft 365 tenant.
Company policy requires that all Windows 10 devices meet the following minimum requirements:
✑ Require complex passwords.
✑ Require the encryption of data storage devices.
✑ Have Microsoft Defender Antivirus real-time protection enabled.
You need to prevent devices that do not meet the requirements from accessing resources in the tenant.
Which two components should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . a configuration policy
- B . a compliance policy
- C . a security baseline profile
- D . a conditional access policy
- E . a configuration profile
You have a Microsoft 365 tenant that contains 1,000 Windows 10 devices. The devices are enrolled in Microsoft Intune.
Company policy requires that the devices have the following configurations:
✑ Require complex passwords.
✑ Require the encryption of removable data storage devices.
✑ Have Microsoft Defender Antivirus real-time protection enabled.
You need to configure the devices to meet the requirements.
What should you use?
- A . an app configuration policy
- B . a compliance policy
C a security baseline profile
D a conditional access policy
HOTSPOT
You have three devices enrolled in Microsoft Intune as shown in the following table.
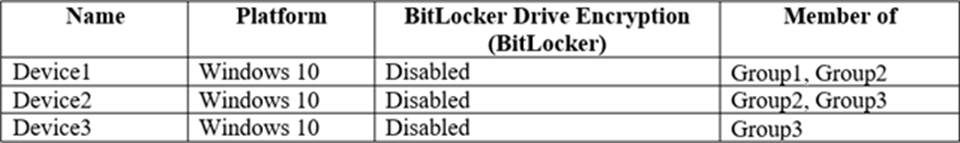
The device compliance policies in Intune are configured as shown in the following table.
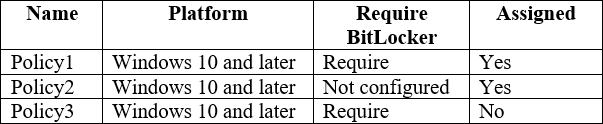
The device compliance policies have the assignments shown in the following table.
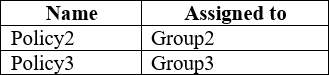
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

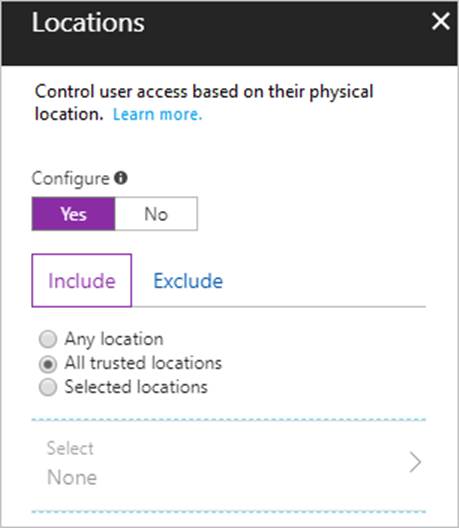
You configure a conditional access policy.
The locations settings are configured as shown in the Locations exhibit. (Click the Locations tab.)
The users and groups settings are configured as shown in the Users and Groups exhibit. (Click Users and Groups tab.)
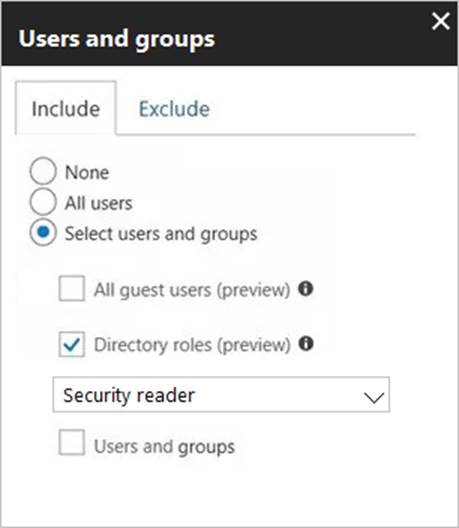
Members of the Security reader group report that they cannot sign in to Microsoft Active Directory (Azure AD) on their device while they are in the office.
You need to ensure that the members of the Security reader group can sign in in to Azure AD on their device while they are in the office. The solution must use the principle of least privilege.
What should you do?
- A . From the conditional access policy, configure the device state.
- B . From the Azure Active Directory admin center, create a custom control.
- C . From the Intune admin center, create a device compliance policy.
- D . From the Azure Active Directory admin center, create a named location.
HOTSPOT
You have a Microsoft Azure Activity Directory (Azure AD) tenant contains the users shown in the following table.
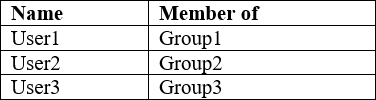
Group3 is a member of Group1.
Your company uses Windows Defender Advanced Threat Protection (ATP).
Windows Defender ATP contains the roles shown in the following table.

Windows Defender ATP contains the device groups shown in the following table.

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

HOTSPOT
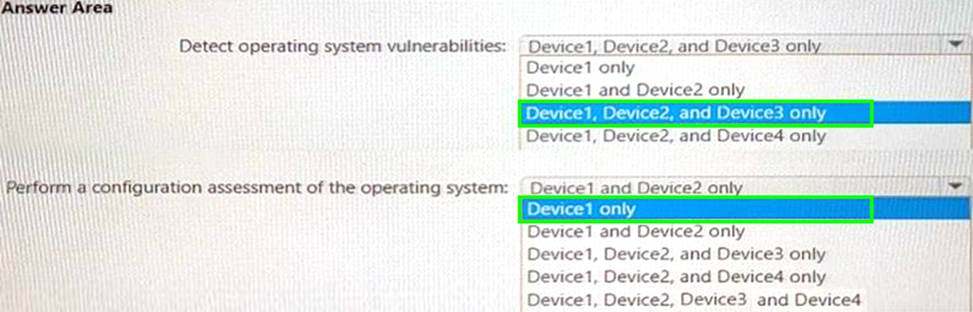
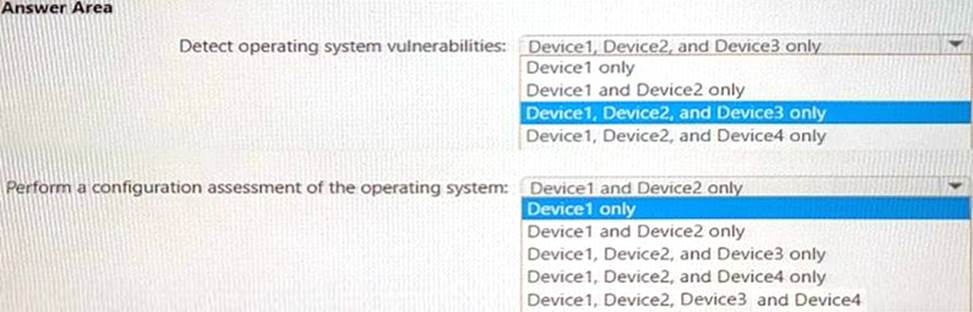
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
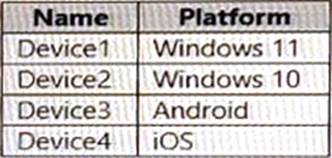
All the devices are onboarded To Microsoft Defender for Endpoint
You plan to use Microsoft Defender Vulnerability Management to meet the following requirements:
• Detect operating system vulnerabilities.
Latest MS-101 Dumps Valid Version with 268 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund