Microsoft MD-100 Windows Client Online Training
Microsoft MD-100 Online Training
The questions for MD-100 were last updated at Feb 13,2026.
- Exam Code: MD-100
- Exam Name: Windows Client
- Certification Provider: Microsoft
- Latest update: Feb 13,2026
You have a workgroup computer that runs Windows 10.
You create a local user named User1.
User1 needs to be able to share and manage folders located in a folder named C:Share by using the Shared Folders snap-in. The solution must use the principle of least privilege.
To which group should you add User1?
- A . Device Owners
- B . Users
- C . Power Users
- D . Administrators
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using [email protected].
Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1.
Share1 has the permission shown in the following table.
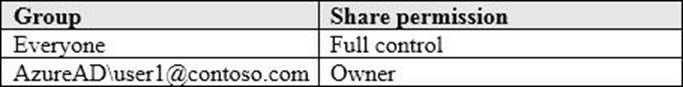
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using [email protected].
User2 attempts to access Share1 and receives the following error message: “The username or password is incorrect.”
You need to ensure that User2 can connect to Share1.
Solution: You create a local group on Computer1 and add the Guest account to the group.
You grant the group Modify access to Share1.
Does this meet the goal?
- A . Yes
- B . No
You have a computer that runs Windows 10.
You can start the computer but cannot sign in.
You need to start the computer into the Windows Recovery Environment (WinRE).
What should you do?
- A . Turn off the computer. Turn on the computer, and then pressF8.
- B . Turn off the computer. Turn on the computer, and then pressF10.
- C . From the sign-in screen, hold the Shift key, and then click Restart.
- D . Hold Alt+Ctrl+Delete for 10 seconds.
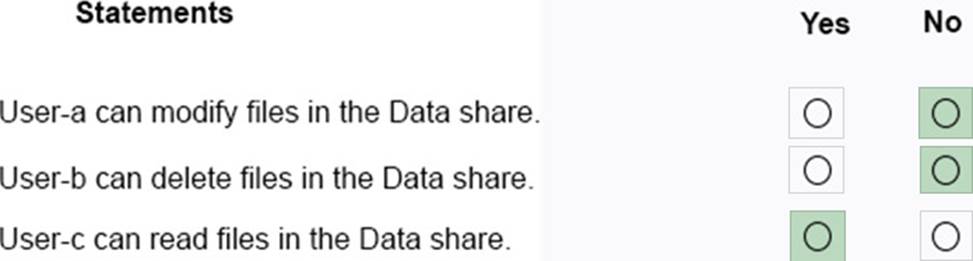
HOTSPOT
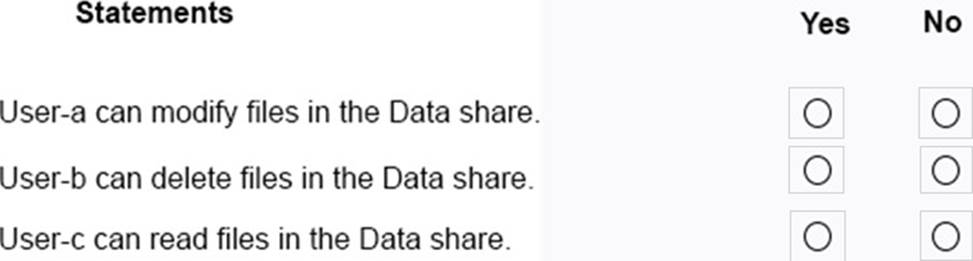
You have a computer named Computer5 that runs Windows 10 that is used to share documents in a workgroup.
You create three users named User-a, User-b, User-c. The users plan to access Computer5 from the network only.
You have a folder named Data.
The Advanced Security Settings for the Data folder are shown in the Security exhibit. (Click the Security Exhibit tab).
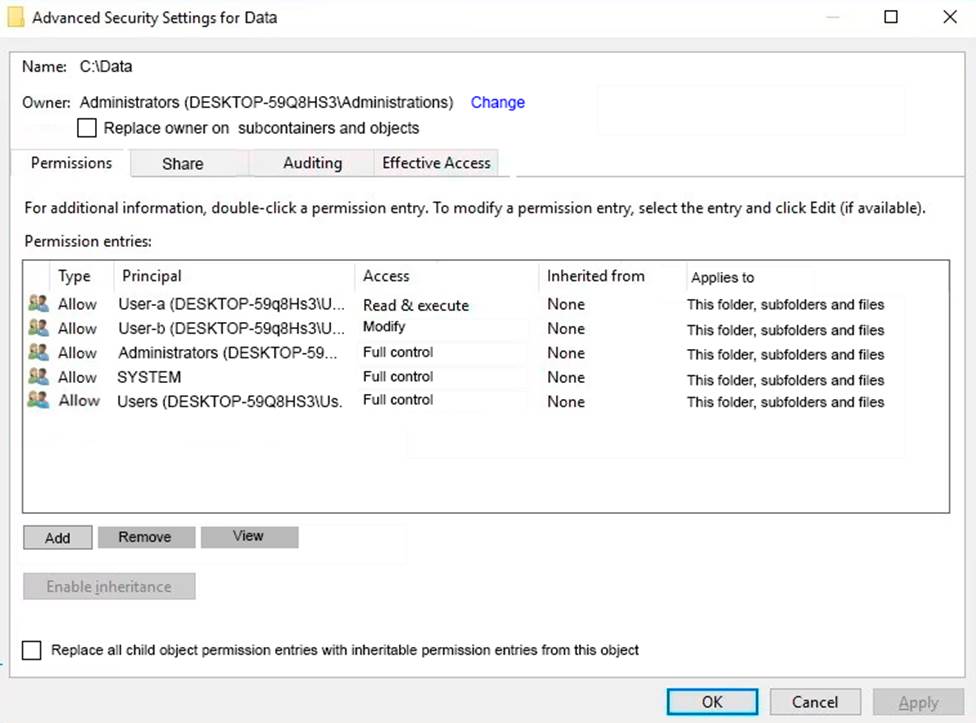
You share the Data folder.
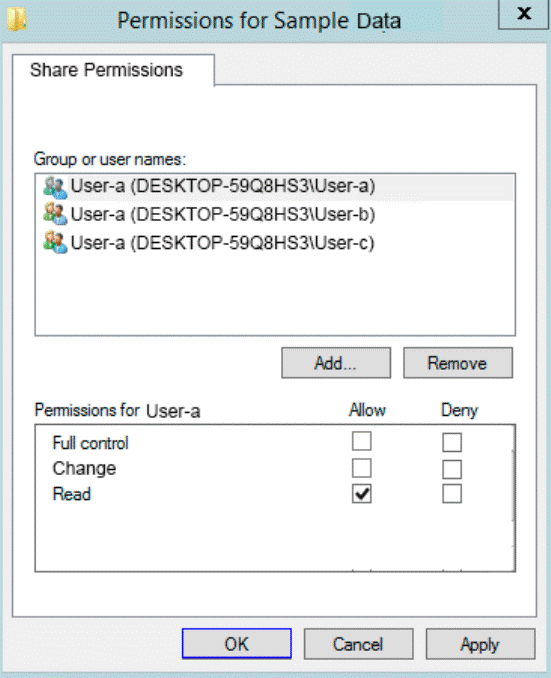
The permission for User-a are shown in the User-a exhibit (Click the User-a tab.)
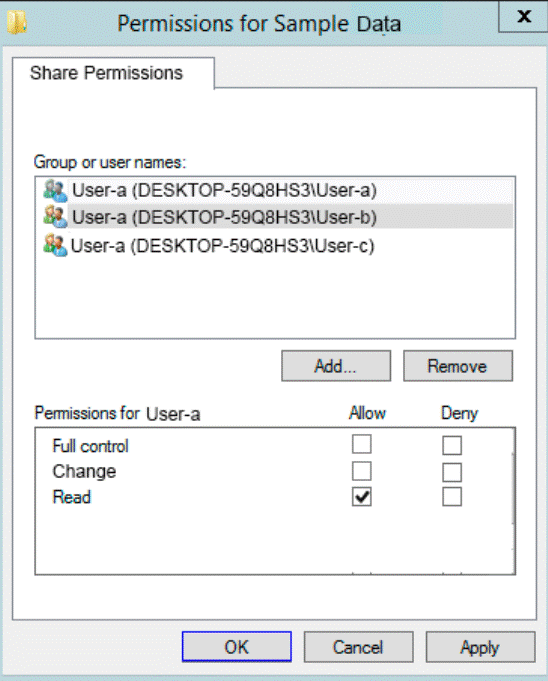
The permissions for user-b are shown in the User-b exhibit. (Click the User-b tab.)
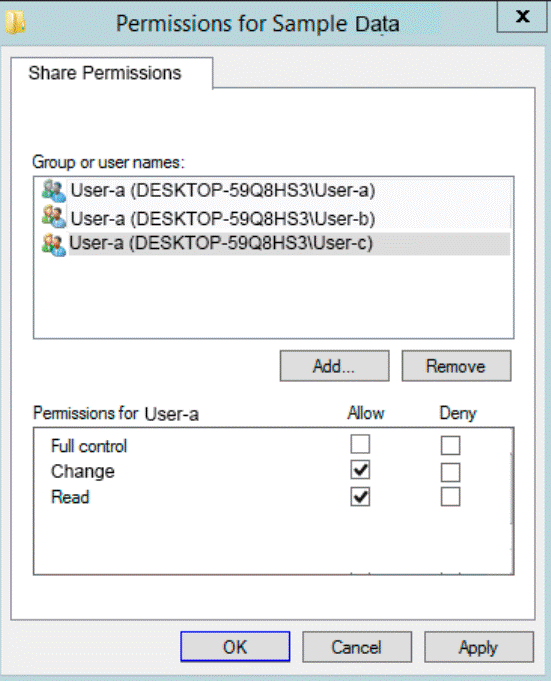
The permissions for user-c are shown in the User-c exhibit. (Click the User-c tab.)
For each of the following statements, select Yes if the statements is true. Otherwise, select No.
NOTE:Reach correct selection is worth one point.
You customize the Start menu on a computer that runs Windows 10 as shown in the following exhibit.

You need to add Remote Desktop Connection to Group1 and remove Group3 from the Start menu.
Which two actions should you perform from the Start menu customizations? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . Unlock Group!
- B . Remove Command Prompt from Group1.
- C . Delete Group3.
- D . Add Remote Desktop Connection to Group1.
- E . Rename Group3 as Group1.
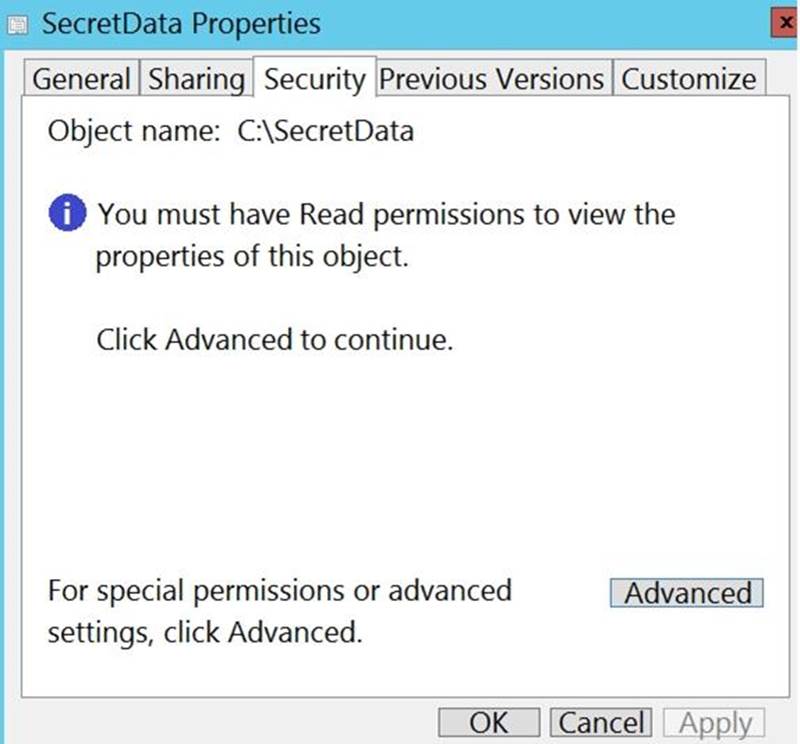
User1 is a member of the Administrators group on a computer that runs Windows 10.
When User1 attempts to view the security settings of a folder named C:SecretData, the user receives the message in the Security exhibit.
On the computer, you sign in as a member of the Administrators group and view the permissions to C:SecretData as shown in the Permissions exhibit.
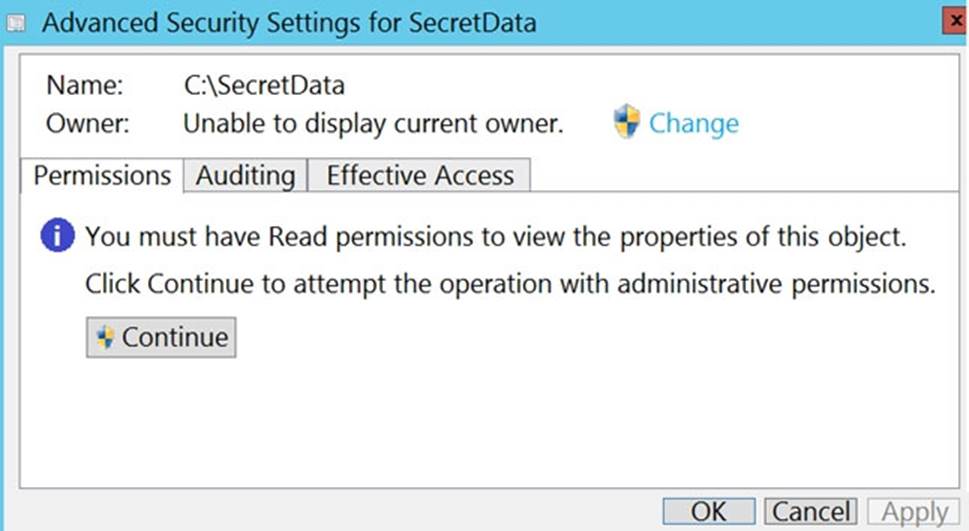
You need to restore Use1’s access to C:SecretData.
What should you do first?
- A . From the Permissions tab of Advanced Security Settings for SecretData, select Change to take ownership of the folder.
- B . From the Permissions tab of Advanced Security Settings for SecretData, select Continue to attempt the operation by using administrative privileges.
- C . Assign User1 Full control permissions to the C folder and set the inheritance to This folder, subfolders and files.
- D . From an elevated command prompt, run cacls.exe c:secretdata /g user1: F.
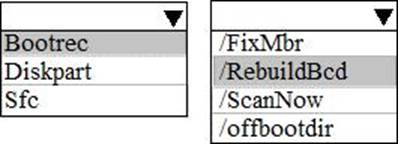
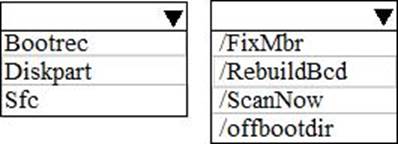
HOTSPOT
You are a network administrator at your company.
A user attempts to start a computer and receives the following error message: “Bootmgr is missing.”
You need to resolve the issue.
You start the computer in the recovery mode.
Which command should you run next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
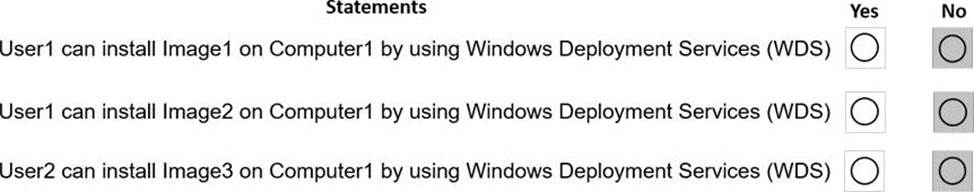
HOTSPOT
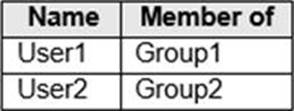
Your network contains an Active Directory domain.
The domain contains the users shown in the following table.
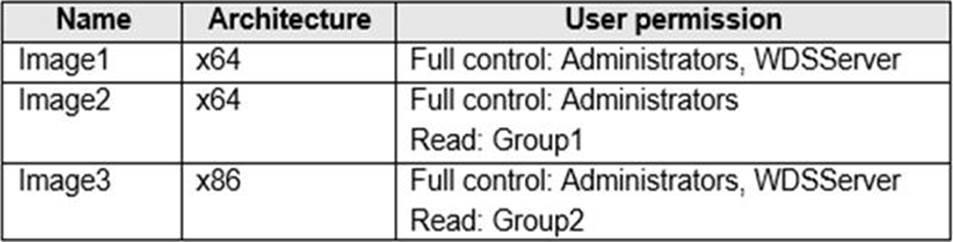
You have a server named Server1 that runs Windows Server 2019 and has the Windows Deployment Services role installed. Server1 contains an x86 boot image and three Windows 10 install images.
The install images are shown in the following table.
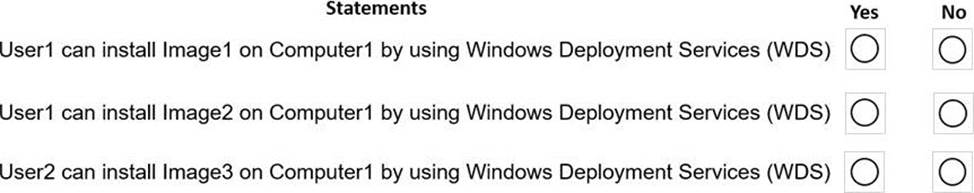
You purchase a computer named Computer1 that is compatible with the 64-bit version of Windows 10.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You have a computer that runs Windows 10 Home.
You need to upgrade the computer to Windows 10 Enterprise as quickly as possible. The solution must retain the user settings.
What should you do first?
- A . Run the scanscace command.
- B . Perform an in-place upgrade to Windows Pro.
- C . Install the latest feature updates.
- D . Run the sysprep command.
Your network contains an Active Directory domain. The domain contains computers that run Windows 10.
You need to provide a user with the ability to remotely create and modify shares on the computers. The solution must use the principle of least privilege.
To which group should you add the user?
- A . Power Users
- B . Remote Management Users
- C . Administrators
- D . Network Configuration Operators
Latest MD-100 Dumps Valid Version with 272 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund