Microsoft AZ-801 Configuring Windows Server Hybrid Advanced Services Online Training
Microsoft AZ-801 Online Training
The questions for AZ-801 were last updated at Feb 28,2026.
- Exam Code: AZ-801
- Exam Name: Configuring Windows Server Hybrid Advanced Services
- Certification Provider: Microsoft
- Latest update: Feb 28,2026
You are evaluating the technical requirements tor Cluster2.
What is the minimum number of Azure Site Recovery Providers that you should install?
- A . 1
- B . 4
- C . 12
- D . 16
Which domain controller should be online to meet the technical requirements for DC4?
- A . DC1
- B . DC2
- C . DC3
Topic 3, Misc. Questions
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Controlled folder access.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From Virus & threat protection, you configure Tamper Protection.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From App & browser control, you configure the Exploit protection settings.
Does this meet the goal?
- A . Yes
- B . No
DRAG DROP
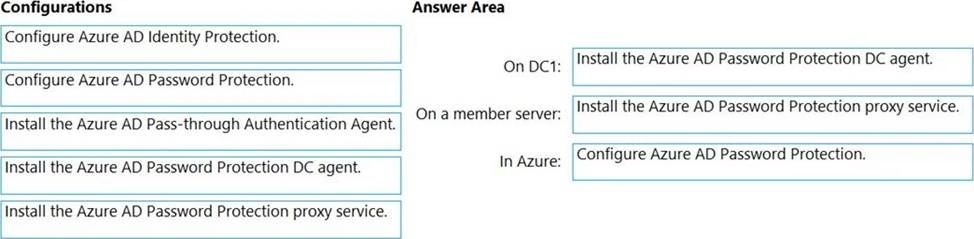
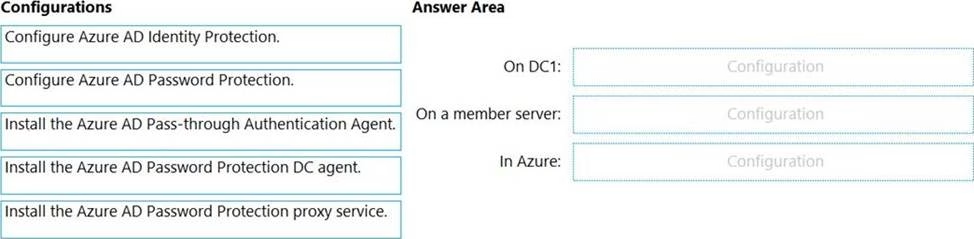
You have an on-premises Active Directory Domain Services (AD DS) domain that syncs with an Azure Active Directory (Azure AD) tenant.
The AD DS domain contains a domain controller named DC1. DC1 does NOT have internet access.
You need to configure password security for on-premises users.
The solution must meet the following requirements:
✑ Prevent the users from using known weak passwords.
✑ Prevent the users from using the company name in passwords.
What should you do? To answer, drag the appropriate configurations to the correct targets. Each configuration may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT
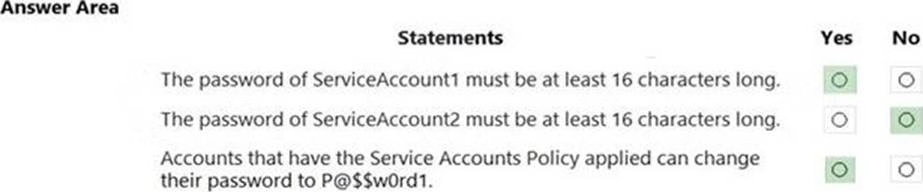
The Default Domain Policy Group Policy Object (GPO) is shown in the GPO exhibit. (Click the GPO tab.)
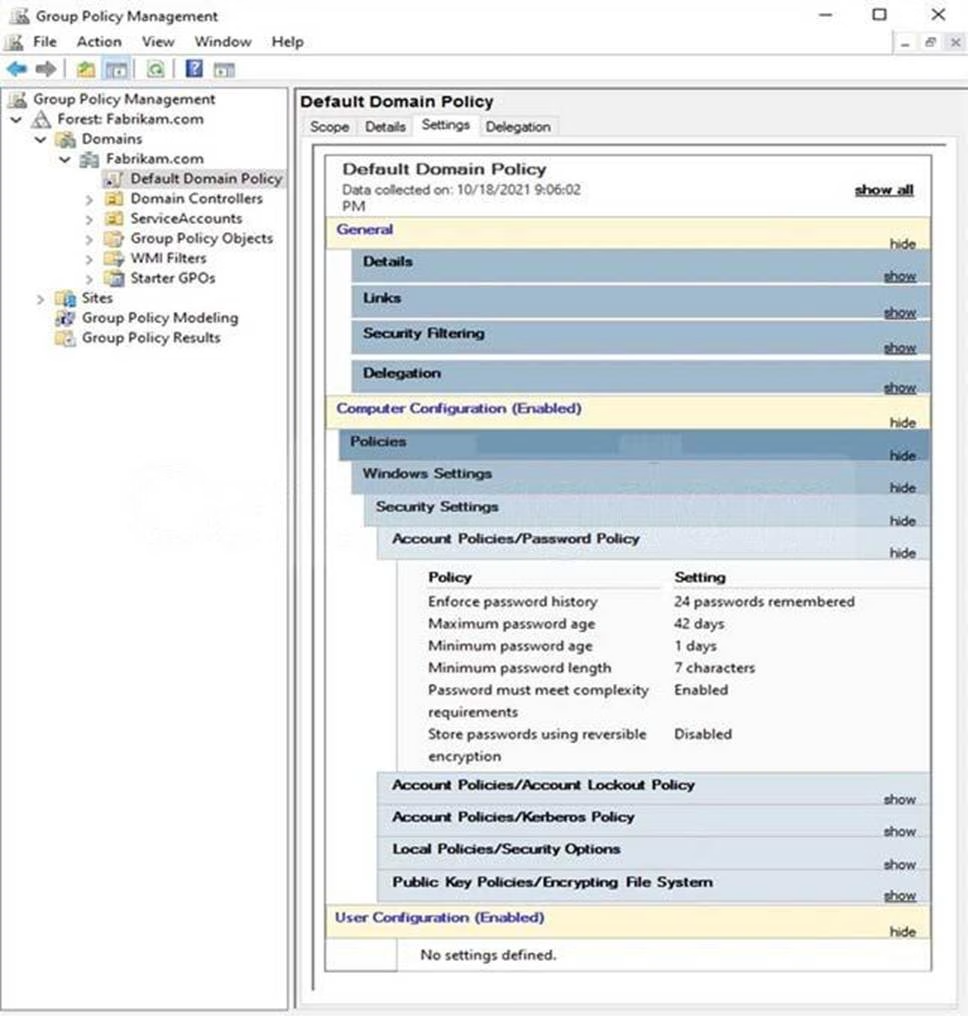
The members of a group named Service Accounts are shown in the Group exhibit. (Click the Group tab.)
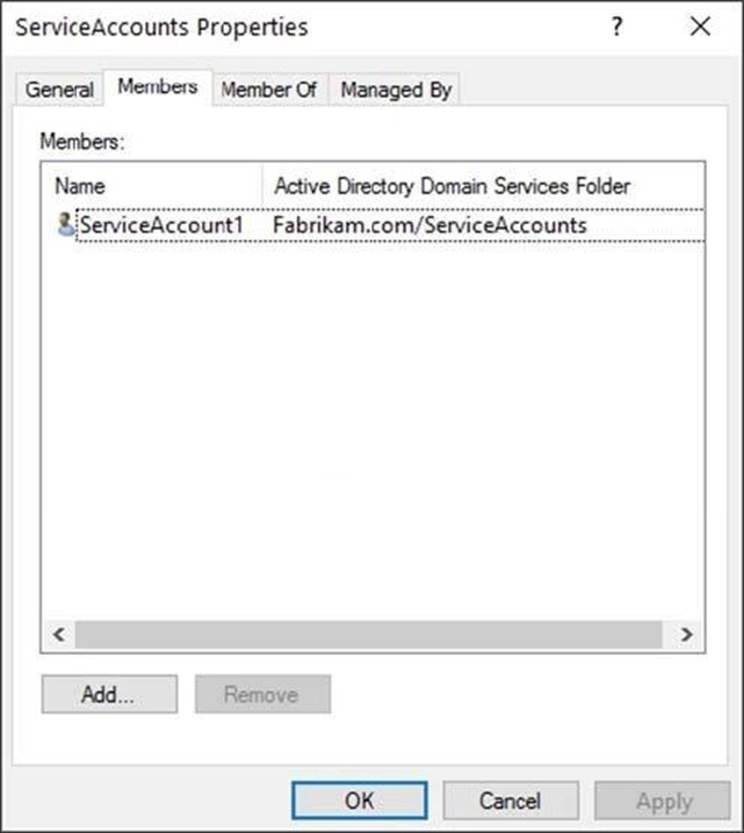
An organizational unit (OU) named ServiceAccounts is shown in the OU exhibit. (Click the OU tab.)
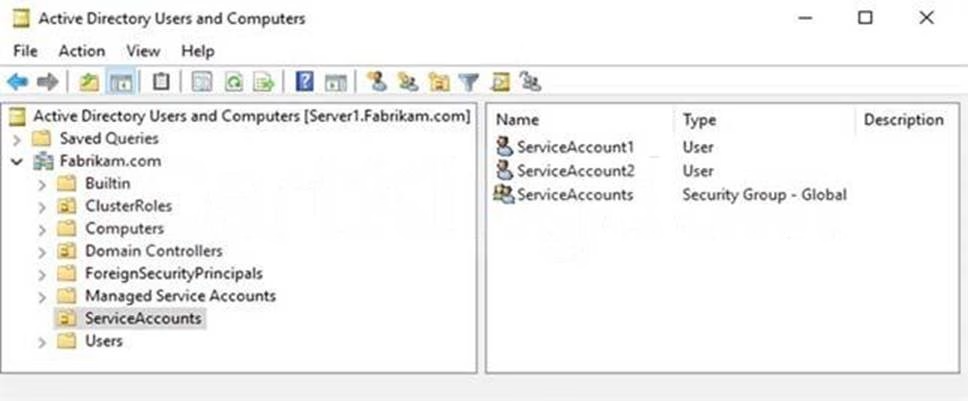
You create a Password Settings Object (PSO) as shown in the PSO exhibit. (Click the PSO tab.)
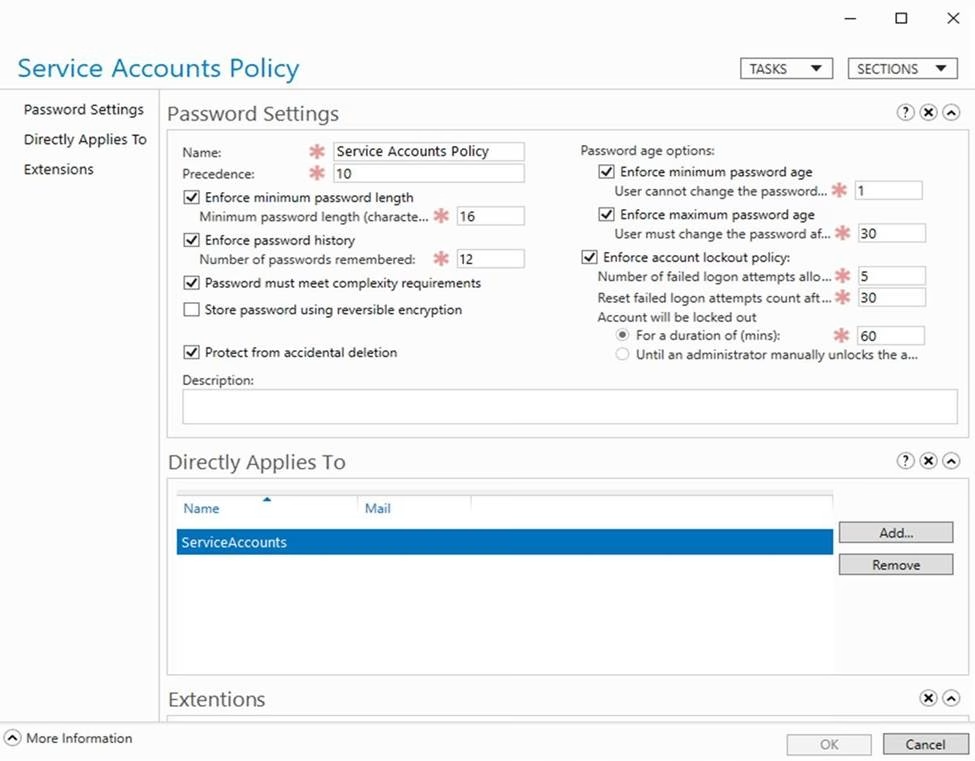
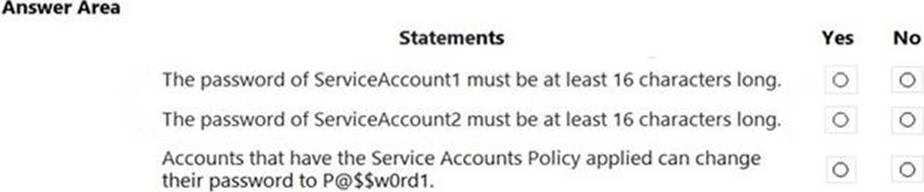
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
DRAG DROP
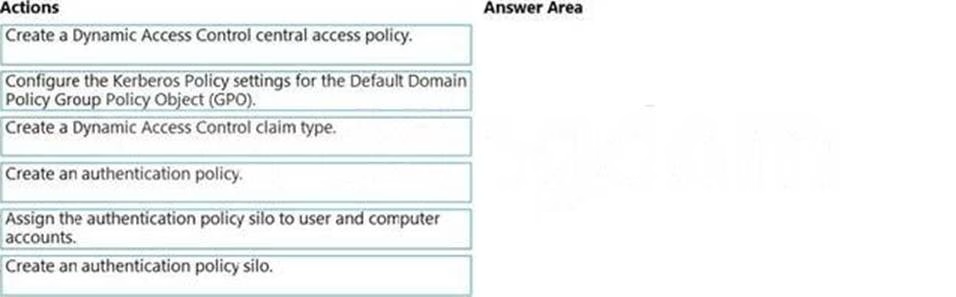
Your network contains an Active Directory Domain Services (AD DS) domain.
You need to implement a solution that meets the following requirements:
✑ Ensures that the members of the Domain Admins group are allowed to sign in only to domain controllers
✑ Ensures that the lifetime of Kerberos Ticket Granting Ticket (TGT) for the members of the Domain Admins group is limited to one hour
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure virtual machine named VM1 that runs Windows Server.
You plan to deploy a new line-of-business (LOB) application to VM1.
You need to ensure that the application can create child processes.
What should you configure on VM1?
- A . Microsoft Defender Credential Guard
- B . Microsoft Defender Application Control
- C . Microsoft Defender SmartScreen
- D . Exploit protection
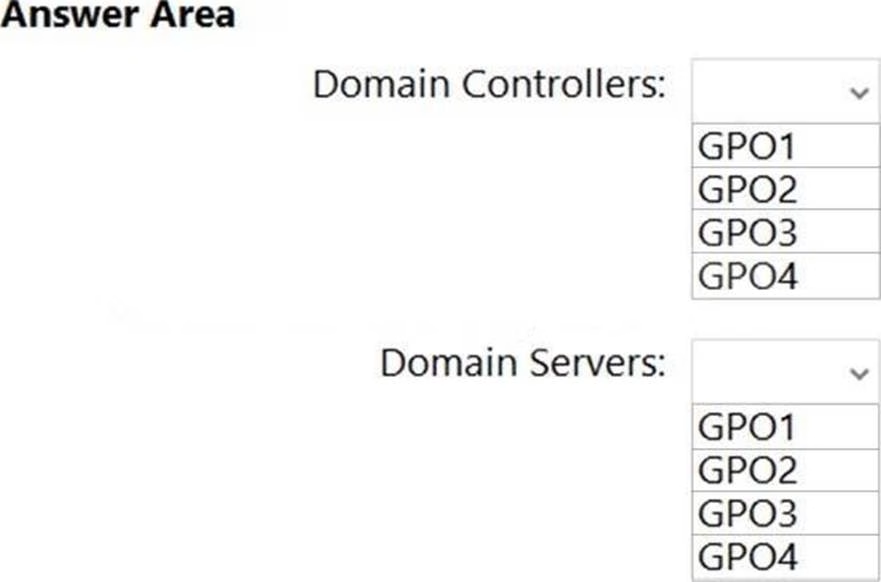
HOTSPOT
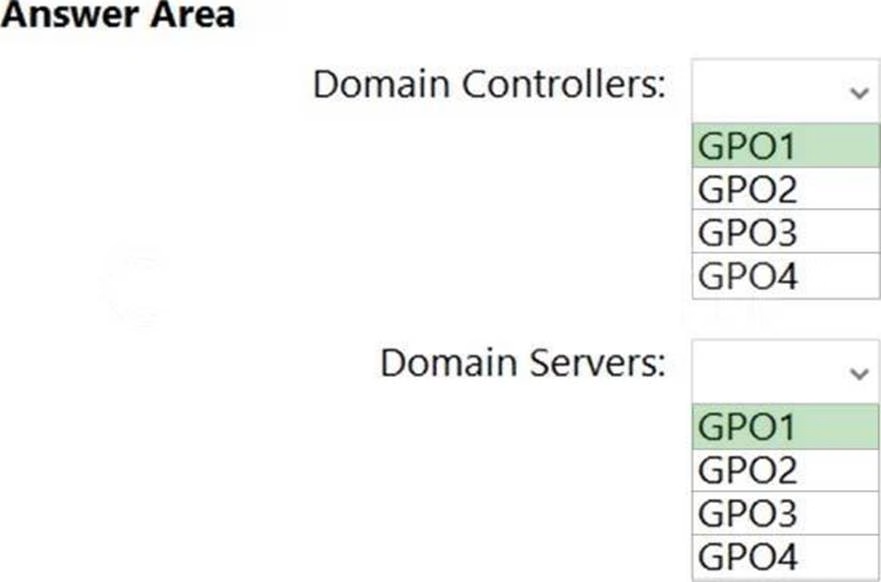
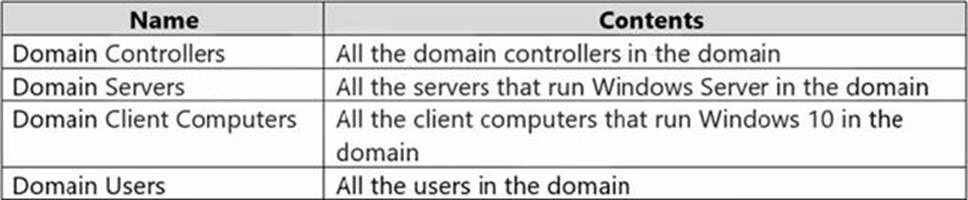
Your network contains an Active Directory Domain Services (AD DS) domain named contoso.com.
The domain contains the organizational units (OUs) shown in the following table.
In the domain, you create the Group Policy Objects (GPOs) shown in the following table.
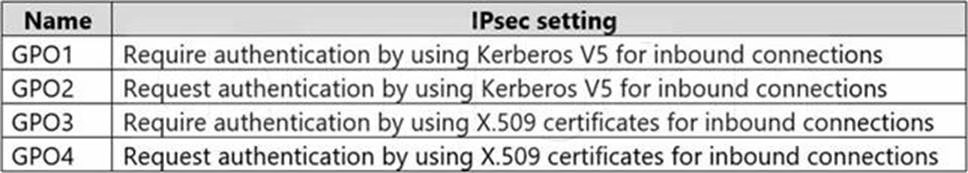
You need to implement IPsec authentication to ensure that only authenticated computer accounts can connect to the members in the domain. The solution must minimize administrative effort.
Which GPOs should you apply to the Domain Controllers OU and the Domain Servers OU? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Latest AZ-801 Dumps Valid Version with 85 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund