Microsoft AZ-700 Designing and Implementing Microsoft Azure Networking Solutions Online Training
Microsoft AZ-700 Online Training
The questions for AZ-700 were last updated at Feb 26,2026.
- Exam Code: AZ-700
- Exam Name: Designing and Implementing Microsoft Azure Networking Solutions
- Certification Provider: Microsoft
- Latest update: Feb 26,2026
You need to provide access to storage2. The solution must meet the PaaS networking requirements and the business requirements.
Which connectivity method should you use?
- A . a service endpoint
- B . a private endpoint
- C . Azure Firewall
- D . Azure Front Door
Topic 2, Contoso Case Study 2
Overview
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab. note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Existing Environment:
Azure Network Infrastructure
Contoso has an Azure Active Directory (Azure AD) tenant named contoso.com.
The Azure subscription contains the virtual networks shown in the following table.
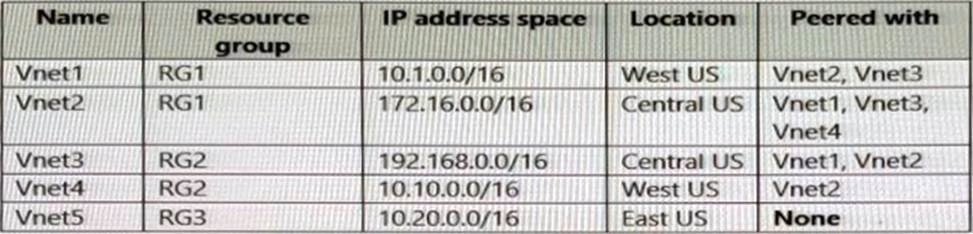
Vnet1 contains a virtual network gateway named GW1.
Azure Virtual Machines
The Azure subscription contains virtual machines that run Windows Server 2019 as shown in the following table.
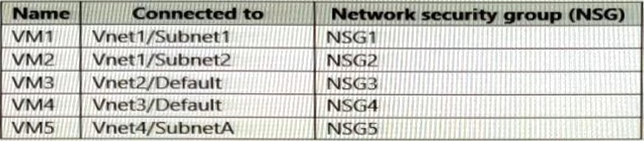
The NSGs are associated to the network interfaces on the virtual machines. Each NSG has one custom security rule that allows RDP connections from the internet. The firewall on each virtual machine allows ICMP traffic.
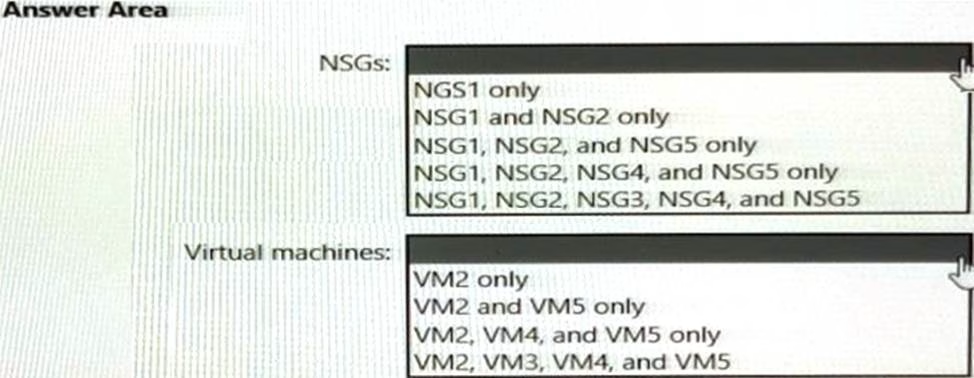
An application security group named ASG1 is associated to the network interface of VM1.
Azure Private DNS Zones
The Azure subscription contains the Azure private DNS zones shown in the following table.

Zone1.contoso.com has the virtual network links shown in the following table.

Other Azure Resources
The Azure subscription contains additional resources as shown in the following table.
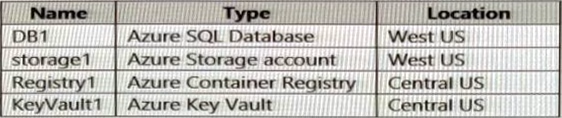
Requirements:
Virtual Network Requirements
Contoso has the following virtual networks requirements:
* Create a virtual network named Vnet6 in West US that will contain the following resources and configurations:
Two container groups that connect to Vnet6
Three virtual machines that connect to Vnet6
Allow VPN connections to be established to Vnet6
Allow the resources in Vnet6 to access KeyVault1, DB1, and Vnet1 over the Microsoft backbone network
* The virtual machines in Vnet4 and Vnet5 must be able to communicate over the Microsoft backbone network.
* A virtual machine named VM-Analyze will be deployed to Subnet1. VM-Analyze must inspect the outbound network traffic from Subnet2 to the internet.
Network Security Requirements
Contoso has the following network security requirements:
* Configure Azure Active Directory (Azure AD) authentication for Point-to-Site (P2S) VPN users.
* Enable NSG flow logs for NSG3 and NSG4.
* Create an NSG named NSG10 that will be associated to Vnet1/Subnet1 and will have the custom inbound security rules shown in the following table.

* Create an NSG named NSG11 that will be associated to Vnet1/Subnet2 and will have the custom outbound security rules shown in the following table.
![]()
HOTSPOT
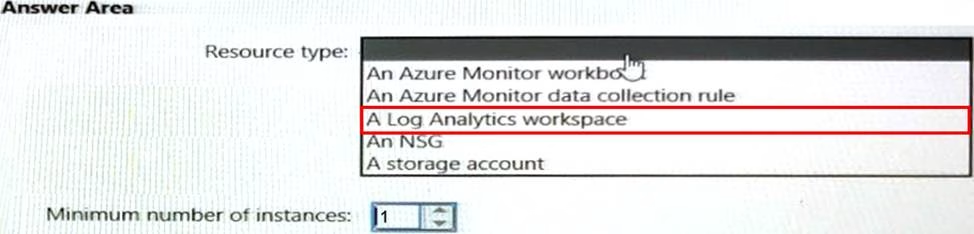
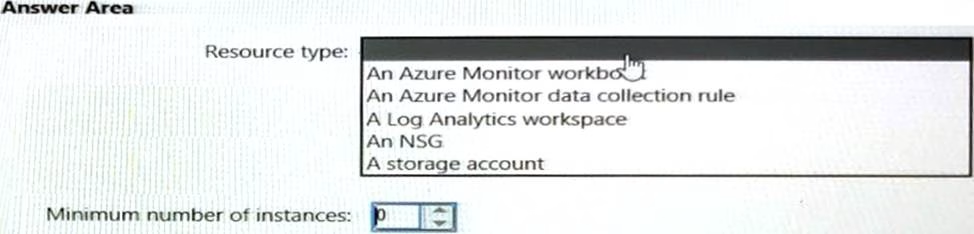
You need to meet the network security requirements for the NSG flow logs.
Which type of resource do you need, and how many instances should you create? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
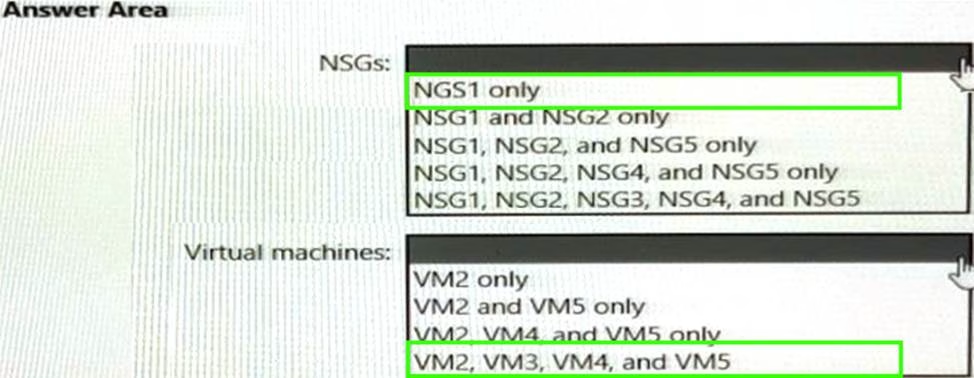
In which NSGs can you use ASG1 and to which virtual machine network interfaces can you associate ASG1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
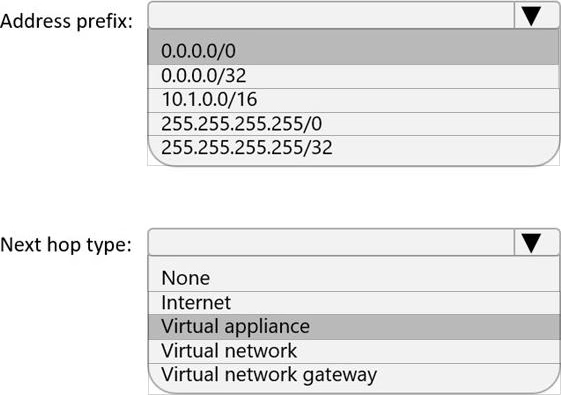
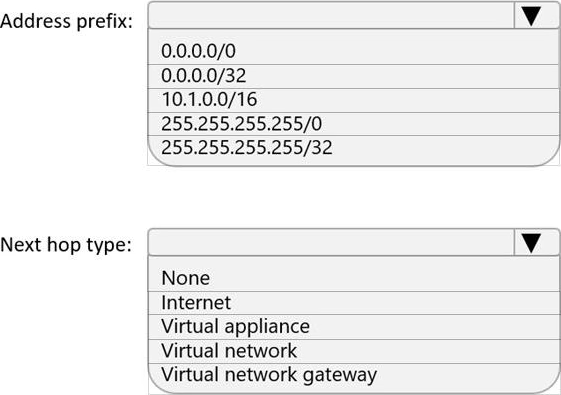
You are implementing the virtual network requirements for VM Analyze.
What should you include in a custom route that is linked to Subnet2? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You are implementing the Virtual network requirements for Vnet6.
What is the minimum number of subnets and service endpoints you should create? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.

What should you implement to meet the virtual network requirements for the virtual machines that connect to Vnet4 and Vnet5?
- A . a private endpoint
- B . a virtual network peering
- C . a private link service
- D . a routing table
- E . a service endpoint
HOTSPOT
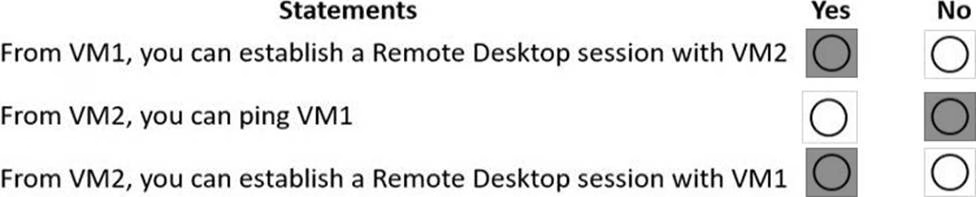
You create NSG10 and NSG11 to meet the network security requirements.
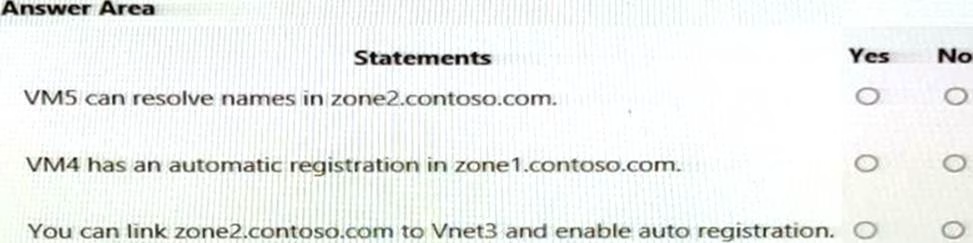
For each of the following statements, select Yes it the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
HOTSPOT
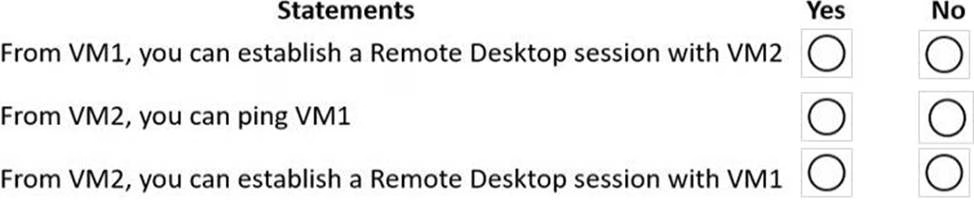
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
You need to configure GW1 to meet the network security requirements for the P2S VPN users.
Which Tunnel type should you select in the Point-to-site configuration settings of GW1?
- A . IKEv2 and OpenVPN (SSL)
- B . IKEv2
- C . IKEv2 and SSTP (SSL)
- D . OpenVPN (SSL)
- E . SSTP (SSL)
HOTSPOT
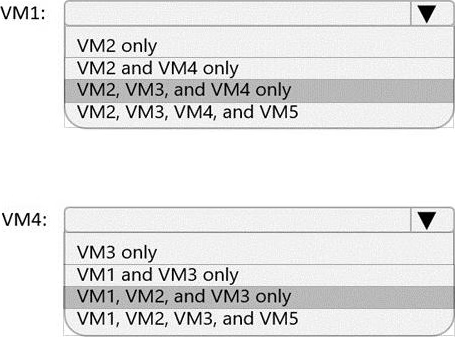
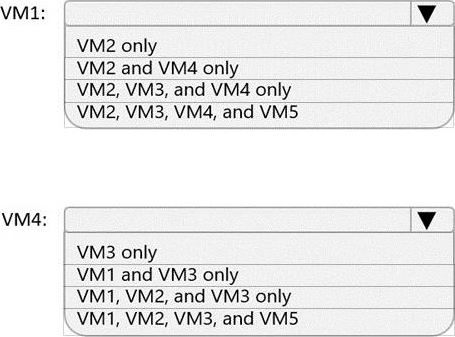
Which virtual machines can VM1 and VM4 ping successfully? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Latest AZ-700 Dumps Valid Version with 59 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund