Microsoft AZ-500 Microsoft Azure Security Technologies Online Training
Microsoft AZ-500 Online Training
The questions for AZ-500 were last updated at Feb 23,2026.
- Exam Code: AZ-500
- Exam Name: Microsoft Azure Security Technologies
- Certification Provider: Microsoft
- Latest update: Feb 23,2026
From the Azure portal, you are configuring an Azure policy.
You plan to assign policies that use the DeployIfNotExist, AuditIfNotExist, Append, and Deny effects.
Which effect requires a managed identity for the assignment?
- A . AuditIfNotExist
- B . Append
- C . DeployIfNotExist
- D . Deny
HOTSPOT
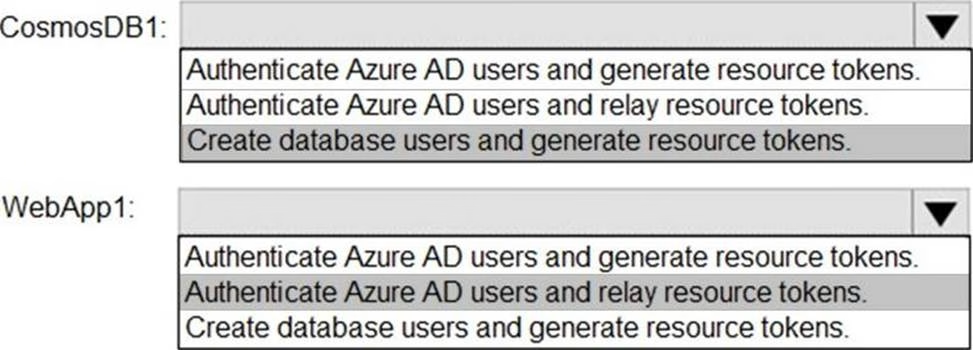
You have an Azure subscription named Sub1 that is associated to an Azure Active Directory (Azure AD) tenant named contoso.com.
You plan to implement an application that will consist of the resources shown in the following table.
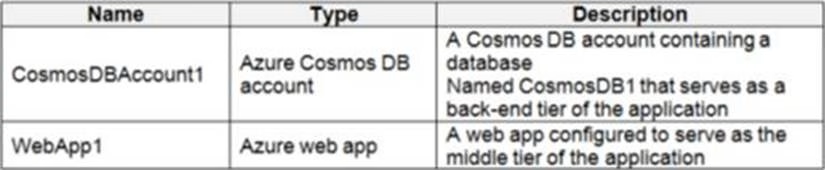
Users will authenticate by using their Azure AD user account and access the Cosmos DB account by using resource tokens.
You need to identify which tasks will be implemented in CosmosDB1 and WebApp1.
Which task should you identify for each resource? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
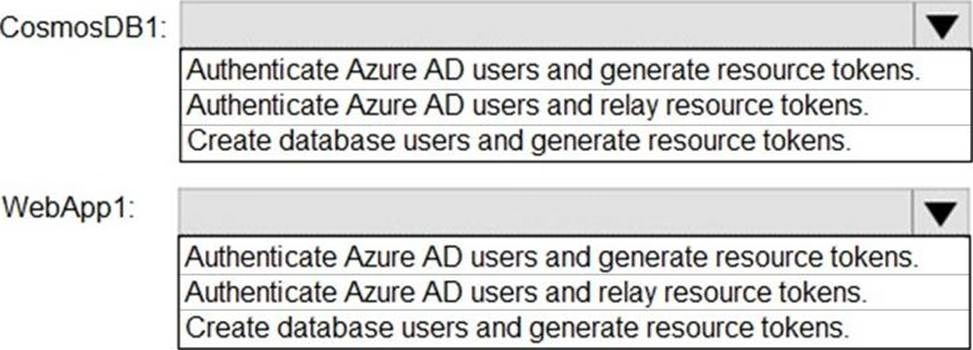
HOTSPOT
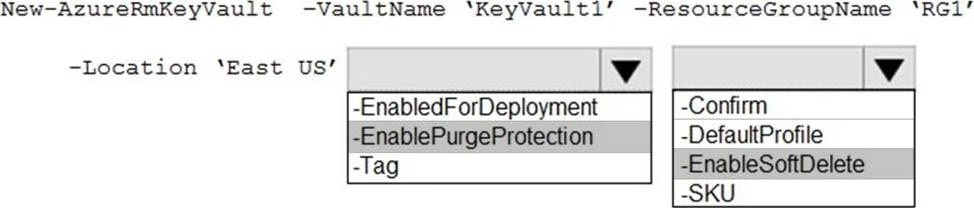
You need to create an Azure key vault. The solution must ensure that any object deleted from the key vault be retained for 90 days.
How should you complete the command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
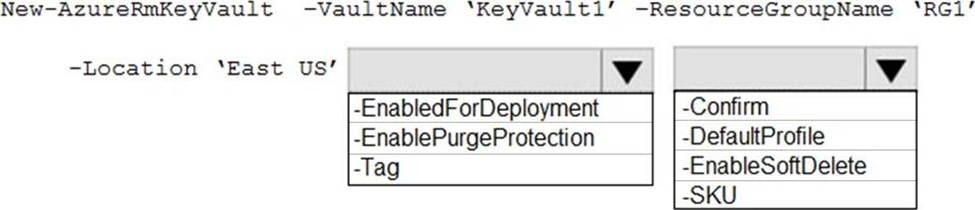
You have an Azure subscription that contains an Azure key vault named Vault1.
In Vault1, you create a secret named Secret1.
An application developer registers an application in Azure Active Directory (Azure AD).
You need to ensure that the application can use Secret1.
What should you do?
- A . In Azure AD, create a role.
- B . In Azure Key Vault, create a key.
- C . In Azure Key Vault, create an access policy.
- D . In Azure AD, enable Azure AD Application Proxy.
You have an Azure SQL database.
You implement Always Encrypted.
You need to ensure that application developers can retrieve and decrypt data in the database.
Nantes’s of information should you provide to the developers? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . a stored access policy
- B . a shared access signature (SAS)
- C . the column encryption key
- D . user credentials
- E . the column master key
You have a hybrid configuration of Azure Active Directory (Azure AD).
All users have computers that run Windows 10 and are hybrid Azure AD joined.
You have an Azure SQL database that is configured to support Azure AD authentication.
Database developers must connect to the SQL database by using Microsoft SQL Server Management Studio
(SSMS) and authenticate by using their on-premises Active Directory account.
You need to tell the developers which authentication method to use to connect to the SQL database from
SSMS. The solution must minimize authentication prompts.
Which authentication method should you instruct the developers to use?
- A . SQL Login
- B . Active Directory C Universal with MFA support
- C . Active Directory C Integrated
- D . Active Directory C Password
You have a hybrid configuration of Azure Active Directory (Azure AD).
All users have computers that run Windows 10 and are hybrid Azure AD joined.
You have an Azure SQL database that is configured to support Azure AD authentication.
Database developers must connect to the SQL database by using Microsoft SQL Server Management Studio
(SSMS) and authenticate by using their on-premises Active Directory account.
You need to tell the developers which authentication method to use to connect to the SQL database from
SSMS. The solution must minimize authentication prompts.
Which authentication method should you instruct the developers to use?
- A . SQL Login
- B . Active Directory C Universal with MFA support
- C . Active Directory C Integrated
- D . Active Directory C Password
You have a hybrid configuration of Azure Active Directory (Azure AD).
All users have computers that run Windows 10 and are hybrid Azure AD joined.
You have an Azure SQL database that is configured to support Azure AD authentication.
Database developers must connect to the SQL database by using Microsoft SQL Server Management Studio
(SSMS) and authenticate by using their on-premises Active Directory account.
You need to tell the developers which authentication method to use to connect to the SQL database from
SSMS. The solution must minimize authentication prompts.
Which authentication method should you instruct the developers to use?
- A . SQL Login
- B . Active Directory C Universal with MFA support
- C . Active Directory C Integrated
- D . Active Directory C Password
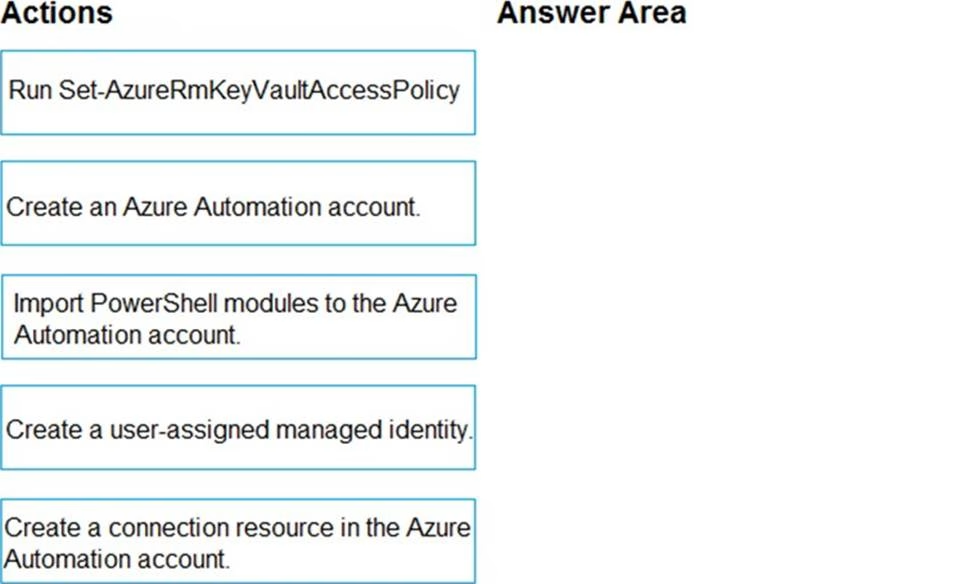
DRAG DROP
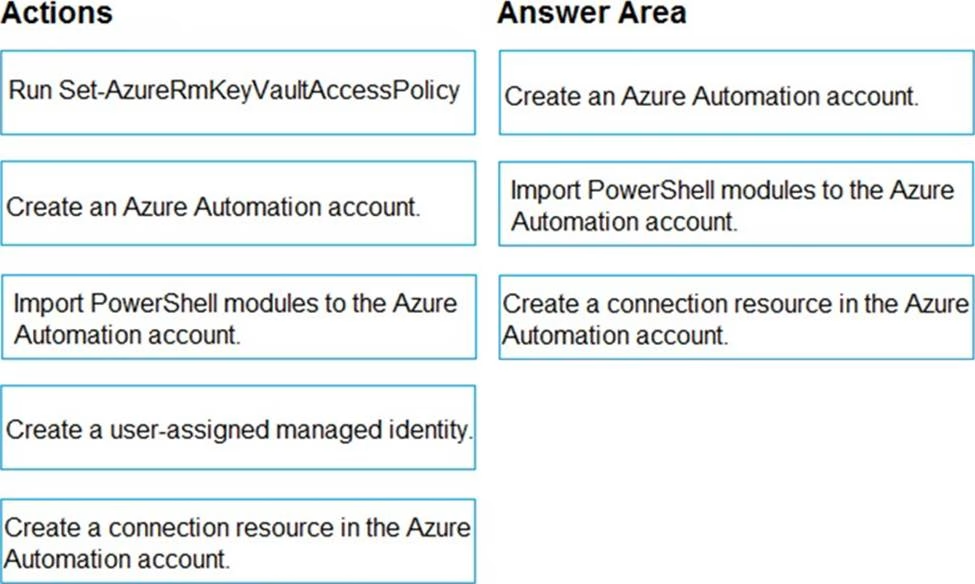
You have an Azure subscription named Sub1 that contains an Azure Storage account named Contosostorage1 and an Azure key vault named Contosokeyvault1.
You plan to create an Azure Automation runbook that will rotate the keys of Contosostorage1 and store them in Contosokeyvault1.
You need to implement prerequisites to ensure that you can implement the runbook.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure SQL Database server named SQL1.
You plan to turn on Advanced Threat Protection for SQL1 to detect all threat detection types.
Which action will Advanced Threat Protection detect as a threat?
- A . A user updates more than 50 percent of the records in a table.
- B . A user attempts to sign as SELECT * from table1.
- C . A user is added to the db_owner database role.
- D . A user deletes more than 100 records from the same table.
Latest AZ-500 Dumps Valid Version with 278 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


May i ask about where to get the AZ-500 Exam lab that contains 12 Questions?
Thank you.