Microsoft AZ-304 Microsoft Azure Architect Design Online Training
Microsoft AZ-304 Online Training
The questions for AZ-304 were last updated at Feb 25,2026.
- Exam Code: AZ-304
- Exam Name: Microsoft Azure Architect Design
- Certification Provider: Microsoft
- Latest update: Feb 25,2026
You manage an Azure environment for a company. The environment has over 25,000 licensed users and 100 mission-critical applications. You need to recommend a solution that provides advanced user threat detection and remediation strategies.
What should you recommend?
- A . Azure Active Directory (Azure AD) Identity Protection
- B . Azure Active Directory Federation Services (AD FS)
- C . Azure Active Directory (Azure AD) authentication
- D . Microsoft Identity Manager
- E . Azure Active Directory (Azure AD) Connect
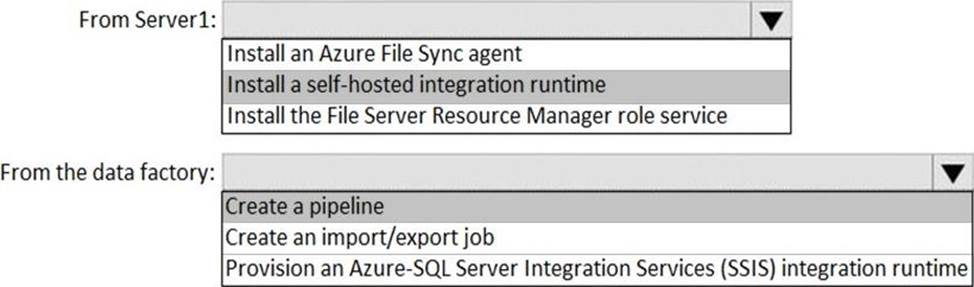
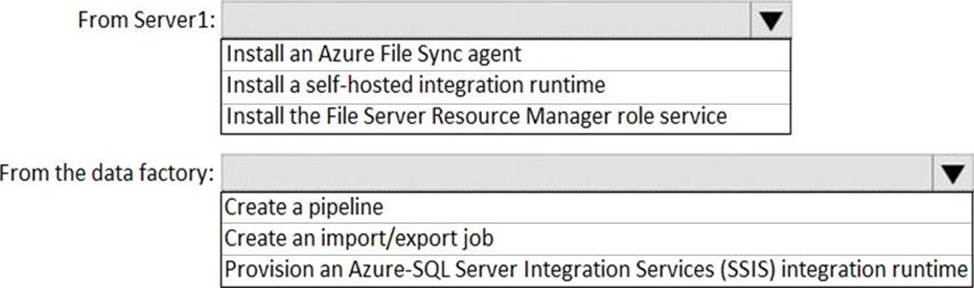
HOTSPOT
Your on-premises network contains a file server named Server1 that stores 500 GB of data.
You need to use Azure Data Factory to copy the data from Server1 to Azure Storage.
You add a new data factory.
What should you do next? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains a storage account.
An application sometimes writes duplicate files to the storage account.
You have a PowerShell script that identifies and deletes duplicate files in the storage account. Currently, the script is run manually after approval from the operations manager.
You need to recommend a serverless solution that performs the following actions:
✑ Runs the script once an hour to identify whether duplicate files exist
✑ Sends an email notification to the operations manager requesting approval to delete the duplicate files
✑ Processes an email response from the operations manager specifying whether the deletion was approved
✑ Runs the script if the deletion was approved
What should you include in the recommendation?
- A . Azure Logic Apps and Azure Functions
- B . Azure Pipelines and Azure Service Fabric
- C . Azure Logic Apps and Azure Event Grid
- D . Azure Functions and Azure Batch
You have 100 servers that run Windows Server 2012 R2 and host Microsoft SQL Server 2012 R2 instances.
The instances host databases that have the following characteristics:
✑ The largest database is currently 3 TB. None of the databases will ever exceed 4 TB.
✑ Stored procedures are implemented by using CLR.
You plan to move all the data from SQL Server to Azure.
You need to recommend an Azure service to host the databases.
The solution must meet the following requirements:
✑ Whenever possible, minimize management overhead for the migrated databases.
✑ Minimize the number of database changes required to facilitate the migration.
✑ Ensure that users can authenticate by using their Active Directory credentials.
What should you include in the recommendation?
- A . Azure SQL Database single databases
- B . Azure SQL Database Managed Instance
- C . Azure SQL Database elastic pools
- D . SQL Server 2016 on Azure virtual machines
Your company, named Contoso, Ltd, implements several Azure logic apps that have HTTP triggers: The logic apps provide access to an on-premises web service.
Contoso establishes a partnership with another company named Fabrikam, Inc.
Fabrikam does not have an existing Azure Active Directory (Azure AD) tenant and uses third-party OAuth 2.0 identity management to authenticate its users.
Developers at Fabrikam plan to use a subset of the logics apps to build applications that will integrate with the on-premises web service of Contoso.
You need to design a solution to provide the Fabrikam developers with access to the logic apps.
The solution must meet the following requirements:
✑ Requests to the logic apps from the developers must be limited to lower rates than the requests from the users at Contoso.
✑ The developers must be able to rely on their existing OAuth 2.0 provider to gain access to the logic apps.
✑ The solution must NOT require changes to the logic apps.
✑ The solution must NOT use Azure AD guest accounts.
What should you include in the solution?
- A . Azure AD business-to-business (B2B)
- B . Azure Front Door
- C . Azure API Management
- D . Azure AD Application Proxy
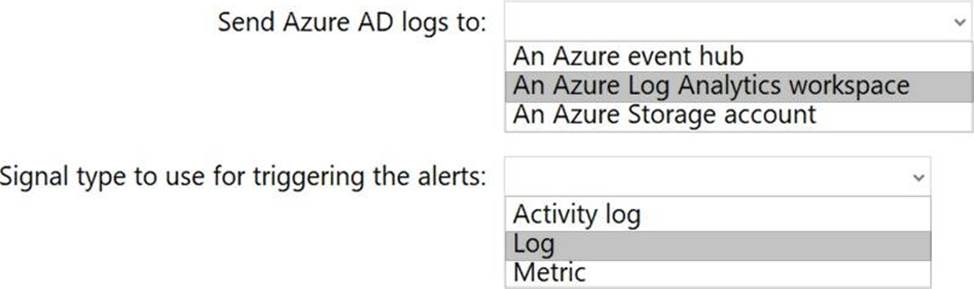
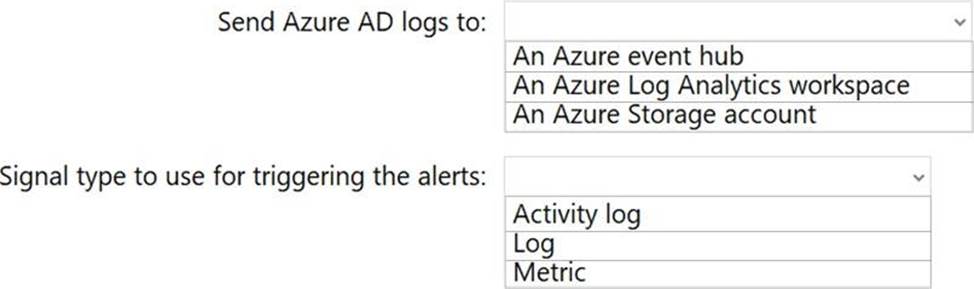
HOTSPOT
You have an Azure Active Directory (Azure AD) tenant.
You plan to use Azure Monitor to monitor user sign-ins and generate alerts based on specific user sign-in events.
You need to recommend a solution to trigger the alerts based on the events.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains several administrative user accounts. You need to recommend a solution to identify which administrative user accounts have NOT signed in during the previous 30 days.
Which service should you include in the recommendation?
- A . Azure AD Identity Protection
- B . Azure AD Privileged identity Management (PIM)
- C . Azure Advisor
- D . Azure Activity log
You have multiple Anne deployments.
You plan to implement Azure Blueprints.
Which artifact types can be added to a blueprint?
- A . Policy assignment Resource group, Role assignment virtual machines, and virtual networks only
- B . Subscriptions. tenants. Resource group, and Key vault only
- C . Subscriptions. tenants. Resource group, and Azure Active Directory only
- D . Azure Resource Manager template (Subscription). Policy assignment Resource group, and Role assignment only
You have an on-premises network to which you deploy a virtual appliance.
You plan to deploy several Azure virtual machines and connect the on-premises network to Azure by using a Site-to-Site connection.
All network traffic that will be directed from the Azure virtual machines to a specific subnet must flow through the virtual appliance.
You need to recommend solutions to manage network traffic.
Which two options should you recommend? Each correct answer presents a complete solution.
- A . Configure Azure Traffic Manager.
- B . Implement an Azure virtual network.
- C . Implement Azure ExpressRoute.
- D . Configure a routing table.
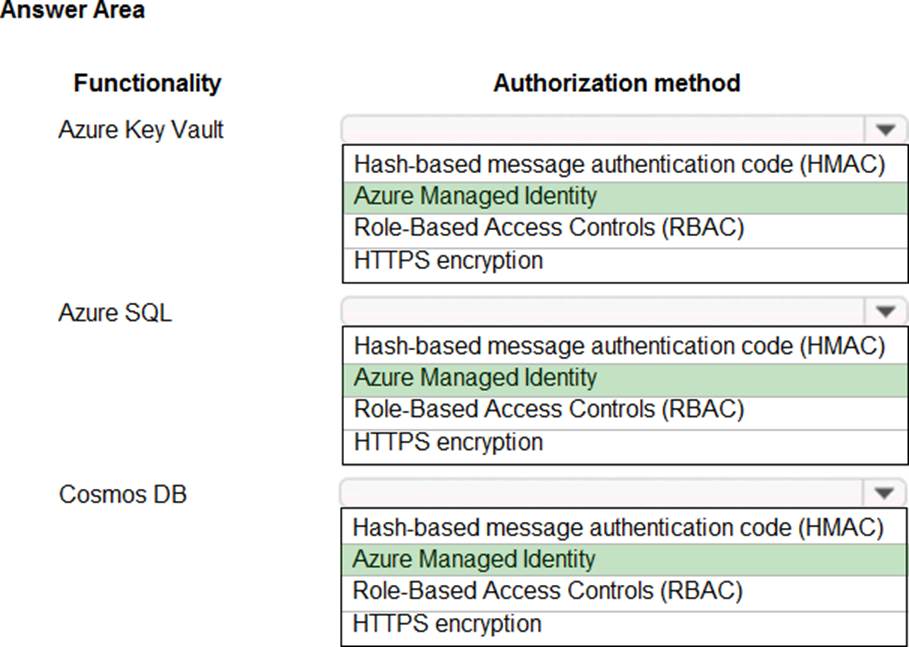
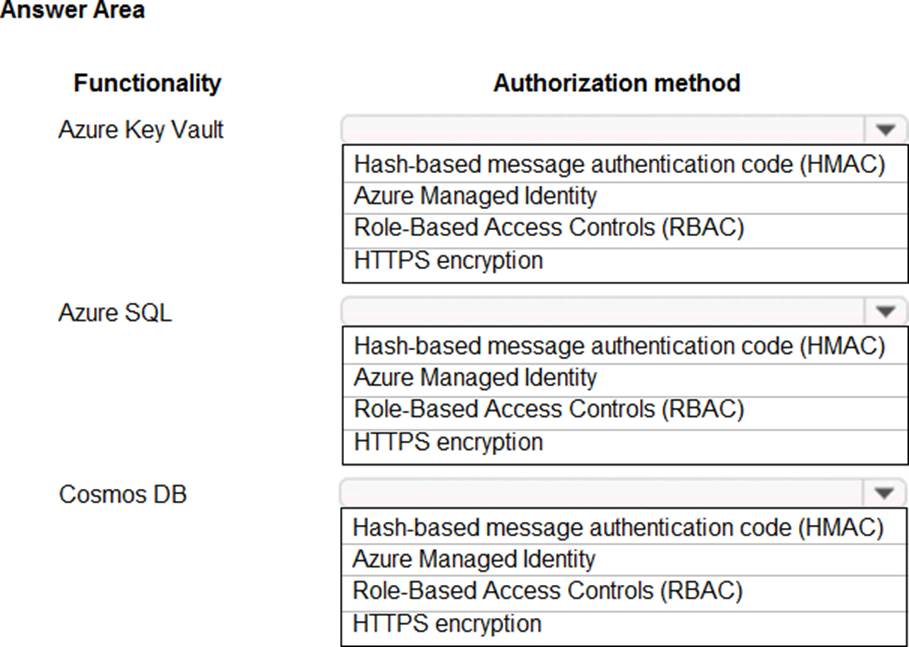
HOTSPOT
You are building an application that will run in a virtual machine (VM). The application will use Azure Managed Identity.
The application uses Azure Key Vault, Azure SQL Database, and Azure Cosmos DB.
You need to ensure the application can use secure credentials to access these services.
Which authentication method should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Latest AZ-304 Dumps Valid Version with 238 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund