Microsoft AZ-301 Microsoft Azure Architect Design Online Training
Microsoft AZ-301 Online Training
The questions for AZ-301 were last updated at Feb 26,2026.
- Exam Code: AZ-301
- Exam Name: Microsoft Azure Architect Design
- Certification Provider: Microsoft
- Latest update: Feb 26,2026
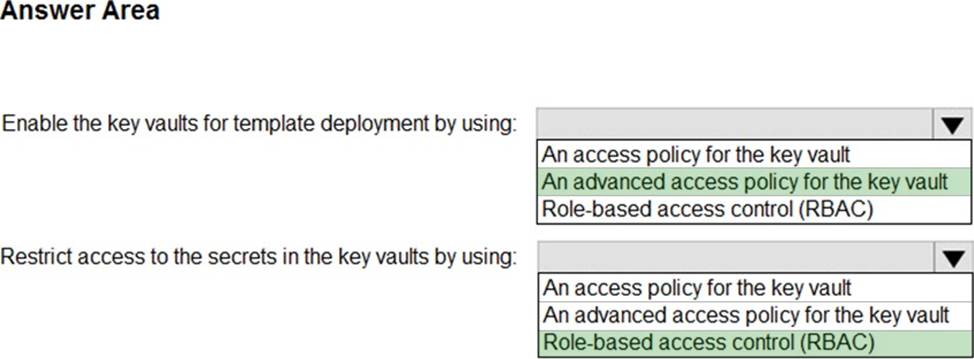
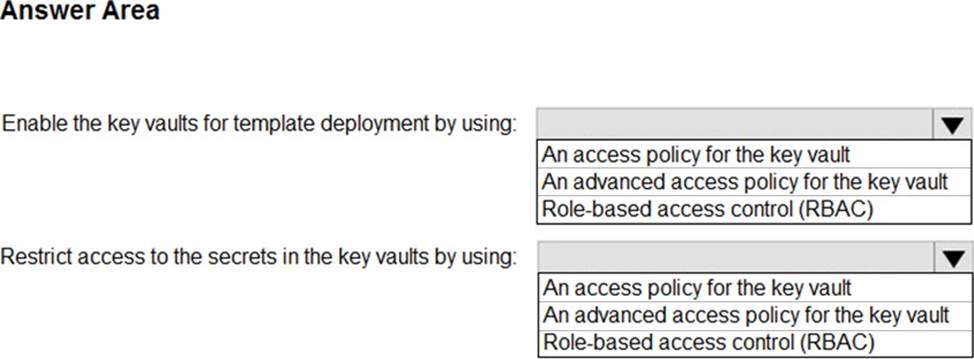
HOTSPOT
You deploy Azure service by using Azure Resources Manager templates. The template reference secrets are stored in Azure key Vault.
You need to recommend a solution for accessing the secrets during deployments.
The solution must prevent the users who are performing the deployments from accessing the secrets in the key vault directly.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
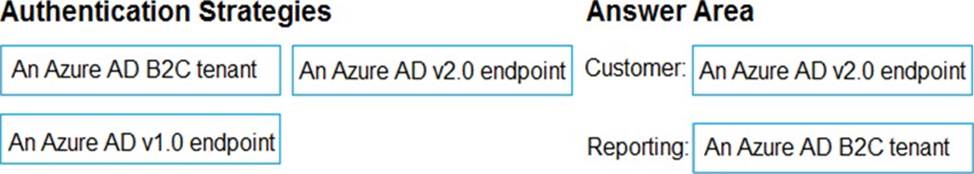
DRAG DROP
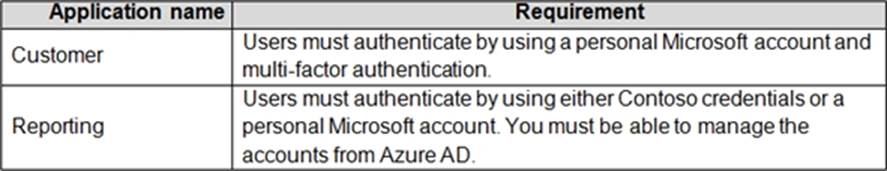
A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that uses the Basic license. You plan to deploy two applications to Azure.
The applications have the requirements shown in the following table.
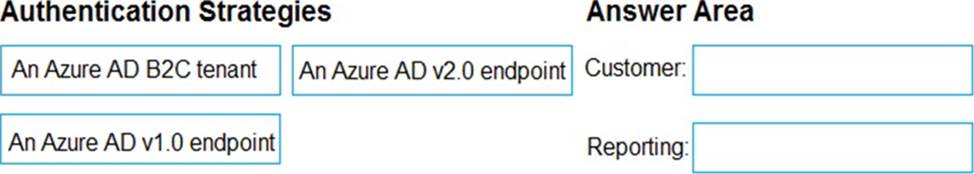
Which authentication strategy should you recommend for each application? To answer, drag the appropriate authentication strategies to the correct applications. Each authentication strategy may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
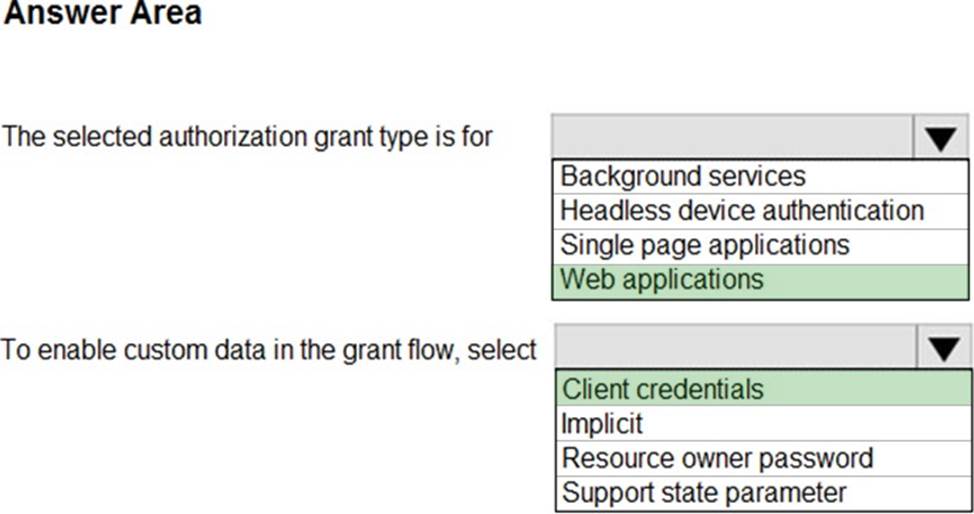
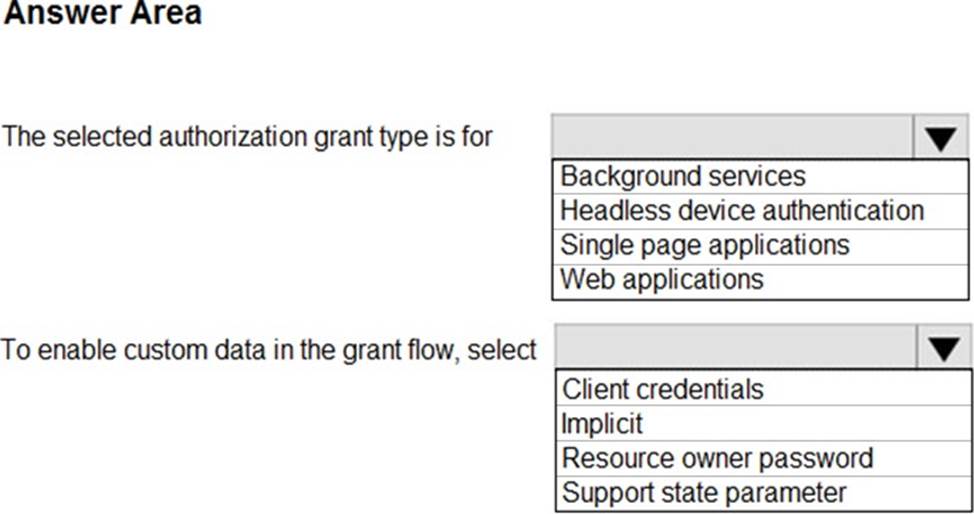
HOTSPOT
You configure OAuth2 authorization in API Management as shown in the exhibit.
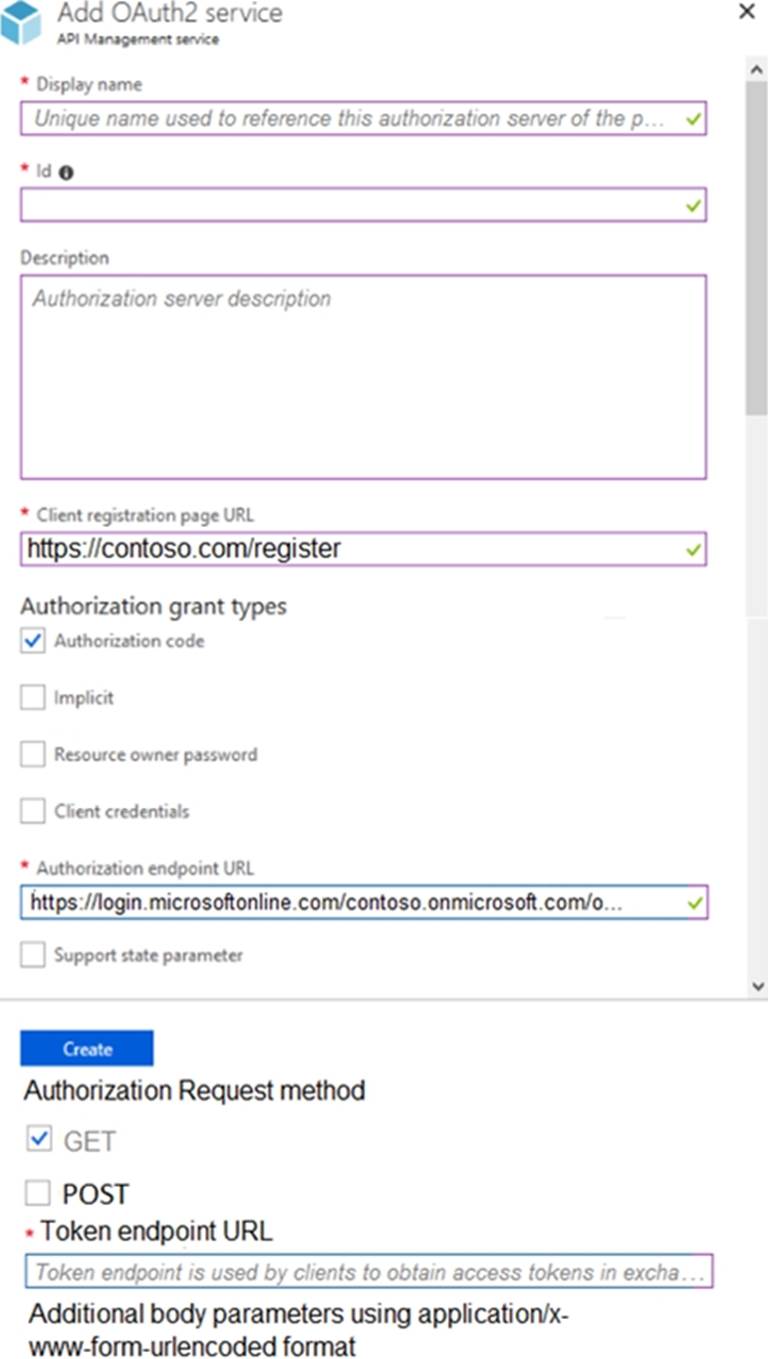
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
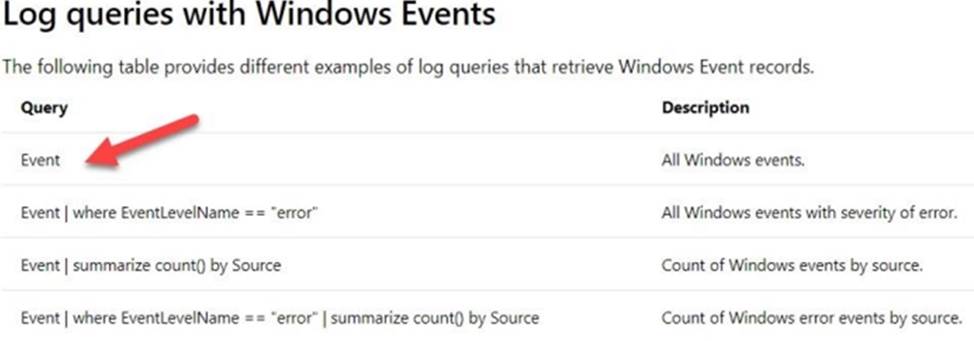
A company has deployed several applications across Windows and Linux Virtual machines in Azure. Log Analytics are being used to send the required data for alerting purposes for the Virtual Machines.
You need to recommend which tables need to be queried for security related queries.
Which of the following would you query for events from Windows Event Logs?
- A . Azure Activity
- B . Azure Diagnostics
- C . Event
- D . Syslog
Note: This question is a part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant named contoso.com. The tenant contains a group named Group1. Group1 contains all the administrative user accounts.
You discover several login attempts to the Azure portal from countries where administrative users do NOT work.
You need to ensure that all login attempts to the Azure portal from those countries require Azure Multi-Factor Authentication (MFA).
Solution: Implement Azure AD Identity Protection for Group1.
Does this solution meet the goal?
- A . Yes
- B . No
You are designing a solution that will host 20 different web applications.
You need to recommend a solution to secure the web applications with a firewall that protects against common web-based attacks including SQL injection, cross-site scripting attacks, and session hijacks. The solution must minimize costs.
Which three Azure features should you recommend? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . VPN Gateway
- B . URL-based content routing
- C . Multi-site routing
- D . Web Application Firewall (WAF)
- E . Azure ExpressRoute
- F . Azure Application Gateway
Note: This question is a part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Install and configure the Microsoft Monitoring Agent and the Dependency Agent on all VMs. Use the Wire Data solution in Azure Monitor to analyze the network traffic.
Does the solution meet the goal?
- A . Yes
- B . No
A company has deployed several applications across Windows and Linux Virtual machines in Azure. Log Analytics are being used to send the required data for alerting purposes for the Virtual Machines.
You need to recommend which tables need to be queried for security related queries.
Which of the following would you query for events from Linux system logging?
- A . Azure Activity
- B . Azure Diagnostics
- C . Event
- D . Syslog
A company named Contoso, Ltd. has an Azure Active Directory (Azure AD) tenant that is integrated with Microsoft Office 365 and an Azure subscription.
Contoso has an on-premises identity infrastructure. The infrastructure includes servers that run Active Directory Domain Services (AD DS), Active Directory Federation Services (AD FS), Azure AD Connect, and Microsoft Identity Manager (MIM).
Contoso has a partnership with a company named Fabrikam, Inc. Fabrikam has an Active Directory forest and an Office 365 tenant. Fabrikam has the same on-premises identity infrastructure as Contoso.
A team of 10 developers from Fabrikam will work on an Azure solution that will be hosted in the Azure subscription of Contoso. The developers must be added to the Contributor role for a resource group in the Contoso subscription.
You need to recommend a solution to ensure that Contoso can assign the role to the 10 Fabrikam developers. The solution must ensure that the Fabrikam developers use their existing credentials to access resources.
What should you recommend?
- A . Configure an AD FS relying party trust between the Fabrikam and Contoso AD FS infrastructures.
- B . Configure an organization relationship between the Office 365 tenants of Fabrikam and Contoso.
- C . In the Azure AD tenant of Contoso, create guest accounts for the Fabrikam developers.
- D . Configure a forest trust between the on-premises Active Directory forests of Contoso and Fabrikam.
You have an Azure Active Directory (Azure AD) tenant named contoso.com that has a security group named Group1. Group1 is configured for assigned membership. Group1 has 50 members, including 20 guest users.
You need to recommend a solution for evaluating the membership of Group1.
The solution must meet the following requirements:
– The evaluation must be repeated automatically every three months.
– Every member must be able to report whether they need to be in Group1.
– Users who report that they do not need to be in Group1 must be removed from Group1 automatically
– Users who do not report whether they need to be in Group1 must be removed from Group1 automatically.
What should you include in the recommendation?
- A . Implement Azure AD Identity Protection.
- B . Change the Membership type of Group1 to Dynamic User.
- C . Create an access review.
- D . Implement Azure AD Privileged Identity Management.
Latest AZ-301 Dumps Valid Version with 293 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund