Microsoft AZ-301 Microsoft Azure Architect Design Online Training
Microsoft AZ-301 Online Training
The questions for AZ-301 were last updated at Feb 27,2026.
- Exam Code: AZ-301
- Exam Name: Microsoft Azure Architect Design
- Certification Provider: Microsoft
- Latest update: Feb 27,2026
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains several administrative user accounts.
You need to recommend a solution to identify which administrative user accounts have NOT signed in during the previous 30 days.
Which service should you include in the recommendation?
- A . Azure AD Identity Protection
- B . Azure Activity Log
- C . Azure Advisor
- D . Azure AD Privileged Identity Management (PIM)
HOTSPOT
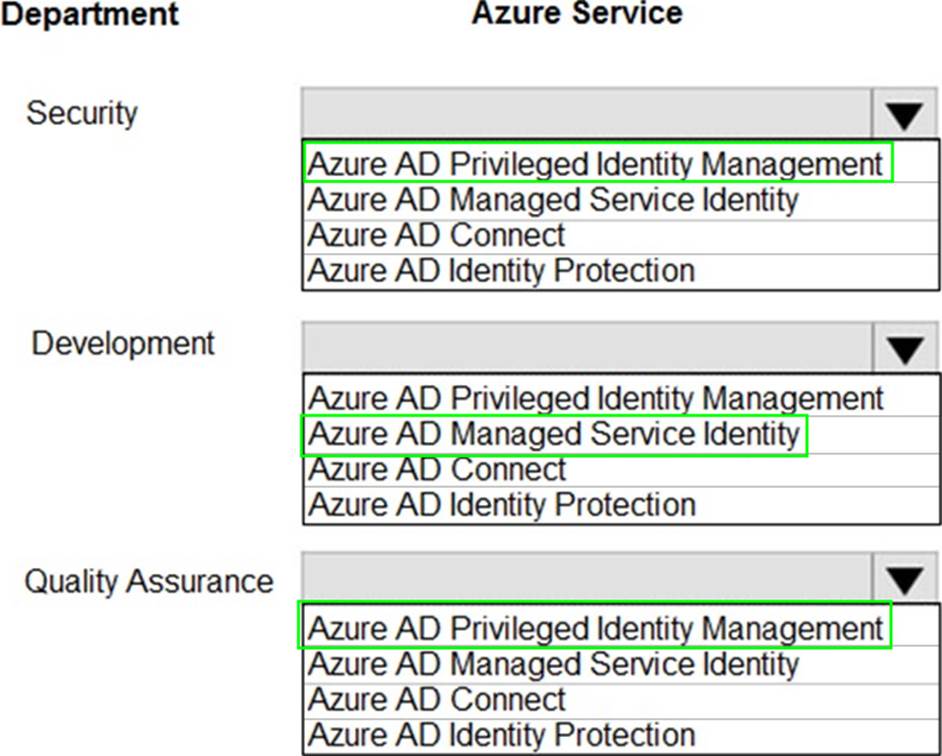
Your organization has developed and deployed several Azure App Service Web and API applications. The applications use Azure Key Vault to store several authentication, storage account, and data encryption keys.
Several departments have the following requests to support the applications:
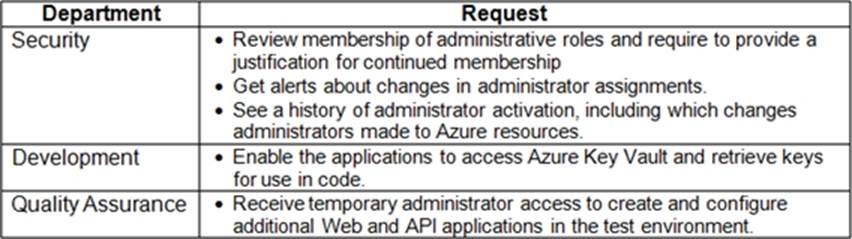
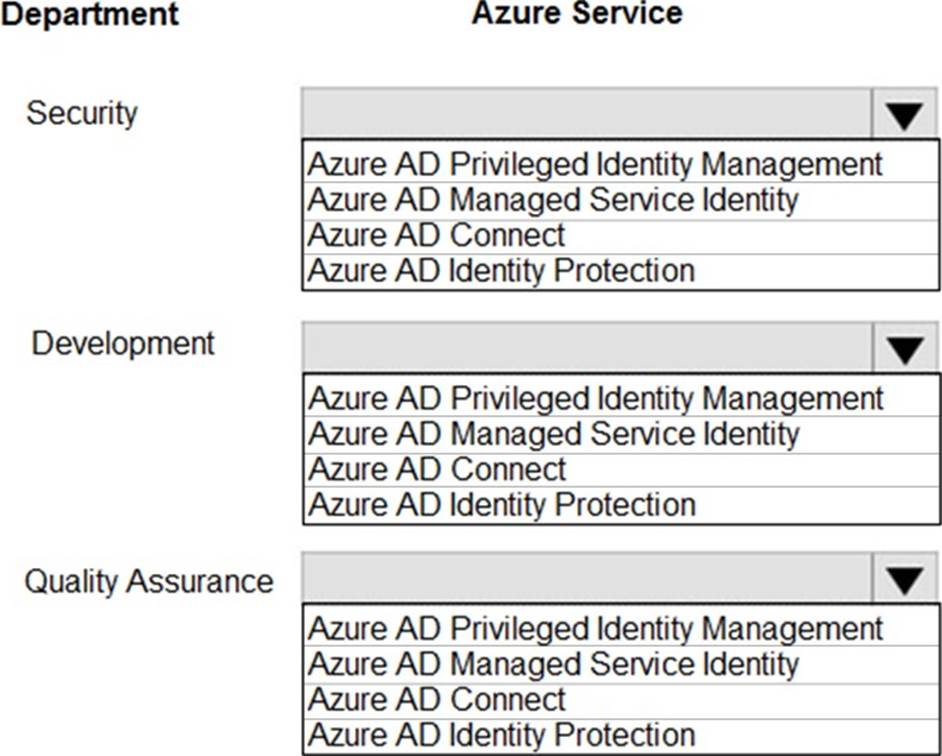
You need to recommend the appropriate Azure service for each department request.
What should you recommend? To answer, configure the appropriate options in the dialog box in the answer area. NOTE: Each correct selection is worth one point.
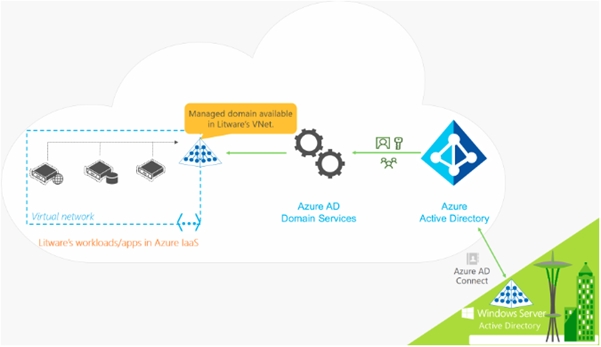
You manage a single-domain, on-premises Active Directory forest named contoso.com. The forest functional level is Windows Server 2016. You have several on-premises applications that depend on Active Directory. You plan to migrate the applications to Azure. You need to recommend an identity solution for the applications.
The solution must meet the following requirements:
– Eliminate the need for hybrid network connectivity.
– Minimize management overhead for Active Directory.
What should you recommend?
- A . In Azure, deploy an additional child domain to the contoso.com forest.
- B . In Azure, deploy additional domain controllers for the contoso.com domain.
- C . Implement a new Active Directory forest in Azure.
- D . Implement Azure Active Directory Domain Services (Azure AD DS).
Note: This question is a part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription named Project1. Only a group named Project1admins is assigned roles in the Project1 subscription. The Project1 subscription contains all the resources for an application named Application1.
Your company is developing a new application named Application2. The members of the Application2 development team belong to an Azure Active Directory (Azure AD) group named App2Dev.
You identify the following requirements for Application2:
– The members of App2Dev must be prevented from changing the role assignments in Azure.
– The members of App2Dev must be able to create new Azure resources required by Application2.
– All the required role assignments for Application2 will be performed by the members of Project1admins.
You need to recommend a solution for the role assignments of Application2.
Solution: In Project1, create a network security group (NSG) named NSG1. Assign Project1admins the Owner role for NSG1. Assign the App2Dev the Contributor role for NSG1.
Does this meet the goal?
- A . Yes
- B . No
HOTSPOT
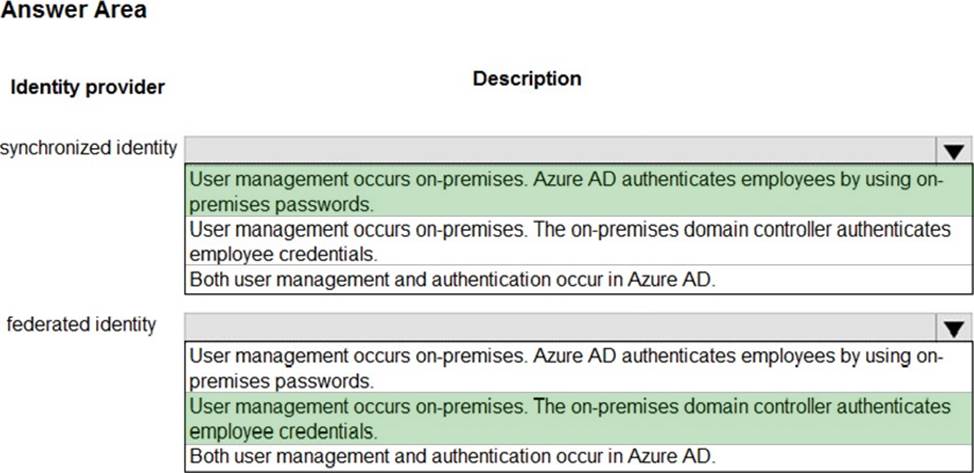
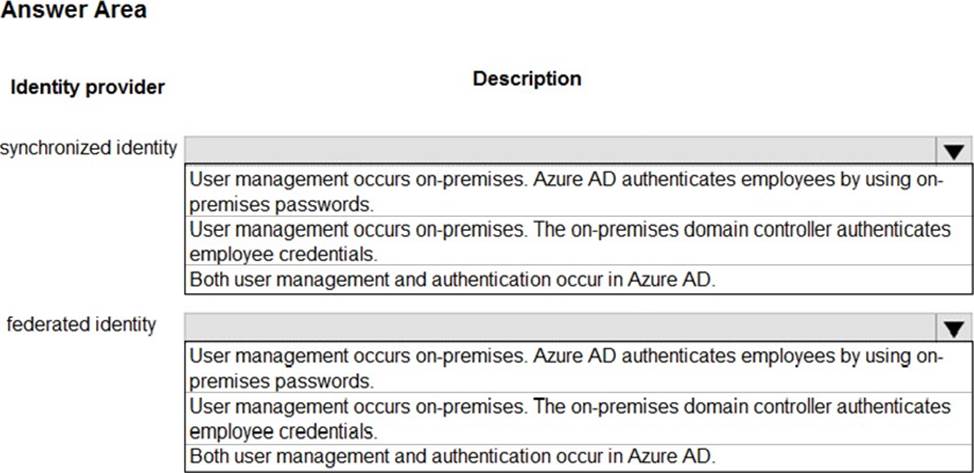
You manage a network that includes an on-premises Active Directory Domain Services domain and an Azure Active Directory (Azure AD).
Employees are required to use different accounts when using on-premises or cloud resources. You must recommend a solution that lets employees sign in to all company resources by using a single account. The solution must implement an identity provider.
You need provide guidance on the different identity providers.
How should you describe each identity provider? To answer, select the appropriate description from each list in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is a part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that contains a resource group named RG1.
You create an Azure Active Directory (Azure AD) group named ResearchUsers that contains the user accounts of all researchers.
You need to recommend a solution that meets the following requirements:
– The researchers must be allowed to create Azure virtual machines.
– The researchers must only be able to create Azure virtual machines by using specific Azure Resource Manager templates.
Solution: On RG1, assign a custom role-based access control (RBAC) role to the ResearchUsers group.
Does this meet the goal?
- A . Yes
- B . No
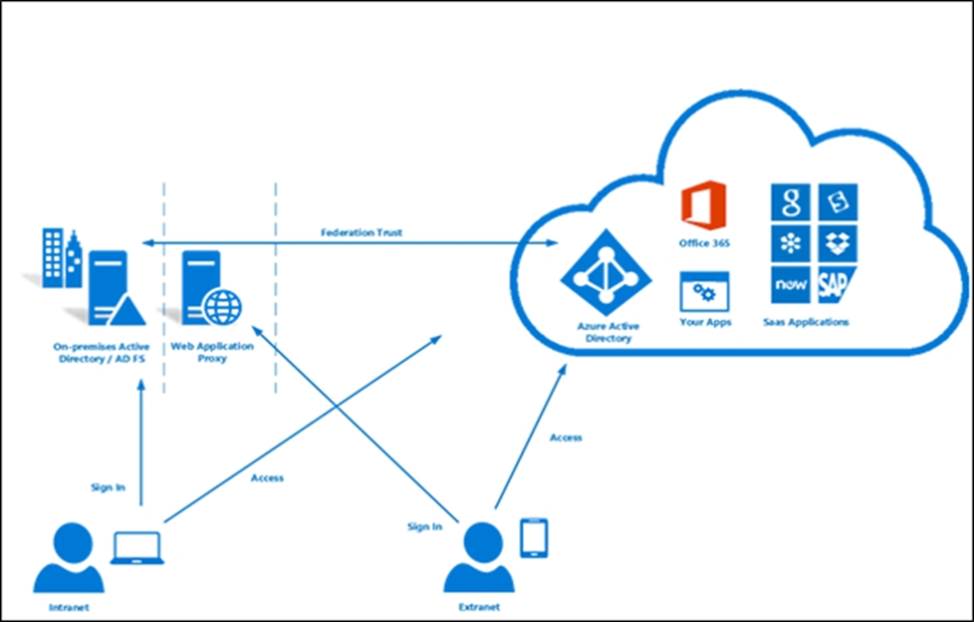
A company deploys Azure Active Directory (Azure AD) Connect to synchronize identity information from their on-premises Active Directory Domain Services (AD DS) directory to their Azure AD tenant. The identity information that is synchronized includes user accounts, credential hashes for authentication (password sync), and group memberships. The company plans to deploy several Windows and Linux virtual machines (VMs) to support their applications.
The VMs have the following requirements:
– Support domain join, LDAP read, LDAP bind, NTLM and Kerberos authentication, and Group Policy.
– Allow users to sign in to the domain using their corporate credentials and connect remotely to the VM by using Remote Desktop.
You need to support the VM deployment.
Which service should you use?
- A . Azure AD Domain Services
- B . Azure AD Privileged Identity Management
- C . Azure AD Managed Service Identity
- D . Active Directory Federation Services (AD FS)
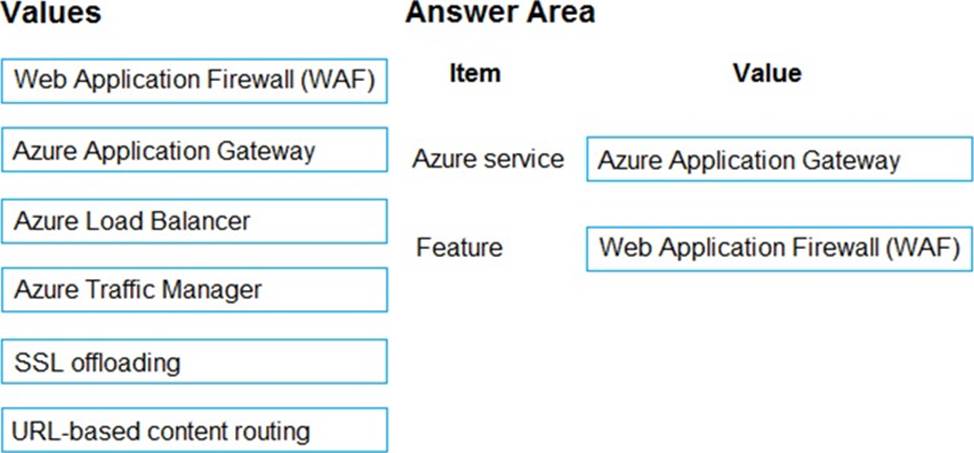
DRAG DROP
A company has an existing web application that runs on virtual machines (VMs) in Azure.
You need to ensure that the application is protected from SQL injection attempts and uses a layer-7 load balancer. The solution must minimize disruption to the code for the existing web application.
What should you recommend? To answer, drag the appropriate values to the correct items. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
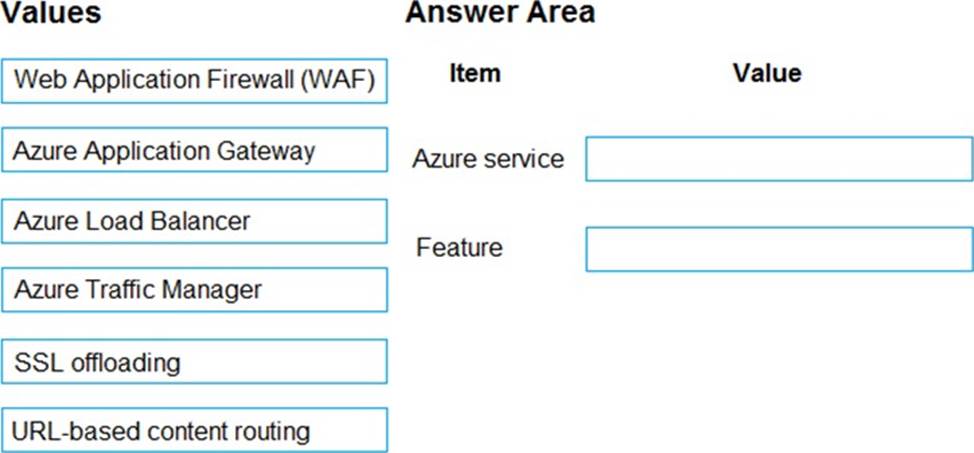
Note: This question is a part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Use the Azure traffic analytics solution in Azure Log Analytics to analyze the network traffic.
Does the solution meet the goal?
- A . Yes
- B . No
Note: This question is a part of series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your company has deployed several virtual machines (VMs) on-premises and to Azure. Azure ExpressRoute has been deployed and configured for on-premises to Azure connectivity.
Several VMs are exhibiting network connectivity issues.
You need to analyze the network traffic to determine whether packets are being allowed or denied to the VMs.
Solution: Use Azure Network Watcher to run IP flow verify to analyze the network traffic.
Does the solution meet the goal?
- A . Yes
- B . No
Latest AZ-301 Dumps Valid Version with 293 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund