Microsoft 70-744 Securing Windows Server 2016 Online Training
Microsoft 70-744 Online Training
The questions for 70-744 were last updated at Feb 16,2026.
- Exam Code: 70-744
- Exam Name: Securing Windows Server 2016
- Certification Provider: Microsoft
- Latest update: Feb 16,2026
DRAG DROP
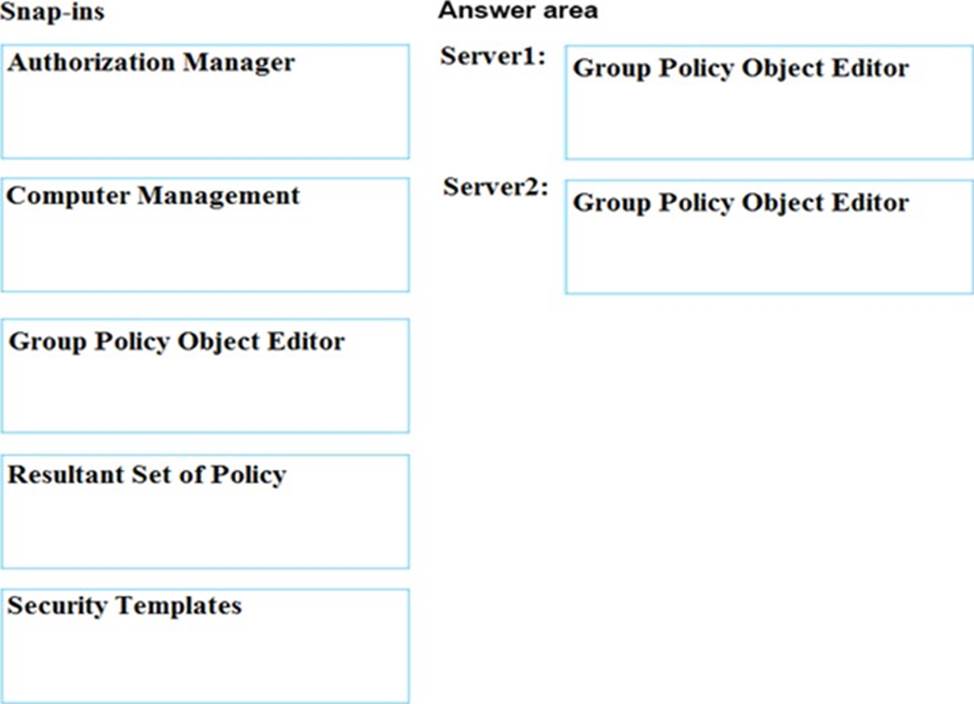
You have two servers named Server1 and Server2 that run Windows Server 2016. The servers are in a workgroup. You need to create a security template that contains the security settings of Server1 and to apply the template to Server2. The solution must minimize administrative effort.
Which snap-in should you use for each server? To answer, drag the appropriate snap-ins to the correct servers. Each snap-in may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point. Select and Place:

You are creating a Nano Server image for the deployment of 10 servers.
You need to configure the servers as guarded hosts that use Trusted Platform Module (TPM) attestation.
Which three packages should you include in the Nano Server image? Each correct answer presents part of the solution.
- A . Microsoft-NanoServer-SCVMM-Compute-Package
- B . Microsoft-NanoServer-SecureStartup-Package
- C . Microsoft-NanoServer-Compute-Package
- D . Microsoft-NanoServer-ShieldedVM-Package
- E . Microsoft-NanoServer-Storage-Package
- F . Microsoft-NanoServer-SCVMM- Package
Your network contains an Active Directory domain named contoso.com. The domain contains several shielded virtual machines. You deploy a new server named Server1 that runs Windows Server 2016. You install the Hyper-V server role on Server1. You need to ensure that you can host shielded virtual machines on Server1.
What should you install on Server1?
- A . Host Guardian Hyper-V Support
- B . the Windows Biometric Framework (WBF)
- C . VM Shielding Tools for Fabric Management
- D . BitLocker Network Unlock
Your network contains an Active Directory domain named contoso.com. You deploy a server named Server1 that runs Windows Server 2016. Server1 is in a workgroup. You need to collect the logs from Server1 by using Log Analytics in Microsoft Operations Management Suite (OMS).
What should you do first?
- A . Create an event subscription
- B . Create a Data Collector-Set
- C . Install Microsoft Monitoring Agent on Server1
- D . Join Server1 to the domain
HOTSPOT
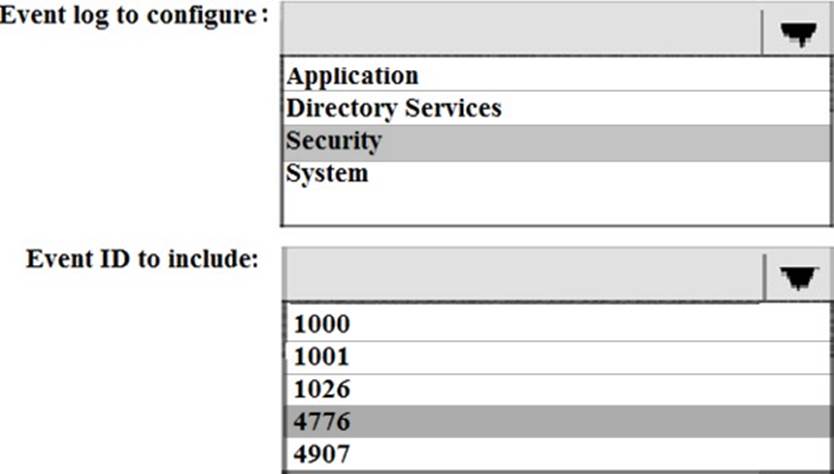
Your network contains an Active Directory domain named contoso.com. You are deploying Microsoft Advanced Threat Analytics (ATA) to the domain. You install the ATA Gateway on a server named Server1. To assist in detecting Pass-the-Hash attacks, you plan to configure ATA Gateway to collect events. You need to configure the query filter for event subscriptions on Server1.
How should you configure the query filter? To answer, select the appropriate options in the answer are.
Note: This question is part of a series of questions that use the same scenario. For yourconvenience, the scenario is repeated in each question. Each question presents a different goaland answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your company has a marketing department.
The network contains an Active Directory domain named contoso.com.
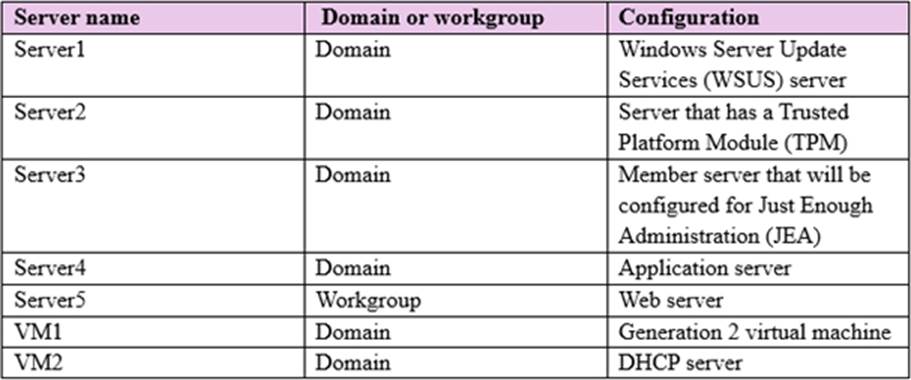
The domain contains the servers configured as shown in the following table.
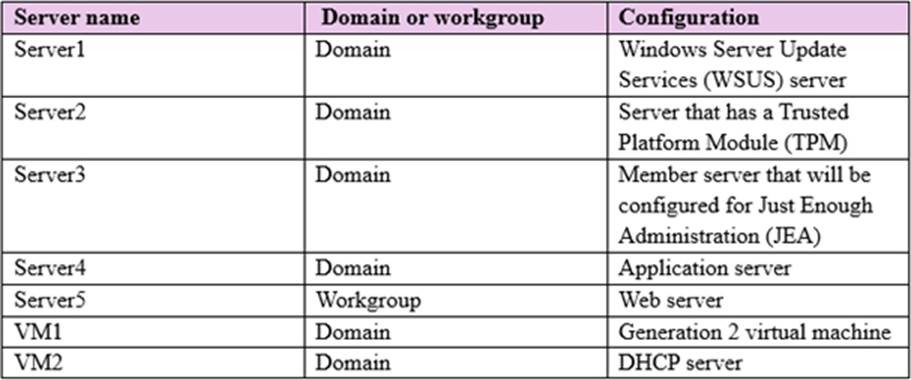
All servers run Windows Server 2016. All client computers run Windows 10 and are domain members. All laptops are protected by using BitLocker Drive Encryption (BitLocker).
You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers. An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1. A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
End of repeated scenario.
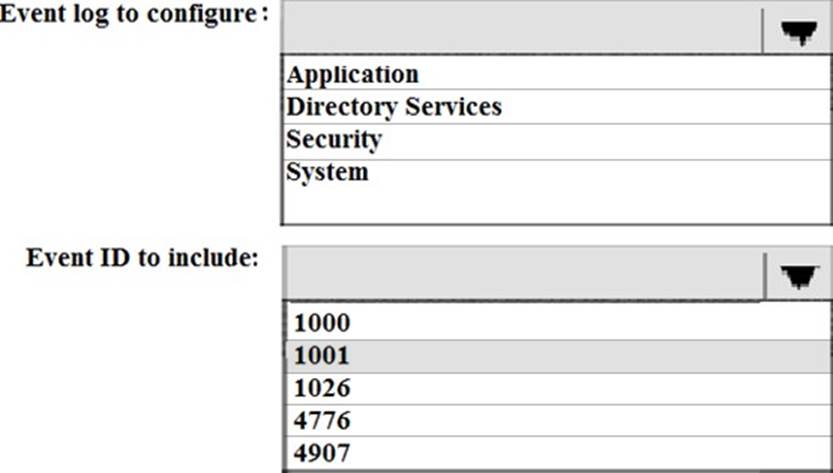
You enable deep script block logging for Windows PowerShell.
In which event log will PowerShell code that is generated dynamically appear?
- A . Applications and Services Logs/Windows PowerShell
- B . Windows Logs/Security
- C . Applications and Services Logs/Microsoft/Windows/PowerShell/Operational
- D . Windows Logs/Application
Note: This question is part of a series of questions that use the same scenario. For yourconvenience, the scenario is repeated in each question. Each question presents a different goaland answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your company has a marketing department.
The network contains an Active Directory domain named contoso.com.
The domain contains the servers configured as shown in the following table.
All servers run Windows Server 2016. All client computers run Windows 10 and are domain members. All laptops are protected by using BitLocker Drive Encryption (BitLocker).
You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers. An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1. A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
End of repeated scenario.
You need to create a Role Capability file on Server3.
Which file should you create?
- A . File1.ini
- B . File1.ps1
- C . File1.xml
- D . File1.psrc
Note: This question is part of a series of questions that use the same scenario. For yourconvenience, the scenario is repeated in each question. Each question presents a different goaland answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your company has a marketing department.
The network contains an Active Directory domain named contoso.com.
The domain contains the servers configured as shown in the following table.
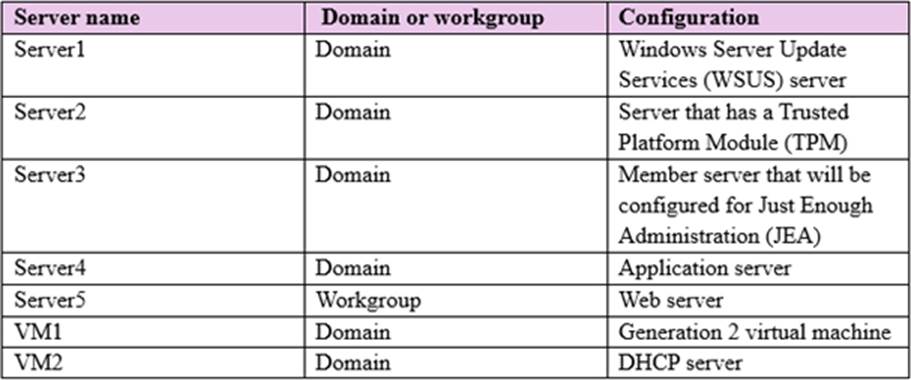
All servers run Windows Server 2016. All client computers run Windows 10 and are domain members. All laptops are protected by using BitLocker Drive Encryption (BitLocker).
You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers. An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1. A GPO named GP2 is linked to OU2.
All computers receive updates from Server1.
You create an update rule named Update1.
End of repeated scenario.
You need to implement BitLocker Network Unlock for all of the laptops.
Which server role should you deploy to the network?
- A . Host Guardian Service
- B . Device Health Attestation
- C . Windows Deployment Services
- D . Network Controller
Note: This question is part of a series of questions that use the same scenario. For yourconvenience, the scenario is repeated in each question. Each question presents a different goaland answer choices, but the text of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your company has a marketing department.
The network contains an Active Directory domain named contoso.com.
The domain contains the servers configured as shown in the following table.
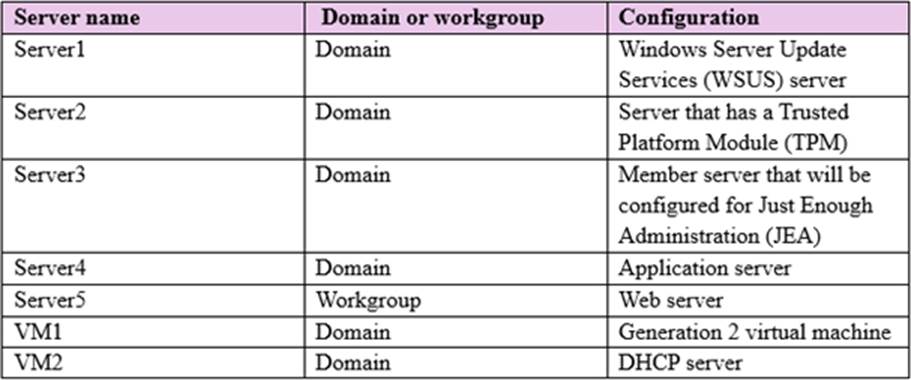
All servers run Windows Server 2016. All client computers run Windows 10 and are domain members. All laptops are protected by using BitLocker Drive Encryption (BitLocker).
You have an organizational unit (OU) named OU1 that contains the computer accounts of application servers. An OU named OU2 contains the computer accounts of the computers in the marketing department. A Group Policy object (GPO) named GP1 is linked to OU1. A GPO named GP2 is linked to OU2.
All computers receive updates from Server1. You create an update rule named Update1.
End of repeated scenario.
You need to ensure that AppLocker rules will apply to the marketing department computers.
What should you do?
- A . From the properties of OU2, modify the COM+ partition Set.
- B . In GP2, configure the Startup type for the Application Identity service.
- C . In GP2, configure the Startup type for the Application Management service.
- D . From the properties of OU2, modify the Security settings.
Your network contains an Active Directory domain named contoso.com. The domain contains a certification authority (CA).
You need to implement code integrity policies and sign them by using certificates issued by the CA.
You plan to use the same certificate to sign policies on multiple computers.
You duplicate the Code Signing certificate template and name the new template CodeIntegrity.
How should you configure the CodeIntegrity template?
- A . Enable the Allow private key to be exported setting and modify the Key Usage extension.
- B . Disable the Allow private key to be exported setting and modify the Application Policies extension.
- C . Disable the Allow private key to be exported setting and disable the Basic Constraints extension.
- D . Enable the Allow private key to be exported setting and enable the Basic Constraints extension
Latest 70-744 Dumps Valid Version with 207 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund