Microsoft 70-744 Securing Windows Server 2016 Online Training
Microsoft 70-744 Online Training
The questions for 70-744 were last updated at Feb 15,2026.
- Exam Code: 70-744
- Exam Name: Securing Windows Server 2016
- Certification Provider: Microsoft
- Latest update: Feb 15,2026
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains multiple Hyper-V hosts.
You need to deploy several critical line-of-business applications to the network to meet the following requirements:
– The resources of the applications must be isolated from the physical host.
– Each application must be prevented from accessing the resources of the other applications.
– The configurations of the applications must be accessible only from the operating system that hosts the application.
Solution: You deploy a separate Hyper-V container for each application.
Does this meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this sections, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com. The domain contains multiple Hyper-V hosts.
You need to deploy several critical line-of-business applications to the network to meet the following requirements:
– The resources of the applications must be isolated from the physical host.
– Each application must be prevented from accessing the resources of the other applications.
– The configurations of the applications must be accessible only from the operating system that hosts the application.
Solution: You deploy one Windows container to host all of the applications.
Does this meet the goal?
- A . Yes
- B . No
Your network contains an Active Directory domain named contoso.com. The domain contains 1,000 client computers that run Windows 10.
A security audit reveals that the network recently experienced a Pass-the-Hash attack. The attack was initiated from a client computer and accessed Active Directory objects restricted to the members of the Domain Admins group.
You need to minimize the impact of another successful Pass-the-Hash attack on the domain.
What should you recommend?
- A . Instruct all users to sign in to a client computer by using a Microsoft account.
- B . Move the computer accounts of all the client computers to a new organizational unit (OU). Remove the permissions to the new OU from the Domain Admins group.
- C . Instruct all administrators to use a local Administrators account when they sign in to a client computer.
- D . Move the computer accounts of the domain controllers to a new organizational unit (OU). Remove the permissions to the new OU from the Domain Admins group.
Your network contains an Active Directory forest named contoso.com. The forest functional level is Windows Server 2012. All servers run Windows Server 2016.
You create a new bastion forest named admin.contoso.com. The forest functional level of admin.contoso.com is Windows Server 2012 R2.
You need to implement a Privileged Access Management (PAM) solution.
Which two actions should you perform? Each correct answer presents part of the solution.
- A . Raise the forest functional level of admin.contoso.com.
- B . Deploy Microsoft Identify Management (MIM) 2016 to admin.contoso.com.
- C . Configure contoso.com to trust admin.contoso.com.
- D . Deploy Microsoft Identity Management (MIM) 2016 to contoso.com.
- E . Raise the forest functional level of contoso.com.
- F . Configure admin.contoso.com to trust contoso.com.
Your network contains an Active Directory domain named contoso.com. The domain contains two servers named Server1 and Server2 that run Windows Server 2016.
Server1 is configured as a domain controller. You configure Server1 as a Just Enough Administration (JEA) endpoint. You configure the required JEA rights for a user named User1.
You need to tell User1 how to manage Active Directory objects from Server2.
What should you tell User1 to do first on Server2?
- A . From a command prompt, runntdsutil.exe.
- B . From Windows PowerShell, run the Import-Module cmdlet.
- C . From Windows PowerShell, run the Enter-PSSession cmdlet.
- D . Install the management consoles for Active Directory, and then launch Active Directory Users and Computers.
Your network contains an Active Directory domain named contoso.com. The domain contains 100 servers. You deploy the Local Administrator Password Solution (LAPS) to the network. You deploy a new server named FinanceServer5, and join FinanceServer5 to the domain. You need to ensure that the passwords of the local administrators of FinanceServer5 are available to the LAPS administrators.
What should you do?
- A . On FinanceServer5, register AdmPwd.dll.
- B . On FinanceServer5, install the LAPS Windows PowerShell module.
- C . In the domain, modify the permissions for the computer account of FinanceServer5.
- D . In the domain, modify the permissions of the Domain Controllers organizational unit (OU).
Your network contains an Active Directory domain named contoso.com. The domain contains four servers.
The servers are configured as shown in the following table.
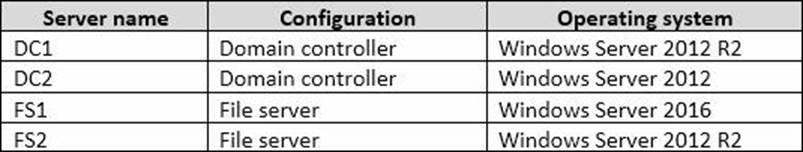
You need to manage FS1 and FS2 by using Just Enough Administration (JEA).
What should you do before you can implement JEA?
- A . Install Microsoft.NET Framework 4.6.2 on FS2.
- B . Install Microsoft.NET Framework 4.6.2 on FS1.
- C . Install Windows Management Framework 5.0 on FS2.
- D . Upgrade DC1 to Windows Server 2016.
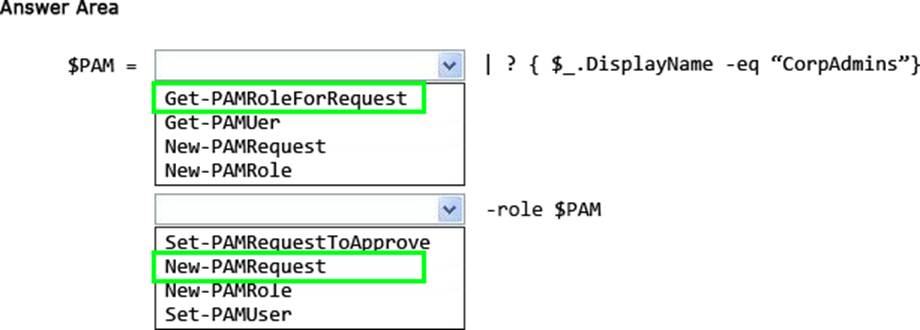
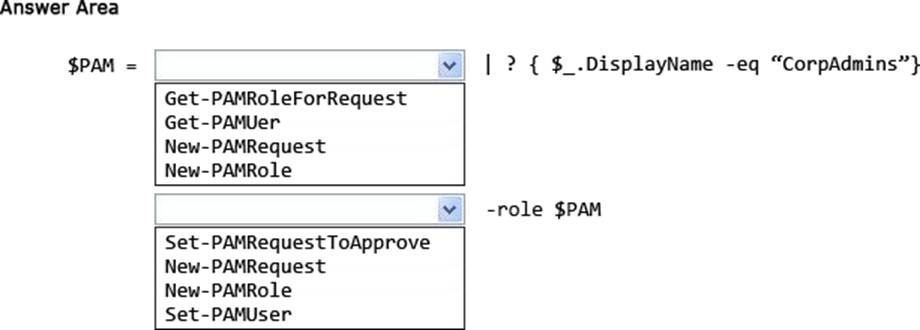
HOTSPOT
Your network contains an Active Directory forest named contoso.com. The forest has Microsoft Identity Manager (MIM) 2016 deployed. You implement Privileged Access Management (PAM). You need to request privileged access from a client computer in contoso.com by using PAM.
How should you complete the Windows PowerShell script? To answer, select the appropriate options in the answer area.
Your network contains an Active Directory domain named contoso.com. The domain contains five servers. All servers run Windows Server 2016.
A new security policy states that you must modify the infrastructure to meet the following requirements:
* Limit the nghts of administrators.
* Minimize the attack surface of the forest
* Support Multi-Factor authentication for administrators.
You need to recommend a solution that meets the new security policy requirements.
What should you recommend deploying?
- A . an administrative forest
- B . domain isolation
- C . an administrative domain in contoso.com
- D . the Local Administrator Password Solution (LAPS)
Your network contains two single-domain Active Directory forests named contoso.com and contosoadmin.com. Contosoadmin.com contains all of the user accounts used to manage the servers in contoso.com.
You need to recommend a workstation solution that provides the highest level of protection from vulnerabilities and attacks.
What should you include in the recommendation?
- A . Provide a Privileged Access Workstation (PAW) for each user account in both forests. Join each PAW to the contoso.com domain.
- B . Provide a Privileged Access Workstation (PAW) for each user in the contoso.com forest. Join each PAW to the contoso.com domain.
- C . Provide a Privileged Access Workstation (PAW) for each administrator. Join each PAW to the contoso.com domain.
- D . Provide a Privileged Access Workstation (PAW) for each administrator. Join each PAW to the contosoadmin.com domain.
Latest 70-744 Dumps Valid Version with 207 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund