Microsoft 70-462 Administering Microsoft SQL Server 2012 Databases Online Training
Microsoft 70-462 Online Training
The questions for 70-462 were last updated at Feb 12,2026.
- Exam Code: 70-462
- Exam Name: Administering Microsoft SQL Server 2012 Databases
- Certification Provider: Microsoft
- Latest update: Feb 12,2026
Note: This question is part of a series of questions that use the same set of answer choices. An answer choice may be correct for more than one question in the series.
You administer a SQL 2012 server that contains a database named SalesDB. SalesDb contains a schema named Customers that has a table named Regions. A user named UserA is a member of a role named Sales.
UserA is granted the Select permission on the Regions table. The Sales role is granted the Select permission on the Customers schema.
You need to remove the Select permission for UserA on the Regions table. You also need to ensure that UserA can still access all the tables in the Customers schema, including the Regions table, through the Sales role permissions.
Which Transact-SQL statement should you use?
- A . DENY SELECT ON Object::Regions FROM UserA
- B . DENY SELECT ON Schema::Customers FROM UserA
- C . EXEC sp_addrolemember ‘Sales’, ‘UserA’
- D . REVOKE SELECT ON Object::Regions FROM UserA
- E . REVOKE SELECT ON Object::Regions FROM Sales
- F . EXEC sp_droprolemember ‘Sales’, ‘UserA’
- G . REVOKE SELECT ON Schema::Customers FROM UserA
- H . DENY SELECT ON Object::Regions FROM Sales
- I . DENY SELECT ON Schema::Customers FROM Sales
- J . REVOKE SELECT ON Schema::Customers FROM Sales
You administer a single server that contains a Microsoft SQL Server 2012 default instance on which several production databases have been deployed.
You plan to install a new ticketing application that requires the deployment of a database on the server. The SQL login for this application requires sysadmin permissions.
You need to ensure that the login for the ticketing application cannot access other production databases.
What should you do?
- A . Use the SQL Server default instance and enable Contained Databases.
- B . Use the SQL Server default instance and configure a user-defined server role. Add the login for the ticketing application to this role.
- C . Install a new named SQL Server instance on the server.
- D . Install a new default SQL Server instance on the server.
You administer a Microsoft SQL Server failover cluster that contains two nodes named Node A and Node B. A single instance of SQL Server is installed on the cluster.
An additional node named Node C has been added to the existing cluster.
You need to ensure that the SQL Server instance can use all nodes of the cluster.
What should you do?
- A . Create a ConfigurationFile.ini file from Node B, and then run the AddNode command-line tool on Node A.
- B . Use Node A to install SQL Server on Node C.
- C . Run the Add Node to SQL Server Failover Cluster Wizard on Node C.
- D . Use Cluster Administrator to add a new Resource Group to Node B.
You administer a Microsoft SQL Server 2012 database.
The database contains a customer table created by using the following definition:
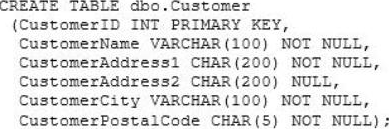
You need to ensure that the minimum amount of disk space is used to store the data in the customer table.
What should you do?
- A . Implement row-level compression.
- B . Implement page-level compression.
- C . Convert all indexes to Column Store indexes.
- D . Implement Unicode compression.
You are creating an application that will connect to the AgentPortal database by using a SQL login named AgentPortalUser. Stored procedures in the database will use sp_send_dbmail to send email messages.
You create a user account in the msdb database for the AgentPortalUser login. You use the Database Mail Configuration Wizard to create a Database Mail profile. Security has not been configured for the Database Mail profile.
You need to ensure that AgentPortalUser can send email messages.
What should you do?
- A . In the Database Mail Configuration Wizard, configure the Database Mail profile as a private profile for the AgentPortalUser account.
- B . Disable the guest user in the msdb database.
- C . Use the sysmail_help_profileaccount_sp stored procedure to add accounts to the Database Mail profile.
- D . In the Database Mail Configuration Wizard, create an email account for each recipient’s email address in the Database Mail profile.
DRAG DROP
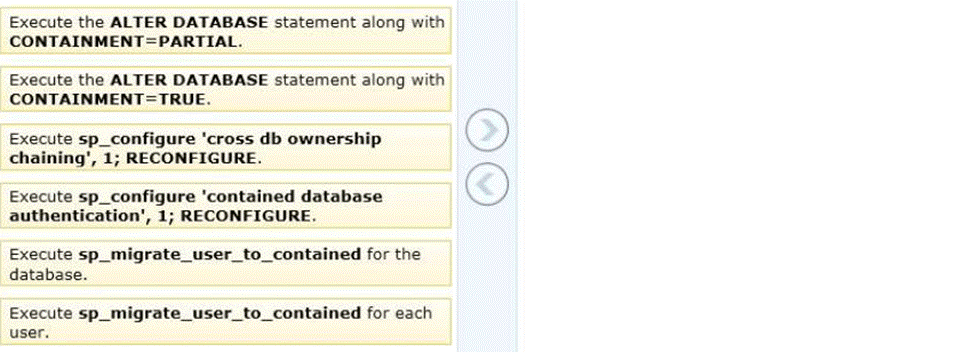
You administer a Microsoft SQL Server database.
You need to convert the database to a contained database. You also need to ensure that all users are converted to contained users.
Which three actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
You administer a Microsoft SQL Server 2012 default instance.
The instance is hosted by a server that has a local firewall configured. The firewall only allows inbound connections on port 1433. The server only hosts a single instance of SQL Server. You need to ensure that the instance is configured to allow remote connections even if the SQL
Server is unresponsive to client connections.
Which three actions should you perform? Each correct answer presents part of the solution.
- A . Enable inbound connections on TCP port 1434 in the Windows Firewall on the server.
- B . Execute the following Transact-SQL command:sp_configure ‘remote admin connections’,1
- C . Execute the Reconfigure command.
- D . Execute the following Transact-SQL command:sp_configure ‘remote access’, 1
- E . Restart the SQL Server Agent Service.
- F . Enable inbound connections on TCP port 135 in the Windows Firewall on the server.
DRAG DROP
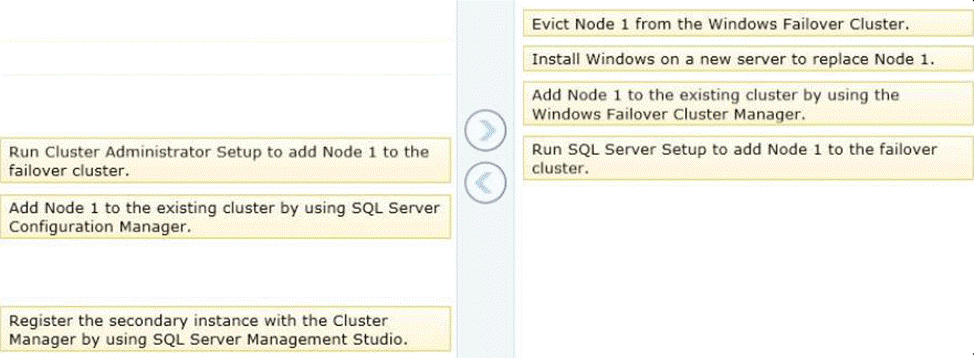
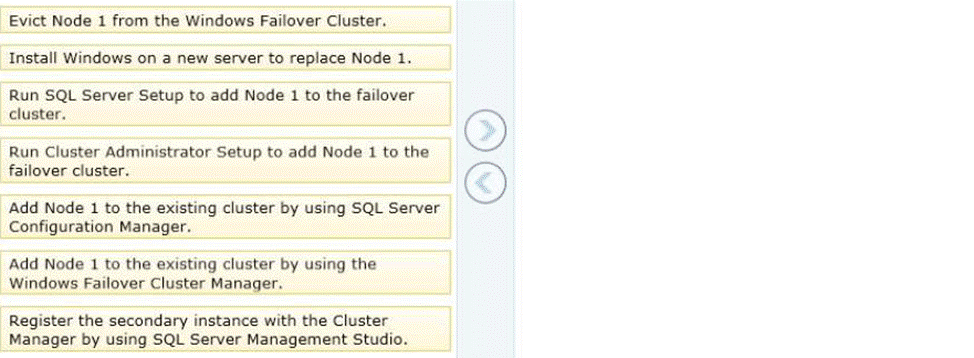
You administer a Microsoft SQL Server 2012 clustered instance that has two nodes named Node 1 and Node 2.
Node 1 fails and the cluster fails over to Node 2.
You need to replace Node 1 and add it to the cluster.
Which four actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
You use Microsoft SQL Server 2012 to write code for a transaction that contains several statements. There is high contention between readers and writers on several tables used by your transaction. You need to minimize the use of the tempdb space.
You also need to prevent reading queries from blocking writing queries.
Which isolation level should you use?
- A . SERIALIZABLE
- B . SNAPSHOT
- C . READ COMMITTED SNAPSHOT
- D . REPEATABLE READ
You administer a Microsoft SQL Server 2012 instance that contains a financial database hosted on a storage area network (SAN).
The financial database has the following characteristics:
– A data file of 2 terabytes is located on a dedicated LUN (drive D).
– A transaction log of 10 GB is located on a dedicated LUN (drive E).
– Drive D has 1 terabyte of free disk space.
– Drive E has 5 GB of free disk space.
The database is continually modified by users during business hours from Monday through Friday between 09:00 hours and 17:00 hours.
Five percent of the existing data is modified each day.
The Finance department loads large CSV files into a number of tables each business day at 11:15 hours and 15:15 hours by using the BCP or BULK INSERT commands.
Each data load adds 3 GB of data to the database.
These data load operations must occur in the minimum amount of time.
A full database backup is performed every Sunday at 10:00 hours.
Backup operations will be performed every two hours (11:00, 13:00, 15:00, and 17:00) during business hours.
You implement log shipping of the financial database to another SQL Server 2012 instance. You decide to failover to this secondary database.
You need to ensure that all transactions will be replicated to the secondary database.
Which backup option should you use?
- A . Differential
- B . Transaction Log
- C . FULL
- D . SIMPLE
- E . SKIP
- F . RESTART
- G . STANDBY
- H . CHECKSUM
- I . DBO_ONLY
- J . COPY_ONLY
- K . NORECOVERY
- L . NO_CHECKSUM
- M . CONTINUE_AFTER_ERROR
- N . BULK_LOGGED
Latest 70-462 Dumps Valid Version with 301 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund