Microsoft 70-412 Configuring Advanced Windows Server 2012 Services Online Training
Microsoft 70-412 Online Training
The questions for 70-412 were last updated at Feb 21,2026.
- Exam Code: 70-412
- Exam Name: Configuring Advanced Windows Server 2012 Services
- Certification Provider: Microsoft
- Latest update: Feb 21,2026
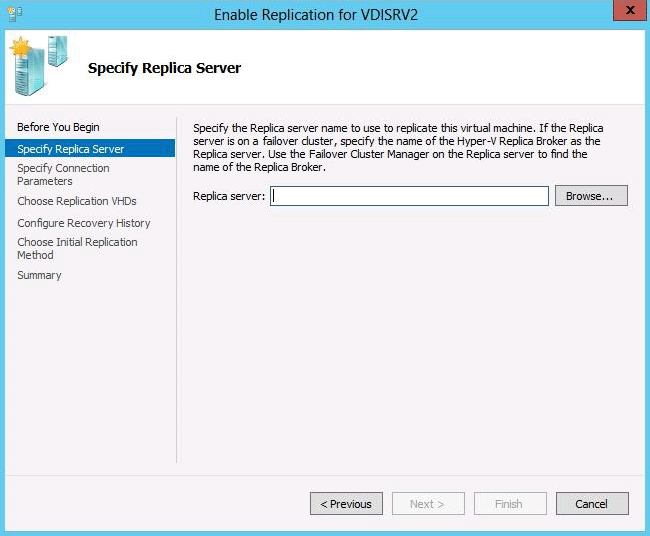
You have a virtual machine named VM1 that runs on a host named Host1. You configure VM1 to replicate to another host named Host2. Host2 is located in the same physical location as Host1.
You need to add an additional replica of VM1. The replica will be located in a different physical site.
What should you do?
- A . From VM1 on Host2, click Extend Replication.
- B . On Host1, configure the Hyper-V settings.
- C . From VM1 on Host1, click Extend Replication.
- D . On Host2, configure the Hyper-V settings.
Your network contains two servers named Server1 and Server2 that run Windows Server 2012 R2.
Both servers have the Hyper-V server role installed. Server1 and Server2 are located in different offices. The offices connect to each other by using a high-latency WAN link.
Server1 hosts a virtual machine named VM1.
You need to ensure that you can start VM1 on Server2 if Server1 fails. The solution must minimize hardware costs.
What should you do?
- A . On Server1, install the Multipath I/O (MPIO) feature. Modify the storage location of the VHDs for VM1.
- B . From the Hyper-V Settings of Server2, modify the Replication Configuration settings. Enable replication for VM1.
- C . On Server2, install the Multipath I/O (MPIO) feature. Modify the storage location of the VHDs for VM1.
- D . From the Hyper-V Settings of Server1, modify the Replication Configuration settings. Enable replication for VM1.
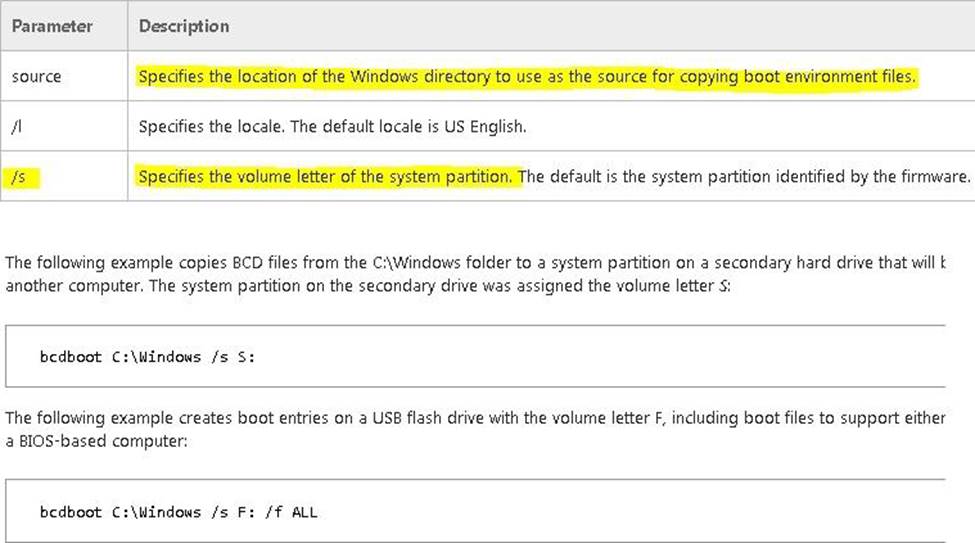
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 contains a virtual machine named VM1 that runs Windows Server 2012 R2. You fail to start VM1 and you suspect that the boot files on VM1 are corrupt. On Server1, you attach the virtual hard disk (VHD) of VM1 and you assign the VHD a drive letter of F. You need to repair the corrupt boot files on VM1.
What should you run?
- A . bootrec.exe /rebuildbcd
- B . bootrec.exe /scanos
- C . bcdboot.exe f:windows /s c:
- D . bcdboot.exe c:windows /s f:
DRAG DROP
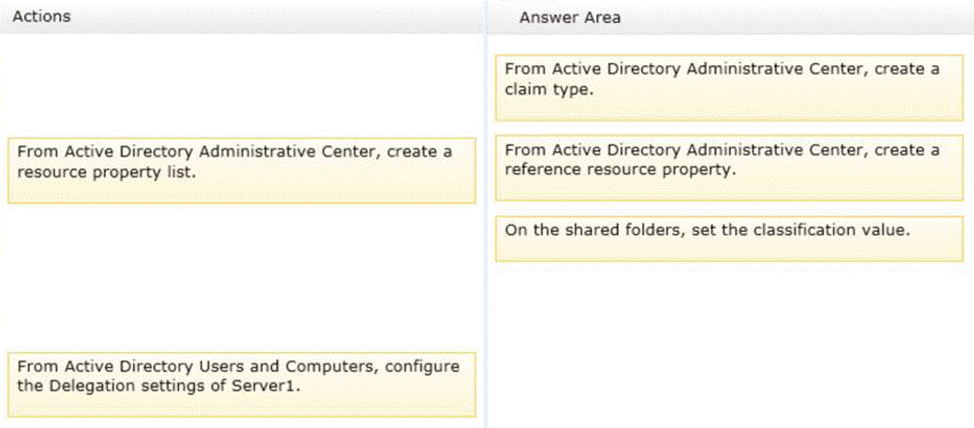
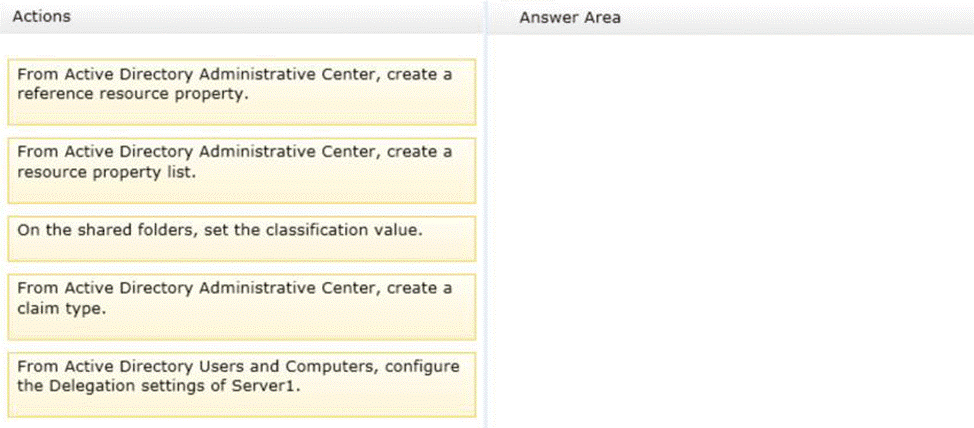
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. All servers run Windows Server 2012 R2.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain.
You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property.
Which three actions should you perform in sequence?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. All servers run Windows Server 2012 R2.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain.
You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property.
Which three actions should you perform in sequence?

DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. All servers run Windows Server 2012 R2.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain.
You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property.
Which three actions should you perform in sequence?

DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains a file server named Server1. All servers run Windows Server 2012 R2.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain.
You need to control access to the file shares on Server1 based on the values in the Division attribute and the Division resource property.
Which three actions should you perform in sequence?

You have a server named LON-DC1 that runs Windows Server 2012 R2.
An iSCSI virtual disk named VirtualiSCSI1.vhd exists on LON-DC1 as shown in the exhibit. (Click the Exhibit button.)
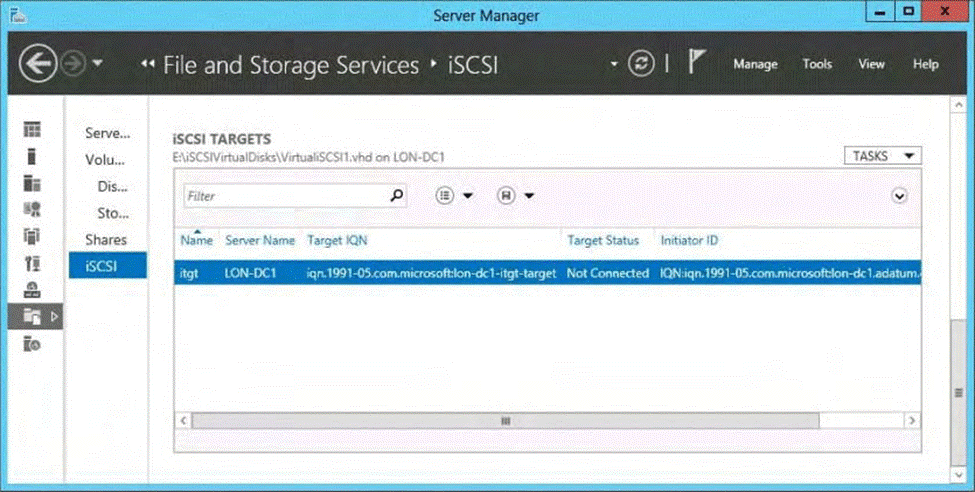
You create a new iSCSI virtual disk named VirtualiSCSI2.vhd by using the existing itgt iSCSI target. VirtualiSCSIl.vhd is removed from LON-DC1. You need to assign VirtualiSCSI2.vhd a logical unit value of 0.
What should you do?
- A . Modify the properties of the itgt ISCSI target.
- B . Modify the properties of the VirtualiSCSI2.vhd iSCSI virtual disk.
- C . Run the Set-VirtualDisk cmdlet and specify the -UniqueId parameter.
- D . Run the iscsicli command and specify the reportluns parameter.
- E . Run the iscsicli command and specify the virtualdisklun parameter.
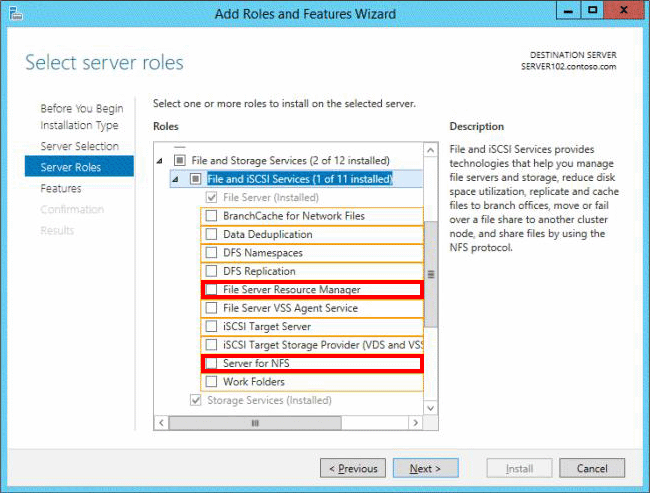
HOTSPOT
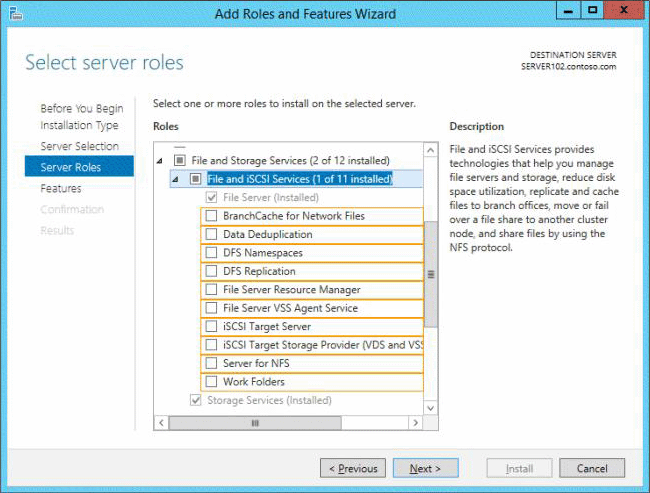
You have a file server named Server1 that runs Windows Server 2012 R2. You need to ensure that you can use the NFS Share – Advanced option from the New Share Wizard in Server Manager.
Which two role services should you install? To answer, select the appropriate two role services in the answer area.
DRAG DROP
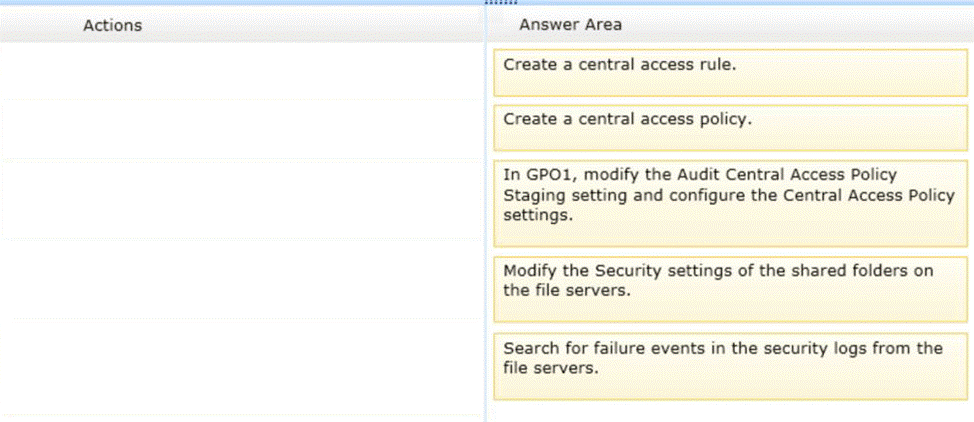
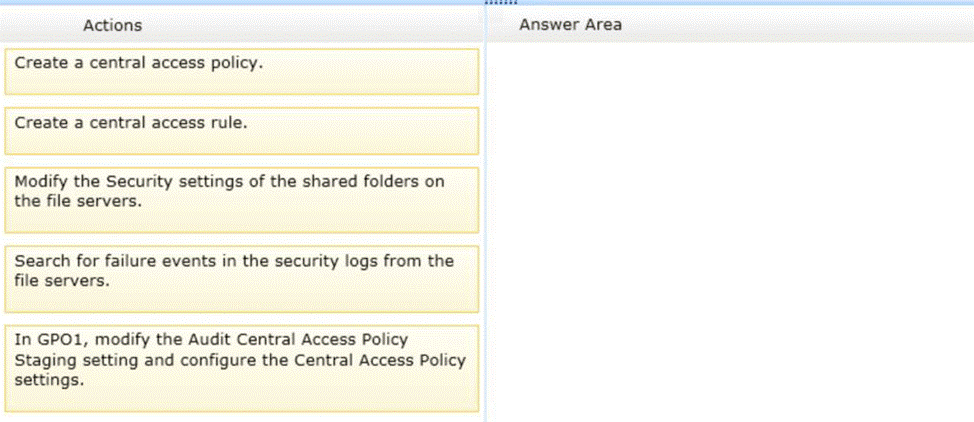
Your network contains an Active Directory domain named contoso.com. All file servers in the domain run Windows Server 2012 R2. The computer accounts of the file servers are in an organizational unit (OU) named OU1. A Group Policy object (GPO) named GPO1 is linked to OU1. You plan to modify the NTFS permissions for many folders on the file servers by using central access policies. You need to identify any users who will be denied access to resources that they can currently access once the new permissions are implemented.
In which order should you Perform the five actions?
Latest 70-412 Dumps Valid Version with 448 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund