Microsoft 70-345 Designing and Deploying Microsoft Exchange Server 2016 Online Training
Microsoft 70-345 Online Training
The questions for 70-345 were last updated at Feb 25,2026.
- Exam Code: 70-345
- Exam Name: Designing and Deploying Microsoft Exchange Server 2016
- Certification Provider: Microsoft
- Latest update: Feb 25,2026
You need to recommend a solution that meets the security requirements for the mailbox databases.
What should you include in the recommendation?
- A . Resilient File System (ReFS)
- B . Transparent Data Encryption (TDE)
- C . BitLocker Drive Encryption (BitLocker)
- D . Encrypting Files System (EFS)
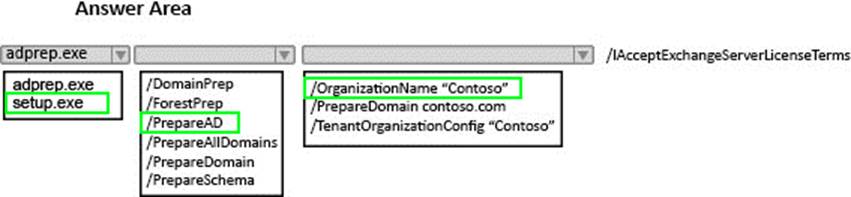
HOTSPOT
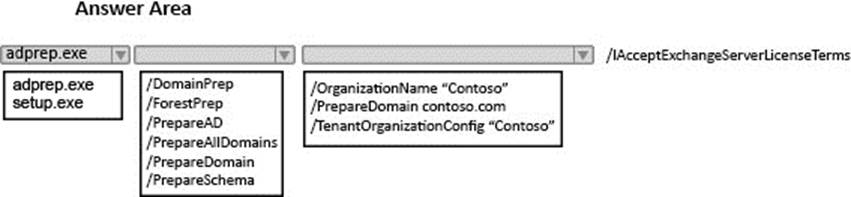
You need to instruct the Active Directory administrators how to prepare the Active Directory environment to support the planned Exchange Server 2016 deployment.
What command should you instruct administrators to run? To answer, select the appropriate options in the answer area.
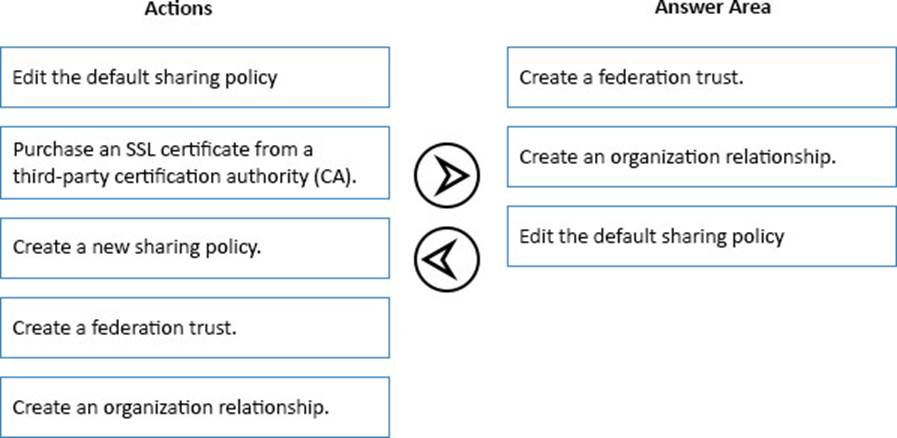
DRAG DROP
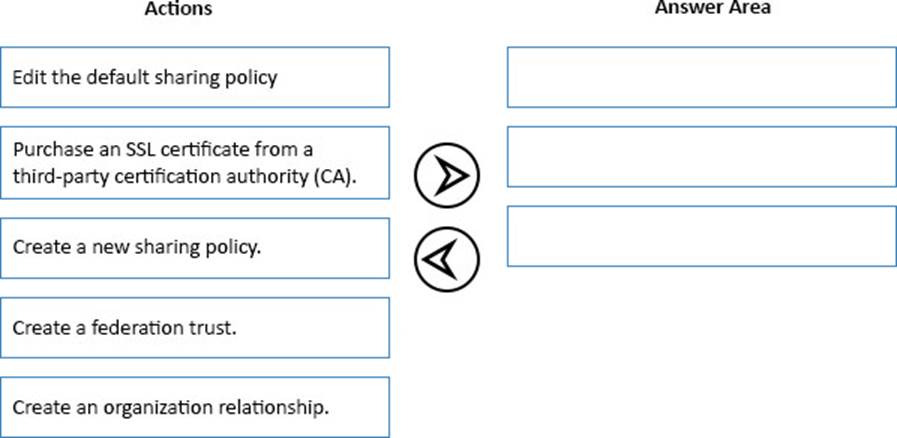
You need to configure the Exchange Server organization to support the security requirements for Calendar sharing.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You need to recommend a solution that meets the security requirements for the tablets.
Which two objects should you include in the recommendation? Each correct answer presents part of the solution.
- A . a mobile device mailbox policy
- B . an Outlook Web App policy
- C . a data loss prevention (DLP) policy
- D . a device access rule
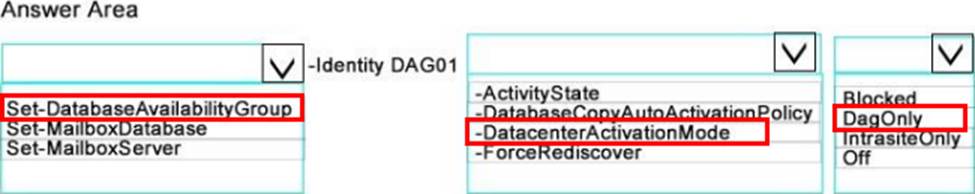
HOTSPOT.
Hotspot Question
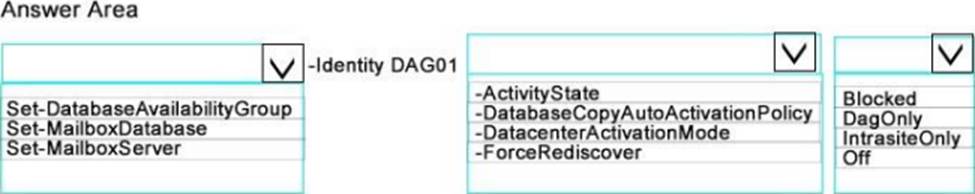
You need to configure DAG01 to meet the availability requirements.
What command should you run? To answer, select the appropriate options in the answer area.
You plan to configure the Exchange organization for site failovers.
You need to recommend how many certificates must be deployed to meet the availability requirements and the security requirements.
What is the minimum number of certificates you should recommend deploying?
- A . One
- B . Two
- C . Three
- D . Four
Case Study: 4, Litware
Case study
Exchange Server
Litware has an Exchange Server 2016 organization that uses the namespaces of mail.litware.com and autodiscover.litware.com.
The organization contains the servers configured as shown in the following table.
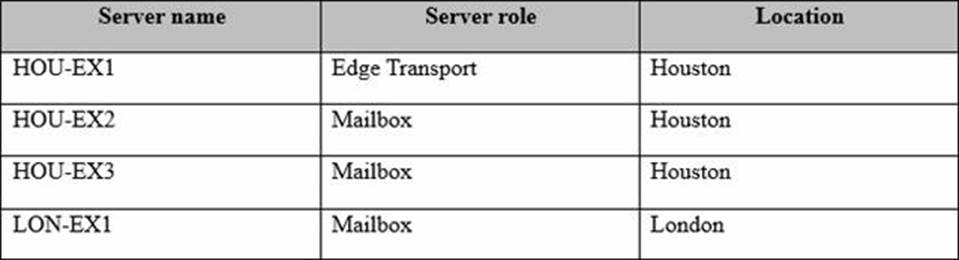
All Internet email is routed through HOU-EX1.
Requirements
Business Goals
Litware has security concerns about the data and messaging content of the research and development department. Preventing information leaks is a priority. All users must be able to access their corporate email from any device.
Litware plans to minimize the costs associated with changing the Exchange Server environment.
Planned Changes
Litware plans to implement a site resilience solution ensuring that outbound email messages can be delivered if one of the sites fail. The site resilience solution must allow all users to access their mailbox if a server fails in each site. Availability Requirements
Litware identifies the following availability requirements:
Load balancing must support the following functionalities:
• Load balancing must support the following functionalities:
• Provide SSL termination
• Remove failed Mailbox servers from the server pool.
• Data collected by Managed Availability from Outlook on the web must be used.
• Target server health must be configured as per-protocol so that only the affected client protocol is directed to another server if a server fails.
• The site resilience solution must follow the bound namespace model.
Security Requirements
Litware identifies the following security requirements:
• Users in the research and development department must be able to encrypt documents sent to external users. The encrypted email messages must never be forwarded by the external recipients.
• Only specific research and development department users must be able to access confidential internal email regarding the high-security government contracts.
• All certificates deployed to the Exchange organization must be issued by a trusted third-party certification authority (CA).
• The principle of least privilege must be applied to all users and permissions.
Compliance Requirements
Litware identifies the following compliance requirements:
• Any new mailbox created for the auditing department must have a retention policy named Audit immediately applied manually after the mailbox is created.
• Each week, a team of regulation auditors must review the email messages sent and received by all the research and development department users.
• The regulation auditors must be able to review the email messages of mailboxes placed on Litigation Hold.
• The regulation auditors must be able to gain quick access to the email messages.
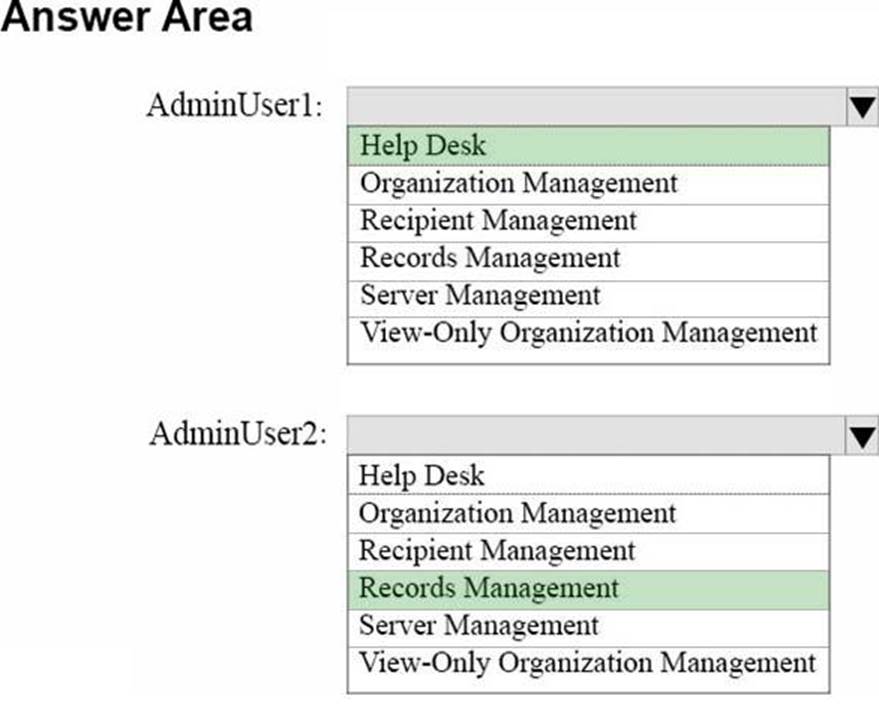
HOTSPOT
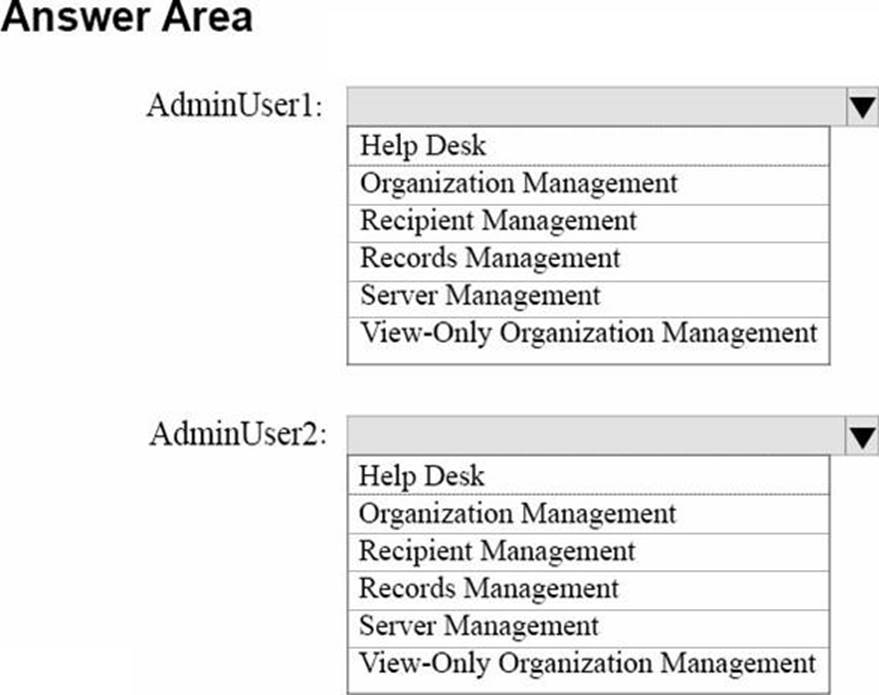
You need to assign user roles to two administrative users to meet the following requirements:
• A user named AdminUser1 must be able to reset user account passwords.
• A user named AdminUser2 must be able to create retention policies and message classifications.
The solution must meet the security requirements.
To which role should you assign each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You plan to create a new mailbox for the auditing department.
You need to recommend which task must be performed immediately after the mailbox is created. The solution must meet the compliance requirements.
What should you recommend?
- A . Enable an archive for the new mailbox.
- B . Place the new mailbox on Litigation Hold.
- C . Run the Set-Mailbox cmdlet.
- D . Run the Start-ManagedFolderAssistant cmdlet.
You implement the load balancing solution.
You need to configure the health probes to meet the availability requirements.
Which URL should you configure for the probe?
- A . https://mail.litware.com/owa/probe.htm
- B . https://mail.litware.com/owa/healthcheck.htm
- C . http://litware.com/owa/healthcheck.htm
- D . http://litware/owa/probe.htm
You need to recommend a solution that meets the security requirements for outbound email delivery.
What should you recommend?
- A . Microsoft Azure Information Protection
- B . data loss prevention (DLP) policies
- C . Outlook protection rules
- D . Active Directory Rights Management Services (AD RMS)
Latest 70-345 Dumps Valid Version with 162 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund