Match the Cyber-Attack Lifecycle stage to its correct description
DRAG DROP
Match the Cyber-Attack Lifecycle stage to its correct description.
Answer: 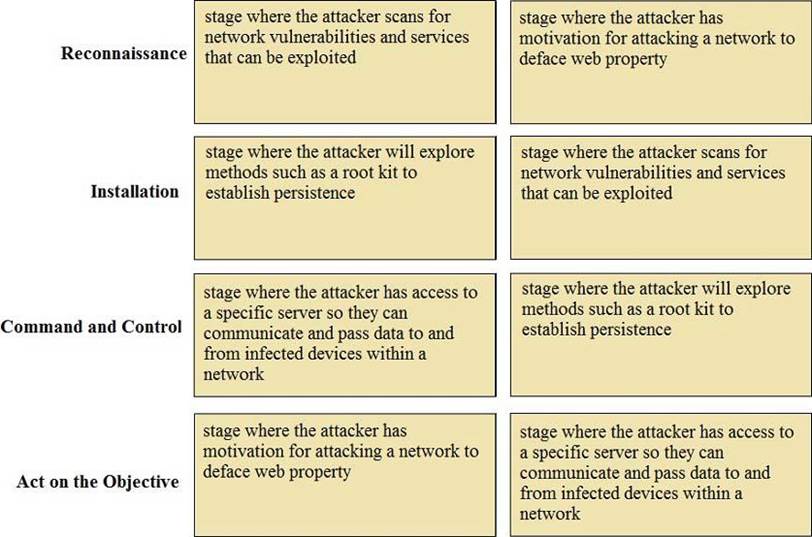
Explanation:
Reconnaissance C stage where the attacker scans for network vulnerabilities and services that can be exploited.
Installation C stage where the attacker will explore methods such as a root kit to establish persistence
Command and Control C stage where the attacker has access to a specific server so they can communicate and pass data to and from infected devices within a network.
Act on the Objective C stage where an attacker has motivation for attacking a network to deface web property
Latest PCNSA Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

