Match the Cyber-Attack Lifecycle stage to its correct description
DRAG DROP
Match the Cyber-Attack Lifecycle stage to its correct description.
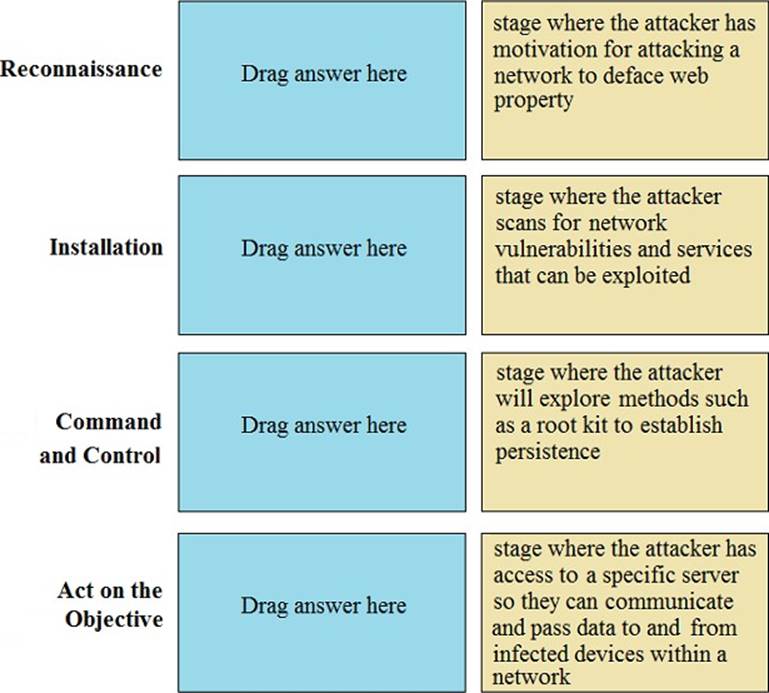
Answer: 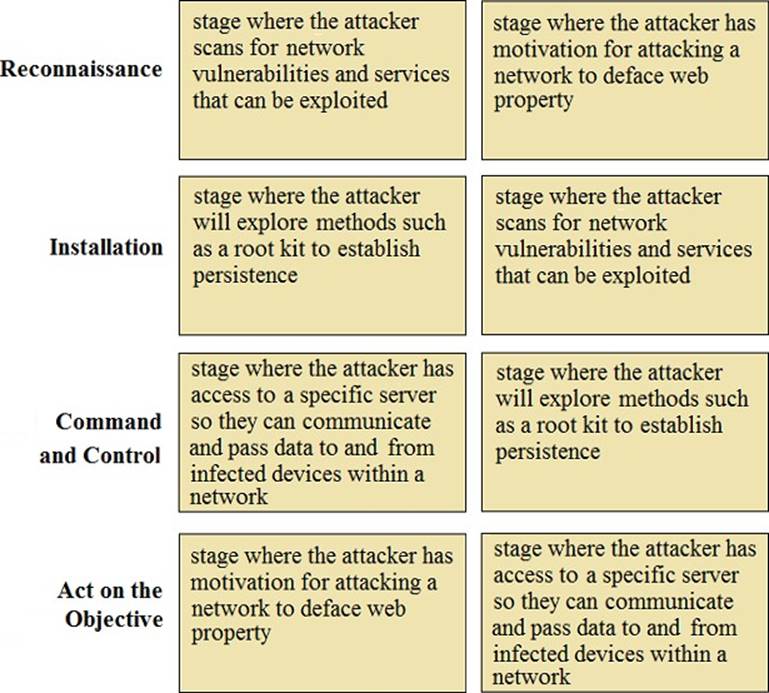
Latest PCNSA Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

