Referring to the exhibit, which two statements are correct? (Choose two.)
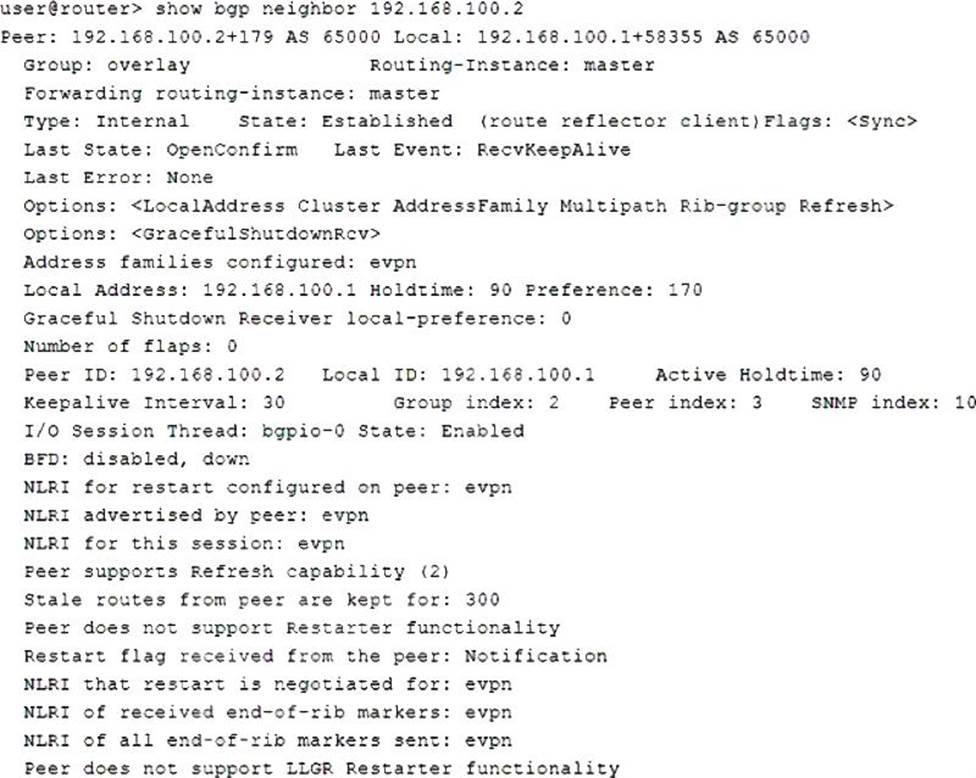
- A . The BGP neighbor can advertise L3 VPN related routes.
- B . The BGP neighbor cannot advertise EVPN related routes.
- C . The BGP neighbor can advertise EVPN related routes.
- D . The BGP neighbor cannot advertise L3 VPN related routes.
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . The maximum wattage that this switch can allocate to attached Ethernet devices is 100 watts.
- B . If the total power consumption exceeds 90 watts, the ge-0/0/11 interface will continue to receive power.
- C . PoE is not enabled on the ge-0/0/0 interface.
- D . The ge-0/0/10 interface supports PoE+.
Referring to the exhibit, how will router E quickly learn that the remote MAC addresses are no longer reachable through the router attached to the failed link?
- A . Router E receives Type 2 withdrawal messages from router D.
- B . Router E receives Type 1 withdrawal messages from router D.
- C . Router E receives Type 1 withdrawal messages from router C.
- D . Router E receives Type 2 withdrawal messages from router C.
You are deploying new Juniper EX Series switches in a network that currently is using Cisco’s Per-VLAN spanning tree plus (PVST+) and you must provide compatibility with this environment.
Which spanning tree protocol do you deploy in this scenario?
- A . STP
- B . MSTP
- C . VSTP
- D . RSTP
Referring to the exhibit, anycast RP is implemented to ensure multicast service availability.
The source is currently sending multicast traffic using group 239.1.1.1 and R3 is receiving PIM register messages, but R2 does not have active source information.
In this scenario, what are two methods to receive the active source information on R2? (Choose two.)
- A . Configure an RP set in PIM on R1, allowing R1 to forward PIM register messages to R2 and R3 in the set.
- B . Configure an MSDP protocol between R2 and R3.
- C . Configure an RP set in PIM on R2 and R3, allowing the RPs to forward PIM register messages to the other RPs in the set.
- D . Configure an MSDP protocol between R1 and R2.
You are troubleshooting an EVPN-VXLAN IP fabric and observe the loop shown in the exhibit.
Which two steps would you take to further troubleshoot this problem? (Choose two.)
- A . Verify that the same ESI is configured on the link from the host and that it matches the source.
- B . Issue the show route table bgp.evpn.0 command on Leaf2 and verify that Type 4 routes are present.
- C . Issue the show route table bgp.evpn.0 command on Leaf2 and verify that Type 3 routes are present.
- D . Verify that the same ESI is configured on the two links from the source.
A user is attempting to watch a high-definition video being streamed from the media server over the network. However, the user complains that the experienced video quality is poor. While logged on to router B, a Juniper Networks device, you notice that video packets are being dropped.
In this scenario, what would solve this problem?
- A . Adjust the scheduler for the expedited-forwarding forwarding class to support a higher transmit rate.
- B . Adjust the expedited-forwarding BA classifier to router B’s ge-0/0/0 interface to support a higher transmit rate.
- C . Adjust the scheduler-map to support a higher transmit rate.
- D . Adjust the expedited-forwarding BA classifier on router B’s ge-0/0/1 interface to support a higher transmit rate.
Your enterprise network uses routing instances to support multitenancy. Your Junos devices use BGP to peer to multiple BGP devices. You must ensure that load balancing is achieved within the routing instance.
Which two statements would accomplish this task? (Choose two.)
- A . Configure the multipath option at the [edit protocols bgp group <group-name> neighbor] hierarchy.
- B . Configure the multipath option at the [edit protocols bgp group] hierarchy.
- C . Configure a load-balance per-packet policy and apply it at the [edit routing-options forwarding-table] hierarchy.
- D . Configure the multipath option at the [edit routing-instances <instance-name> routing-options] hierarchy.
You must ensure that all routes in the 10.0.0/8 address range are not advertised outside of your AS.
Which well-known BGP community should be assigned to these addresses to accomplish this task?
- A . no-export
- B . no-peer
- C . internet
- D . no-advertise
You are asked to establish interface level authentication for users connecting to your network. You must ensure that only corporate devices, identified by MAC addresses, are allowed to connect and authenticate. Authentication must be handled by a centralized server to increase scalability.
Which authentication method would satisfy this requirement?
- A . MAC RADIUS
- B . captive portal
- C . 802.1X with single-secure supplicant mode
- D . 802.1X with multiple supplicant mode
You are troubleshooting a BGP connection.
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . Packet fragmentation is preventing the session from establishing.
- B . The 192.168.1.5 peer has a misconfigured MD5 key.
- C . The ge-0/0/1 interface is disabled.
- D . The 192.168.1.4 peer has a misconfigured autonomous system number.
You are deploying IP phones in your enterprise network that must receive their power through their Ethernet connection. You are using your EX Series switch’s PoE ports that support IEEE 802.3af.
In this scenario, what is the maximum amount of power allocated to each interface?
- A . 10.2 W
- B . 15.4 W
- C . 30 W
- D . 50 W
Referring to the exhibit, which statement is correct when a failure exists on the link between host2 and switch5 on this EVPN-VXLAN fabric?
- A . The switch5 device will send a Type 2 route to all peers.
- B . The switch5 device will send a Type 4 route to all peers.
- C . The switch5 device will send a Type 1 route to all peers.
- D . The switch5 device will send a Type 3 route to all peers.
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . The host that the route is associated with is multihomed to two leaf nodes.
- B . The route is a Type 1 EVPN route.
- C . The route is a Type 2 EVPN route.
- D . The host that the route is associated with is single-homed to one leaf node.
Which three configuration parameters must match on all switches within the same MSTP region? (Choose three.)
- A . VLAN to instance mapping
- B . revision level
- C . configuration name
- D . bridge priority
- E . region name
You recently committed a change to a router to reject OSPF routes sourced from area 10.
However, you are still seeing area 10 routes in the routing table.
Referring to the exhibit, which statement is correct?
- A . The OSPF protocol is first matched by find-ospf and accepted.
- B . The routes only timeout after 24 hours.
- C . The routes remain in the table until the device is rebooted.
- D . The routes remain in the table until the routing daemon is restarted.
Referring to the exhibit, traffic ingresses on interface ge-0/0/3 and egresses on interface ge-0/0/4.
Which queue does traffic with the IP precedence value of 100 use?
- A . network-control
- B . assured-forwarding
- C . best-effort
- D . expedited-forwarding
You are running OSPF as your IGP. The interfaces connecting two routers are in the ExStart state. You notice that something is incorrect with the configuration.
Referring to the exhibit, which statement is correct?
- A . The subnet mask is incorrect.
- B . The MTU setting are incorrect.
- C . The interface type is incorrect.
- D . The IP addresses are incorrect.
The connection between DC1 and DC2 is routed as shown in the exhibit.
In this scenario, which statement is correct?
- A . The border devices must be able to perform Layer 3 routing and provide IRB functionality.
- B . L3VPN must be enabled to advertise reachability.
- C . An IP prefix route provides encoding for intra-subnet forwarding.
- D . Type 2 and Type 5 routes will be exchanged between DC1 and DC2.
You are asked to enforce user authentication using a captive portal before users access the corporate network.
Which statement is correct in this scenario?
- A . HTTPS is the default protocol for a captive portal.
- B . A captive portal can be bypassed using an allowlist command containing a device’s IP address.
- C . When enabled, a captive portal must be applied to each individual interface.
- D . All Web browser requests are redirected to the captive portal until authentication is successful.