Juniper JN0-637 Security, Professional (JNCIP-SEC) Online Training
Juniper JN0-637 Online Training
The questions for JN0-637 were last updated at Mar 02,2026.
- Exam Code: JN0-637
- Exam Name: Security, Professional (JNCIP-SEC)
- Certification Provider: Juniper
- Latest update: Mar 02,2026
Exhibit:
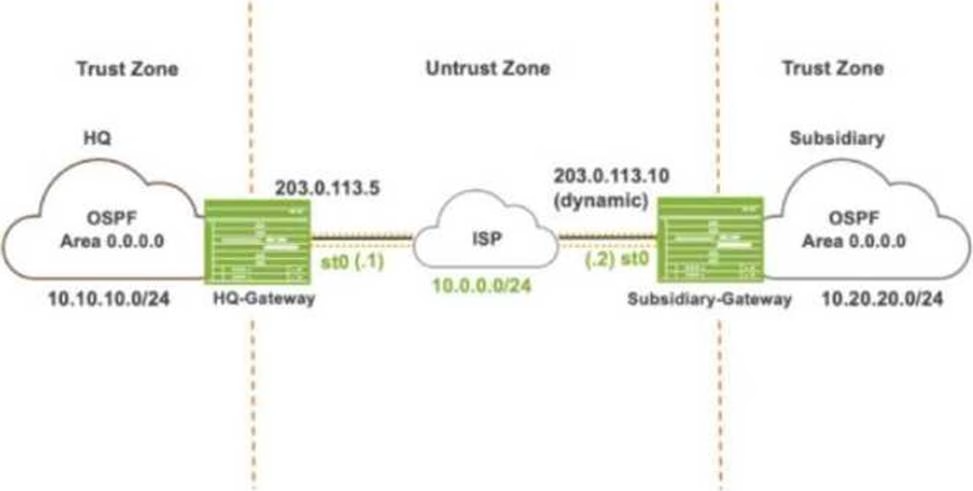
Referring to the exhibit, which IKE mode will be configured on the HQ-Gateway and Subsidiary-Gateway?
- A . Main mode on both the gateways
- B . Aggressive mode on both the gateways
- C . Main mode on the HQ-Gateway and aggressive mode on the Subsidiary-Gateway
- D . Aggressive mode on the HQ-Gateway and main mode on the Subsidiary-Gateway
You are deploying threat remediation to endpoints connected through third-party devices.
In this scenario, which three statements are correct? (Choose three.)
- A . All third-party switches must support AAA/RADIUS and Dynamic Authorization Extensions to the RADIUS protocol.
- B . The connector uses an API to gather endpoint MAC address information from the RADIUS server.
- C . All third-party switches in the specified network are automatically mapped and registered with the RADIUS server.
- D . The connector queries the RADIUS server for the infected host endpoint details and initiates a change of authorization (CoA) for the infected host.
- E . The RADIUS server sends Status-Server messages to update infected host information to the connector.
Exhibit:
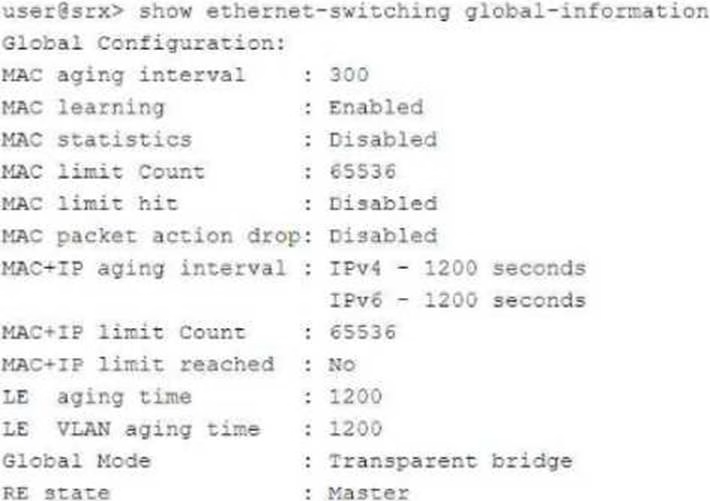
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . You cannot secure intra-VLAN traffic with a security policy on this device.
- B . You can secure inter-VLAN traffic with a security policy on this device.
- C . The device can pass Layer 2 and Layer 3 traffic at the same time.
- D . The device cannot pass Layer 2 and Layer 3 traffic at the same time.
You want to test how the device handles a theoretical session without generating traffic on the Junos security device.
Which command is used in this scenario?
- A . request security policies check
- B . show security flow session
- C . show security match-policies
- D . show security policies
Exhibit:
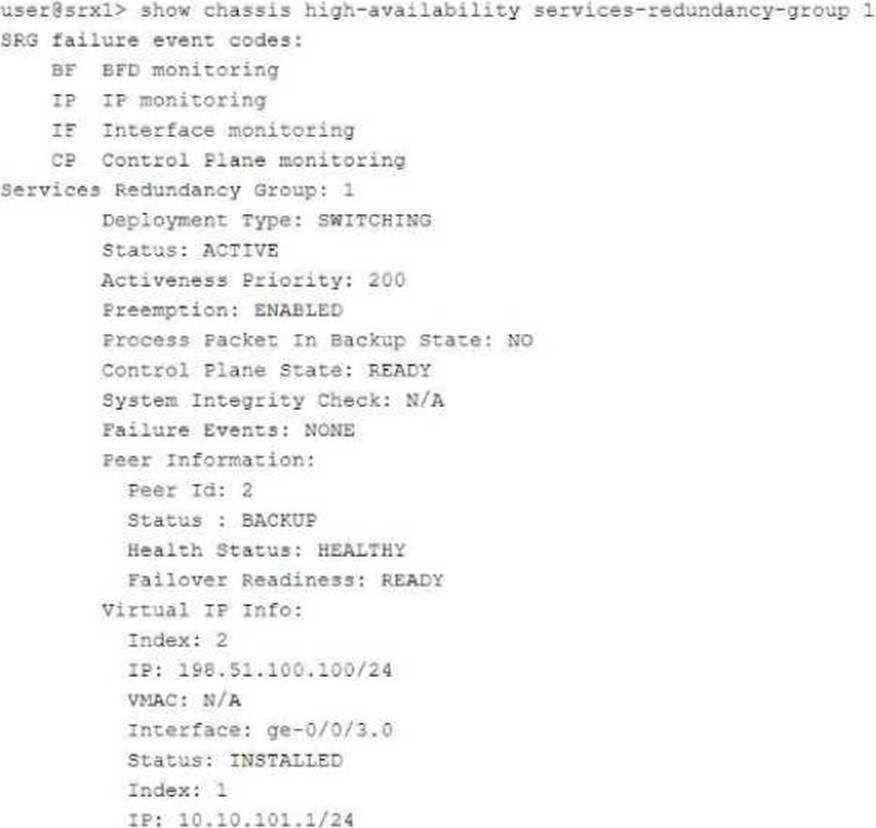
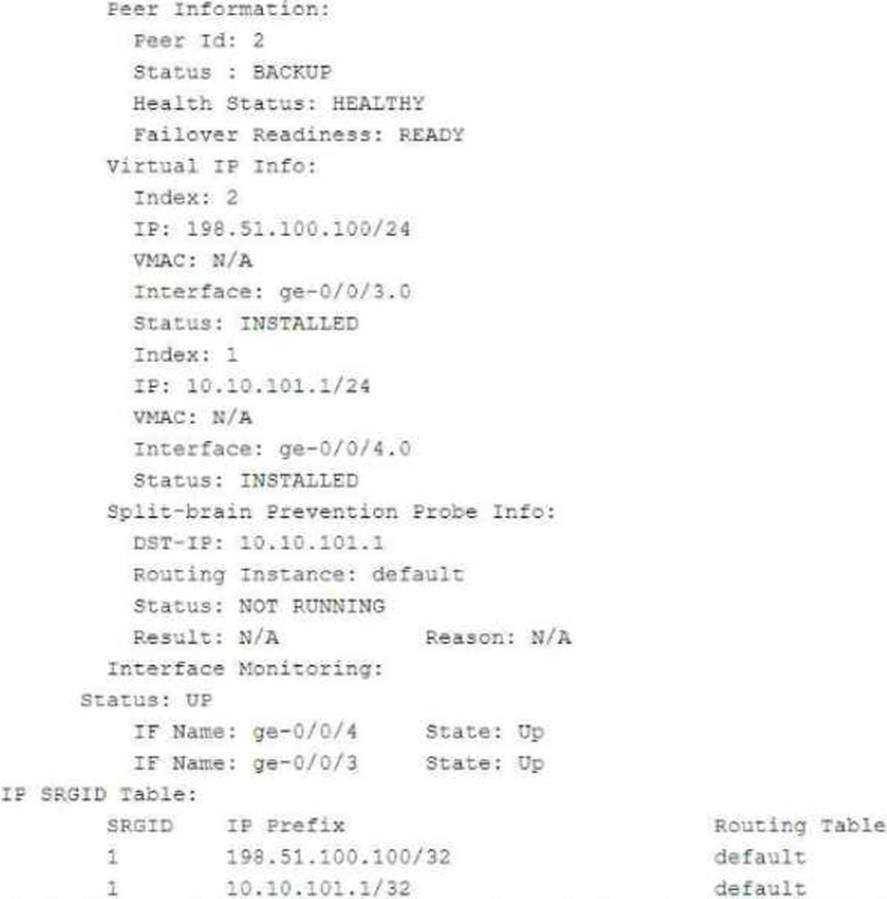
Referring to the exhibit, which two statements are correct? (Choose two.)
- A . The ge-0/0/3.0 and ge-0/0/4.0 interfaces are not active and will not respond to ARP requests to the virtual IP MAC address.
- B . This device is the backup node for SRG1.
- C . The ge-0/0/3.0 and ge-0/0/4.0 interfaces are active and will respond to ARP requests to the virtual IP MAC address.
- D . This device is the active node for SRG1.
Which role does an SRX Series device play in a DS-Lite deployment?
- A . Softwire concentrator
- B . STUN server
- C . STUN client
- D . Softwire initiator
Which two statements are correct about the ICL in an active/active mode multinode HA environment? (Choose two.)
- A . The ICL is strictly a Layer 2 interface.
- B . The ICL uses a separate routing instance to communicate with remote multinode HA peers.
- C . The ICL traffic can be encrypted.
- D . The ICL is the local device management interface in a multinode HA environment.
Exhibit:

Your company uses SRX Series devices to establish an IPsec VPN that connects Site-1 and the HQ networks. You want VoIP traffic to receive priority over data traffic when it is forwarded across the VPN.
Which three actions should you perform in this scenario? (Choose three.)
- A . Enable next-hop tunnel binding.
- B . Create a firewall filter that identifies VoIP traffic and associates it with the correct forwarding class.
- C . Configure CoS forwarding classes and scheduling parameters.
- D . Enable the copy-outer-dscp parameter so that DSCP header values are copied to the tunneled packets.
- E . Enable the multi-sa parameter to enable two separate IPsec SAs for the VoIP and data traffic.
Your IPsec tunnel is configured with multiple security associations (SAs). Your SRX Series device supports the CoS-based IPsec VPNs with multiple IPsec SAs feature. You are asked to configure CoS for this tunnel.
Which two statements are true in this scenario? (Choose two.)
- A . The local and remote gateways do not need the forwarding classes to be defined in the same order.
- B . A maximum of four forwarding classes can be configured for a VPN with the multi-sa forwarding-classes statement.
- C . The local and remote gateways must have the forwarding classes defined in the same order.
- D . A maximum of eight forwarding classes can be configured for a VPN with the multi-sa forwarding-classes statement.
The exhibit shows part of the flow session logs.
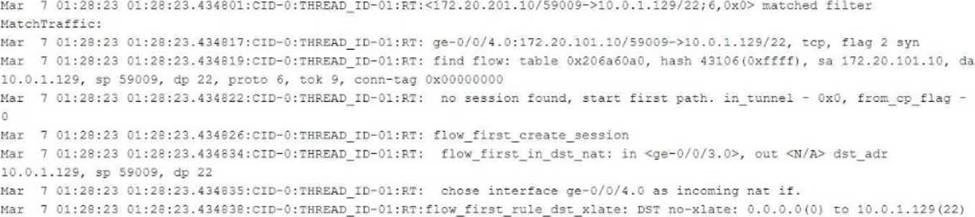
Which two statements are true in this scenario? (Choose two.)
- A . The existing session is found in the table, and the fast path process begins.
- B . This packet arrives on interface ge-0/0/4.0.
- C . Junos captures a TCP packet from source address 172.20.101.10 destined to 10.0.1.129.
- D . Destination NAT occurs.
Latest JN0-637 Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

