Juniper JN0-637 Security, Professional (JNCIP-SEC) Online Training
Juniper JN0-637 Online Training
The questions for JN0-637 were last updated at Feb 27,2026.
- Exam Code: JN0-637
- Exam Name: Security, Professional (JNCIP-SEC)
- Certification Provider: Juniper
- Latest update: Feb 27,2026
You are enabling advanced policy-based routing. You have configured a static route that has a next hop from the inet.0 routing table. Unfortunately, this static route is not active in your routing instance.
In this scenario, which solution is needed to use this next hop?
- A . Use RIB groups.
- B . Use filter-based forwarding.
- C . Use transparent mode.
- D . Use policies.
Exhibit:
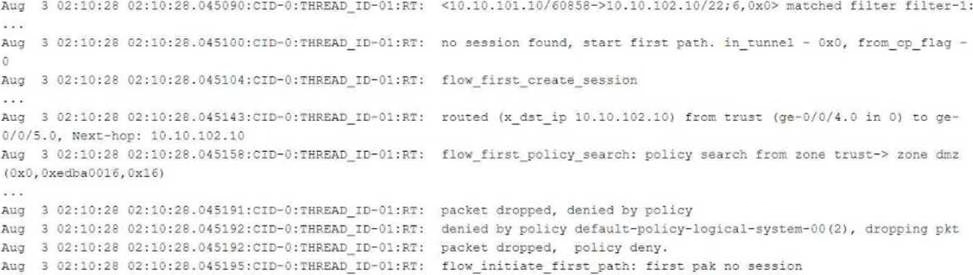
Referring to the flow logs exhibit, which two statements are correct? (Choose two.)
- A . The packet is dropped by the default security policy.
- B . The packet is dropped by a configured security policy.
- C . The data shown requires a traceoptions flag of host-traffic.
- D . The data shown requires a traceoptions flag of basic-datapath.
Exhibit:
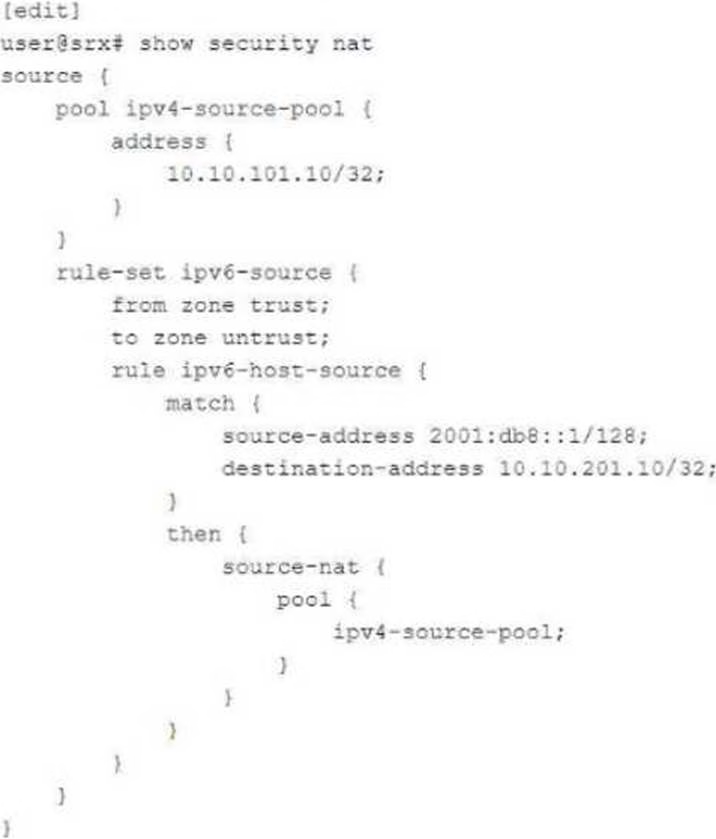
You are configuring NAT64 on your SRX Series device. You have committed the configuration shown in the exhibit. Unfortunately, the communication with the 10.10.201.10 server is not working. You have verified that the interfaces, security zones, and security policies are all correctly configured.
In this scenario, which action will solve this issue?
- A . Configure source NAT to translate return traffic from IPv4 address to the IPv6 address of your source device.
- B . Configure proxy-ARP on the external IPv4 interface for the 10.10.201.10/32 address.
- C . Configure proxy-NDP on the IPv6 interface for the 2001:db8::1/128 address.
- D . Configure destination NAT to translate return traffic from the IPv4 address to the IPv6 address of your source device.
What are three core components for enabling advanced policy-based routing? (Choose three.)
- A . Filter-based forwarding
- B . Routing options
- C . Routing instance
- D . APBR profile
- E . Policies
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
- A . The session did not properly reclassify midstream to the correct APBR rule.
- B . IDP disable is not configured on the APBR rule.
- C . The application services bypass is not configured on the APBR rule.
- D . The APBR rule does a match on the first packet.
Which two statements are correct about mixed mode? (Choose two.)
- A . Layer 2 and Layer 3 interfaces can use the same security zone.
- B . IRB interfaces can be used to route traffic.
- C . Layer 2 and Layer 3 interfaces can use separate security zones.
- D . IRB interfaces cannot be used to route traffic.
Exhibit:
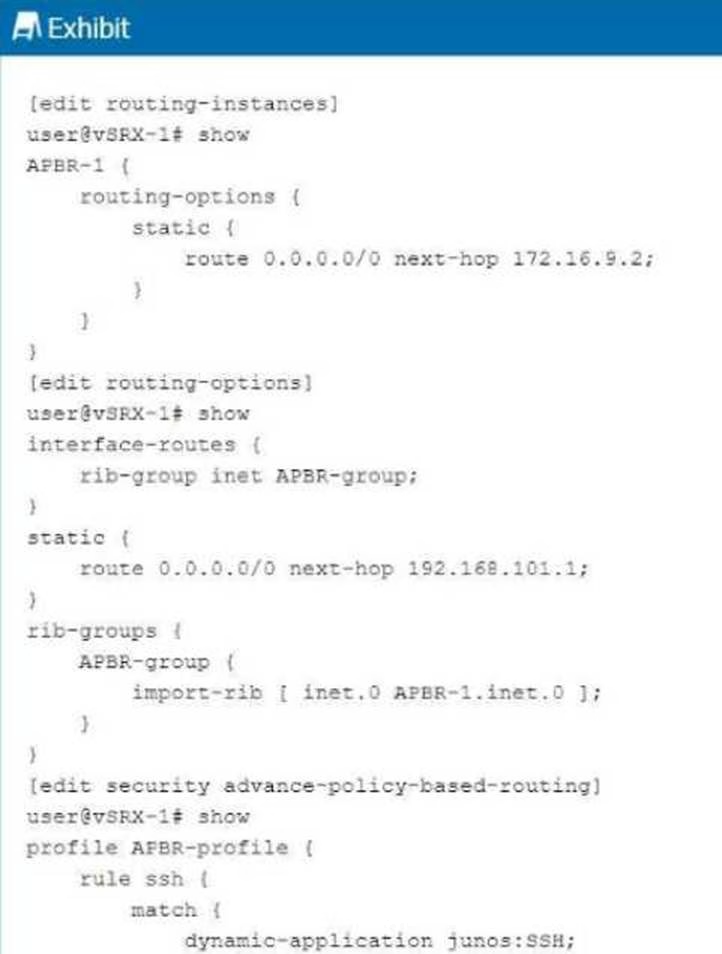
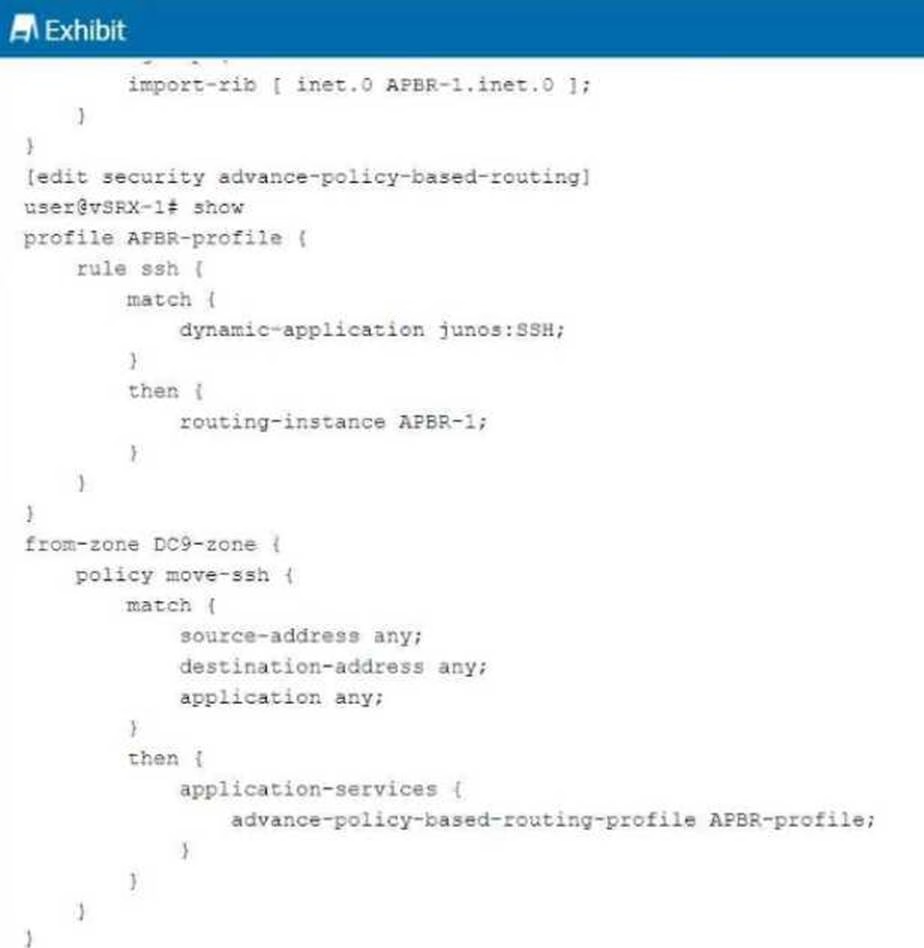
You are having problems configuring advanced policy-based routing.
What should you do to solve the problem?
- A . Apply a policy to the APBR RIB group to only allow the exact routes you need.
- B . Change the routing instance to a forwarding instance.
- C . Change the routing instance to a virtual router instance.
- D . Remove the default static route from the main instance configuration.
Exhibit:
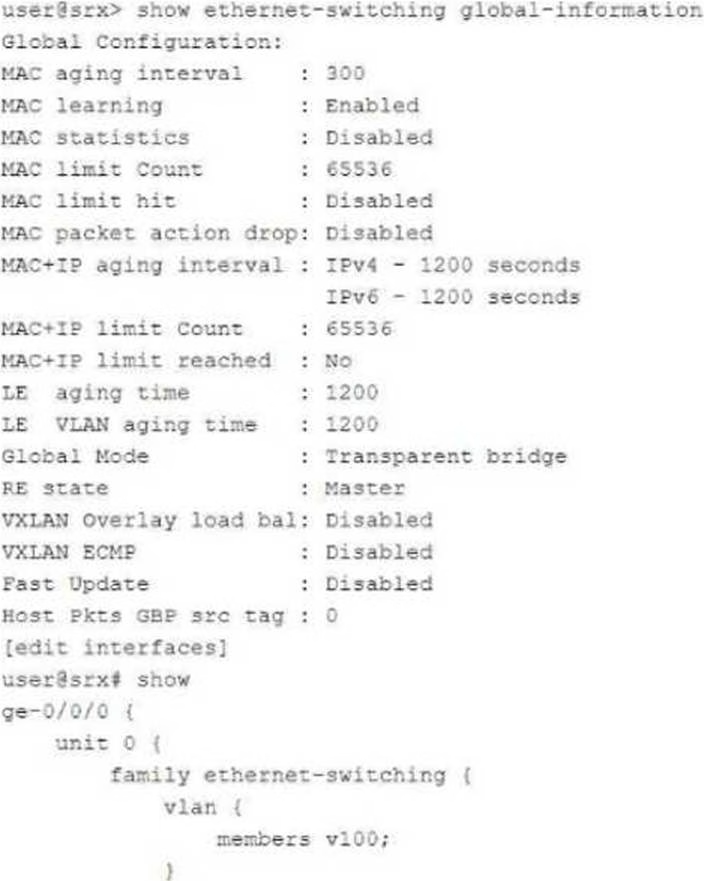
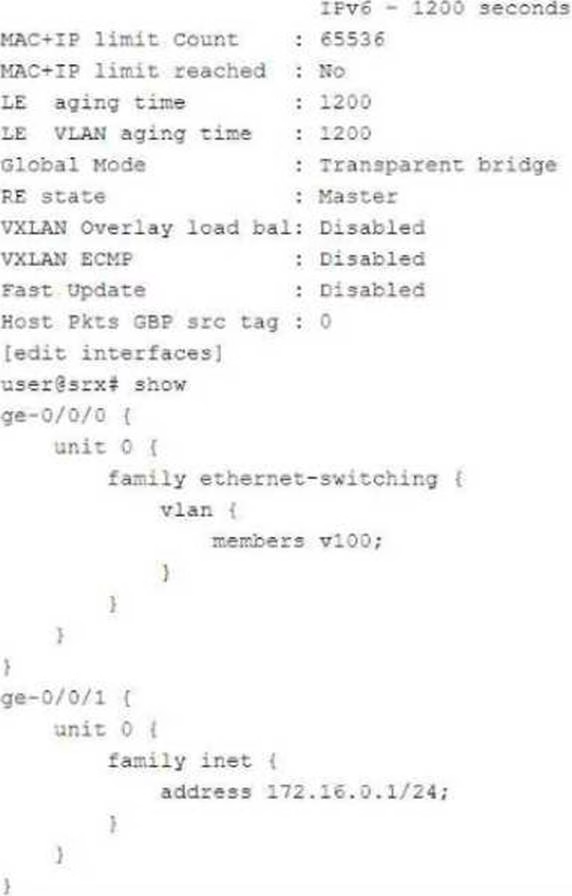
In which mode is the SRX Series device?
- A . Packet
- B . Ethernet switching
- C . Mixed
- D . Transparent
You configure two Ethernet interfaces on your SRX Series device as Layer 2 interfaces and add them to the same VLAN. The SRX is using the default L2-learning setting. You do not add the interfaces to a security zone.
Which two statements are true in this scenario? (Choose two.)
- A . You are unable to apply stateful security features to traffic that is switched between the two interfaces.
- B . You are able to apply stateful security features to traffic that enters and exits the VLAN.
- C . The interfaces will not forward traffic by default.
- D . You cannot add Layer 2 interfaces to a security zone.
Which two statements are true about the procedures the Junos security device uses when handling traffic destined for the device itself? (Choose two.)
- A . If the received packet is addressed to the ingress interface, then the device first performs a security policy evaluation for the junos-host zone.
- B . If the received packet is destined for an interface other than the ingress interface, then the device performs a security policy evaluation for the junos-host zone.
- C . If the received packet is addressed to the ingress interface, then the device first examines the host-inbound-traffic configuration for the ingress interface and zone.
- D . If the received packet is destined for an interface other than the ingress interface, then the device performs a security policy evaluation based on the ingress and egress zone.
Latest JN0-637 Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

